misc
SignIn
赛博厨子一把梭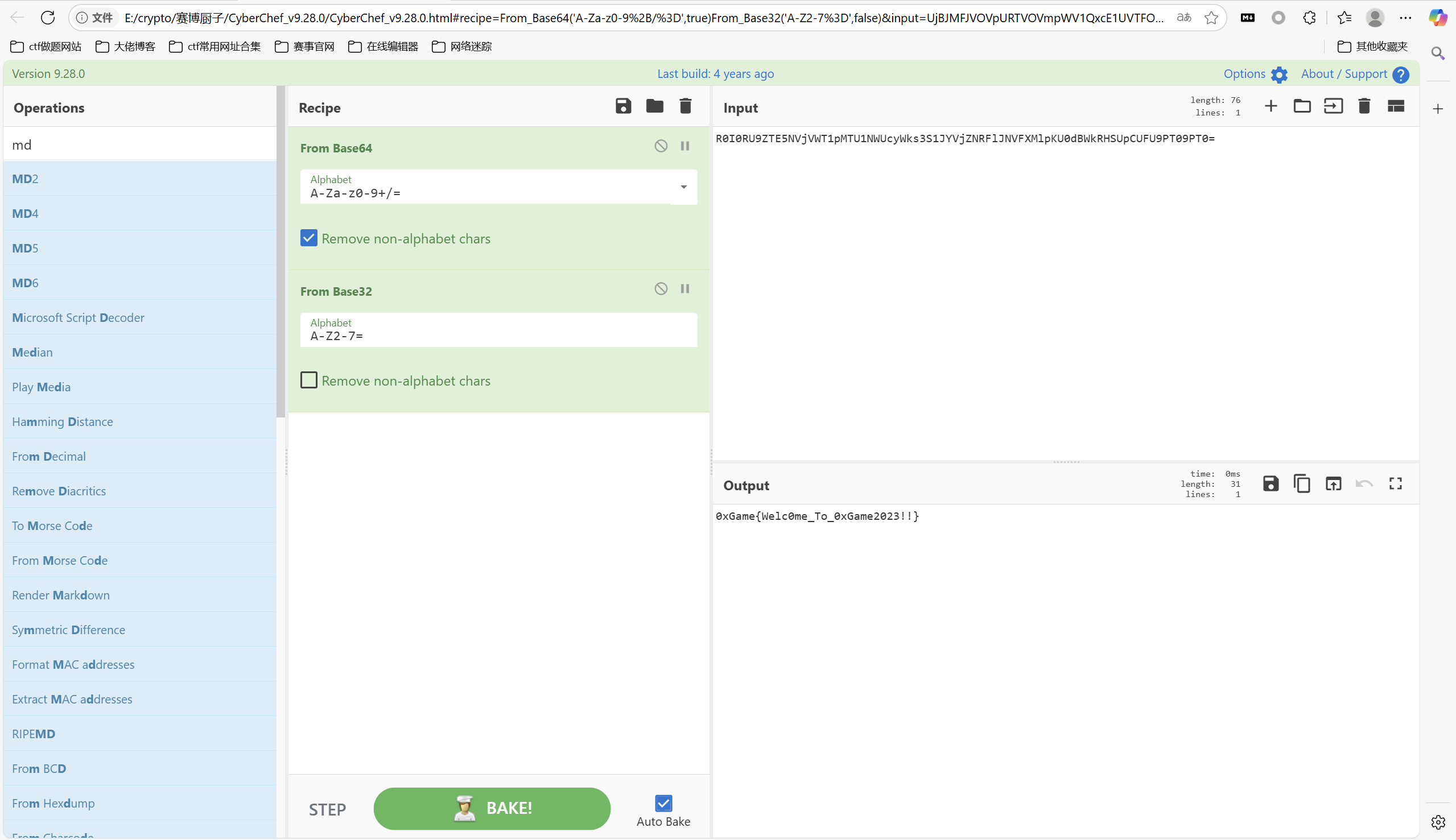
最后flag为
1 | 0xGame{Welc0me_To_0xGame2023!!} |
重生之我在教学楼打cs
bsp⽂件再结合题⽬名可以搜索到是cs的地图,尝试之后可以⽤GCFScape打开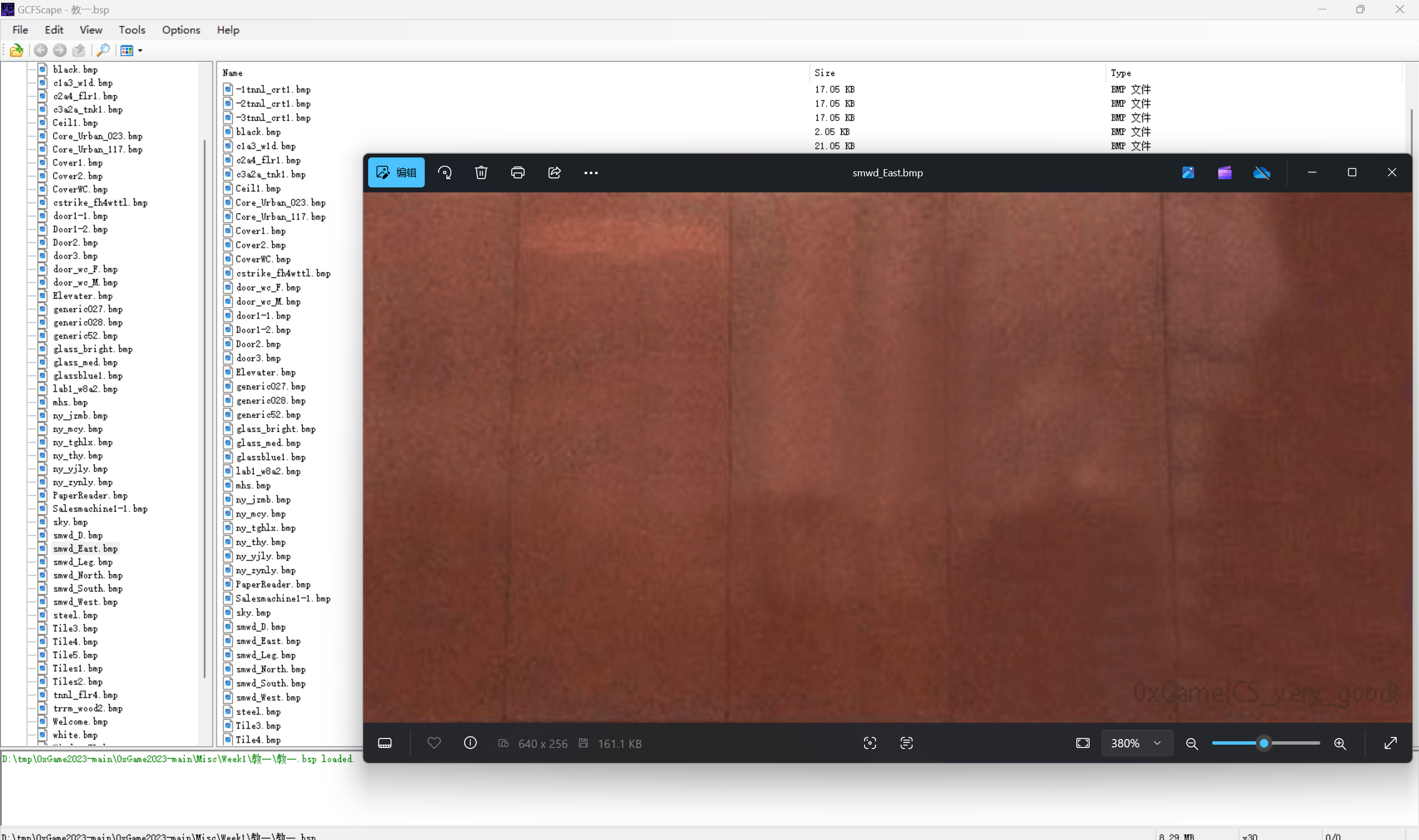
最后flag为
1 | 0xGame{CS_very_good} |
shark shark
ctfnat-A一把梭得到ftp登录密码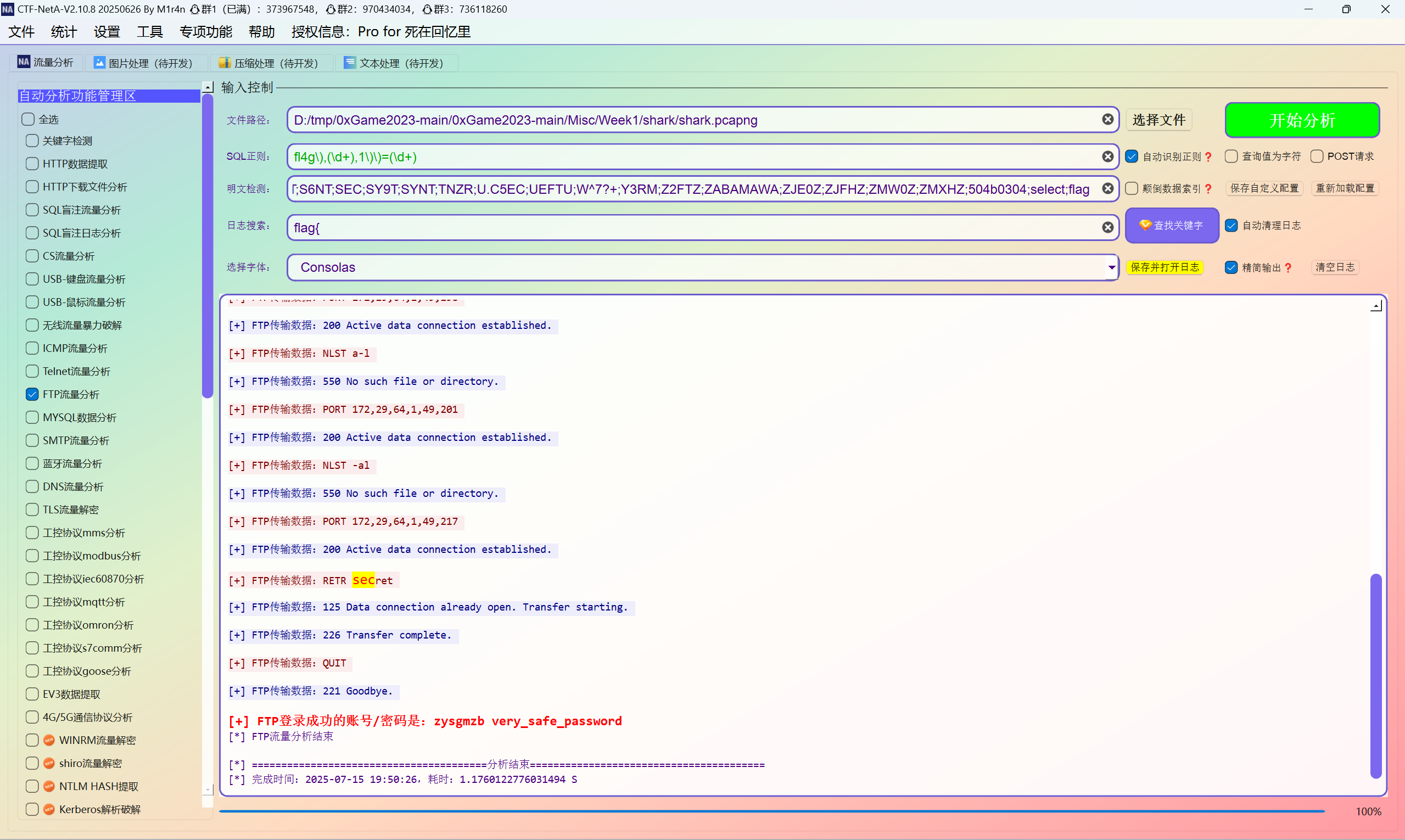
ftp追踪流得到压缩包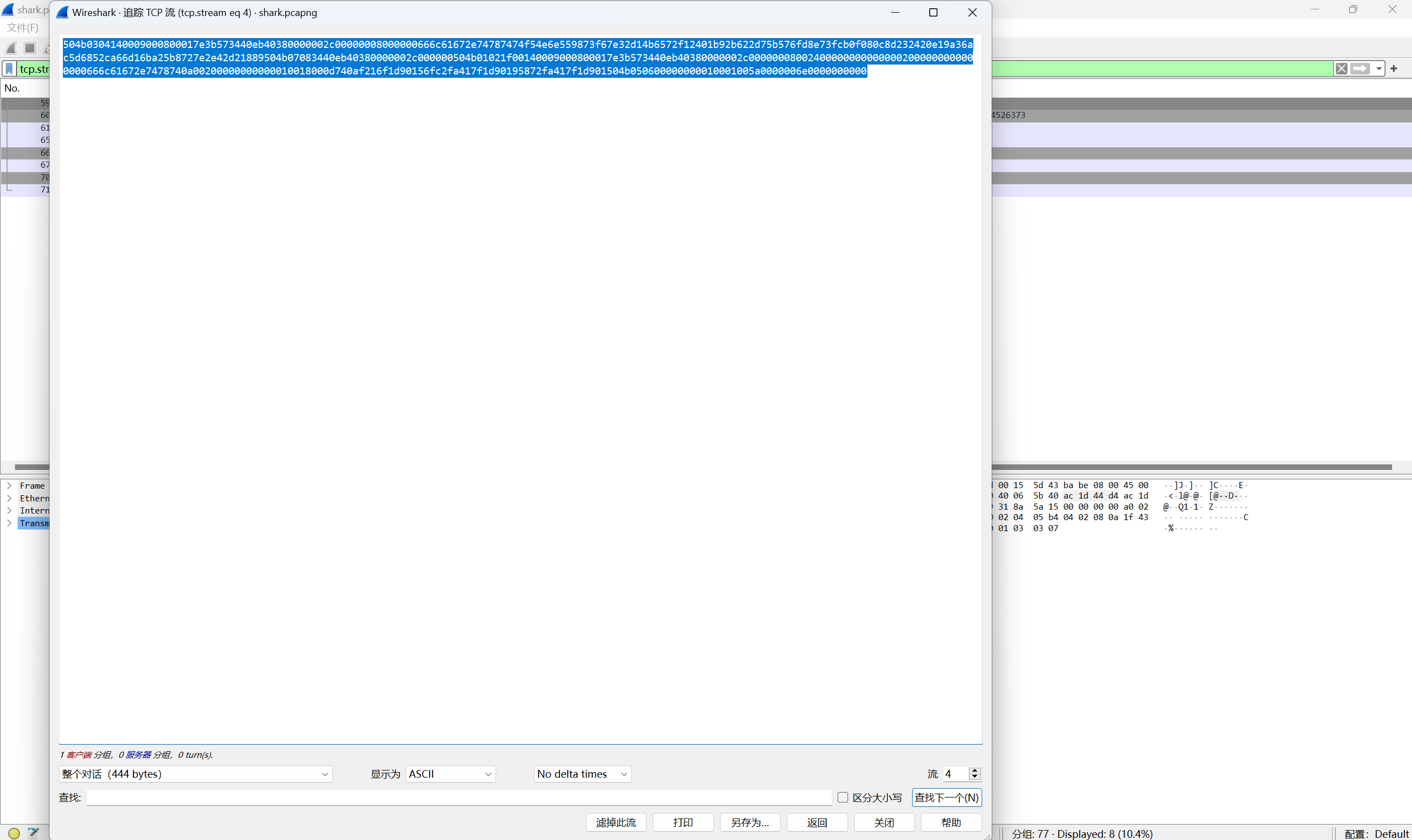
保存压缩包并解压压缩包得到flag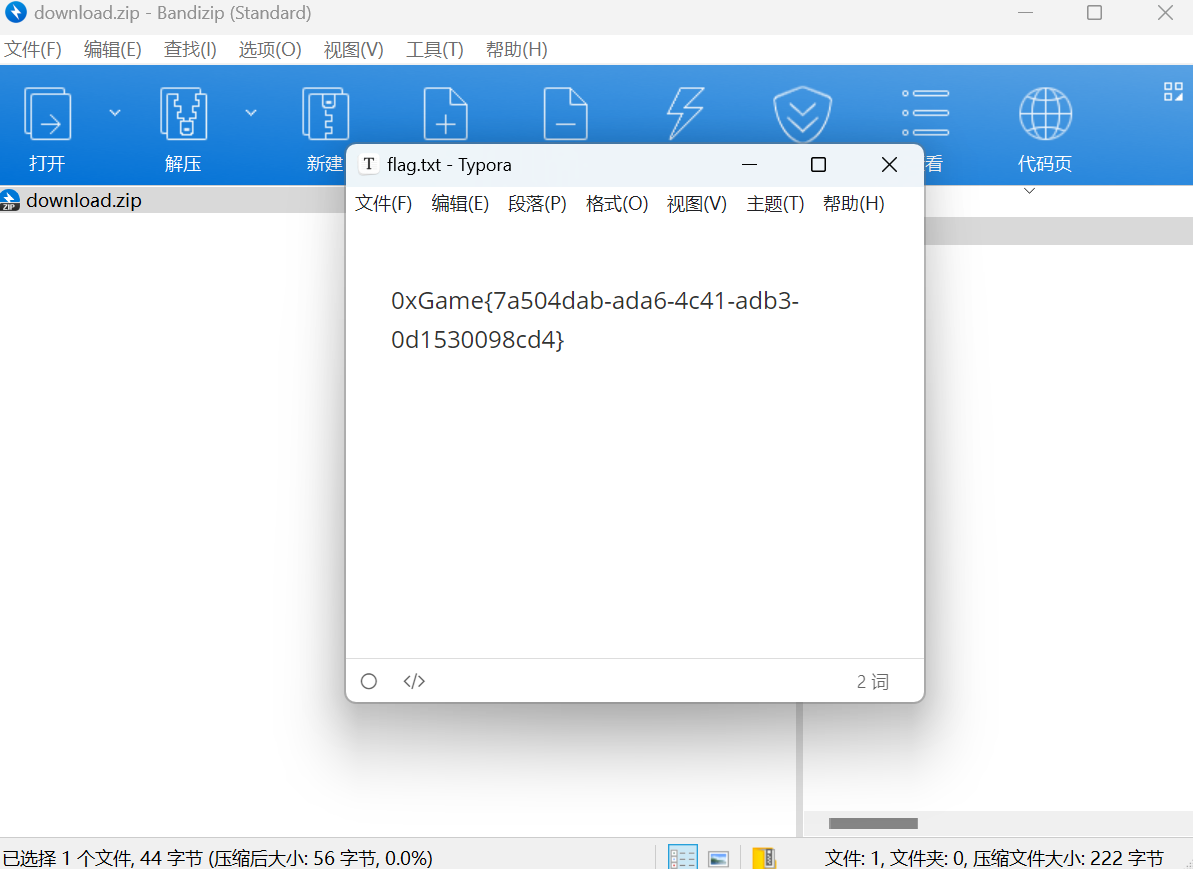
最后flag为
1 | 0xGame{7a504dab-ada6-4c41-adb3-0d1530098cd4} |
hide and seek
steghide隐写弱⼝令爆破,使⽤rockyou.txt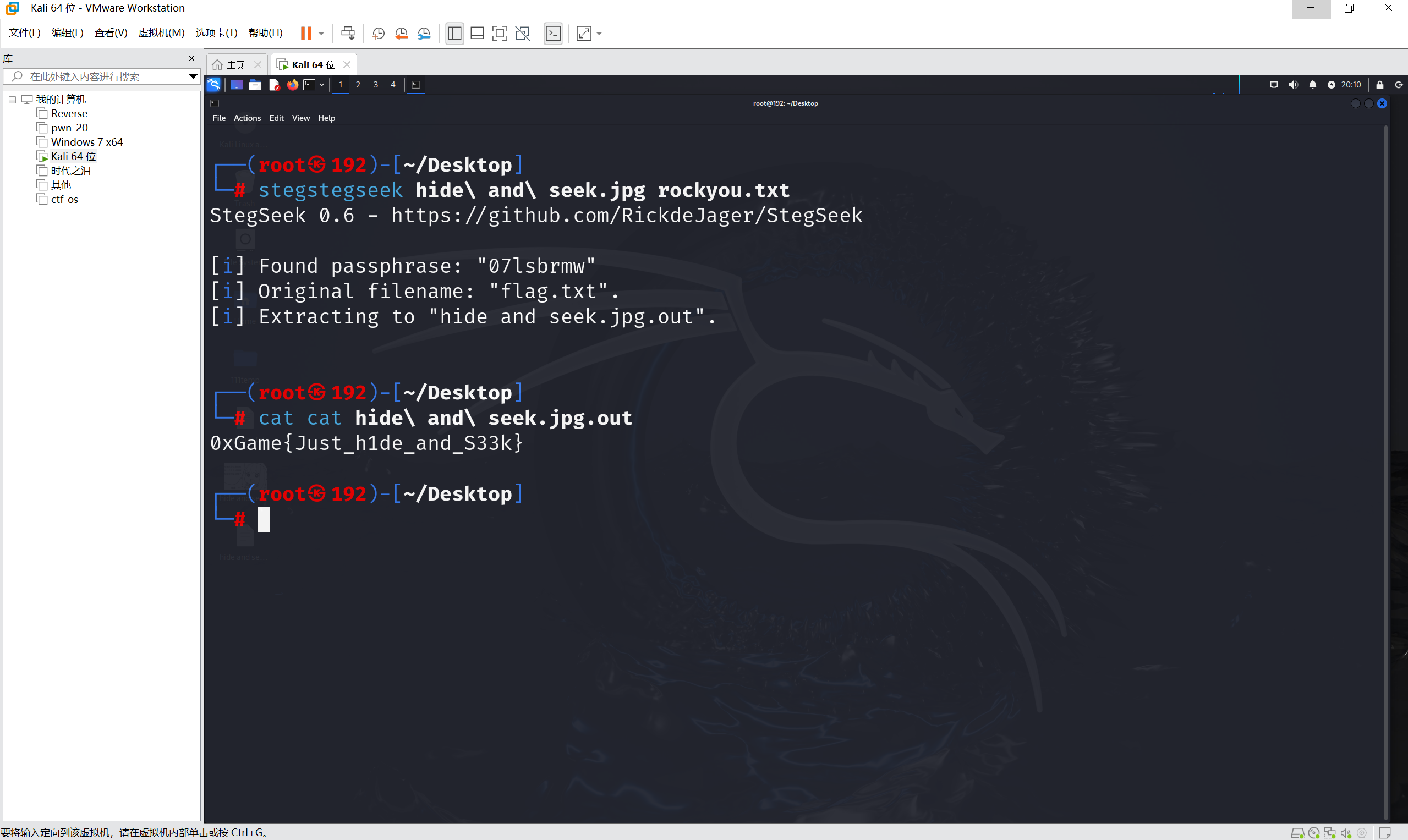
最后flag为
1 | 0xGame{Just_h1de_and_S33k} |
least and most
least significant bit和most significant bit
使⽤stegsolve⼯具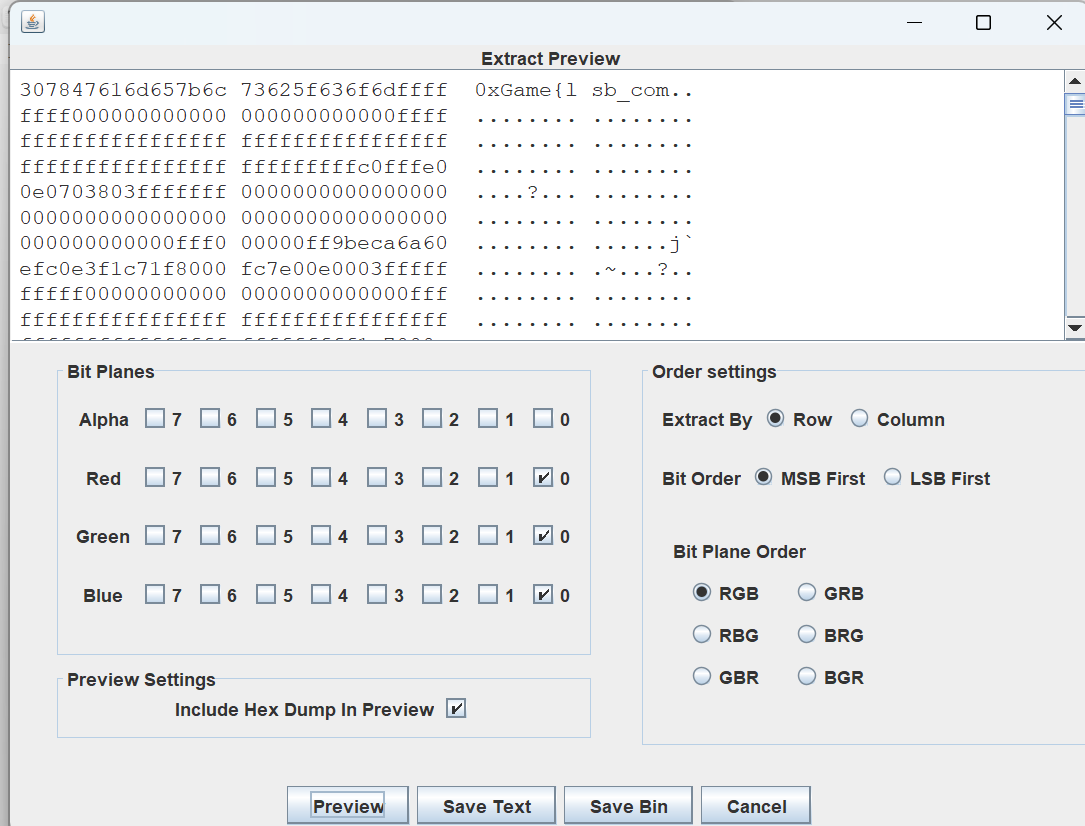
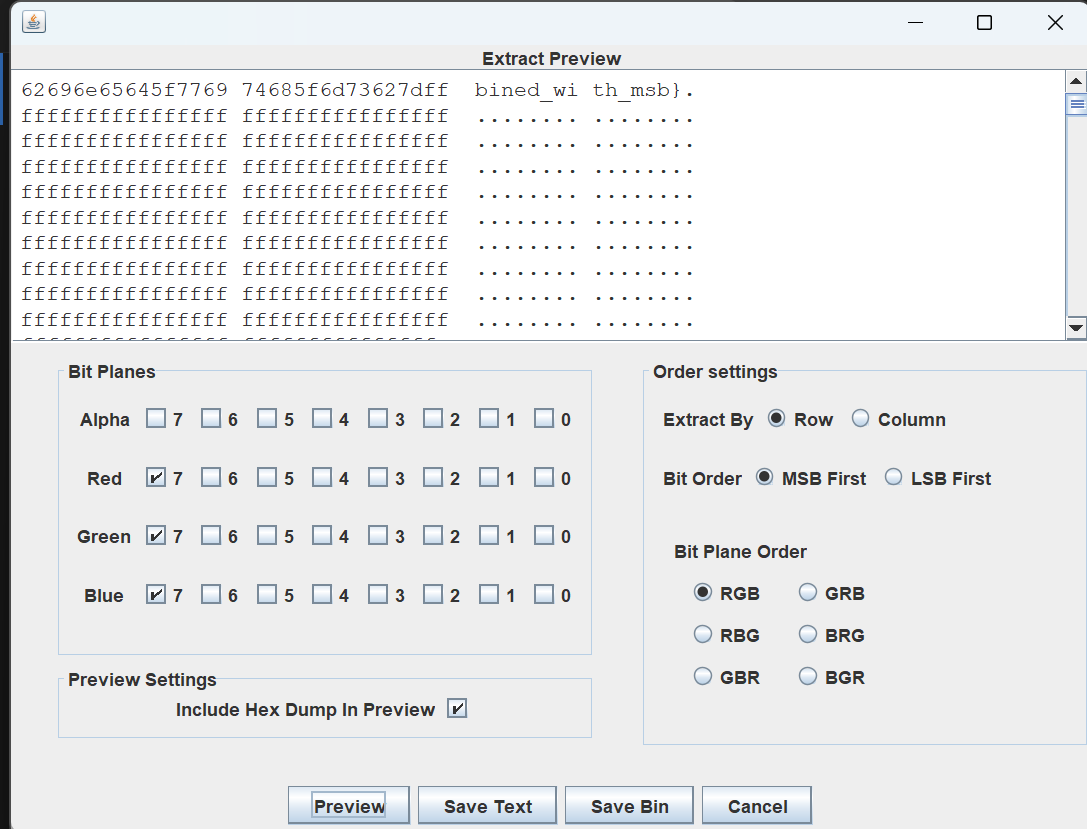
最后flag为
