nc
题目描述:
1 | test your nc |
nc连接
1 | tac fla* >&2 |
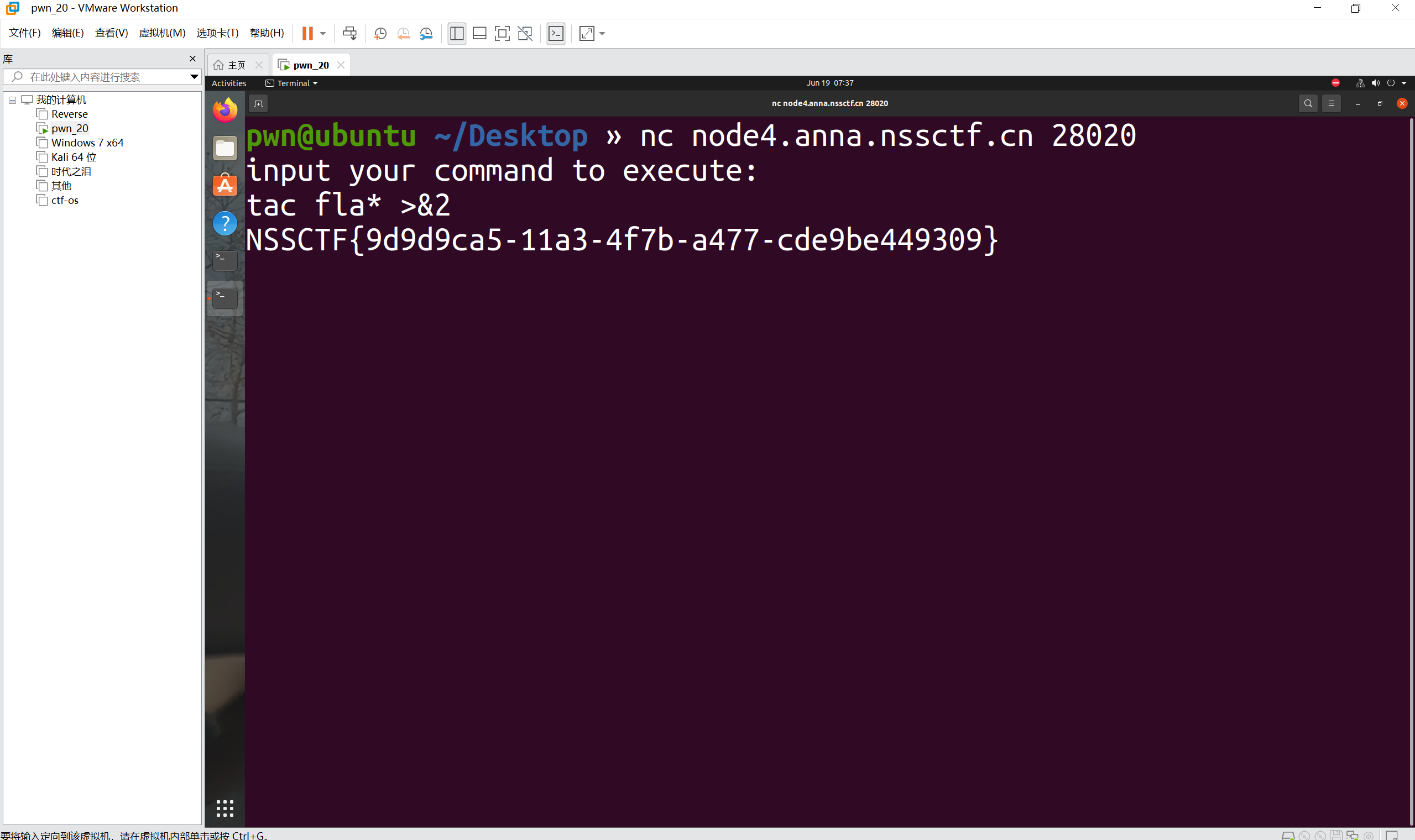
最后flag为
1 | NSSCTF{9d9d9ca5-11a3-4f7b-a477-cde9be449309} |
rdi
题目描述:
1 | normal rdi |
查看一下保护机制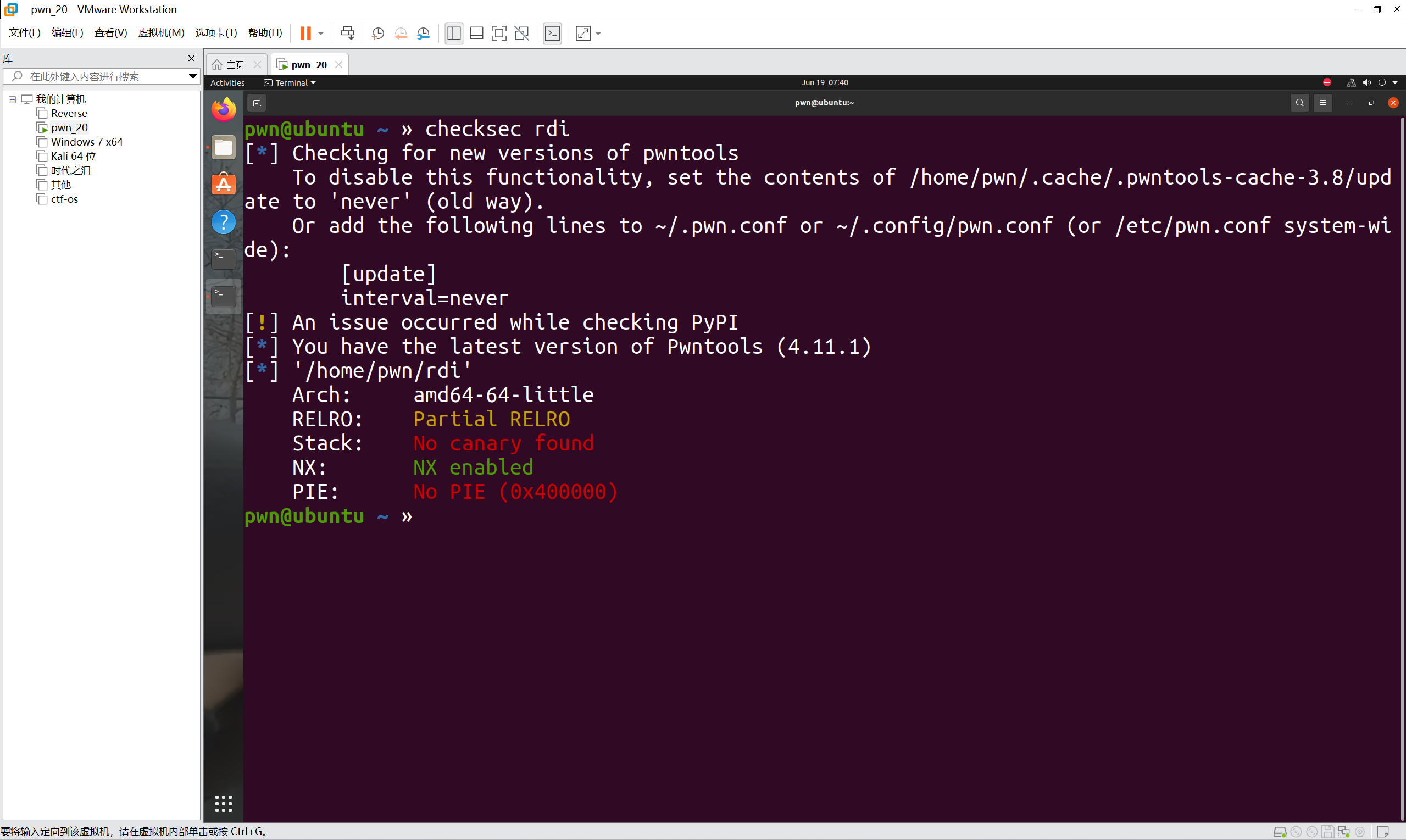
只打开了NX
