signin
脱壳,IDA64载入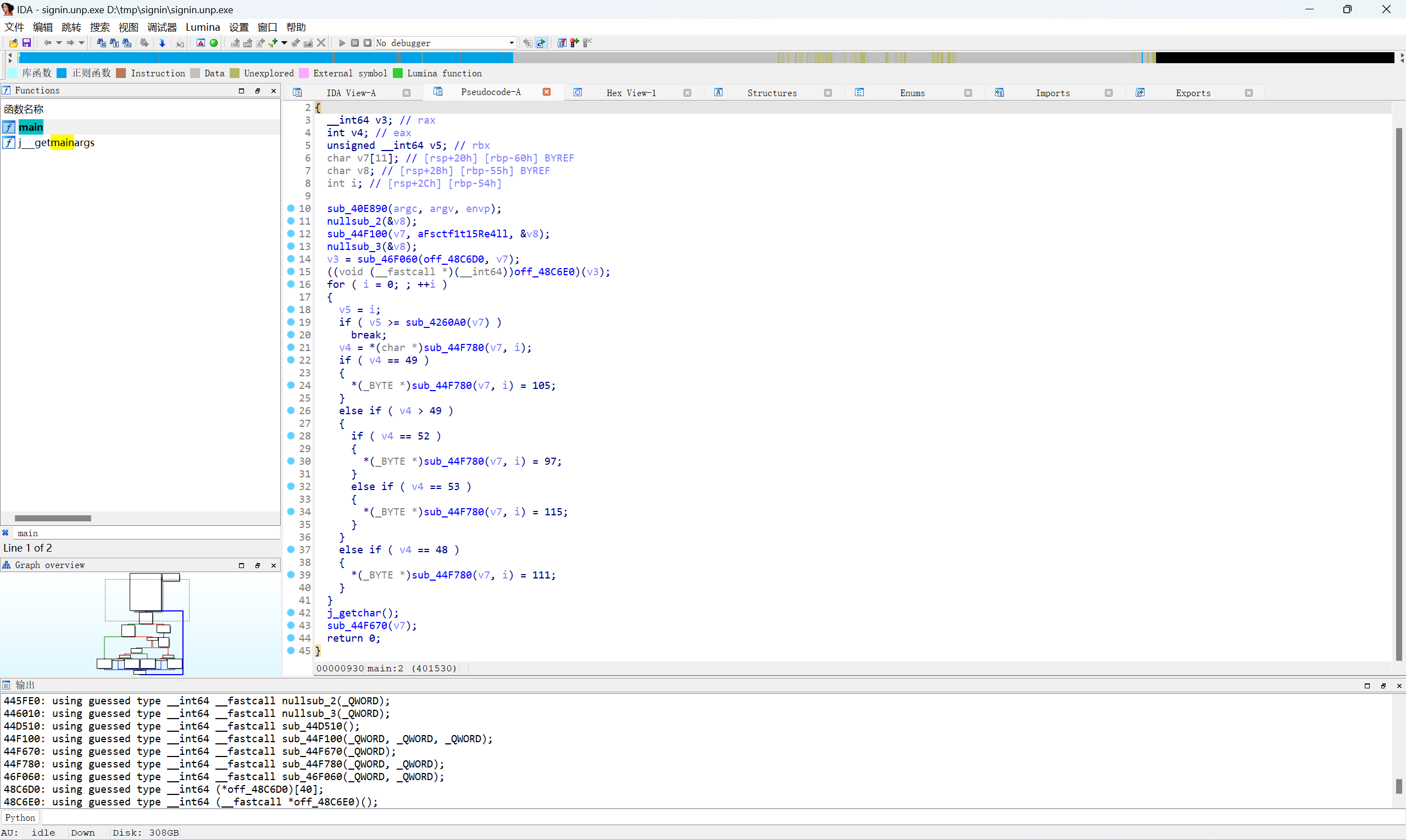
简单替换,查看字符串找到密文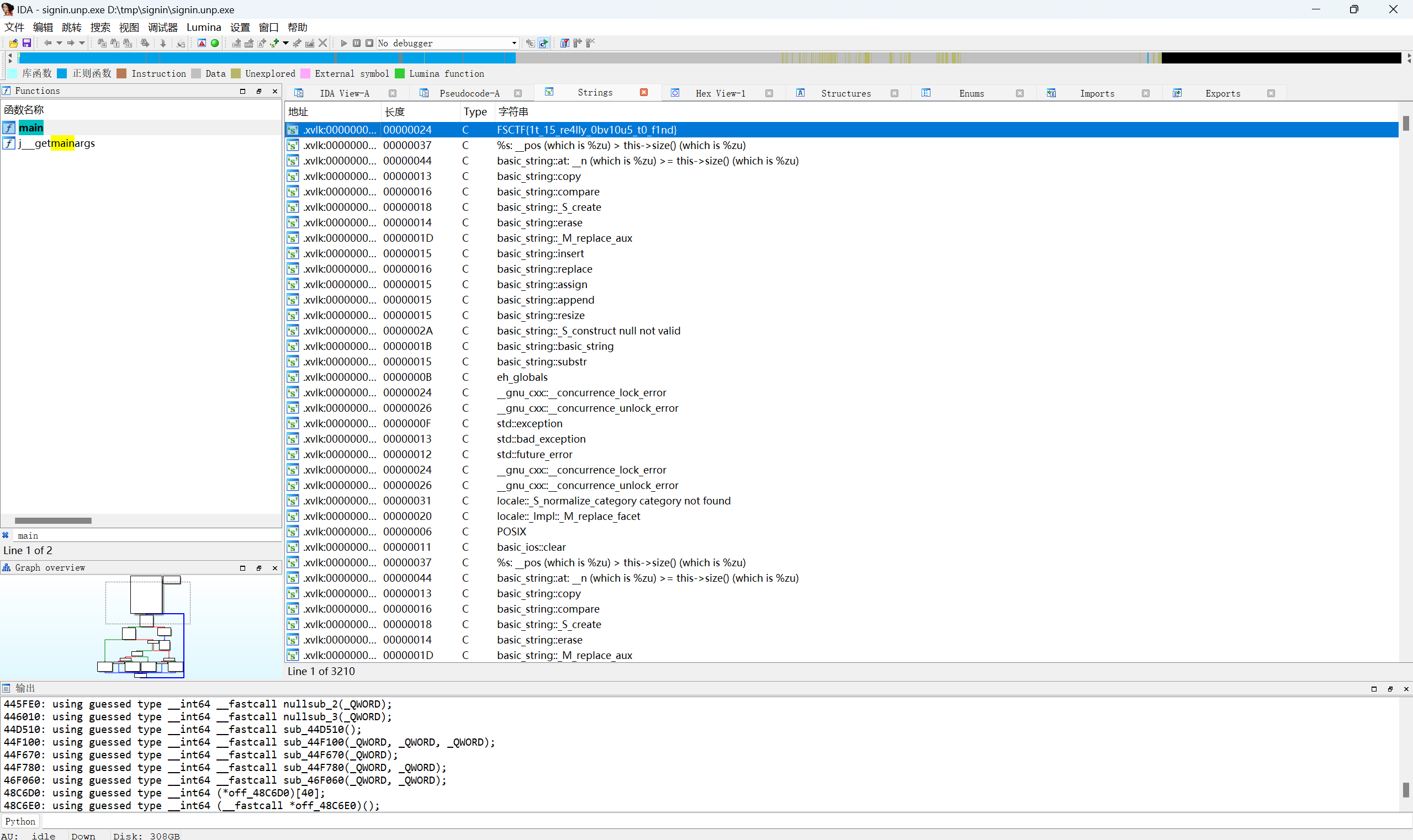
转ascll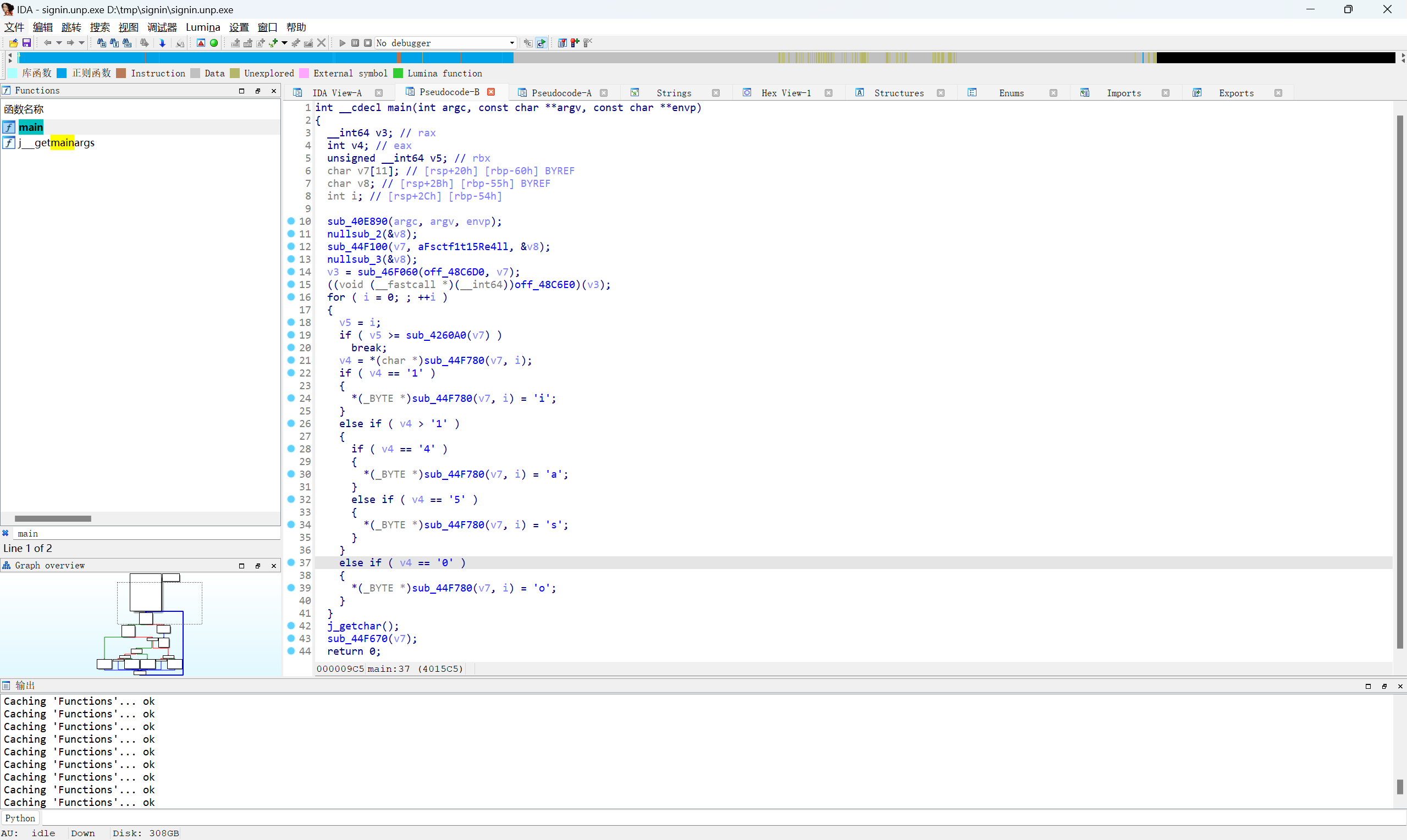
i代替1,a代替4,s代替5,o代替0
最后flag为
1 | FSCTF{it_is_really_obvious_to_find} |
Xor
题目描述:
1 | 简单的异或题 |