1 | 0xGame{lsb_combined_with_msb} |
findme2
下载附件
1 | 我们的老朋友WearyMeadow听说0xGame2023开始了,和zysgmzb进行了一手小小的py提前拿到了第二周的所有题目,然后顺手写了Misc部分的wp发到博客里,为了防止上次的情况再次发生,他把github里的密码全删了,这次应该安全了 |
根据题目描述,直接去github搜索WearyMeadow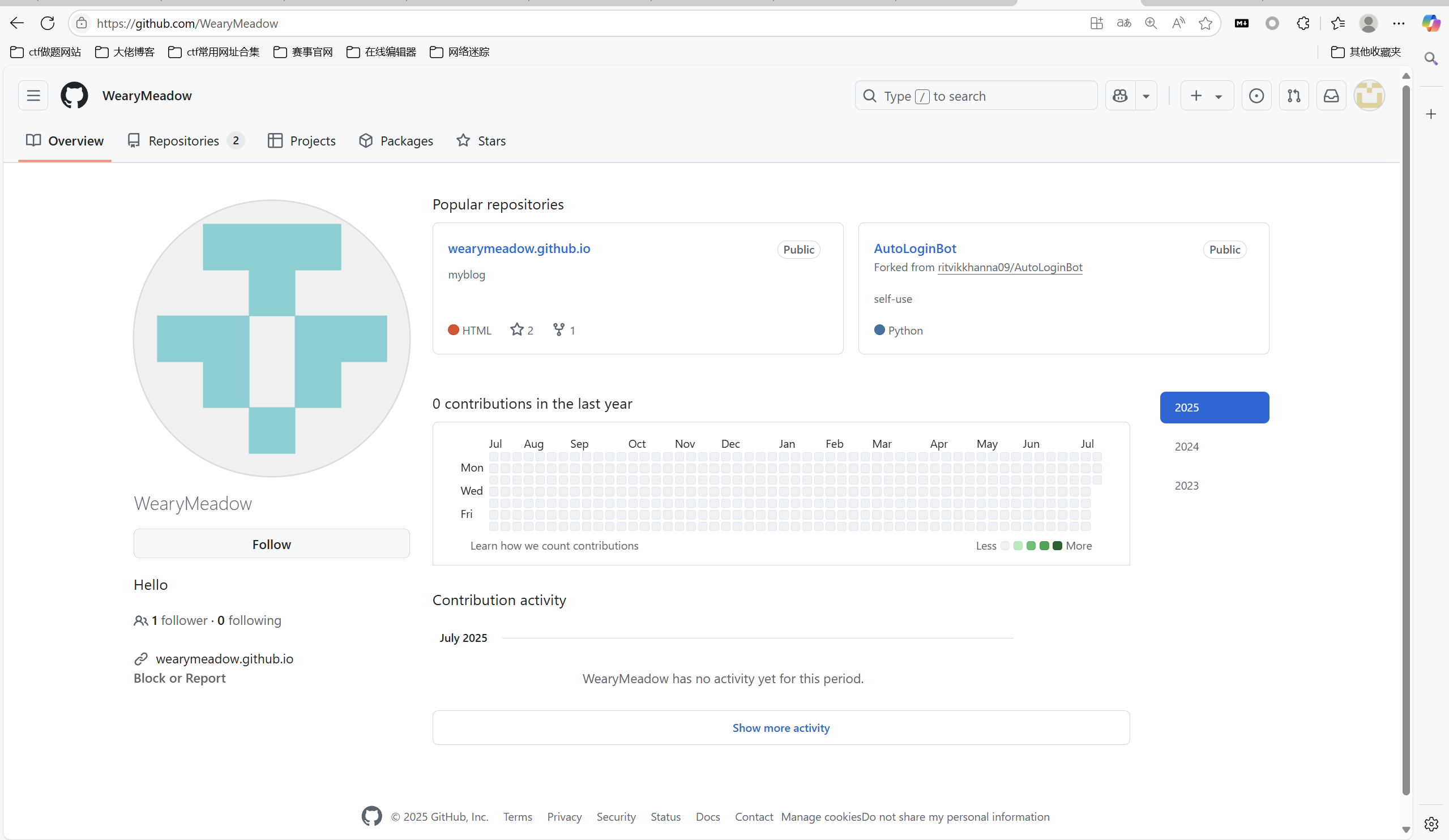
可以看到一共两个项目, 一个是博客,另一个是自用的登录脚本
博客里只有一篇上锁的wp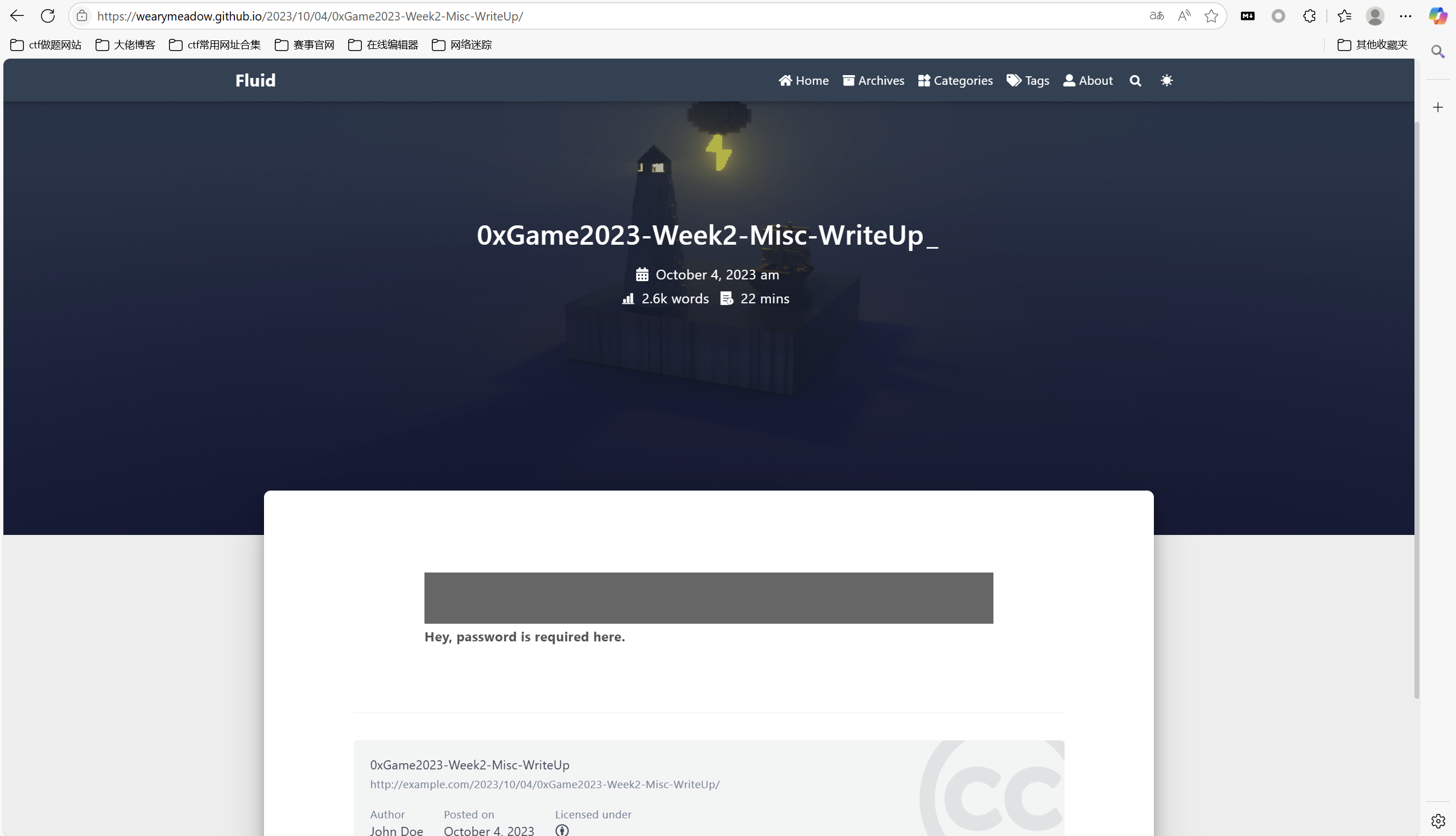
结合题目描述说把密码删了,就可以去翻一翻修改记录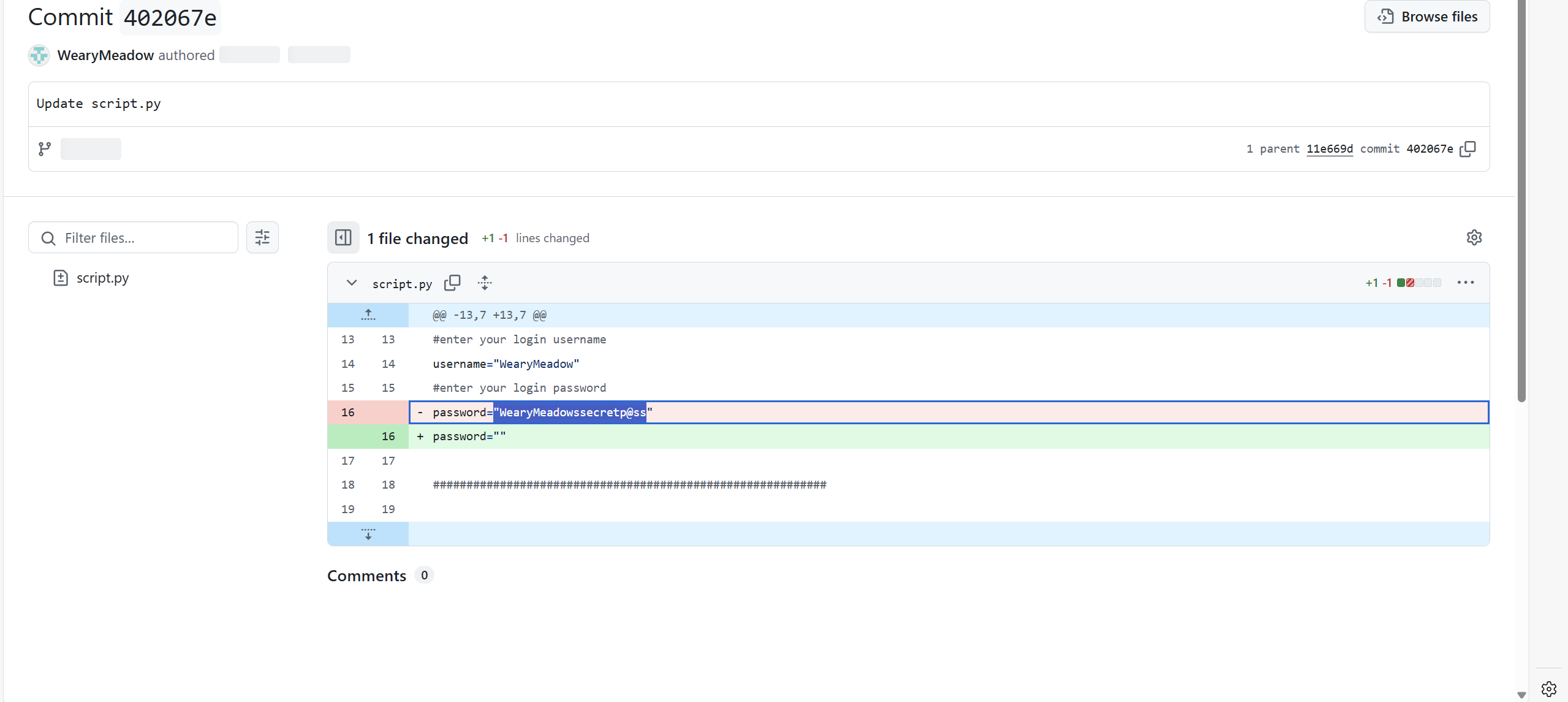
直接解锁文章就可以拿到flag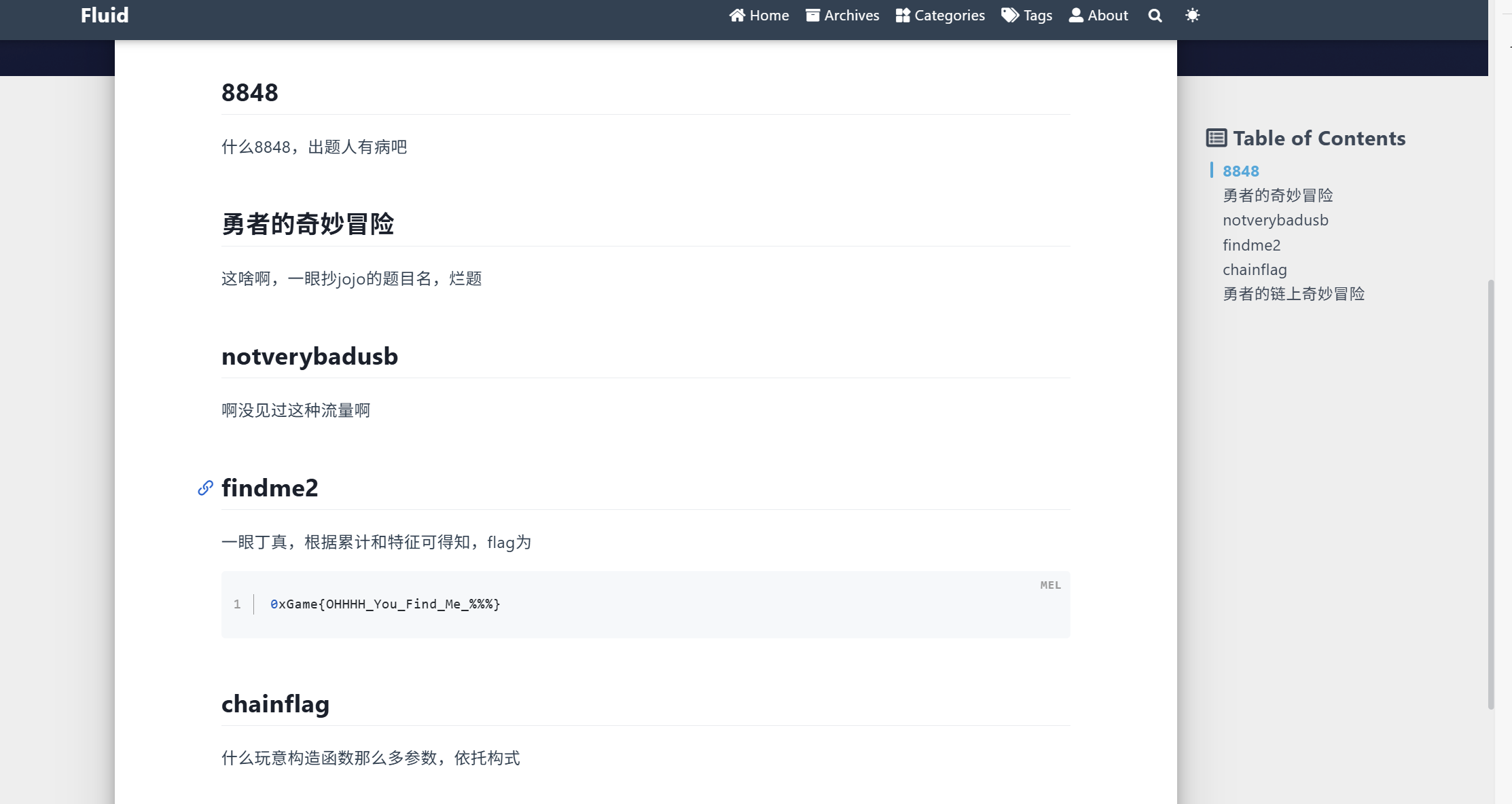
最后flag为
1 | 0xGame{OHHHH_You_Find_Me_%%%} |
Miversc
先用ook和brainfuck之间的对应关系得到原始的brainfuck代码
1 | >++++++++[>>++>++++>++++++>++++++++>++++++++++>++++++++++++>++++++++++++++>++++++++++++++++>++++++++++++++++++>++++++++++++++++++++>++++++++++++++++++++++>++++++++++++++++++++++++>++++++++++++++++++++++++++>++++++++++++++++++++++++++++>++++++++++++++++++++++++++++++<<<<<<<<<<<<<<<<-]>>>>>++++++++.