ida载入,在gift函数存在system函数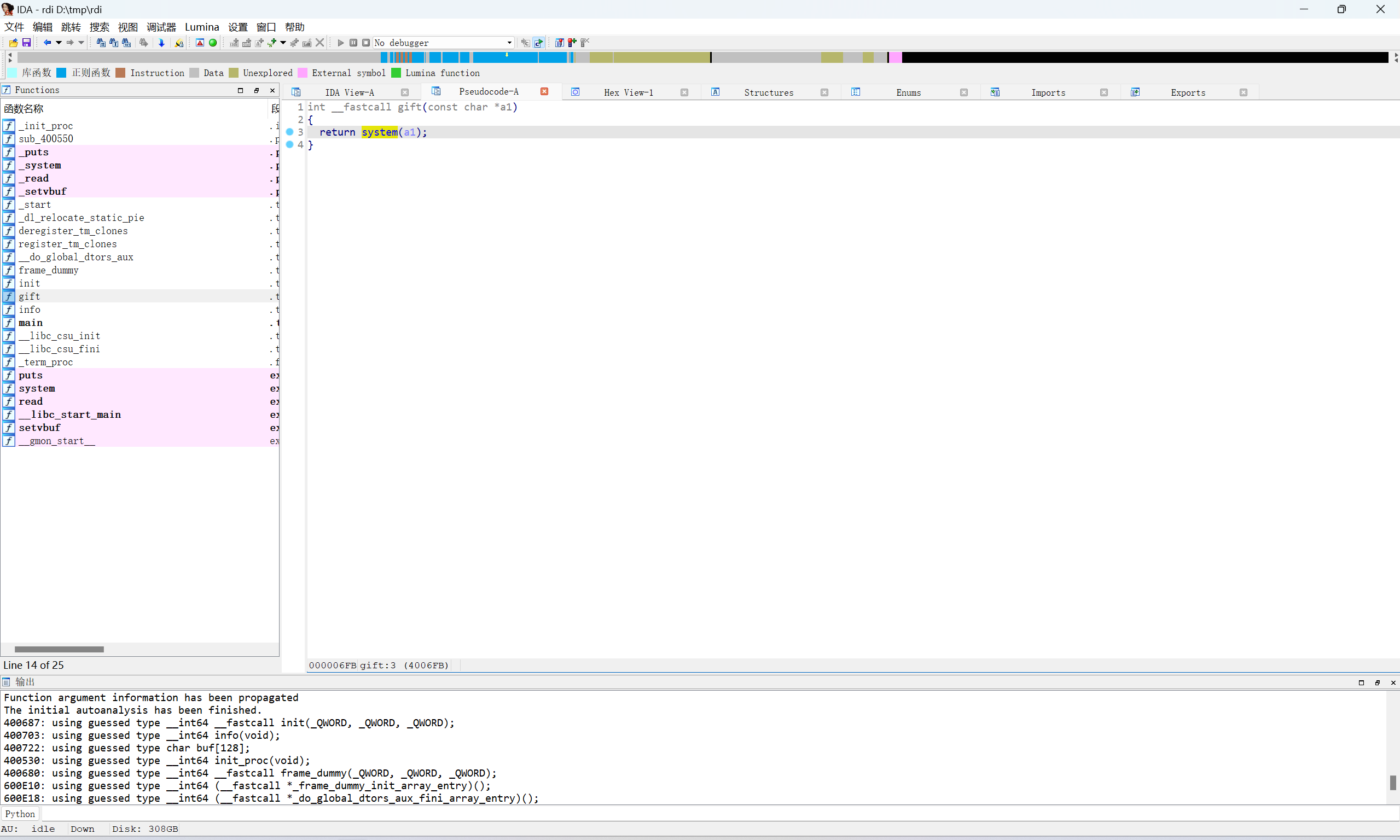
main函数存在栈溢出
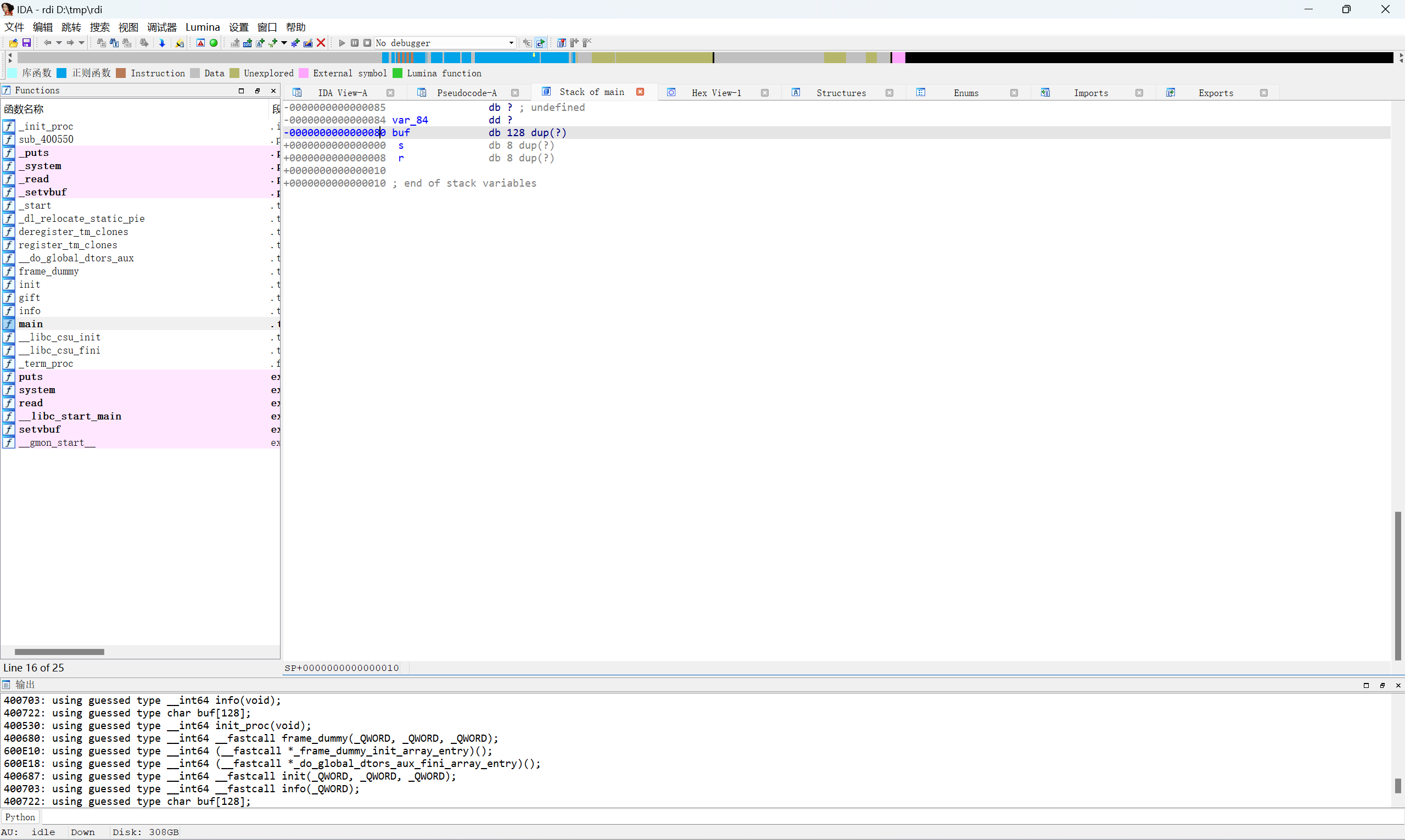
查看sys地址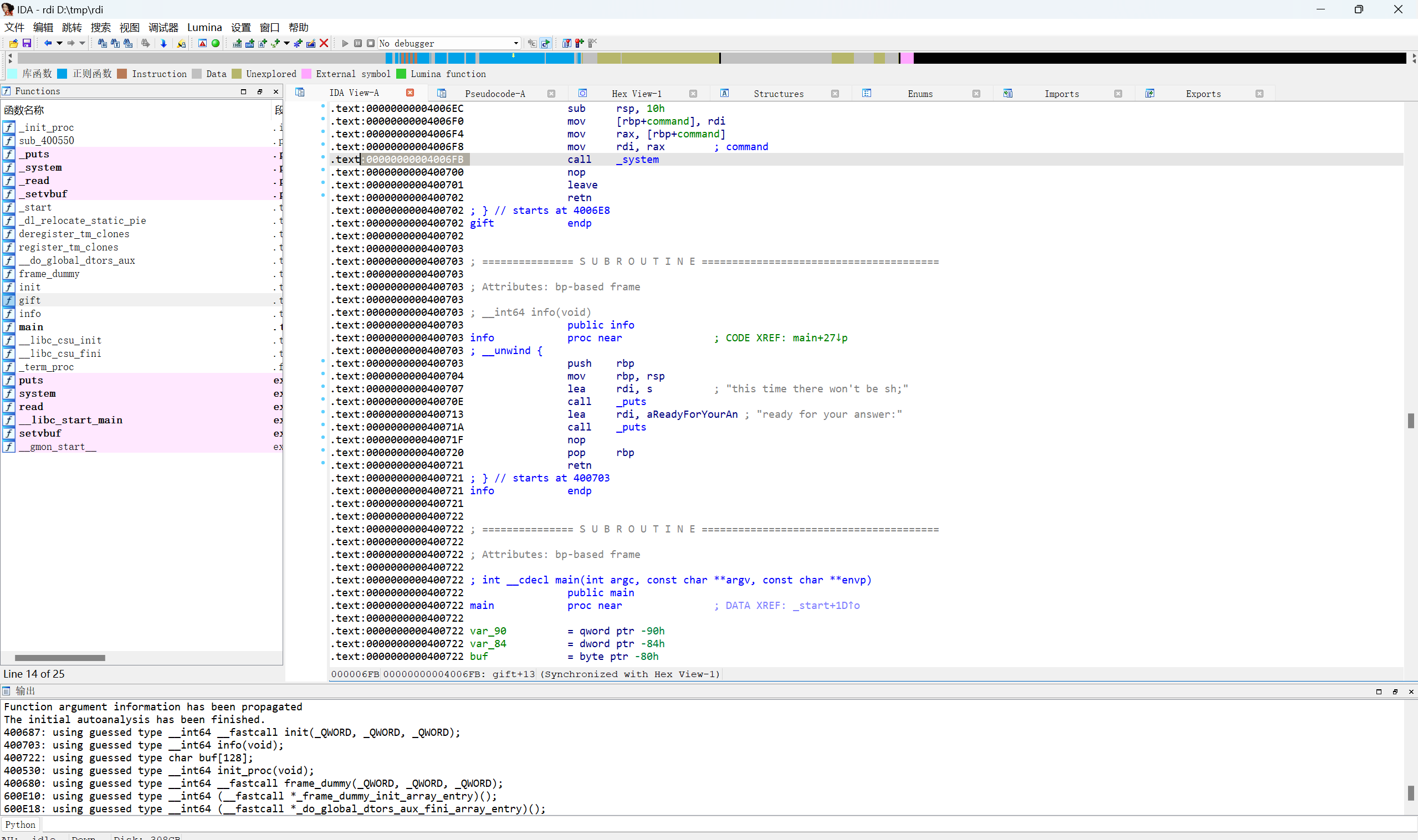
ROPgadget搜索rdi地址
ROPgadget搜索sh地址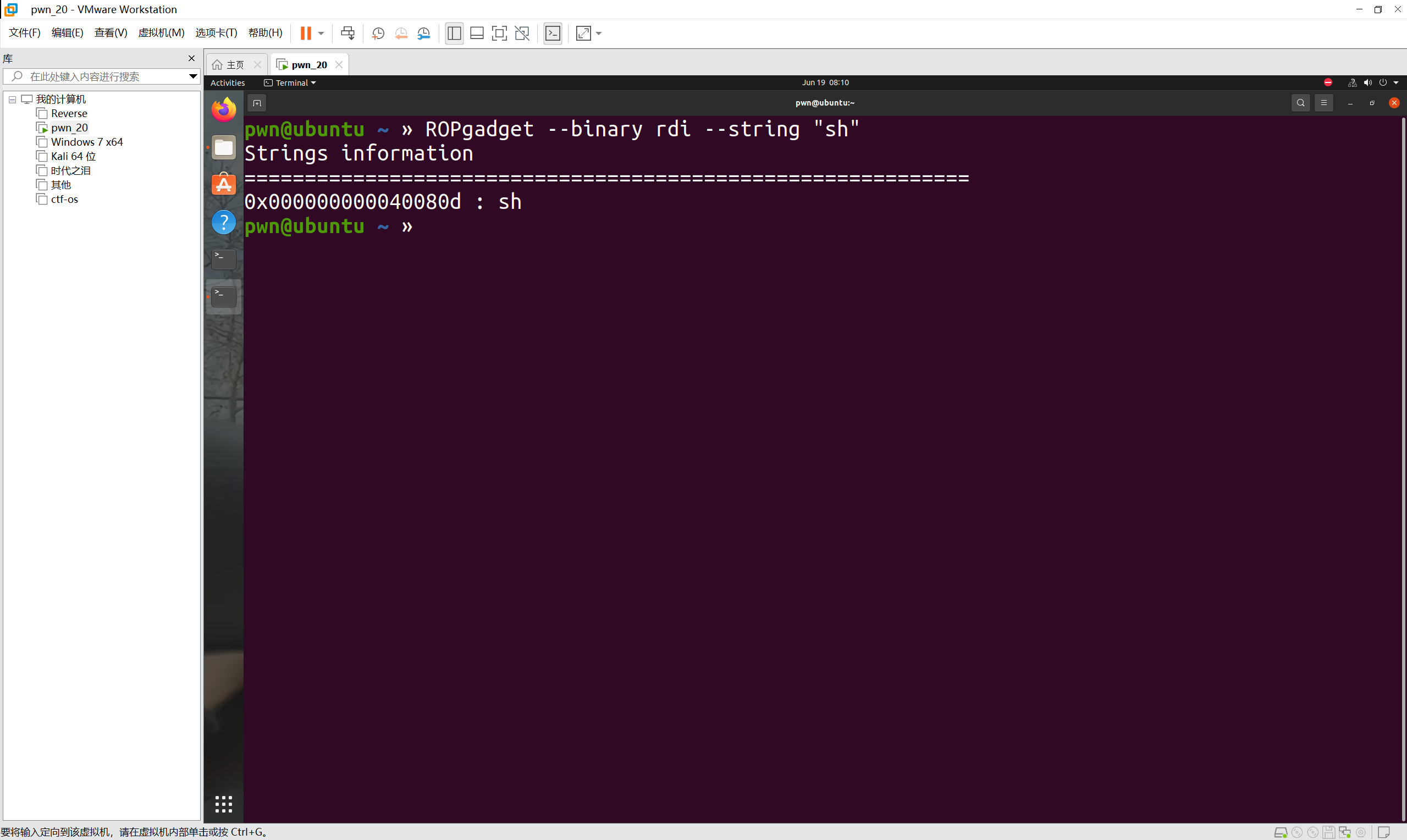
exp:
1 | from pwn import * |