伪代码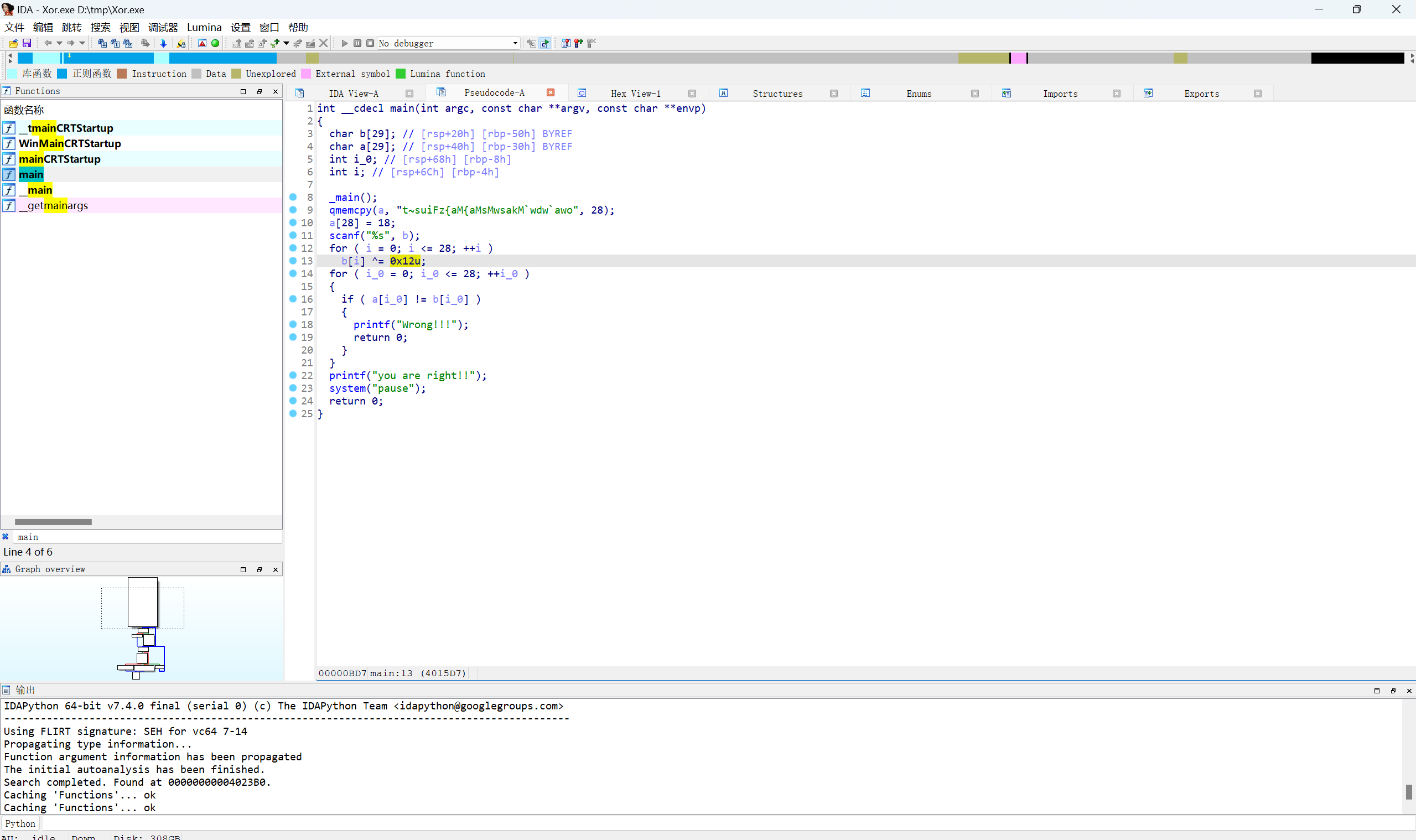
简单异或,赛博厨子直接一把梭
最后flag为
1 | flag{This_is_a_easy_reverse} |
EZRC4
题目描述:
1 | 听说你喜欢玩原神? |
查看伪代码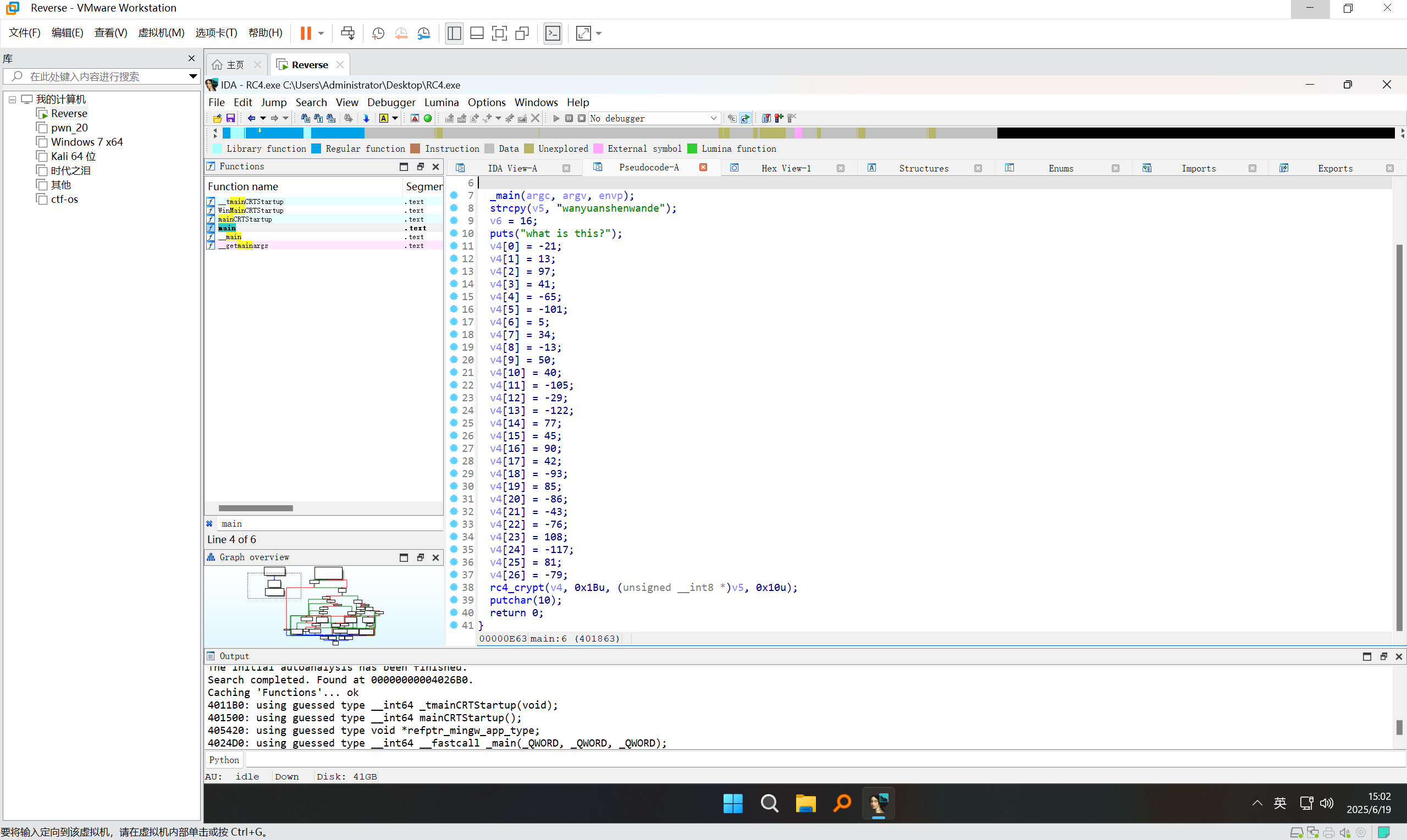
rc4解密
exp:
1 | def rc4_init(s_box, key, key_len): # rc4初始化函数,产生s_box |