>>+++++.>----..+++.<<<<----.<.>>>>>+.----.<.----.>+++++++.<++++.<<<<.>>>>++++.+++++.++.>++.-.<<<<<.>>>>>.<--------.---.<<<<.>>>>+.++++++.-----------.++++++.[>]+[[-]<]>,<++++++[->--------<]>,<++++++++++[->------------<]>,-<+++++++[->----------<]>,--<+++++[->-------------------<]>,+<++++++++++[->-----------<]>,-<++++++++++[->----------<]>,---<++++++++++[->------------<]>,+<+++++[->---------------<]>,+++<++++++++++[->------------<]>,<+++++[->-----------------------<]>,<++++[->-----------------------------<]>,<+++++[->-------------------<]>,--<++++++++[->----------<]>,-<++++++++++[->----------<]>,++<++++++++++[->------------<]>,-<++++++++++[->----------<]>,<++++++[->-------------------<]>,<+++++[->-----------------------<]>,-<++++++++++[->----------<]>,<+++++[->-------------------<]>,+<++++++++[->----------<]>,-<++++++++++[->-----------<]>,<+++++[->---------------<]>,<+++[->-----------<]>,<+++++[->-------------------------<]++++++++[>>++>++++>++++++>++++++++>++++++++++>++++++++++++>++++++++++++++>++++++++++++++++>++++++++++++++++++>++++++++++++++++++++>++++++++++++++++++++++>++++++++++++++++++++++++>++++++++++++++++++++++++++>++++++++++++++++++++++++++++>++++++++++++++++++++++++++++++<<<<<<<<<<<<<<<<-]>>>>>>>++++++.>----.<-----.>-----.<<<<<.>>>>>++.++++++++++.<<<<<.>>>>>++++.<+++++++.-------.>---.<<<<<.>>>>>+++++.----------.++++++.<<<<<.>>>>++++++++.+++++.++.>.-. |
然后搜索brainfuck基本语法再来看这段代码即可知道只是非常简单的比较,每一轮比较的结果是当前cell和下一个cell都为0
借用大佬exp:
1 | # msg = open('miverse.txt').read().replace('\n','').replace('\r','') |
最后flag为
1 | 0xGame{Just_ReLerse_OoK!} |
crypto
觅码
下载附件
1 | from secret import flag #从中导入秘密的flag,这是我们要破解的信息 |
分了4段进行加密,part1是转整后再5次幂,part2是转二进制,part3是base64,part4是16进制,最后合起来是乱码bytes转str用utf-8(默认值)
exp:
1 | from gmpy2 import iroot |
运行得到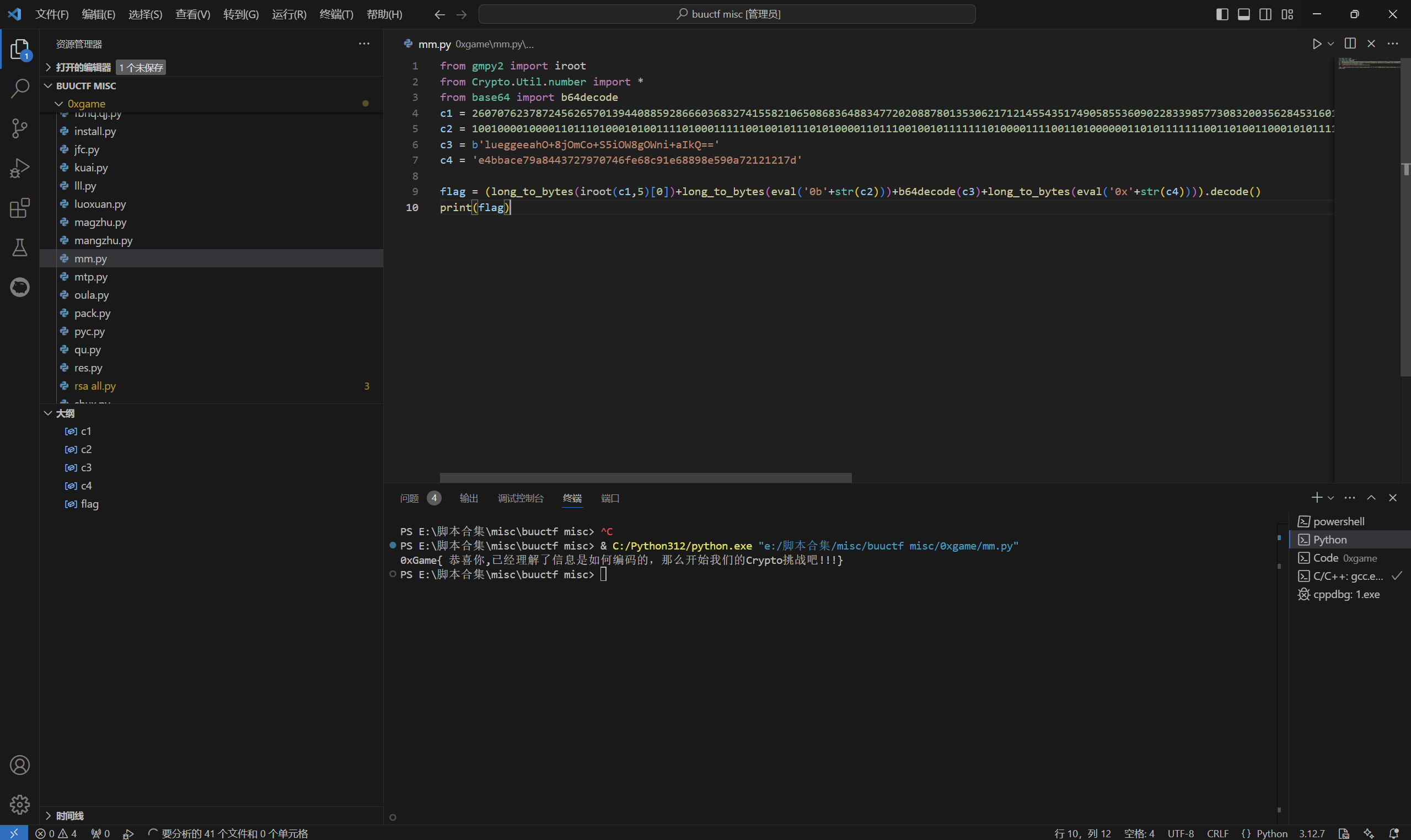
最后flag为
1 | 0xGame{ 恭喜你,已经理解了信息是如何编码的,那么开始我们的Crypto挑战吧!!!} |
BabyRSA
下载附件
1 | from Crypto.Util.number import * |
exp:
1 | from Crypto.Util.number import * |
运行得到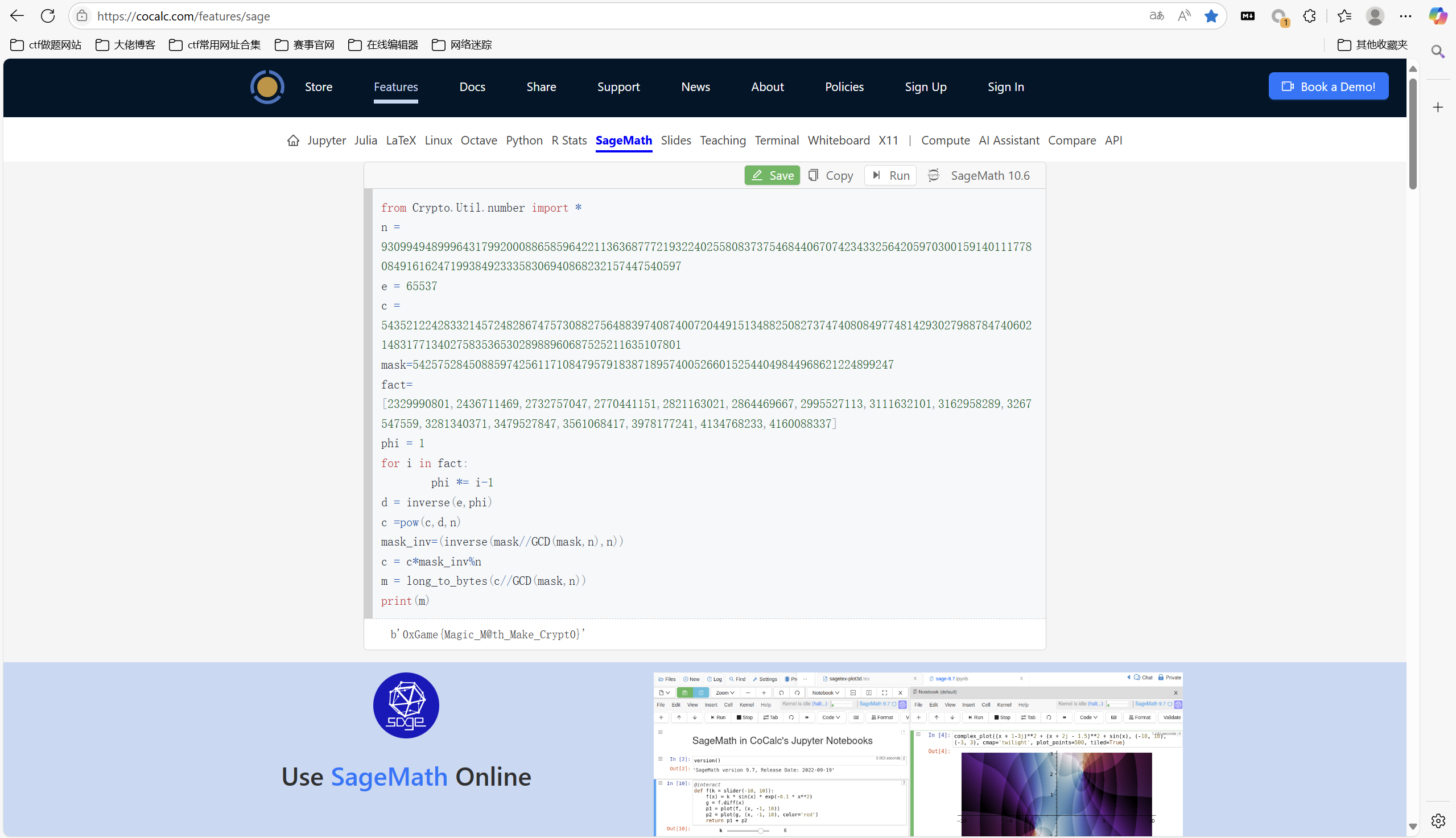
最后flag为
1 | 0xGame{Magic_M@th_Make_Crypt0} |
Take my bag
下载附件
1 | from Crypto.Util.number import * |
超递增序列,背包密码
exp:
1 | from Crypto.Util.number import * |
运行得到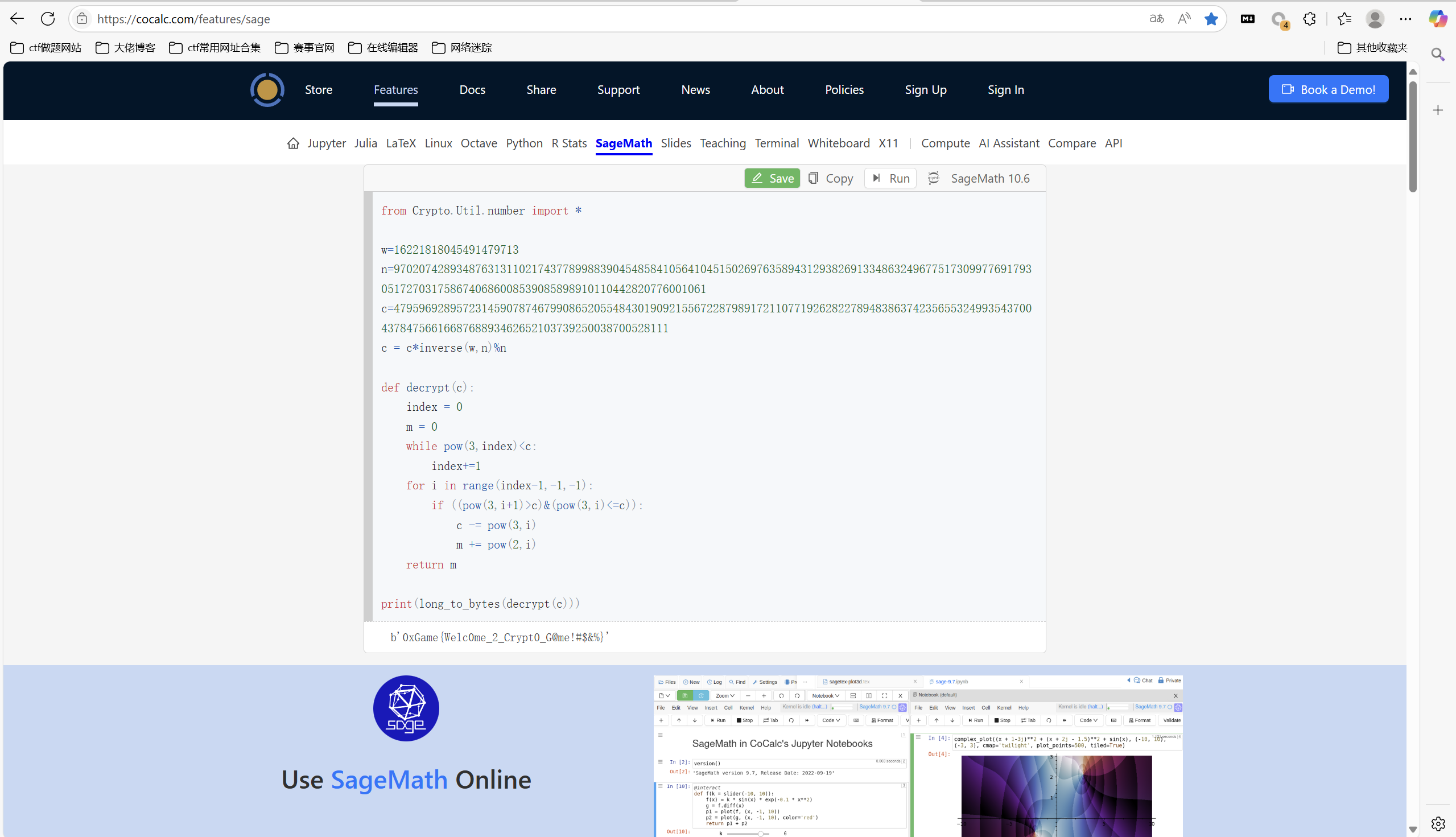
最后flag为
1 | 0xGame{Welc0me_2_Crypt0_G@me!#$&%} |