运行得到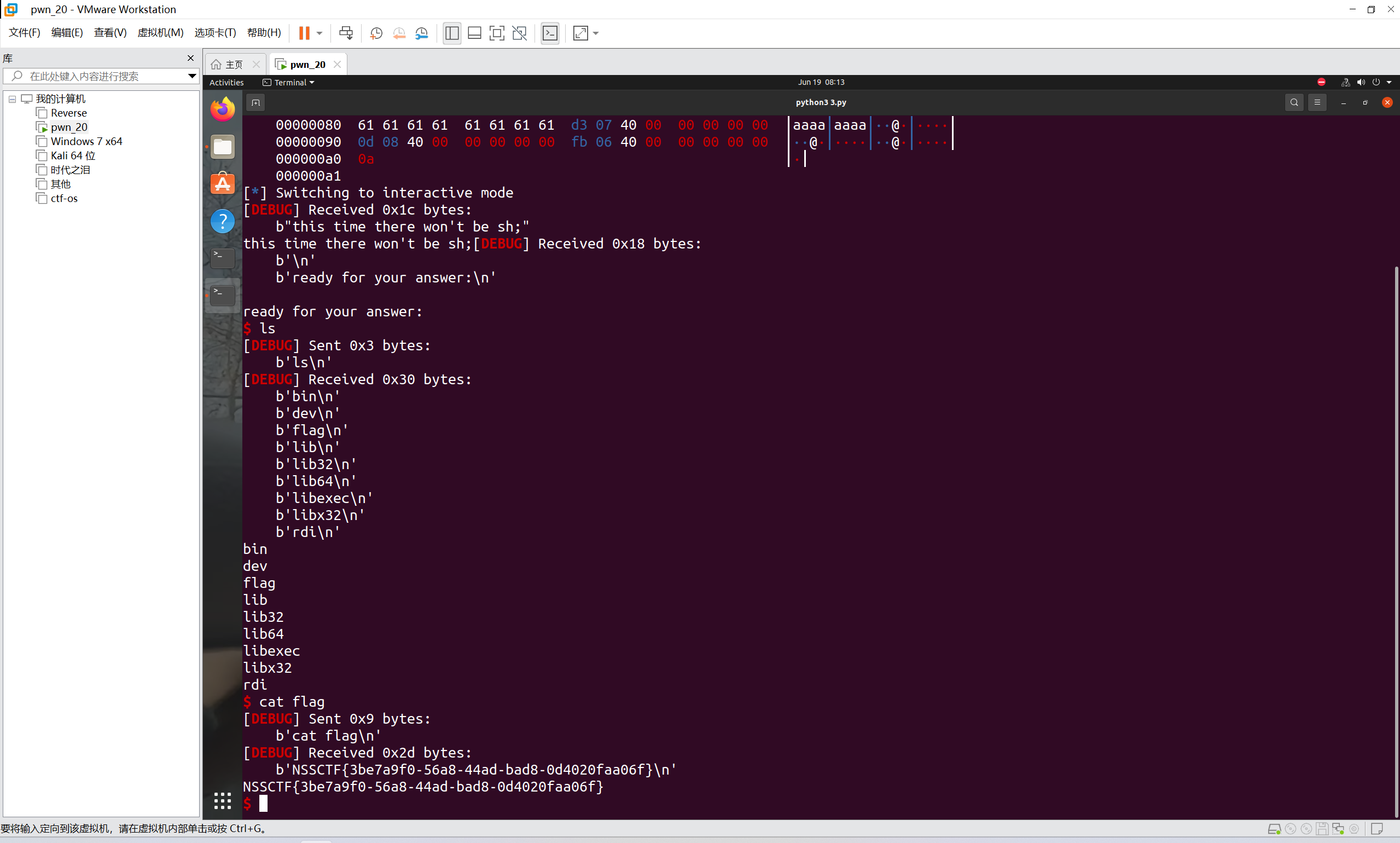
最后flag为
1 | NSSCTF{3be7a9f0-56a8-44ad-bad8-0d4020faa06f} |
2str
题目描述:
1 | 如何优雅的绕过 |
ida查看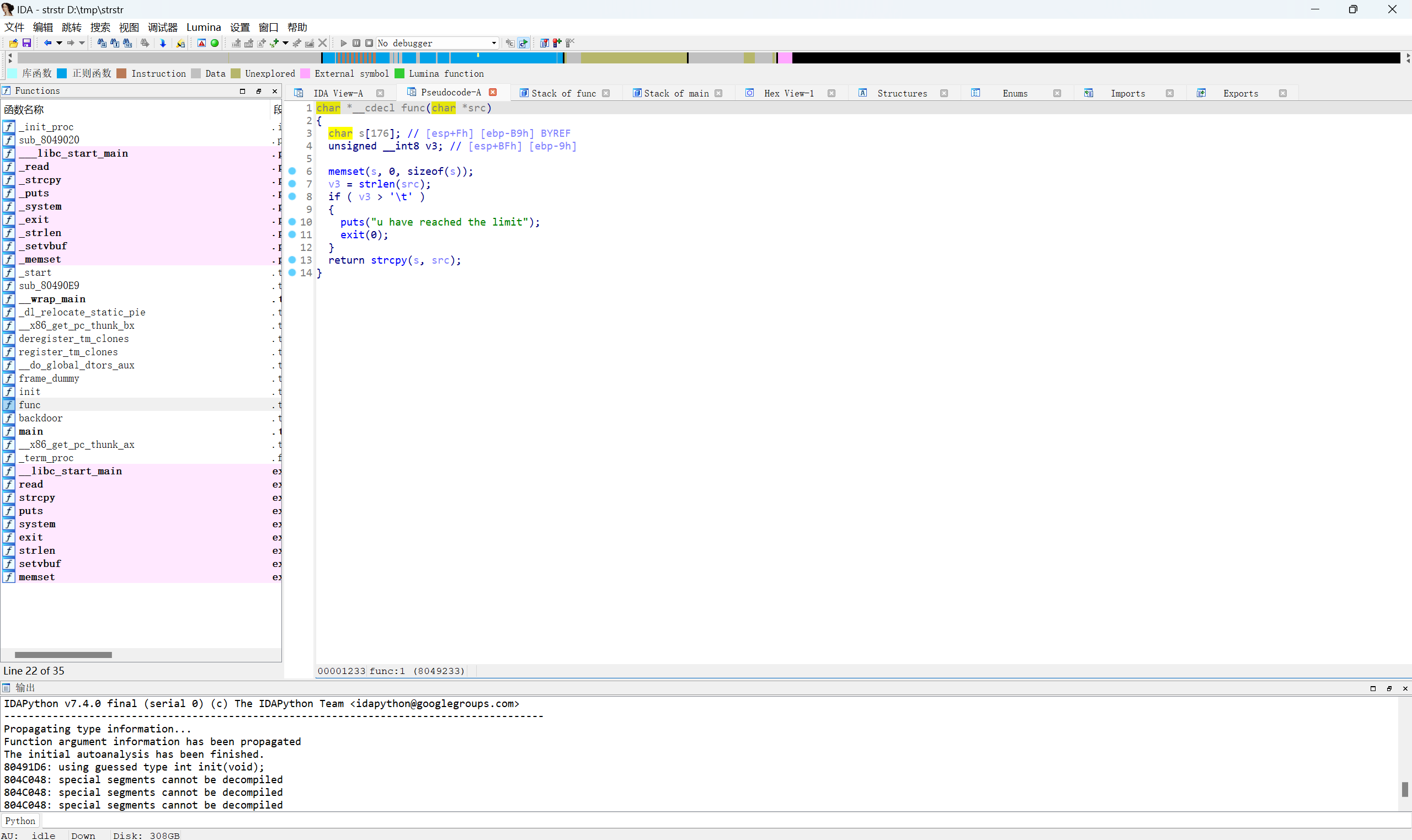
整数溢出
unsigned int8 的大小是 0 ~ 255,payload构造长度超过255
后门地址
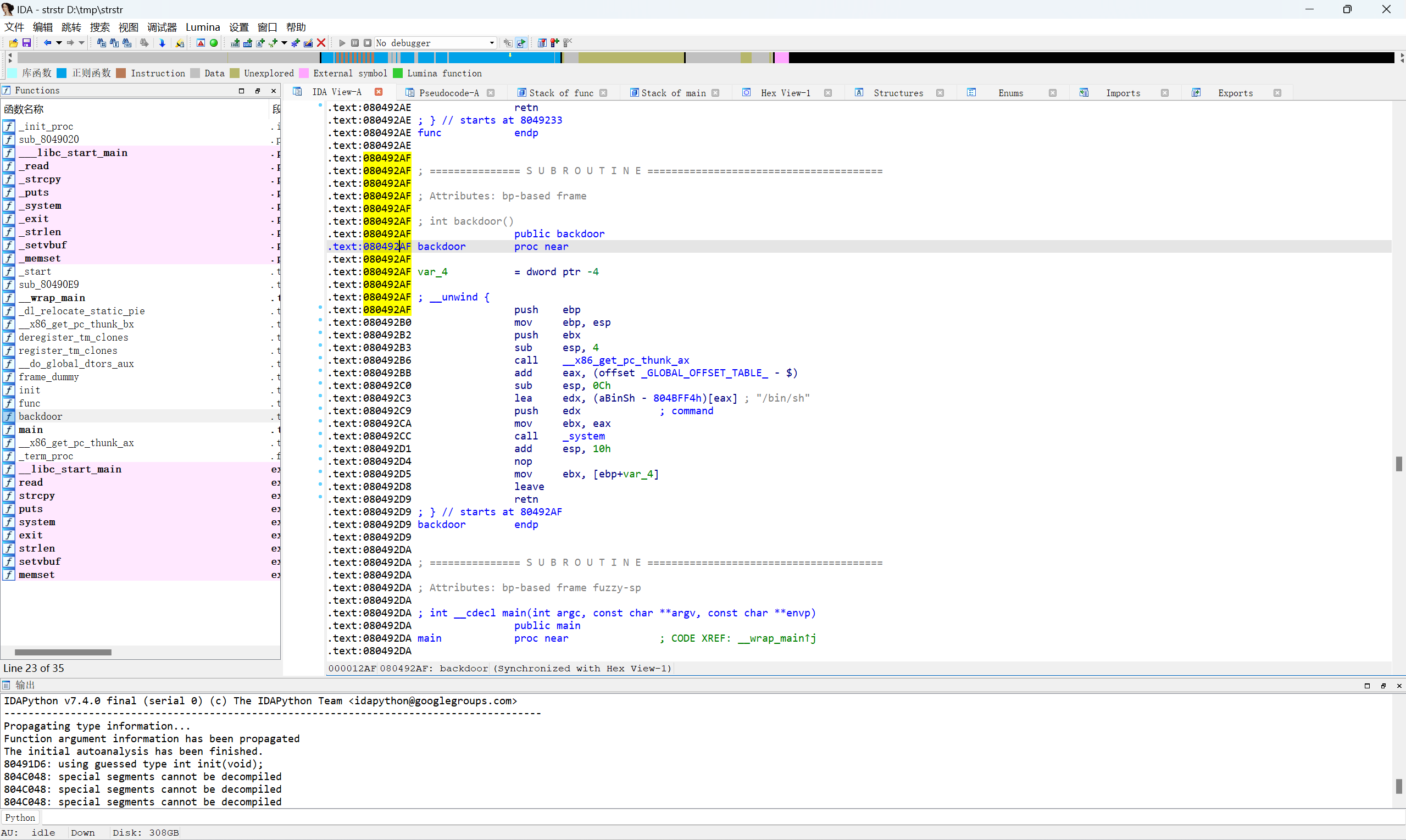