运行得到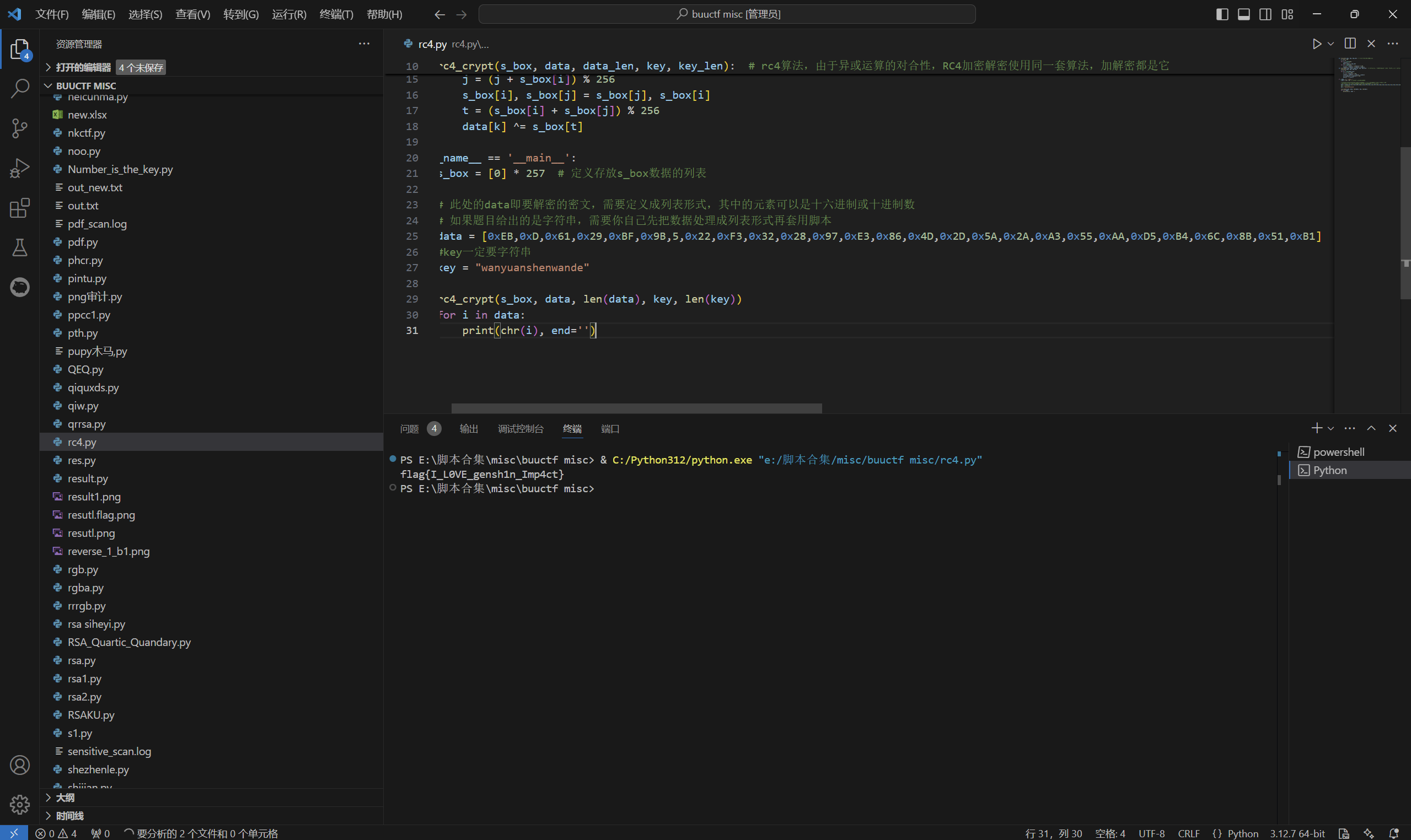
最后flag为
1 | flag{I_L0VE_gensh1n_Imp4ct} |
MINE SWEEPER
纯签到题,查看伪代码找到flag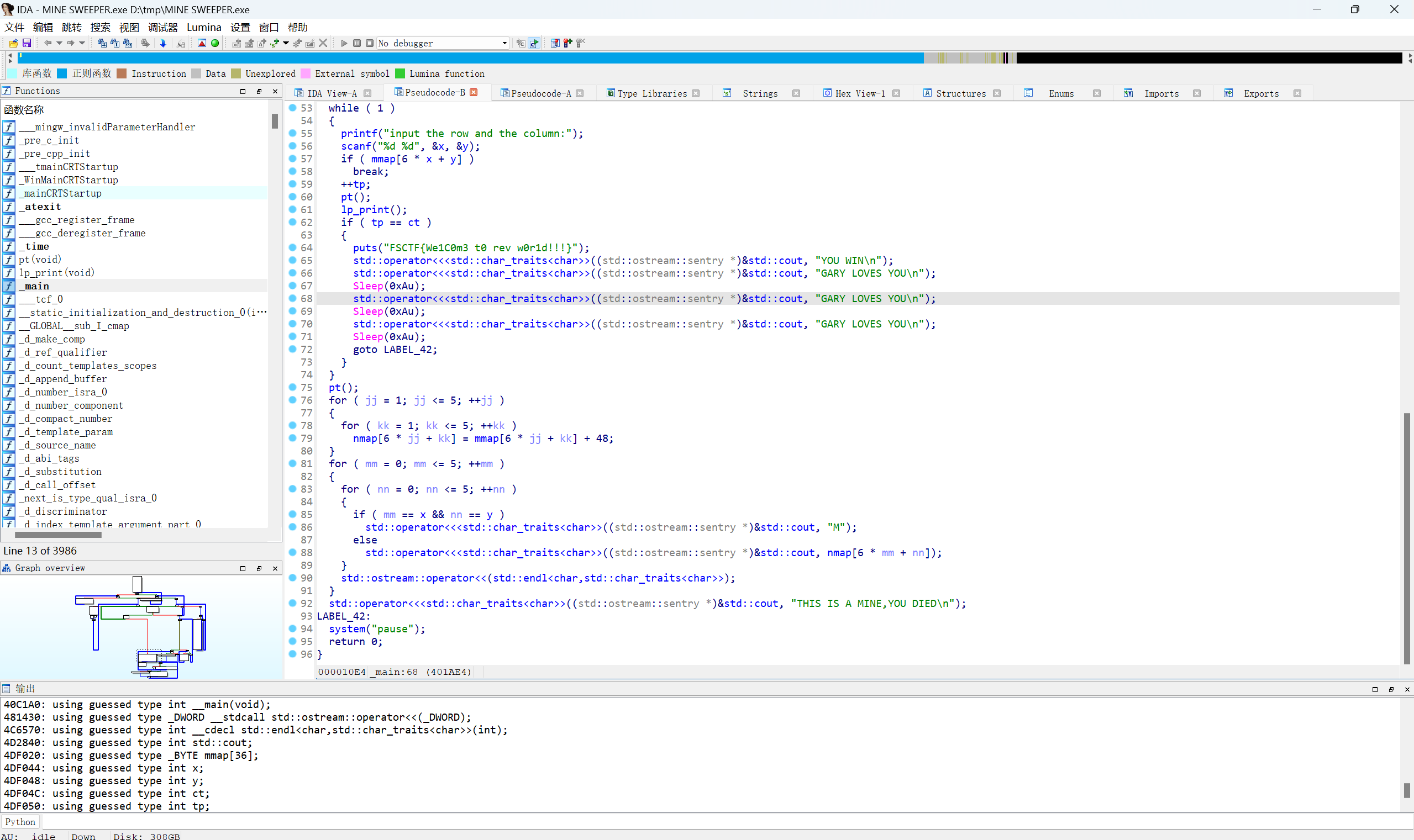
最后flag为
1 | FSCTF{We1C0m3 t0 rev w0r1d!!!} |
ez_pycxor
pyc反编译得到源码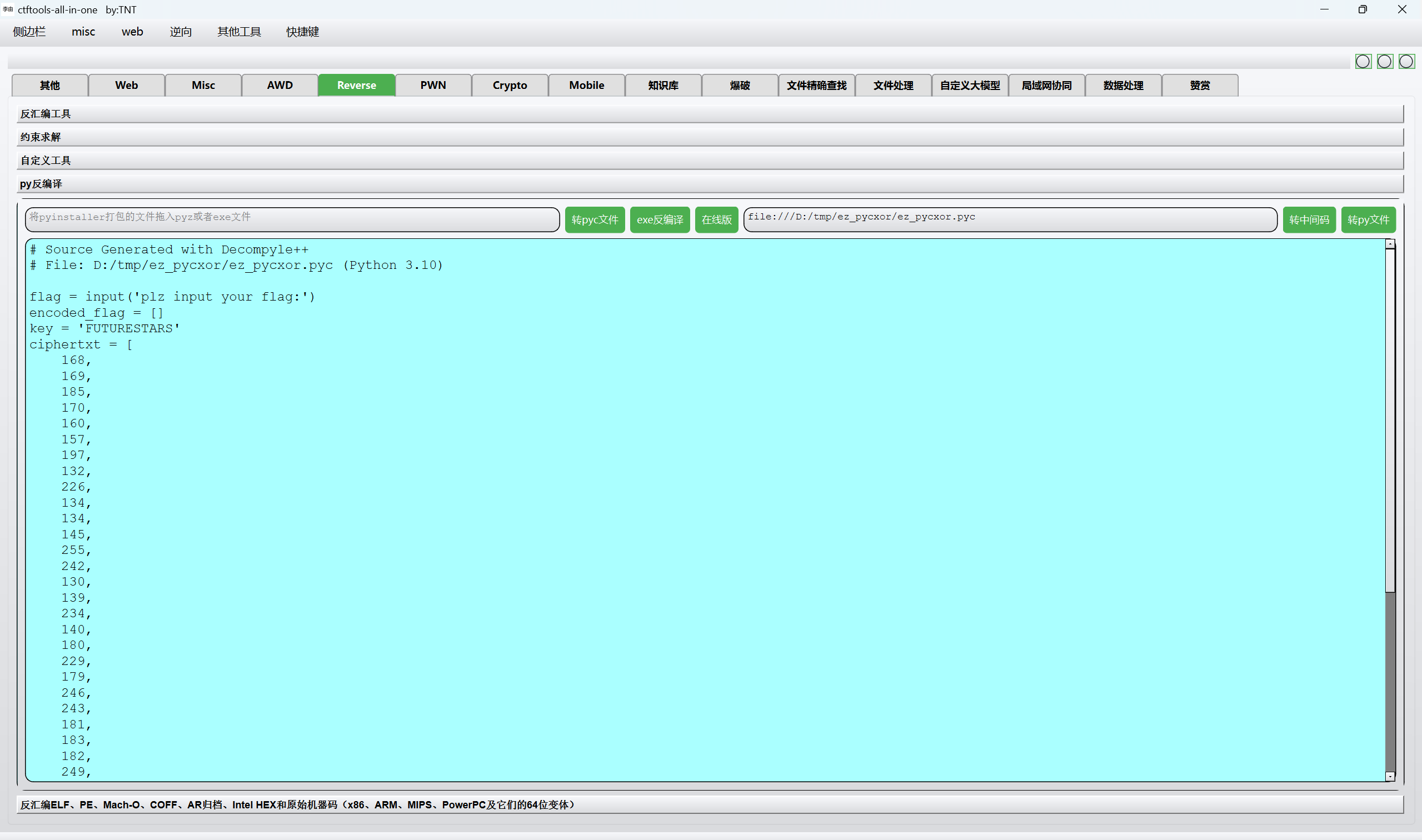