CBC
下载附件
1 | from Crypto.Util.number import * |
穷举爆破
exp:
1 | from Crypto.Util.number import * |
运行得到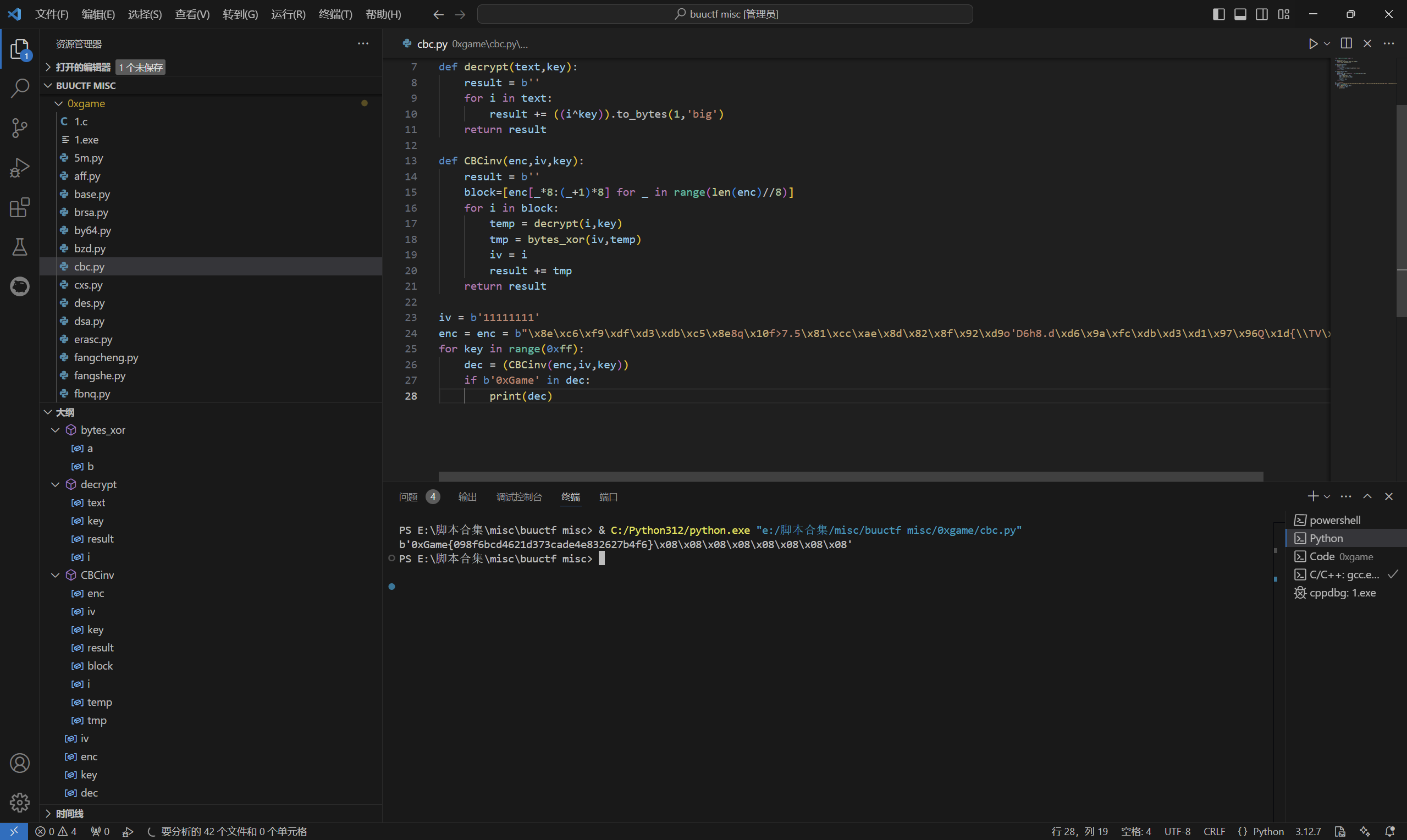
最后flag为
1 | 0xGame{098f6bcd4621d373cade4e832627b4f6} |
猜谜
下载附件
1 | from secret import flag,key |
侧信道攻击
exp:
1 | from Crypto.Util.number import * |
运行得到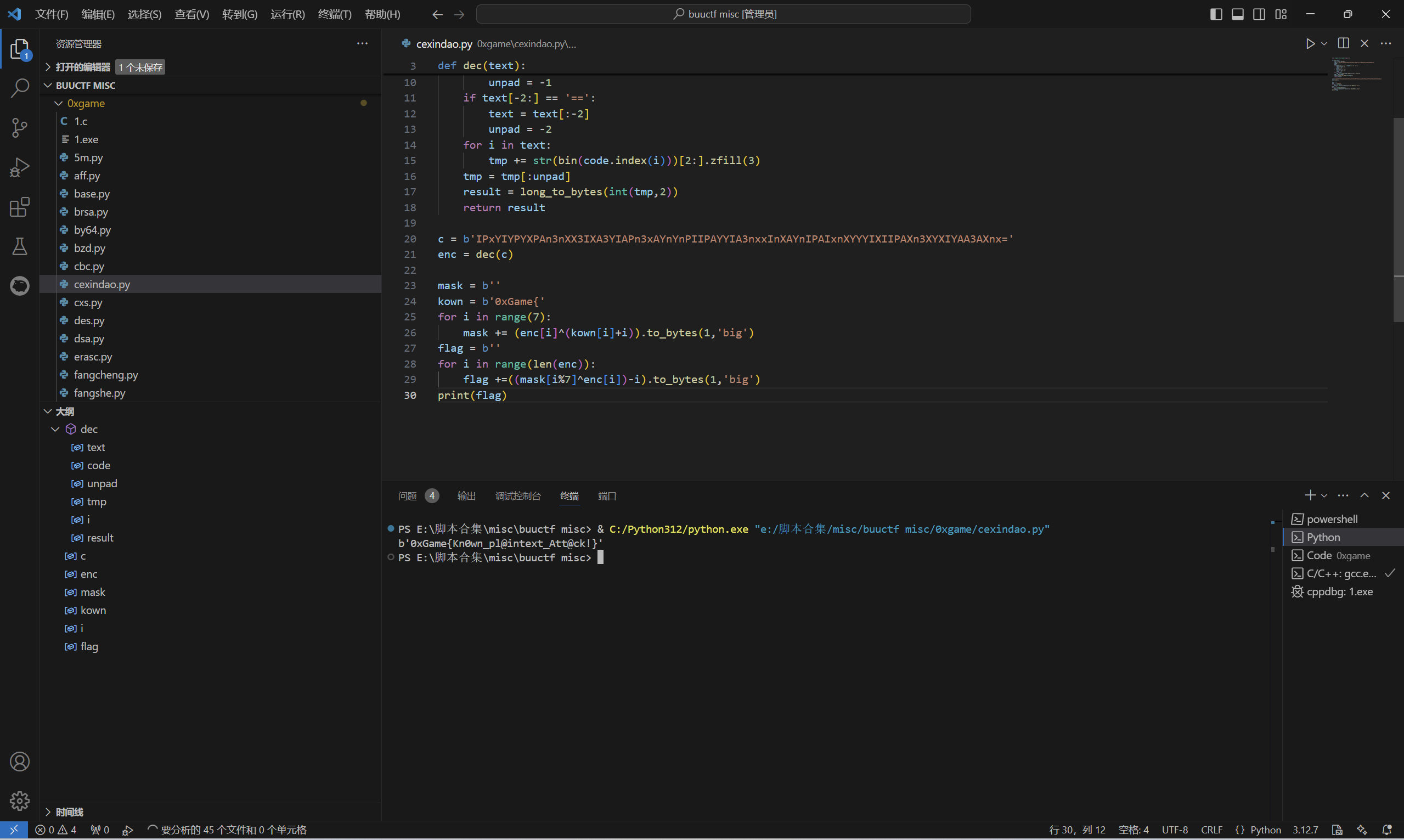
最后flag为
1 | 0xGame{Kn0wn_pl@intext_Att@ck!} |
维吉尼亚密码
下载附件
1 | 0dGmqk{79ap4i0522g0a67m6i196he52357q60f} |
维吉尼亚根据flag格式推算密钥得到game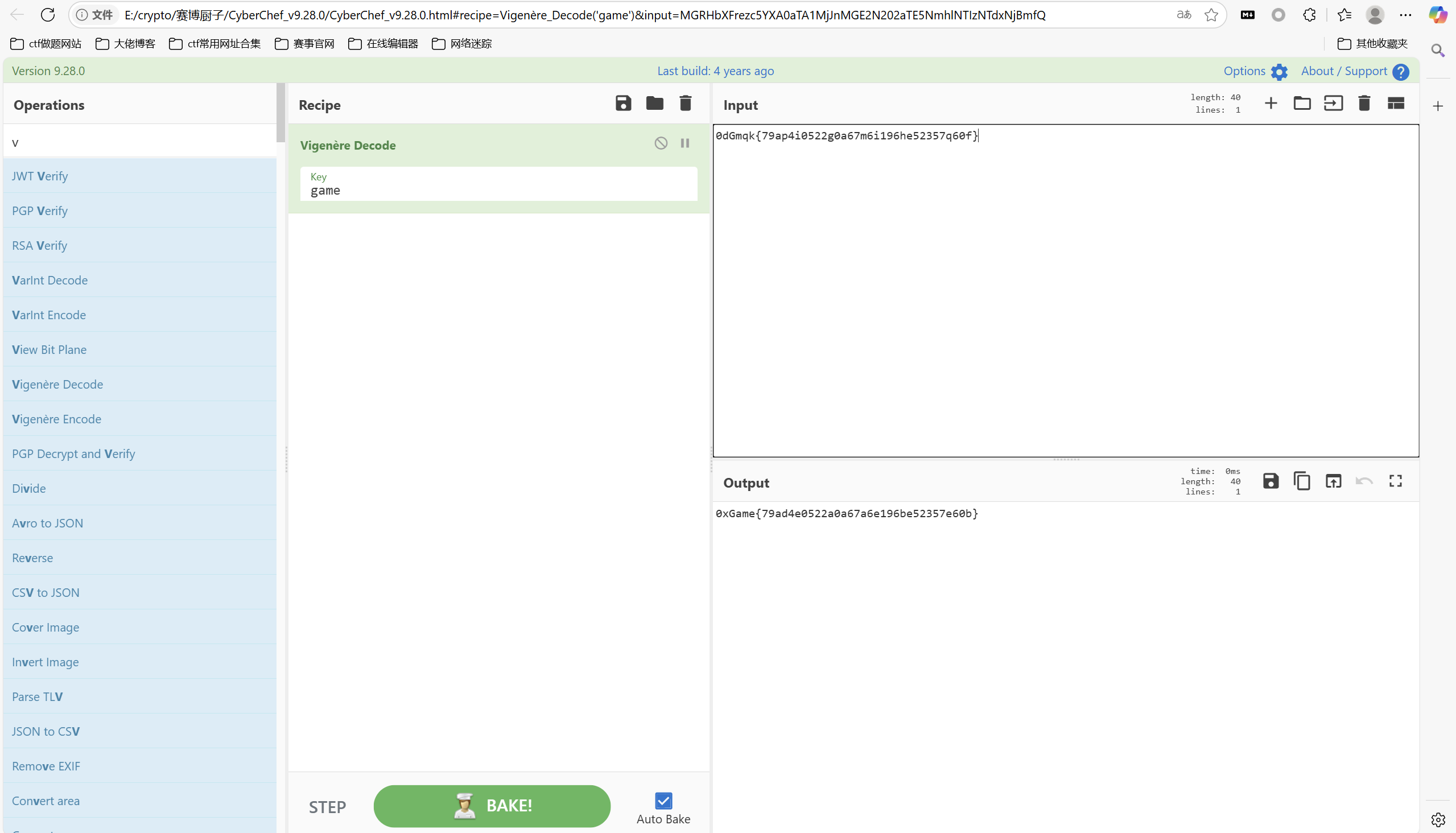
最后flag为
1 | 0xGame{79ad4e0522a0a67a6e196be52357e60b} |
中间的那个人
下载附件
1 | from secret import flag |
DH算法
exp:
1 | from Crypto.Util.number import * |
运行得到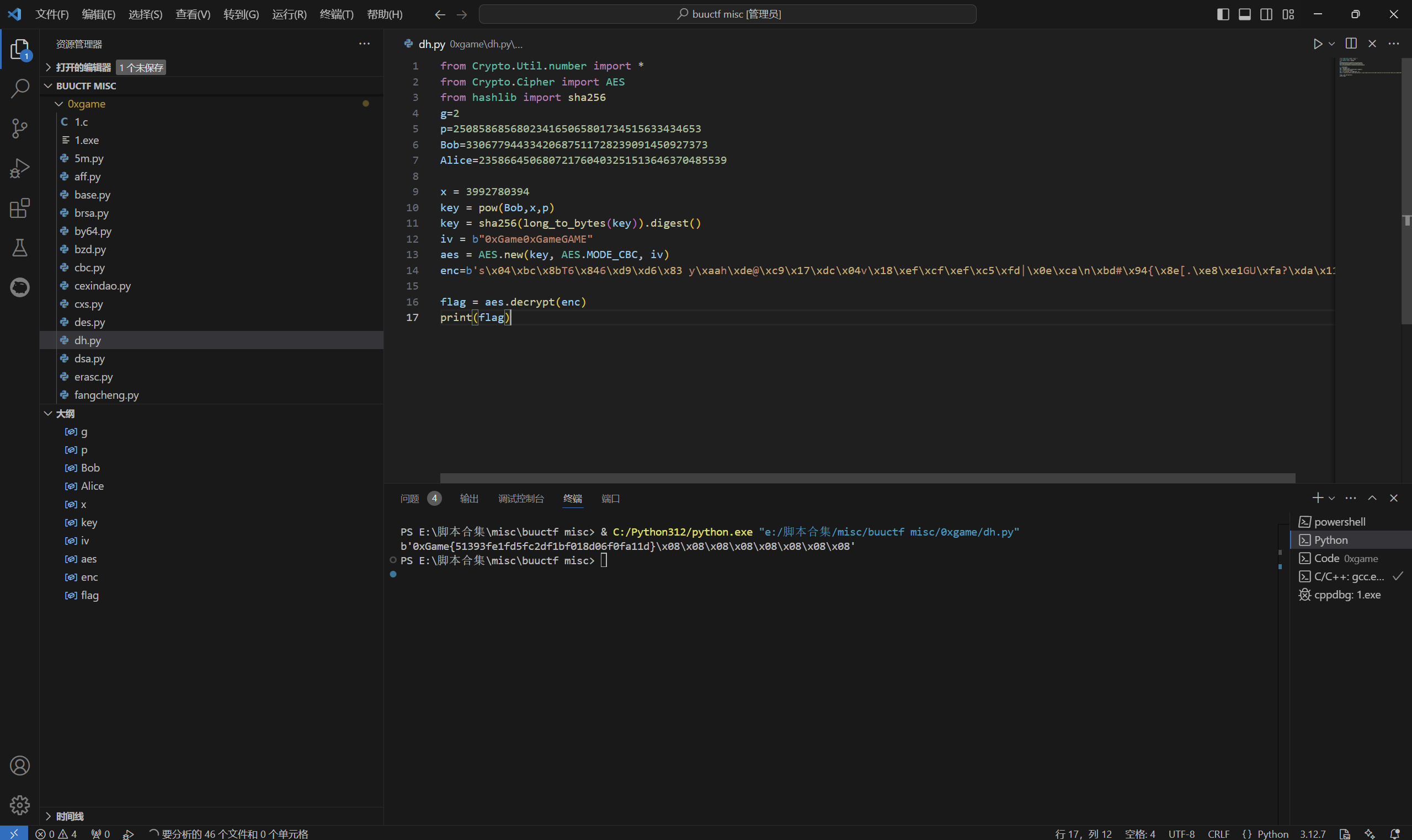
最后flag为
1 | 0xGame{51393fe1fd5fc2df1bf018d06f0fa11d} |
What’s CRT?