exp:
1 | from pwn import * |
运行得到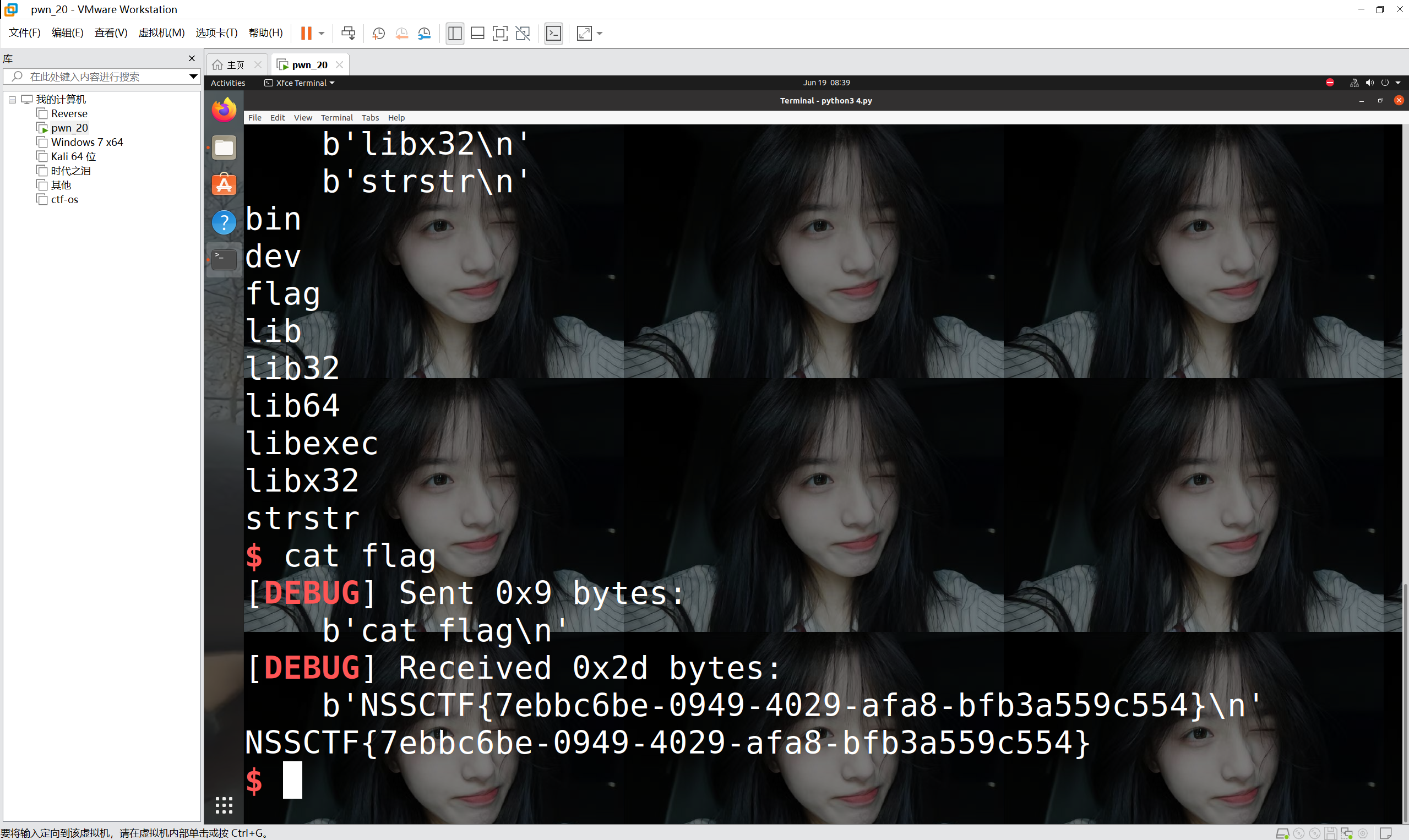
最后flag为
1 | NSSCTF{7ebbc6be-0949-4029-afa8-bfb3a559c554} |
stackmat
题目描述:
1 | 给后门稍微加个锁 |
查看保护机制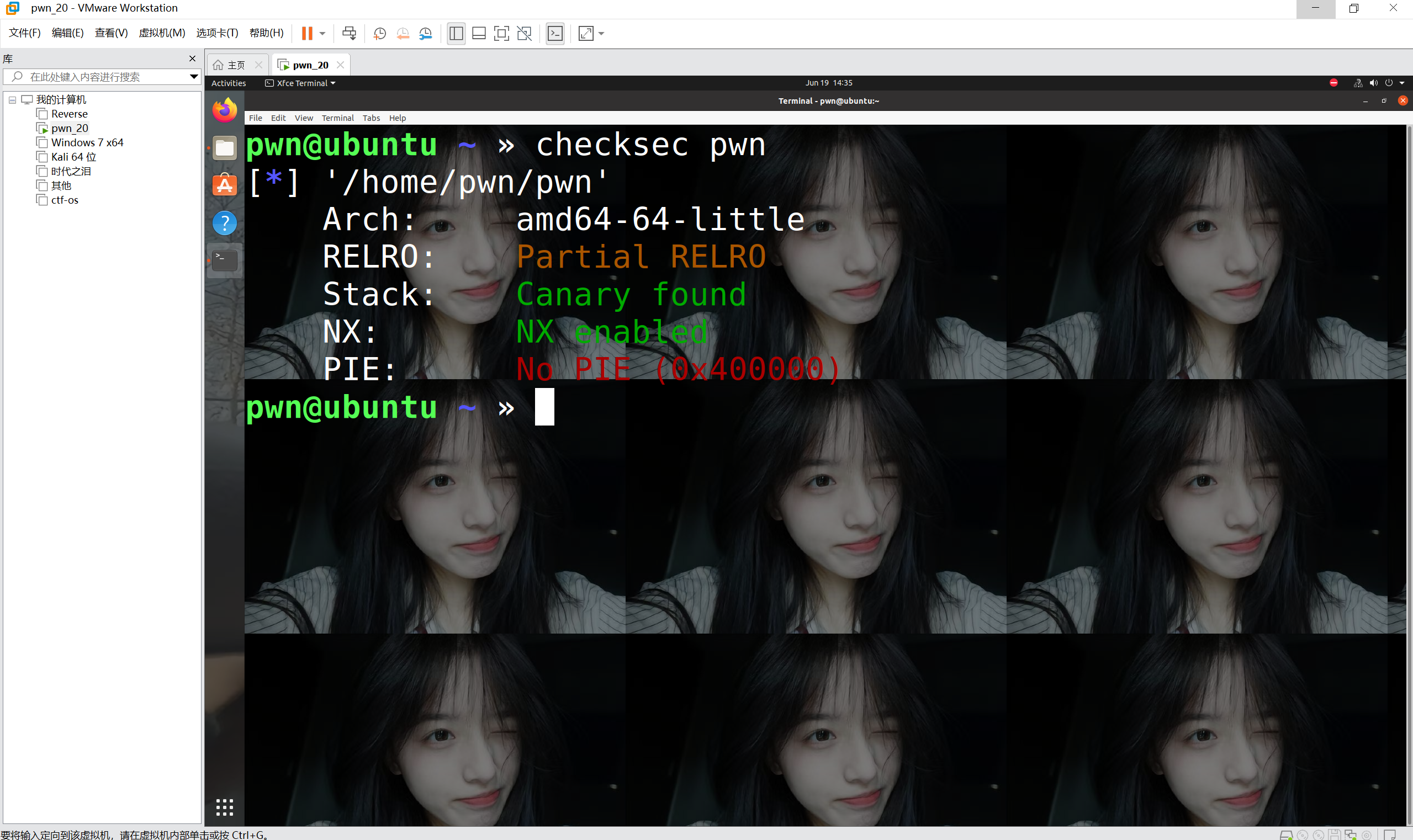
打开了canary和NX
ida查看