得到
1 | flag = input('plz input your flag:') |
写个解密脚本
exp:
1 | ciphertxt = [ |
运行得到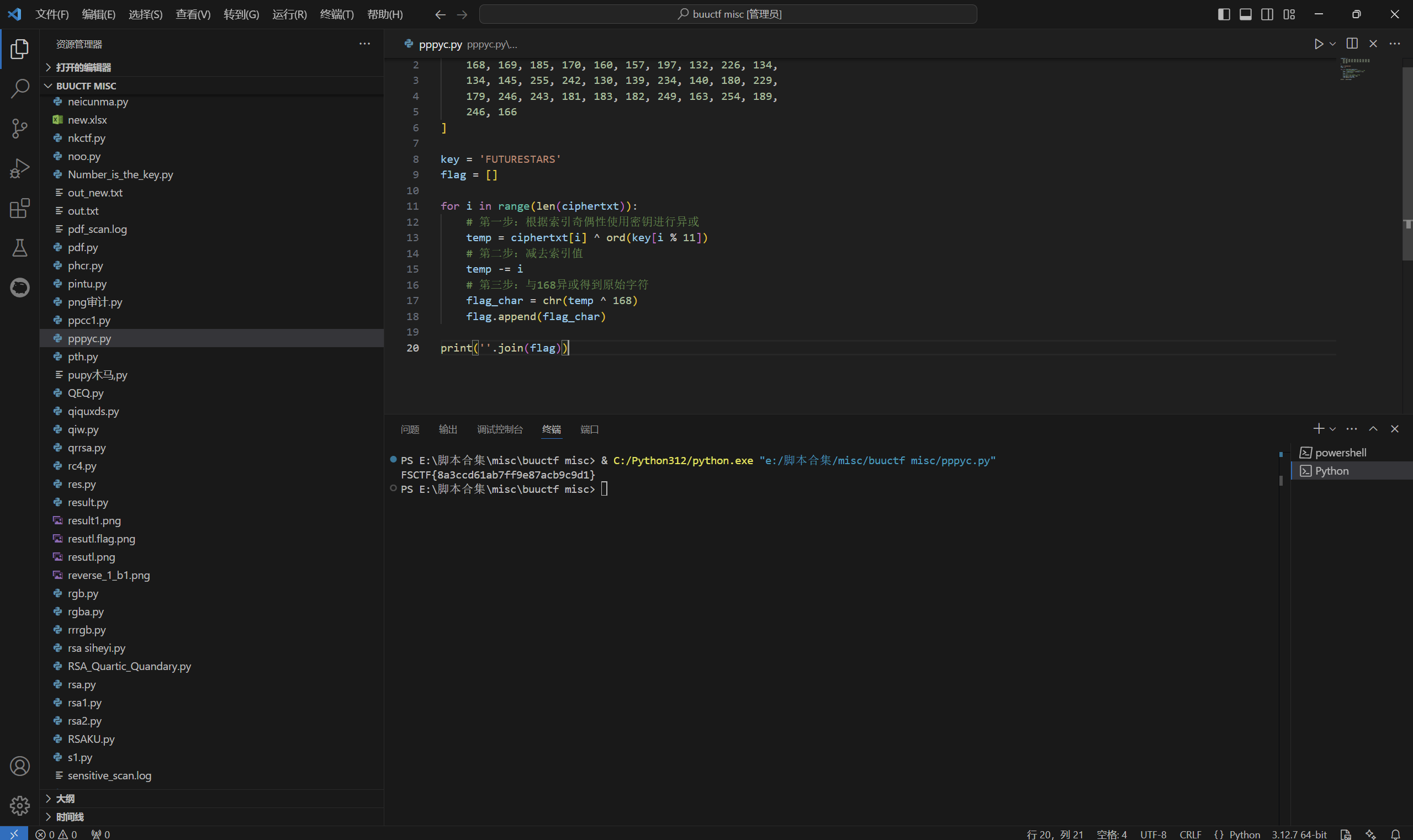
最后flag为
1 | FSCTF{8a3ccd61ab7ff9e87acb9c9d1} |
Tea_apk
题目描述:
1 | 这是个apk |
jadx打开apk文件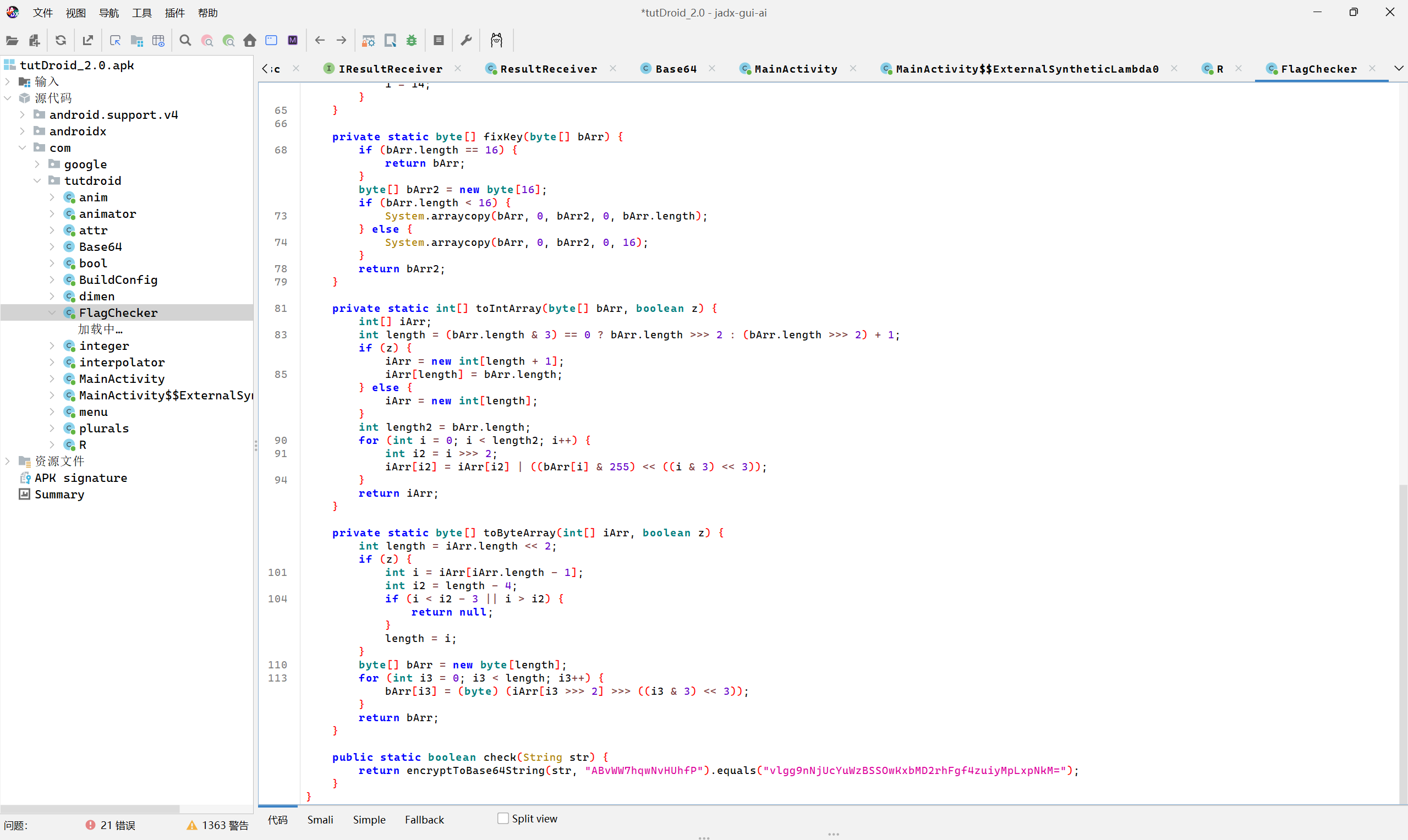