下载附件
1 | from Crypto.Util.number import * |
exp:
1 | import gmpy2 |
运行得到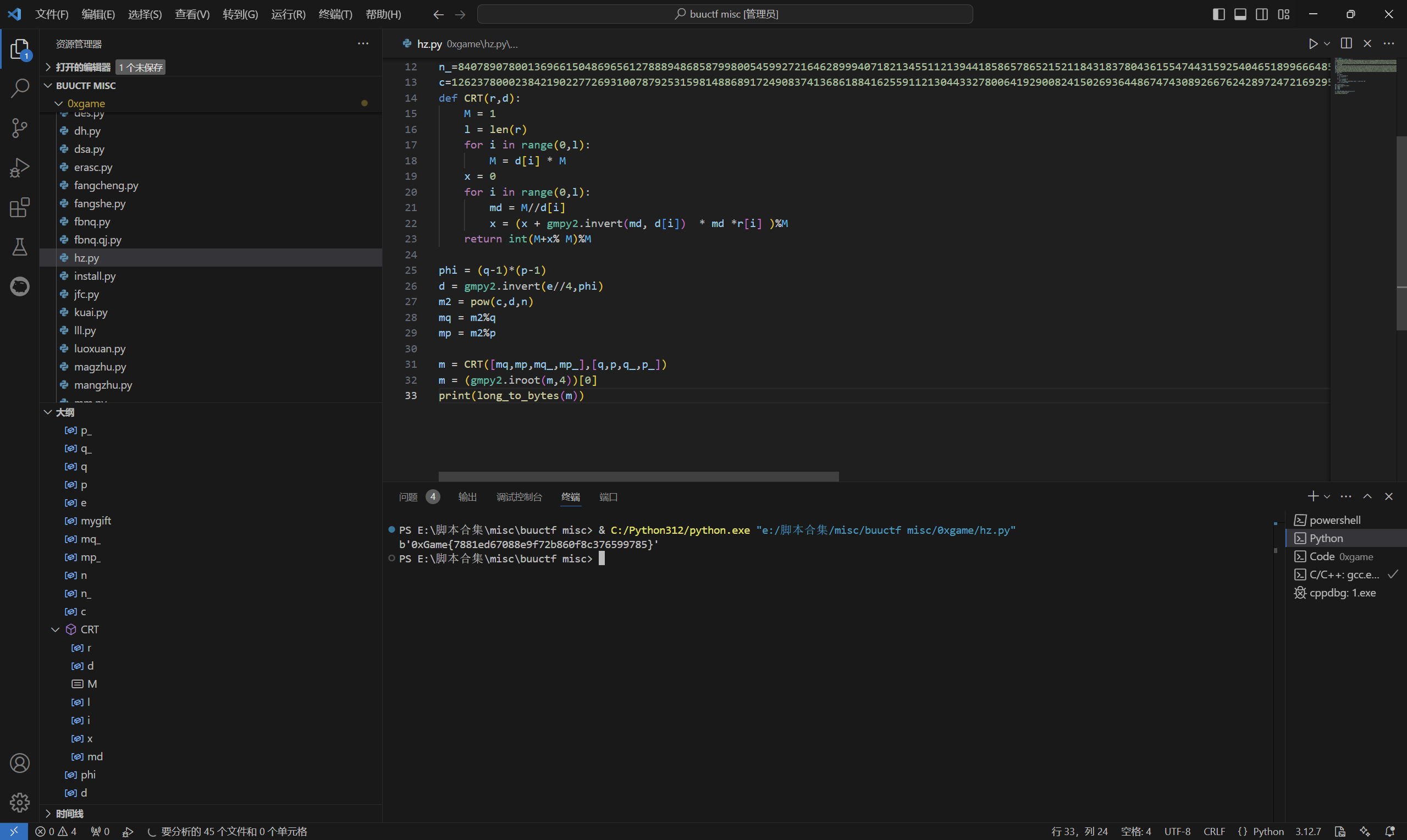
最后flag为
1 | 0xGame{7881ed67088e9f72b860f8c376599785} |
EzLFSR
下载附件
1 | from Crypto.Util.number import * |
线性反馈移位寄存器
exp:
1 | from Crypto.Util.number import * |
运行得到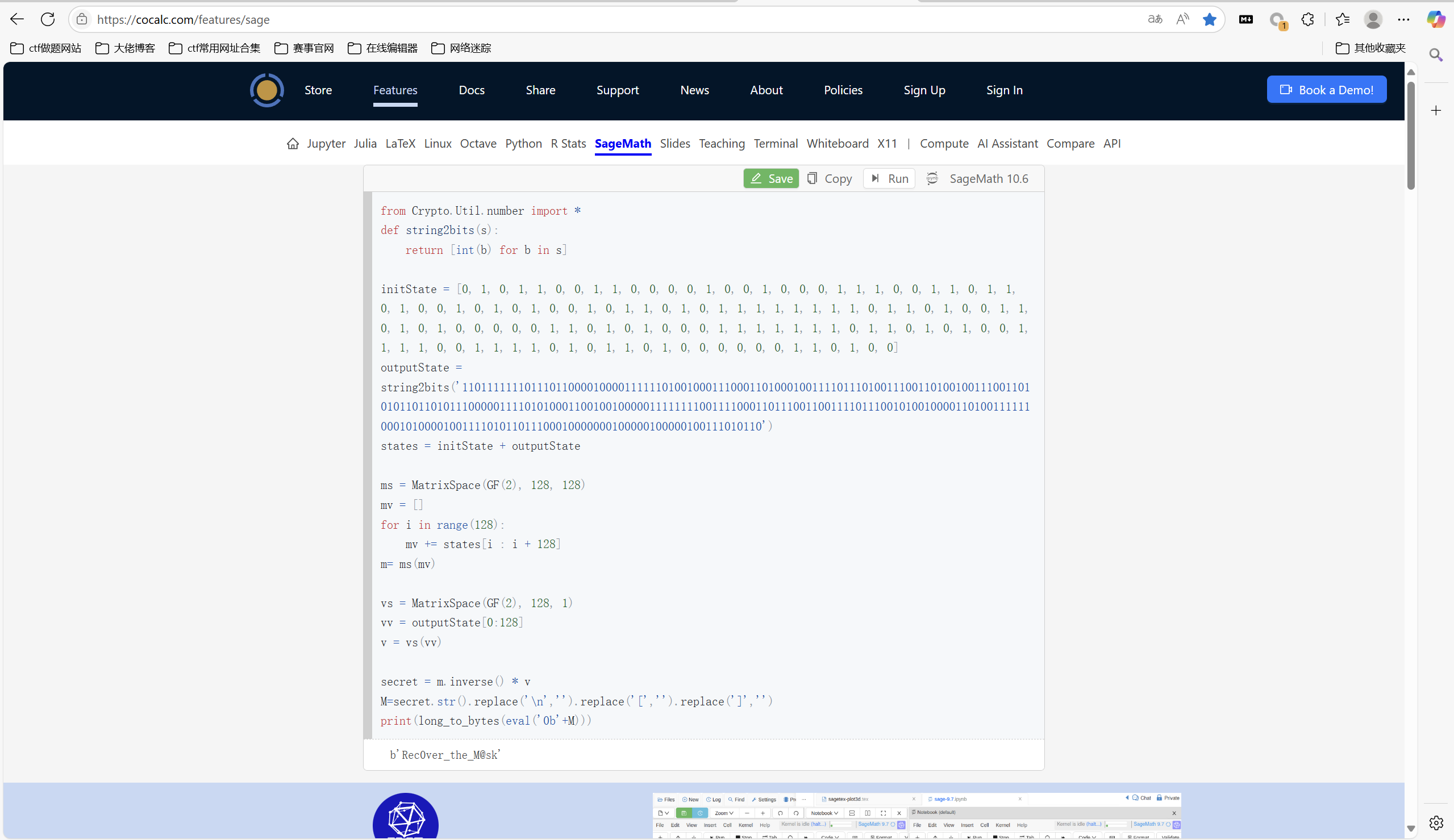
最后flag为
1 | 0xGame{Rec0ver_the_M@sk} |
ECC
下载附件
1 | from Crypto.Util.number import * |
exp:
1 | #part1:求私钥 |
运行得到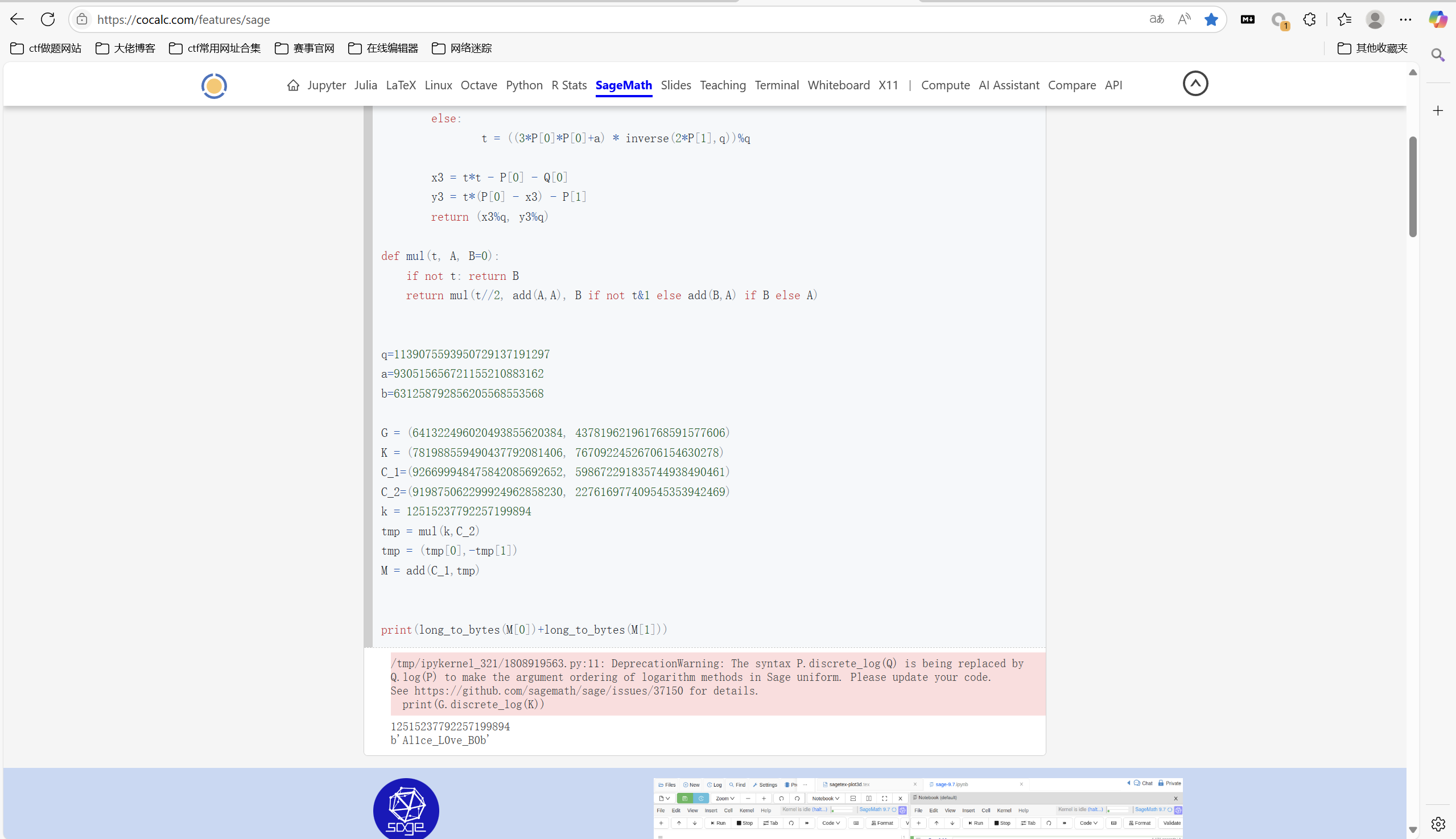
最后flag为
1 | 0xGame{Al1ce_L0ve_B0b} |
LLL-FirstBlood
下载附件
1 | from random import randrange |
exp:
1 | from Crypto.Util.number import * |
运行得到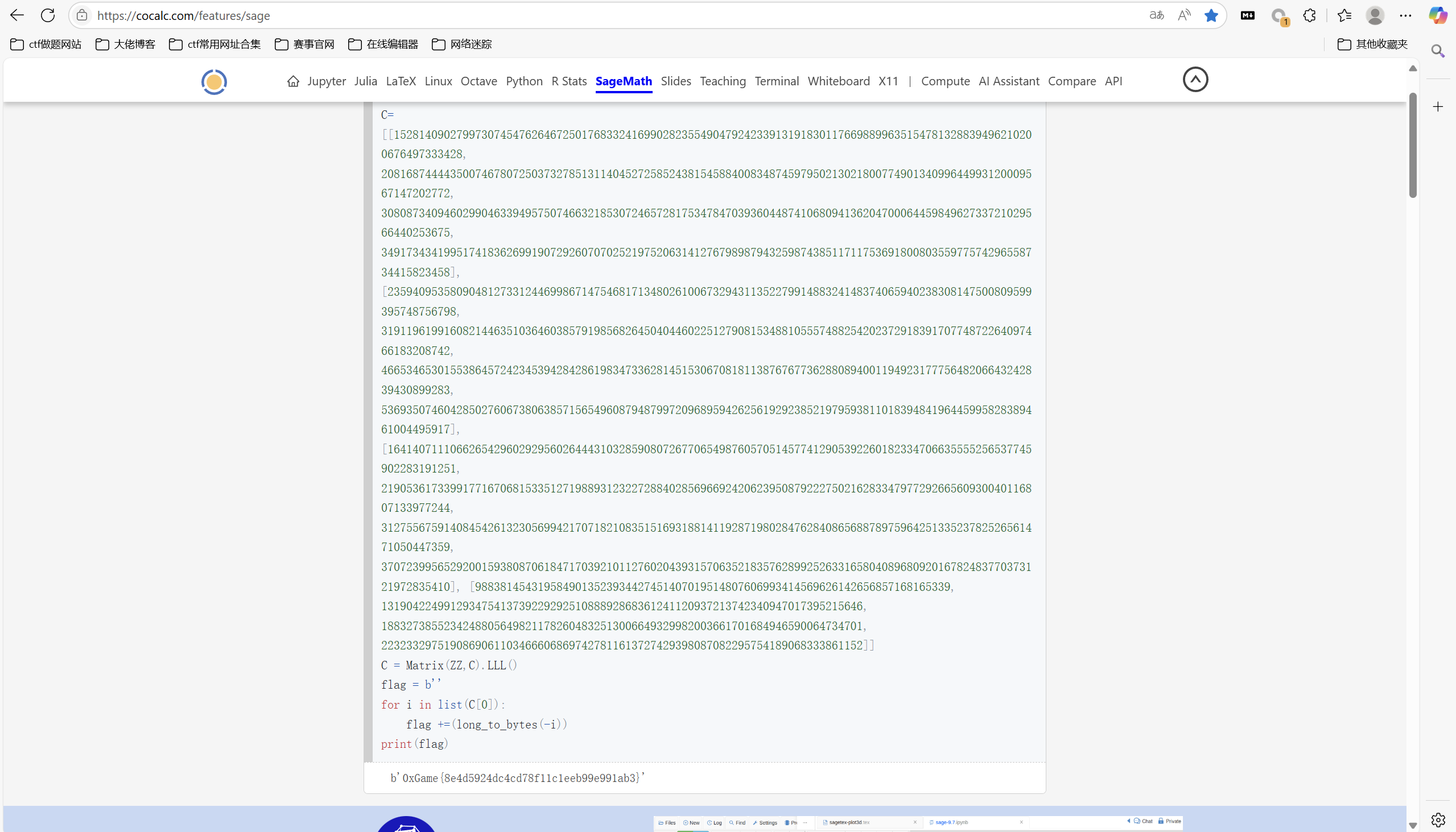
最后flag为
1 | 0xGame{8e4d5924dc4cd78f11c1eeb99e991ab3} |
LLL-SecondBlood
下载附件
1 | from Crypto.Util.number import * |
exp:
1 | from Crypto.Util.number import * |
运行得到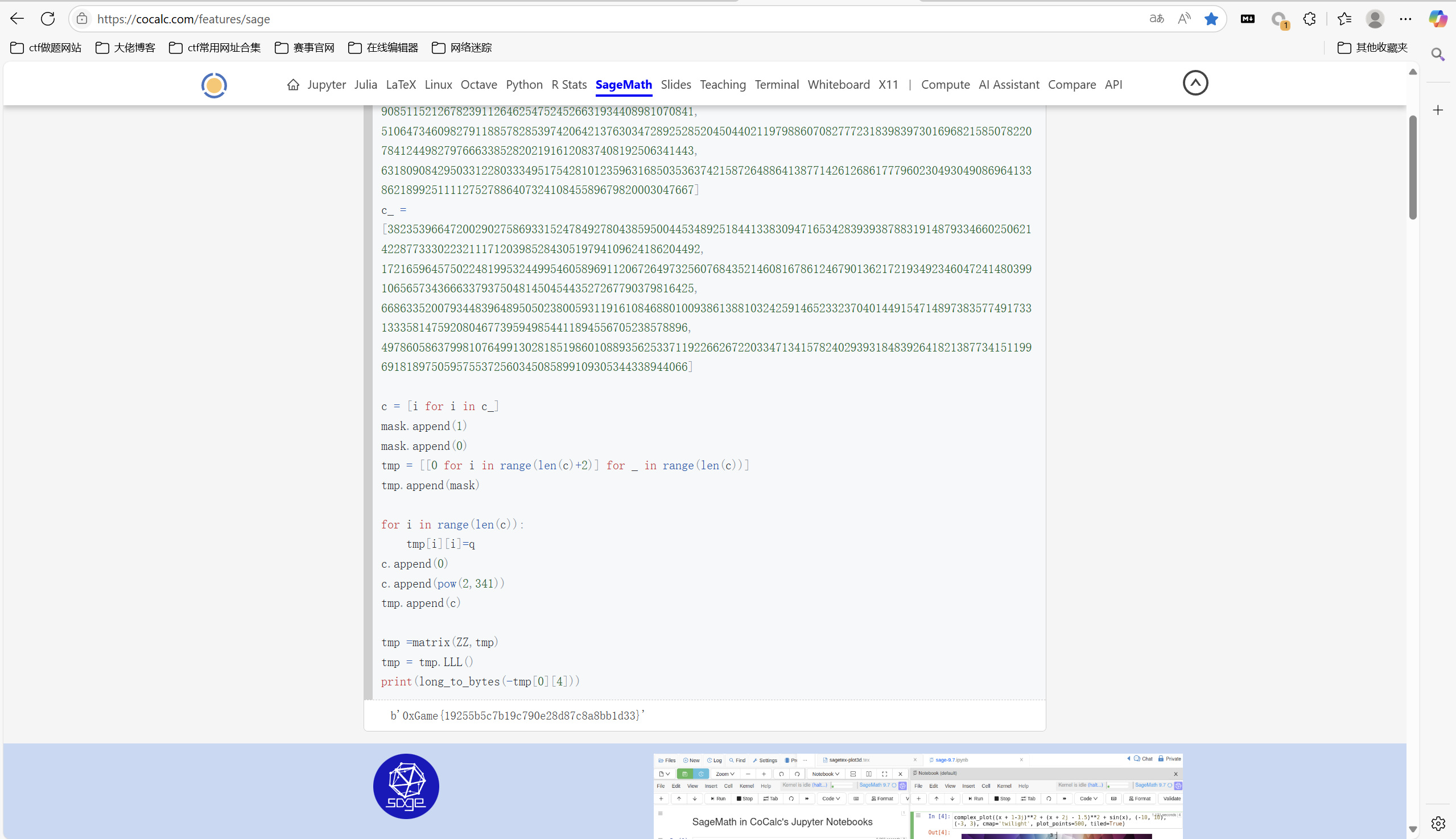
最后flag为
1 | 0xGame{19255b5c7b19c790e28d87c8a8bb1d33} |
Matrix
下载附件
1 | from Crypto.Util.number import getPrime |
exp:
1 | A=[[12143520799533590286, 1517884368, 12143520745929978443, 796545089340, 12143514553710344843, 28963398496032, 12143436449354407235, 158437186324560, 12143329129091084963, 144214939188320, 12143459416553205779, 11289521392968],[12143520799533124067, 1552775781, 12143520745442171123, 796372987410, 12143514596803995443, 28617862048776, 12143437786643111987, 155426784993480, 12143333265382547123, 140792203111560, 12143460985399172467, 10983300063372],[12143520799533026603, 1545759072, 12143520746151921286, 781222462020, 12143514741528175043, 27856210942560, 12143440210529480891, 150563969013744, 12143339455702534403, 135941365971840, 12143463119774571623, 10579745342712],[4857408319806885466, 2428704161425648657, 12143520747462241175, 758851601758, 12143514933292307603, 7286139389566980165, 9714738936567334300, 144947557513044, 12143346444338047691, 130561054163540, 4857352974113333366, 2428714303424782417],[12143520799533339320, 1476842796, 12143520749060275613, 733281428880, 12143515144091549812, 25896324662208, 12143446129977471347, 139126289668080, 12143353609086952433, 125093278125816, 12143467808884068695, 