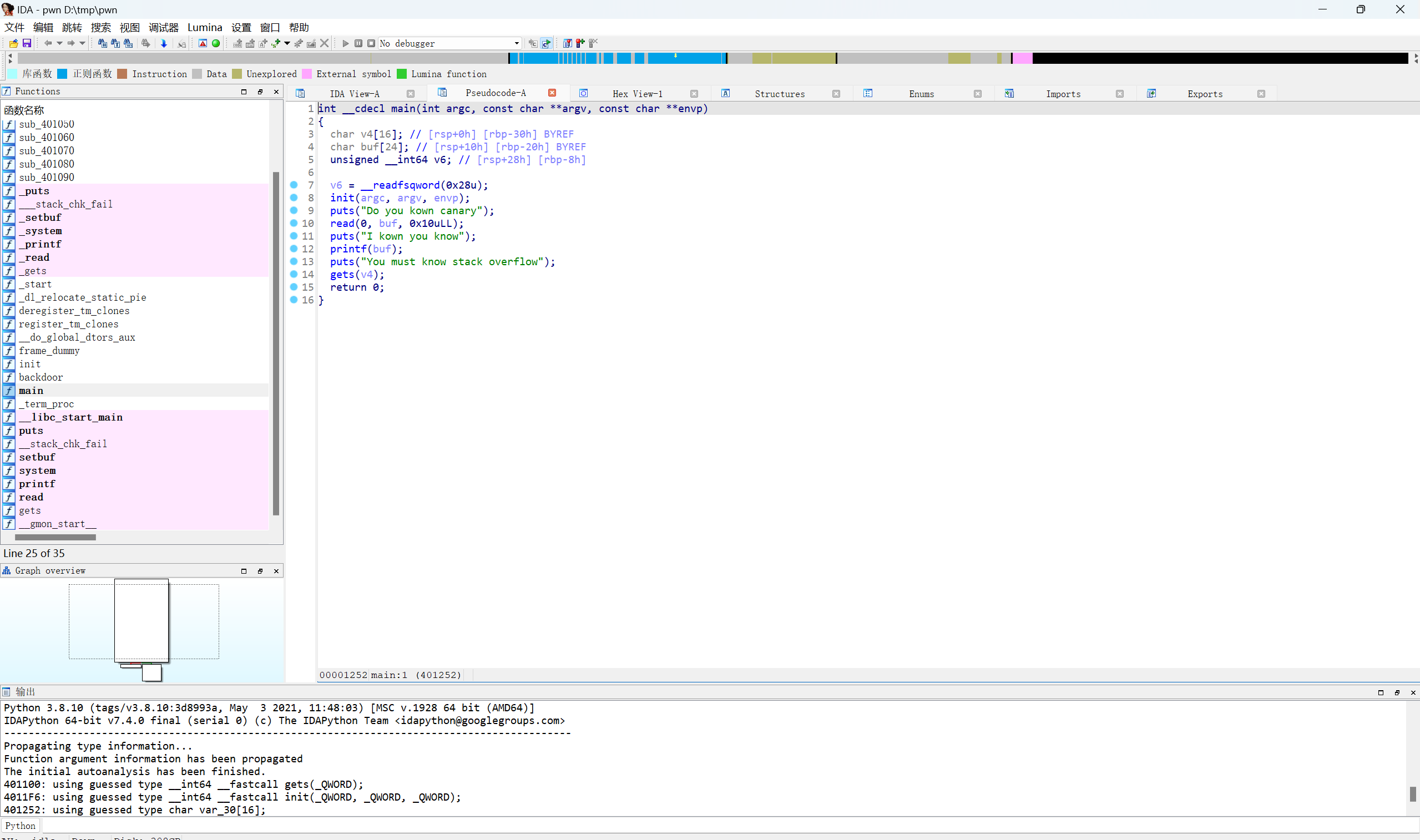
格式化字符串泄露Canary
exp:
1 | from pwn import * |
运行得到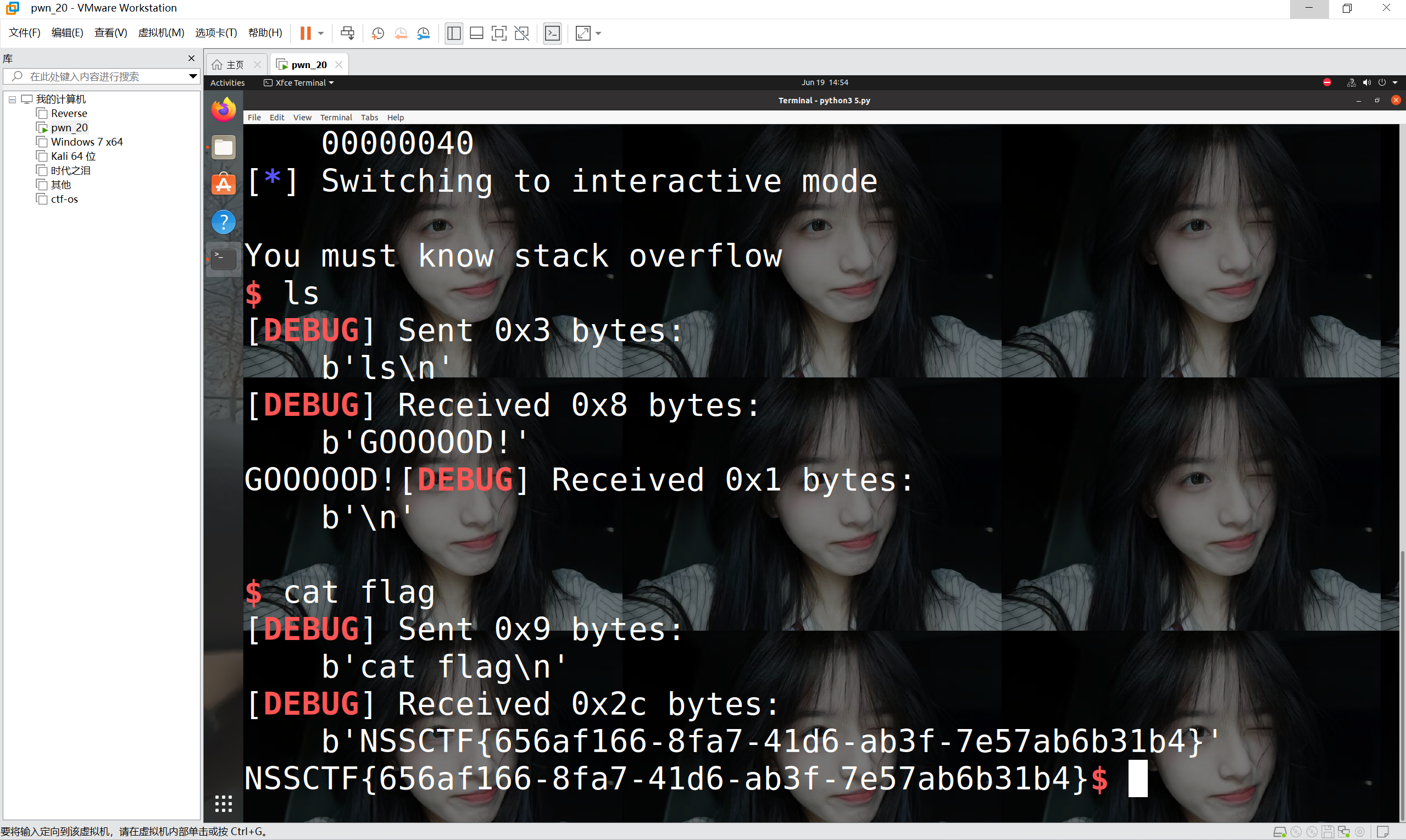
最后flag为
1 | NSSCTF{656af166-8fa7-41d6-ab3f-7e57ab6b31b4} |
Fi3h
题目描述:
1 | 新开了一家鱼店,老板开业大酬宾 |
查看保护机制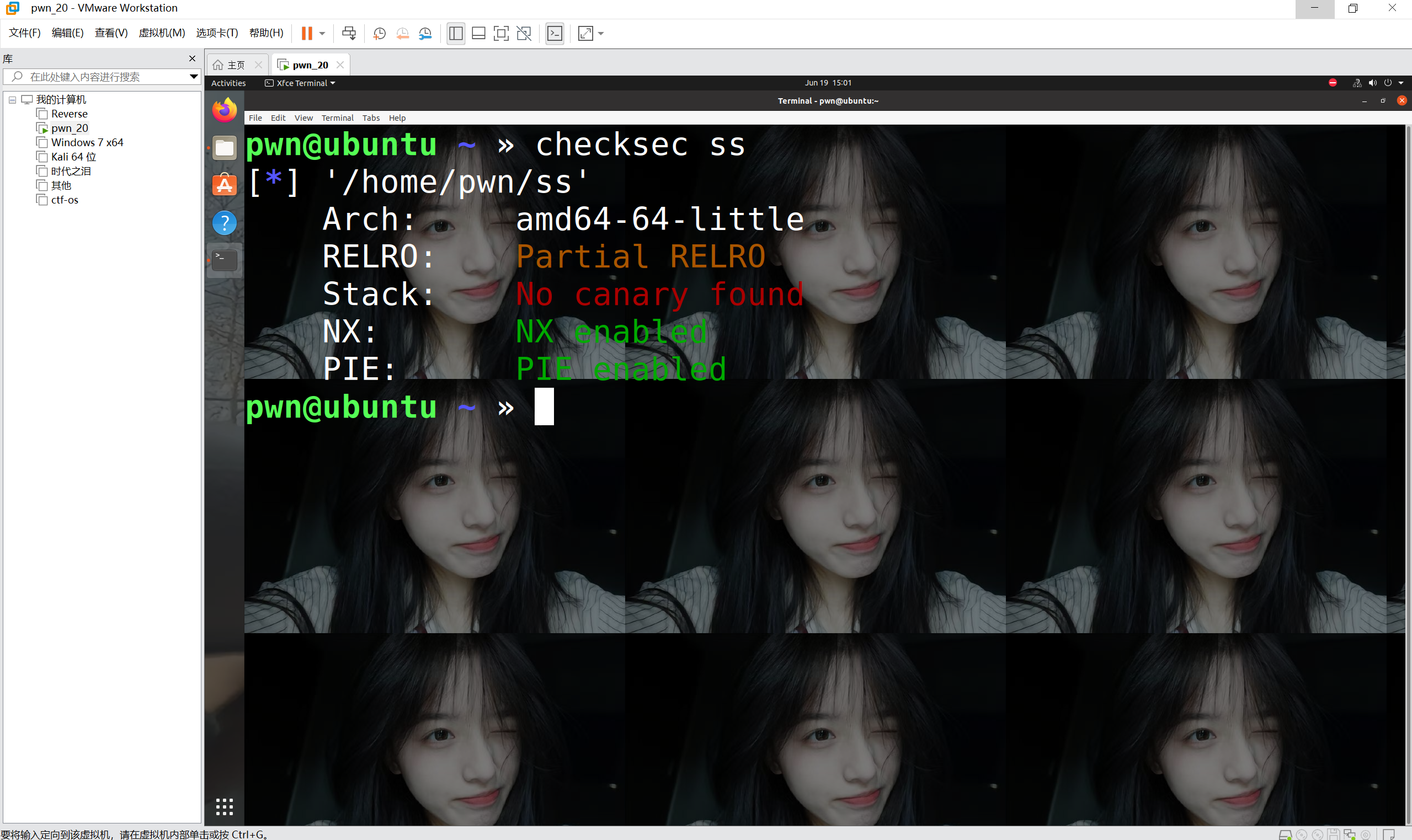