xxtea解密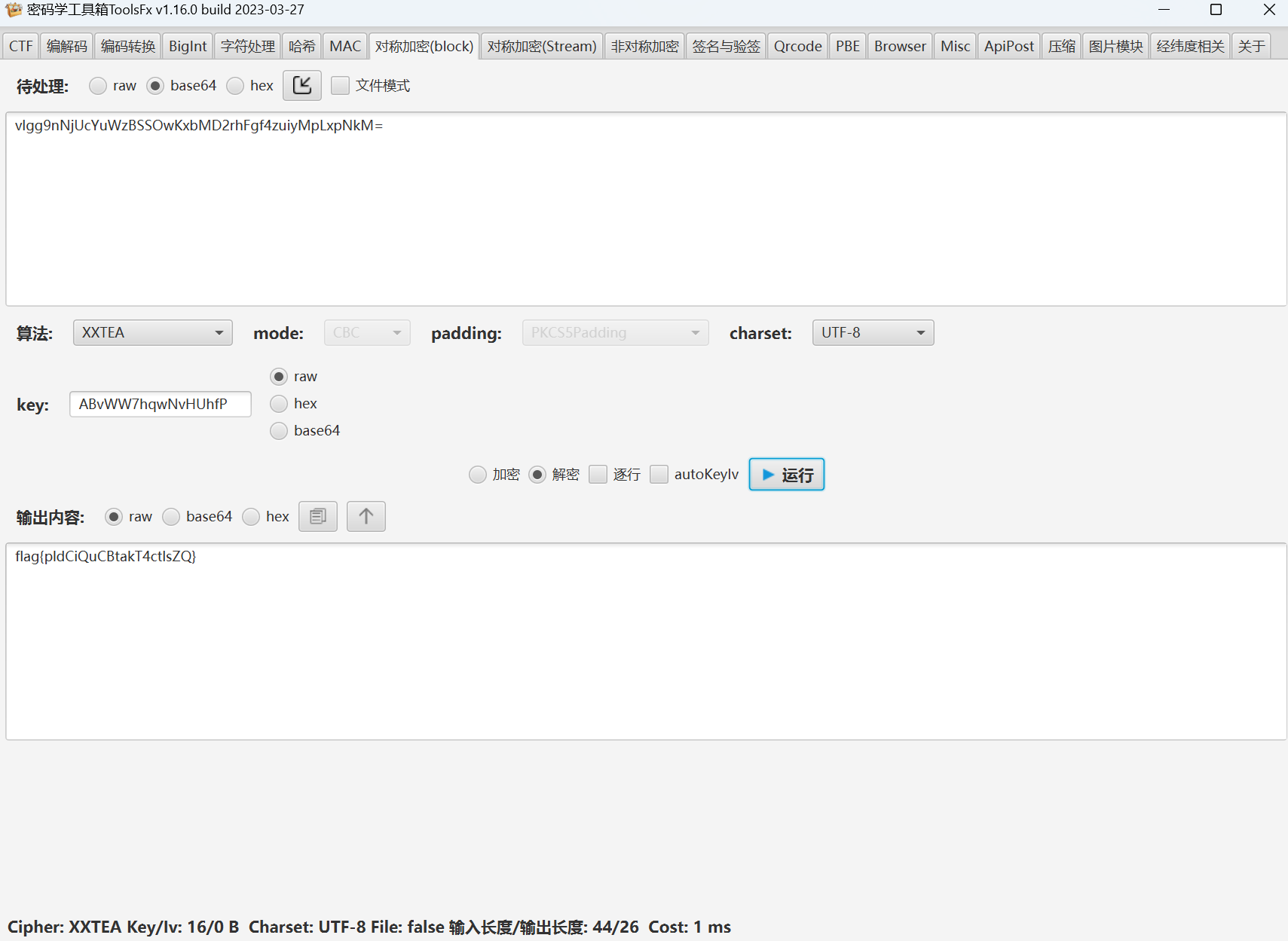
最后flag为
1 | flag{pldCiQuCBtakT4ctlsZQ} |
ezcode
魔改RC4
看到base表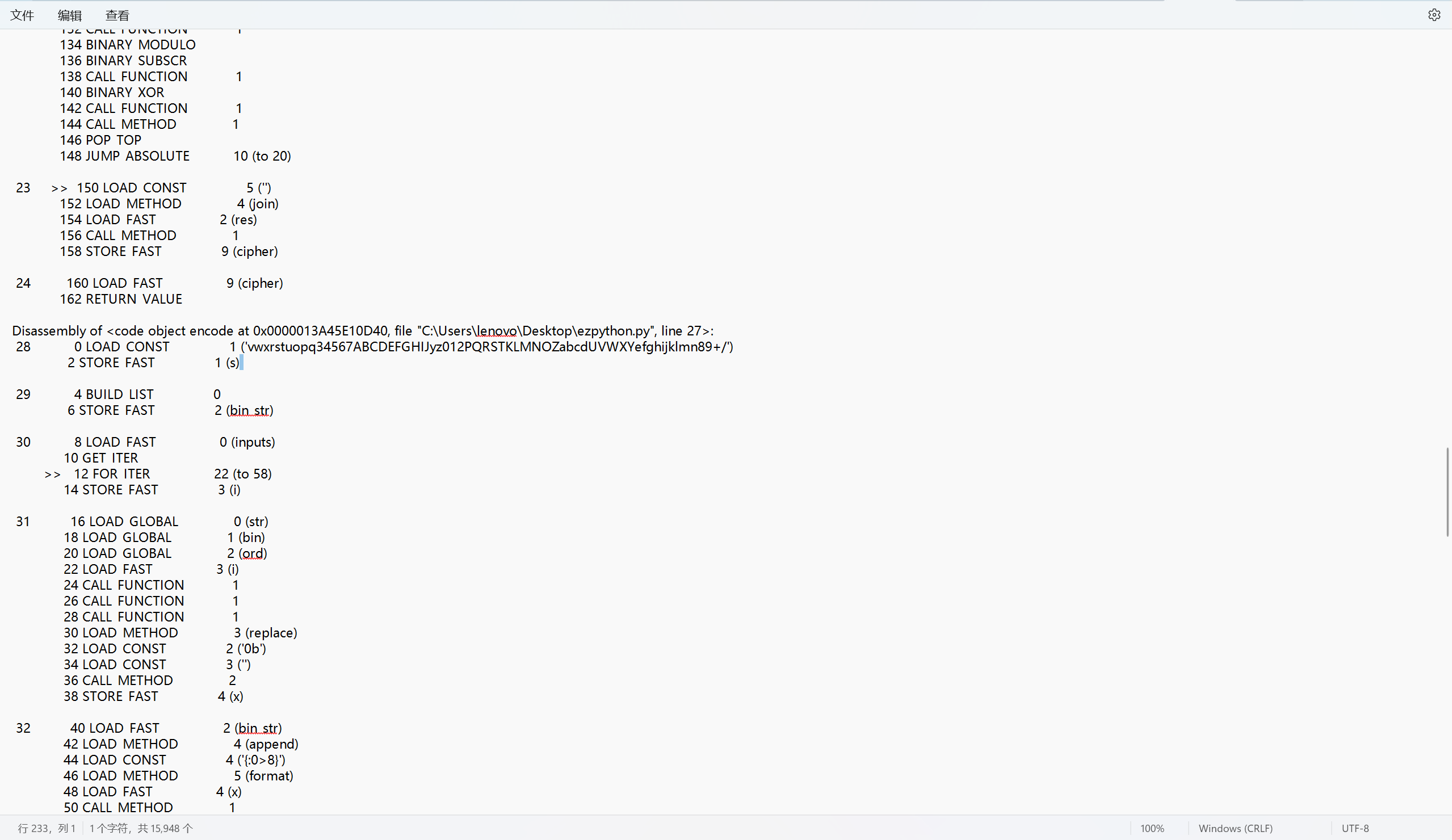
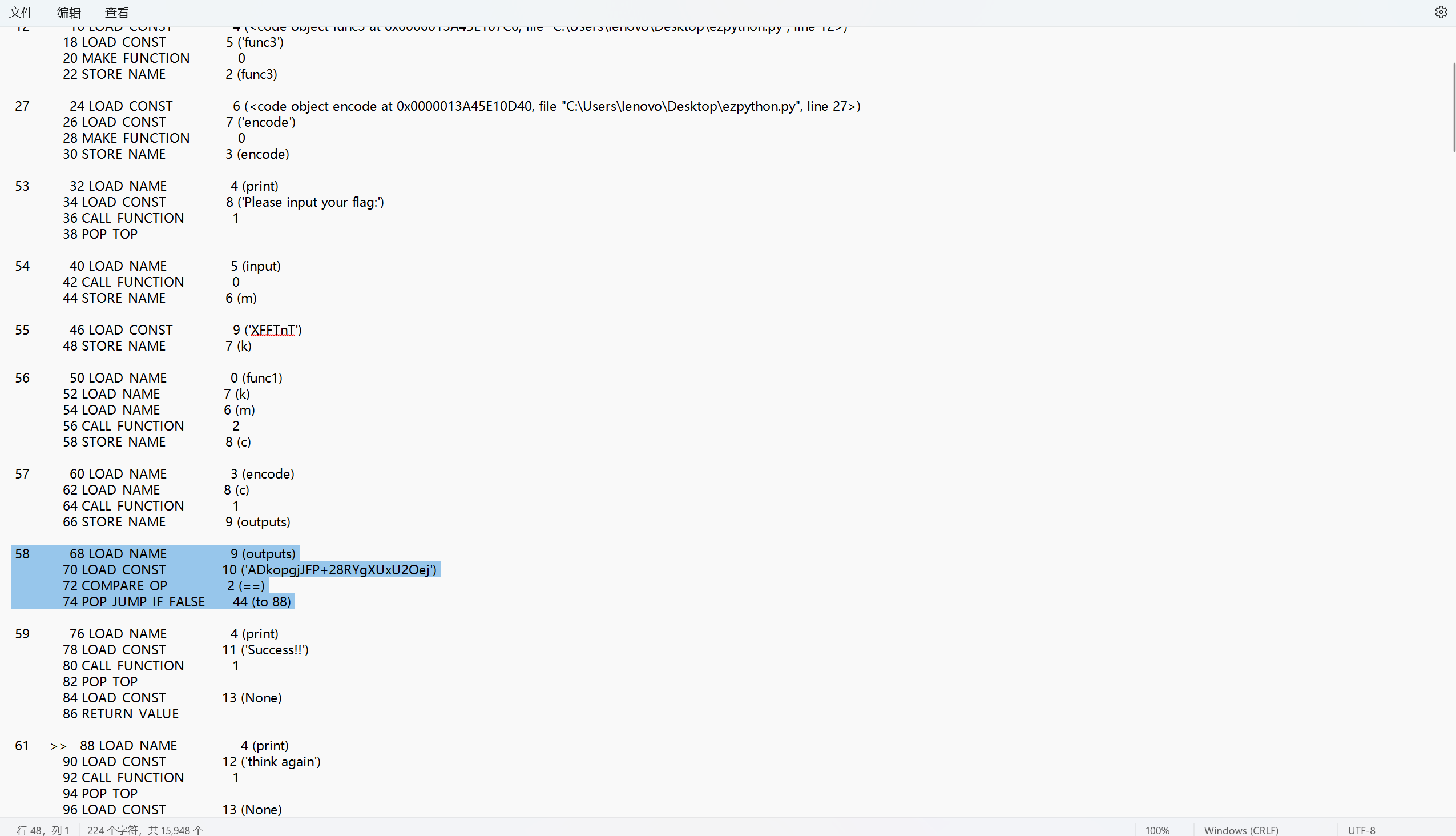
赛博厨子一把梭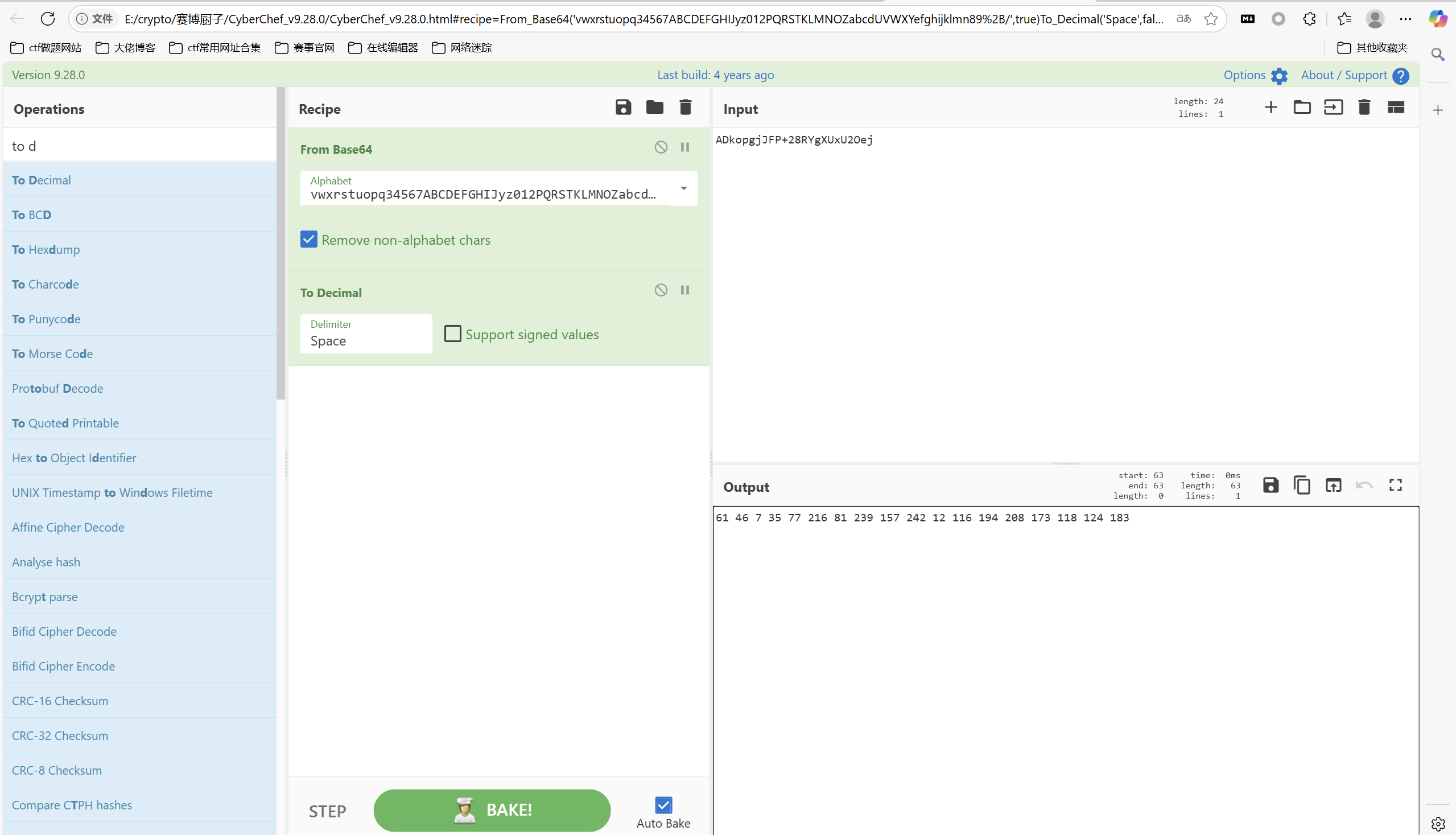
RC4解密
exp:
1 | def rc4_decrypt(ciphertext, key): |
运行得到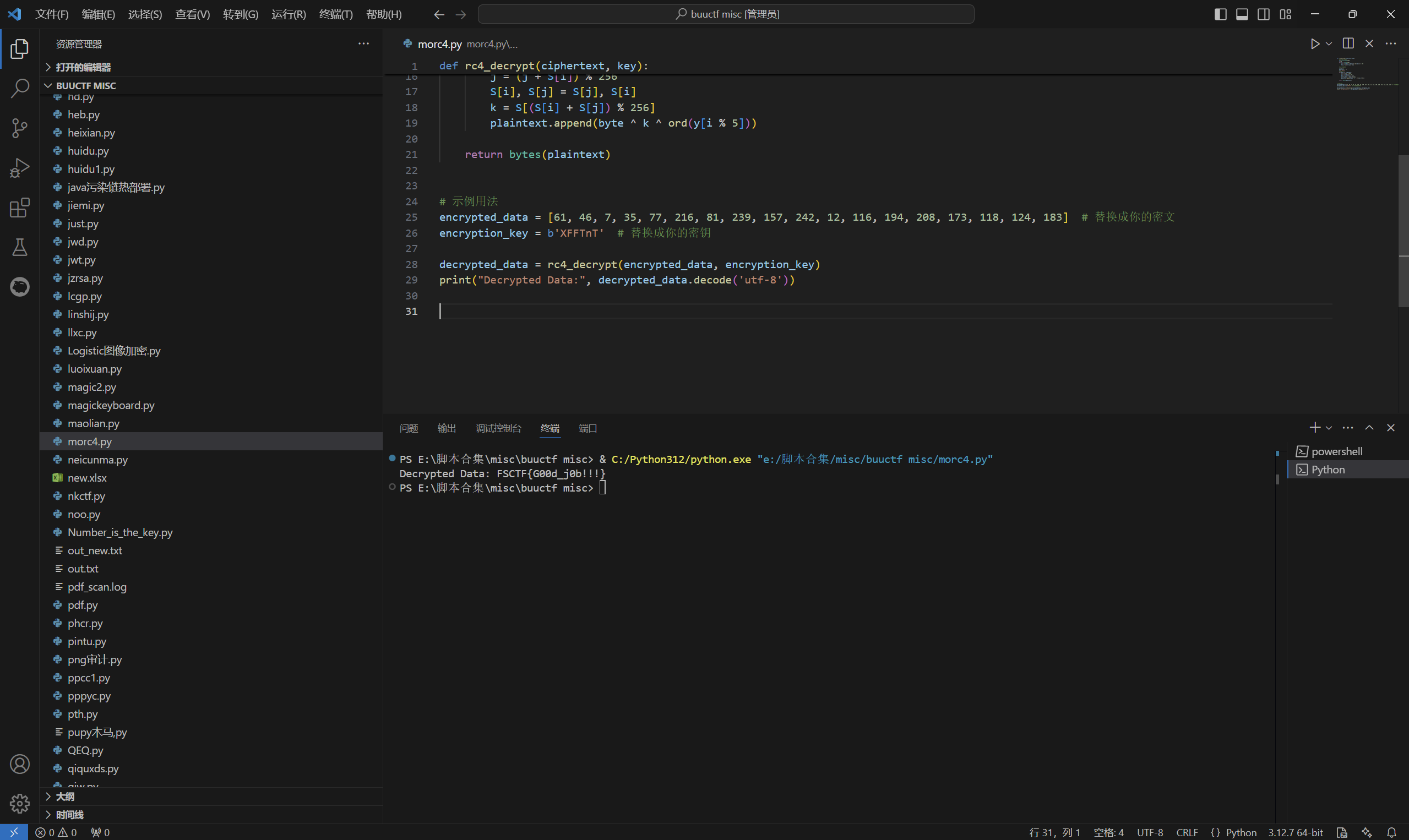
最后flag为
最后flag为
1 | FSCTF{G00d_j0b!!!} |
ezbroke
修复mz头、pe头、壳UPX修复再脱壳
IDA查看伪代码,VM虚拟机的题目
异或0x17
exp:
1 | list_1 = [0x51, 0x44, 0x54, 0x43, 0x51, 0x6C, 0x4E, 0x27, 0x62, 0x37, 0x64, 