9705993135696],[3469577371288079926, 5204366058378782250, 12143520750775862343, 706665985740, 12143515359139397843, 24876891455539, 12143449149385190675, 5204499435641729607, 1734628523990131469, 119757210113970, 12143470097256549947, 9282407958928],[10986995009101166671, 1734788687033207505, 12143520752514668698, 680173911560, 12143515570582515443, 23883386182656, 12143452072344092516, 10408859957710764174, 8673790006740000925, 4047954924507284041, 12143472277719610437, 8879790035168],[12143520799534210329, 8095680534365818753, 12143520754224346525, 6071761054204856029, 12143515774342357443, 22931775530664, 12143454859049102627, 122586336122081, 12143373761302849103, 109840689548590, 8095634066844843878, 8500892291801],[2428704159899526175, 7286112481016467893, 12143520755876491019, 629765964828, 12143515968446948123, 9714838668887734012, 4857345013259425502, 117630592711632, 12143379764863568374, 105318302849760, 2428659620509049335, 7286120625945355053],[7286112479717322389, 7286112480971640825, 12143520757456628435, 606320684970, 12143516152115449139, 4857429497934652454, 4857347490735050126, 112978994964264, 12143385390297217523, 101086824360217, 7286069740980100293, 7286120294834973633],[7727695054246476847, 1202487728, 12143520758958480293, 584144077140, 12143516325240923843, 20377952745696, 12143462294760579275, 108622249048560, 12143390651947217363, 97133513961120, 12143479741445599772, 8831658996900830432],[12143520799535388887, 1161628182, 12143520760380594623, 563225247585, 12143516488091679443, 19626876325056, 12143464472820678035, 104545135017180, 12143395570399006523, 93441517429260, 12143481309754543787, 7218375794633]] |
运行得到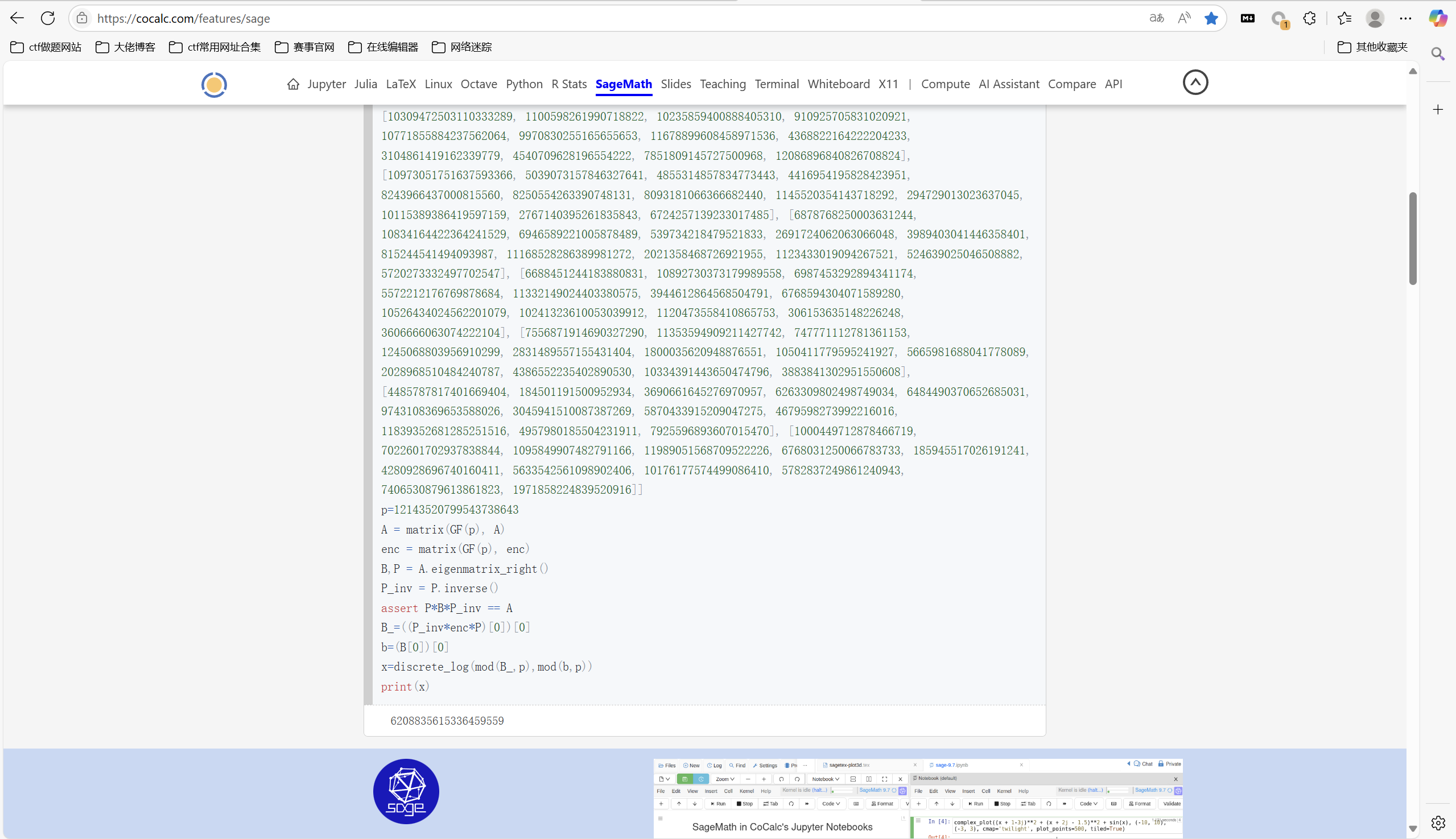
md5加密
1 | 06450201eb6171d40151563d967e59ea |
最后flag为
1 | 0xGame{06450201eb6171d40151563d967e59ea} |
Normal ECC
下载附件
1 | from Crypto.Util.number import getPrime |
exp:
1 | from hashlib import md5 |
Drange Leak
下载附件
1 | from random import * |
exp:
1 | import itertools |
LLL-ThirdBlood
exp1:
1 | #part1:拖取数据 |
exp2:
1 | from Crypto.Util.number import inverse |
exp3:
1 | from Crypto.Util.number import * |