打开了NX和PIE地址随机化
ida查看main函数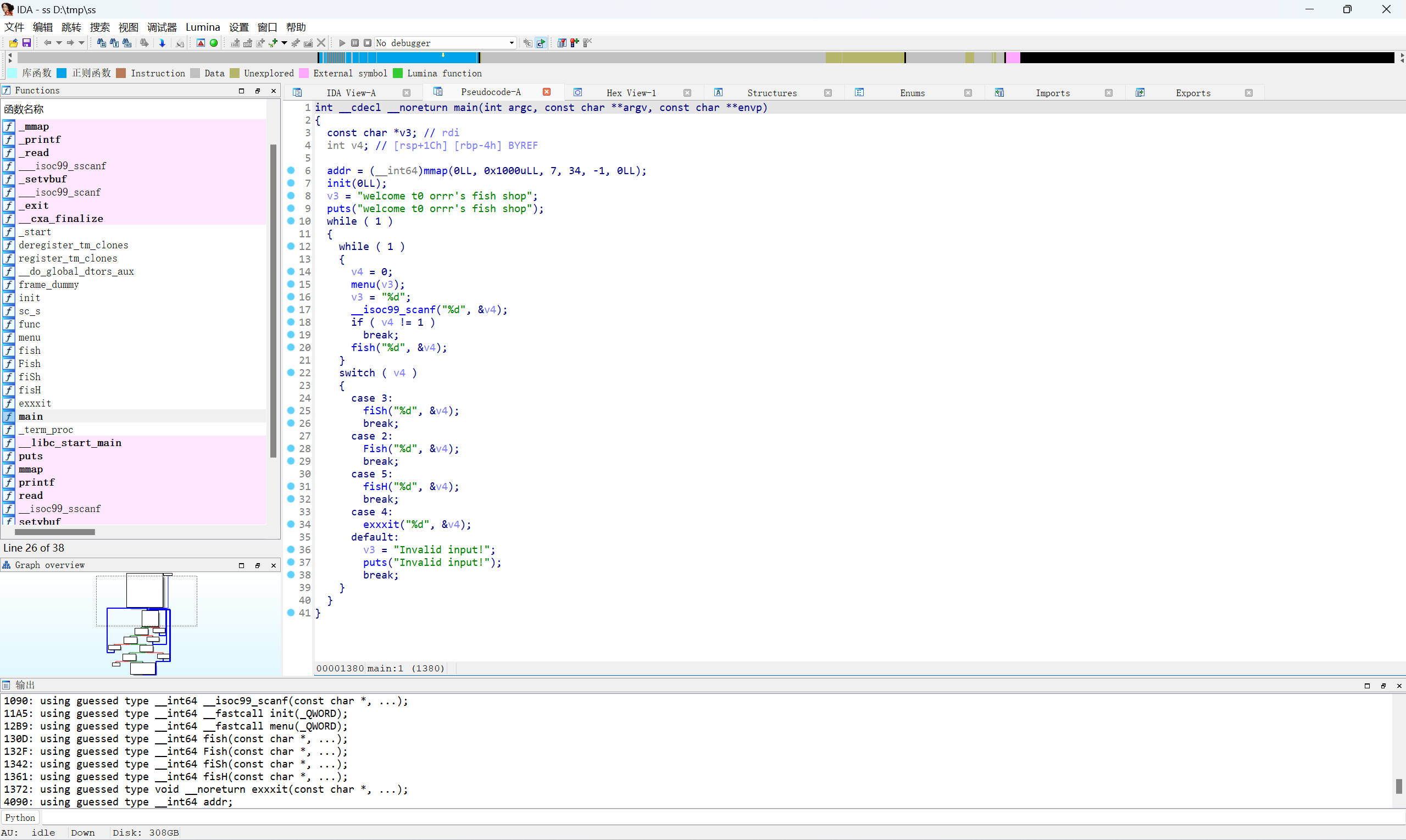
orw pwn
计算偏移为0x80,溢出返回到bss段,写入orw,读取flag
exp:
1 | from pwn import * |
运行得到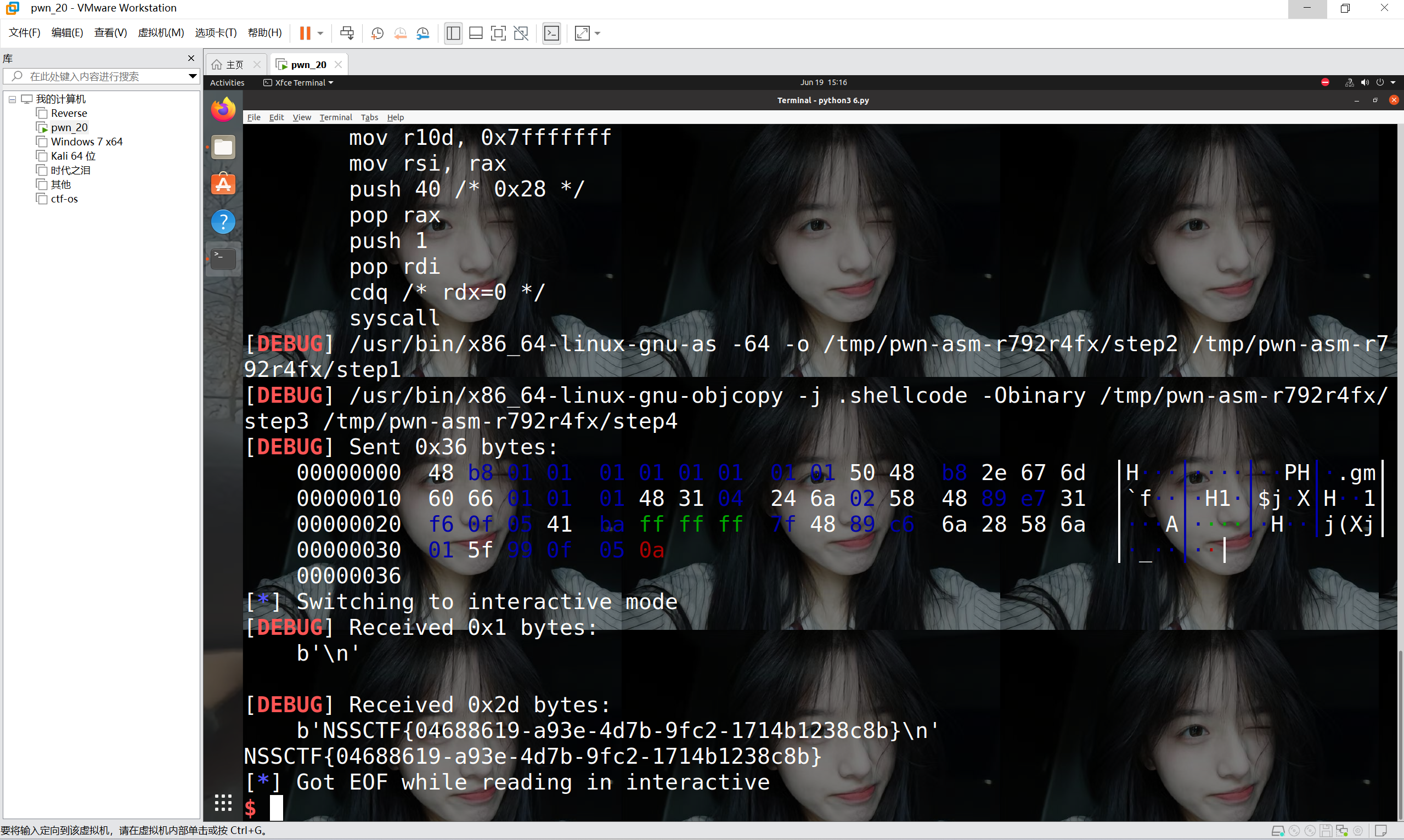
最后flag为
1 | NSSCTF{04688619-a93e-4d7b-9fc2-1714b1238c8b} |
What am I thinking?