0x62, 0x74, 0x74, 0x72, 0x64, 0x64, 0x71, 0x62, 0x26, 0x26, 0x6E, 0x37, 0x75, 0x65, 0x27, 0x7C, 0x24, 0x37, 0x7A, 0x6E, 0x37, 0x67, 0x65, 0x27, 0x63, 0x24, 0x74, 0x63, 0x26, 0x27, 0x79, 0x36, 0x36, 0x36, 0x6A, 0x00] |
运行得到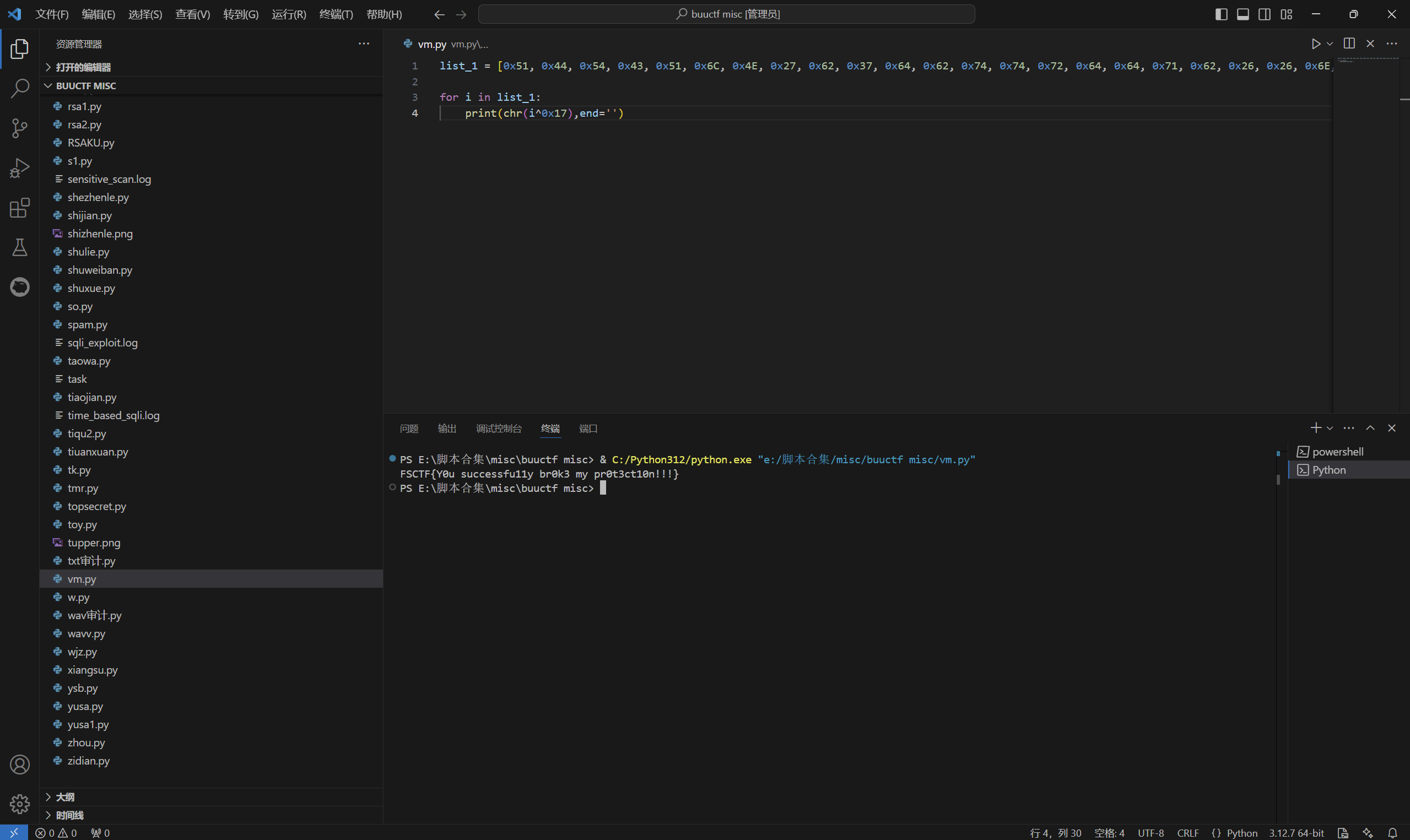