题目描述:
1 | 运行一下我的脑子看看 |
nc连接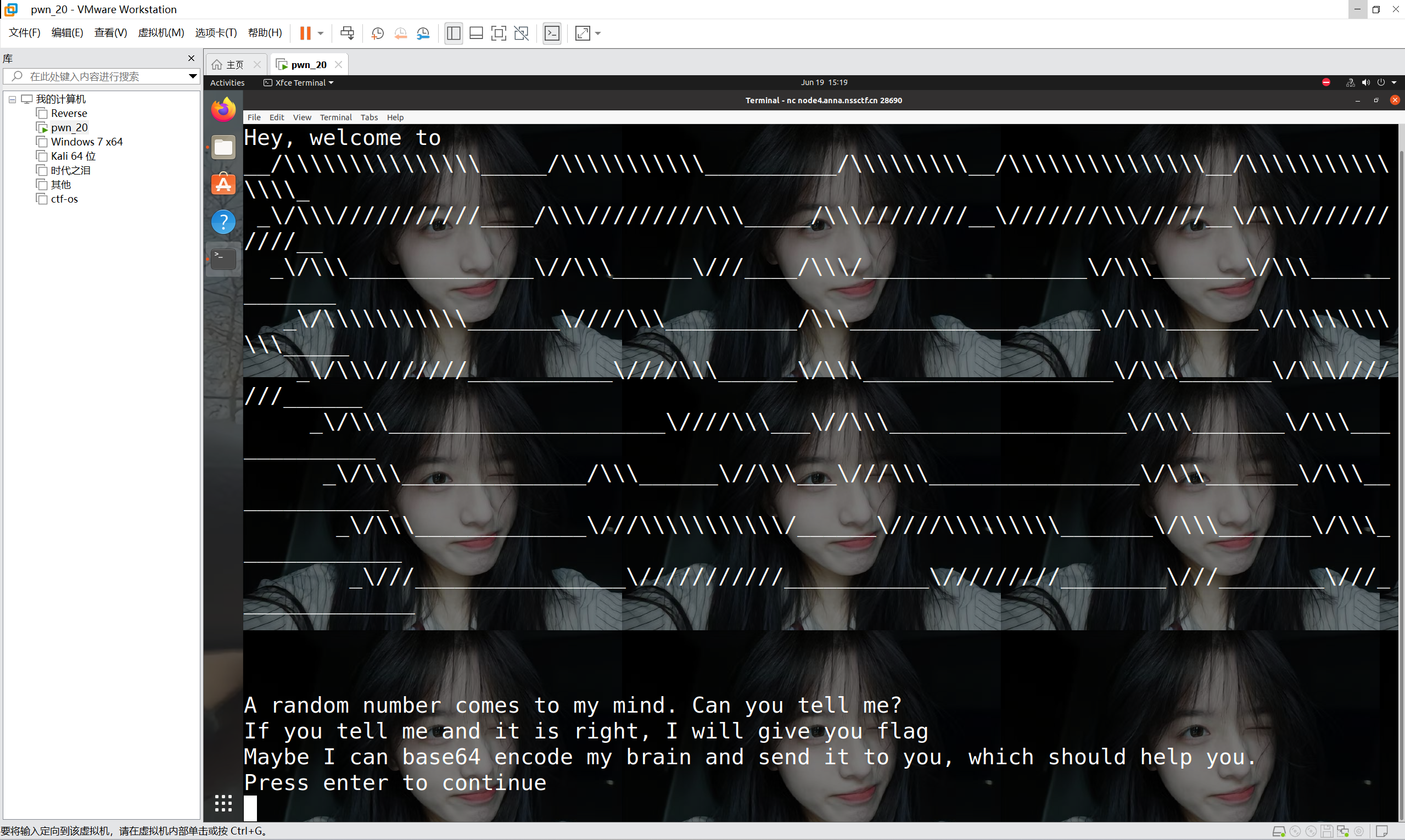
接收程序发来的 brain 代码,之后进行base64解密运行得到随机数
exp:
1 | from pwn import * |
运行得到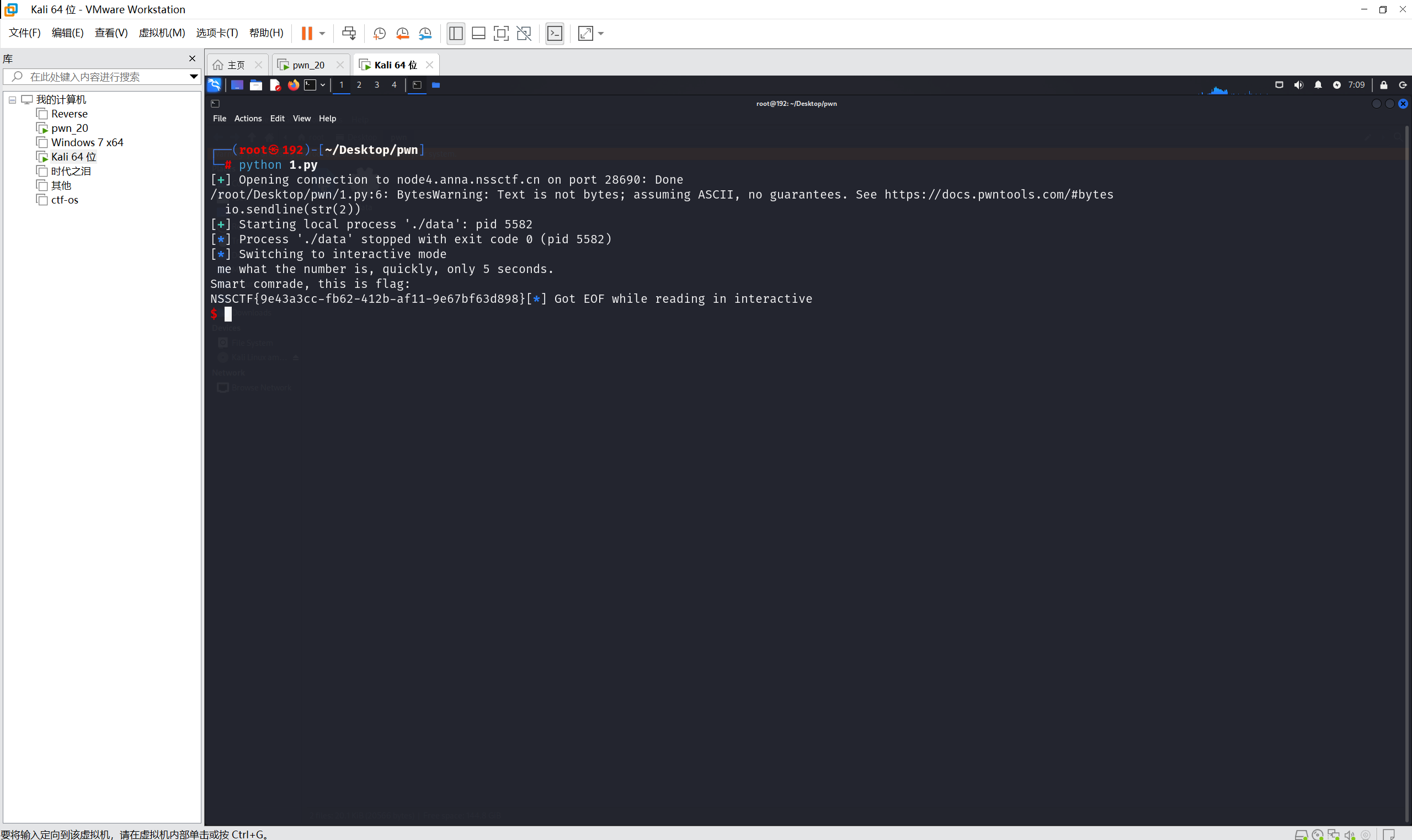
最后flag为
1 | NSSCTF{9e43a3cc-fb62-412b-af11-9e67bf63d898} |
YS,START!