最后flag为
1 | FSCTF{Y0u successfu11y br0k3 my pr0t3ct10n!!!} |
rrrrust!!!
动调,循环异或
exp:
1 | res = [0x3E,0x2A,0x27,0x33,0x15,0x03,0x3D,0x77,0x25,0x64,0x03,0x67, |
运行得到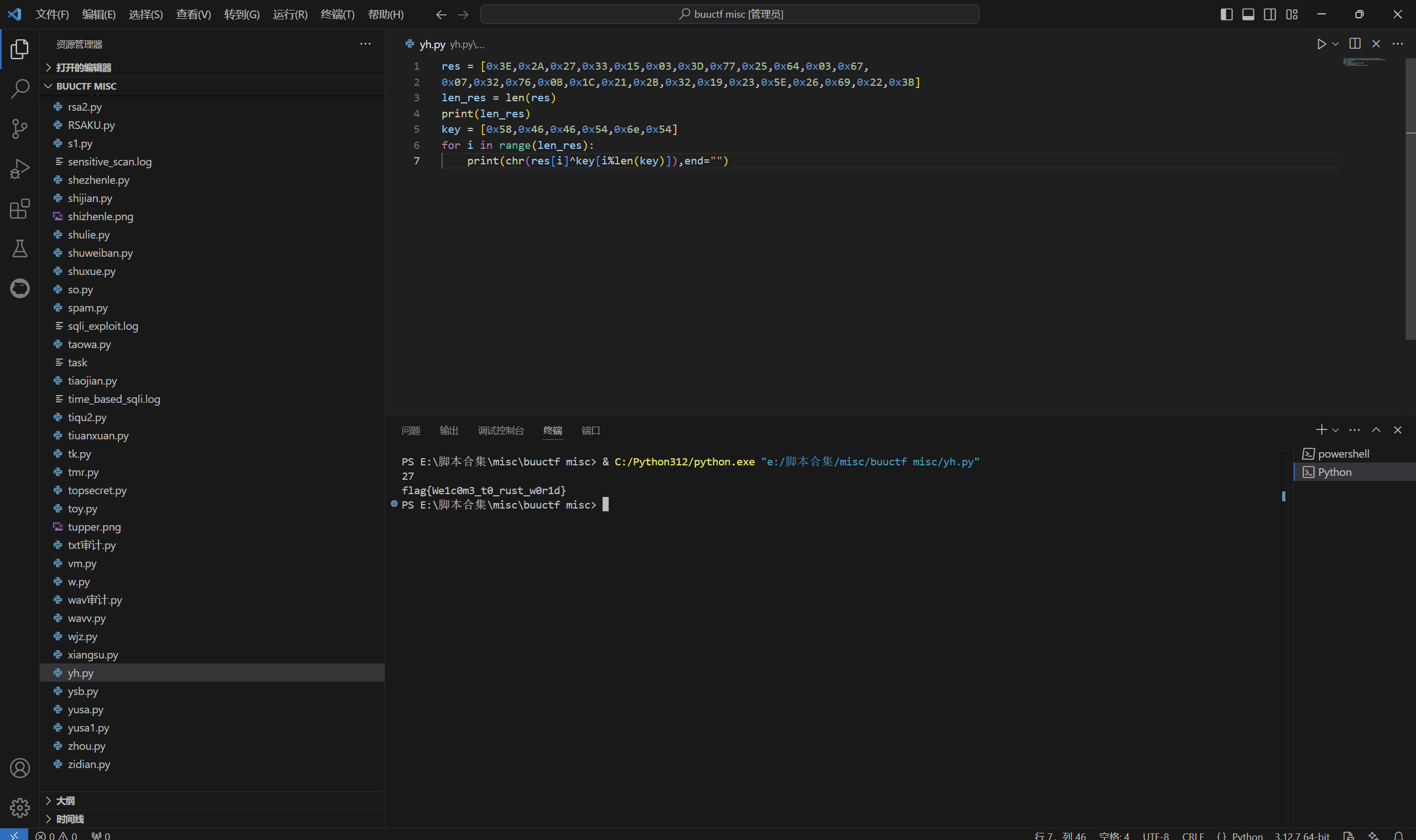
最后flag为
1 | flag{We1c0m3_t0_rust_w0r1d} |