题目描述:
1 | 我 要 玩 □ □! |
查看保护机制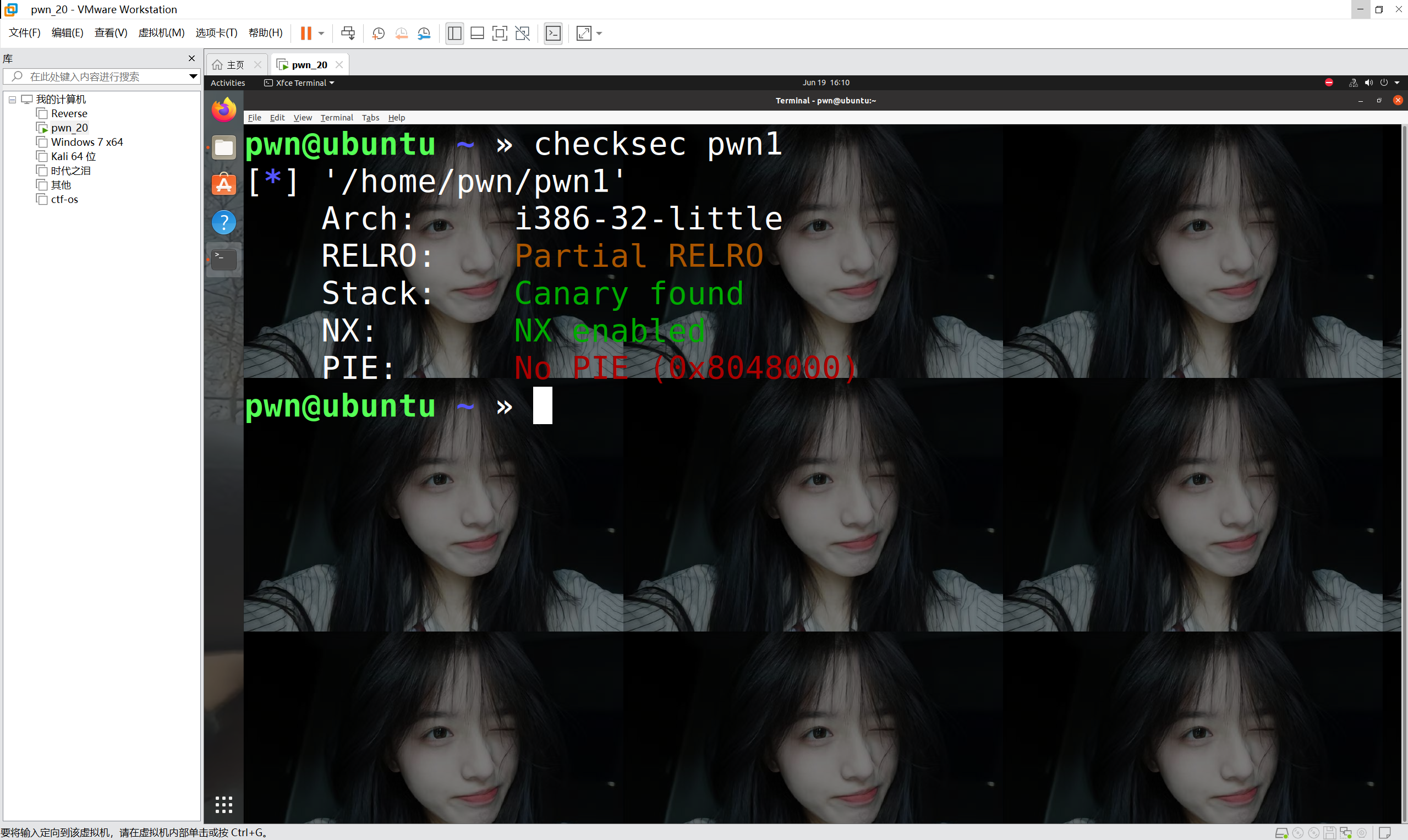
格式化字符串
exp:
1 | from pwn import * |
运行得到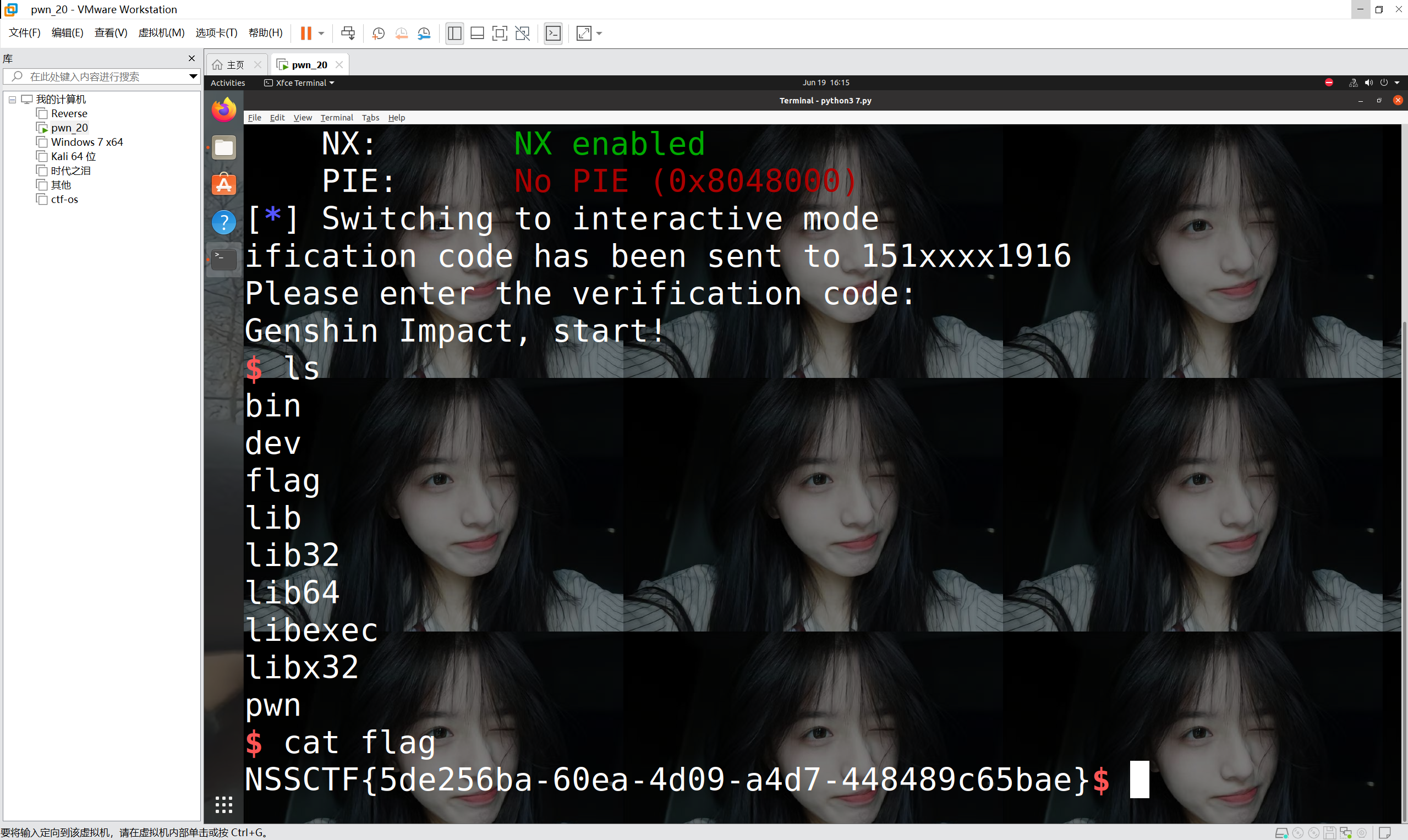
最后flag为
1 | NSSCTF{5de256ba-60ea-4d09-a4d7-448489c65bae} |



