week1
Base
题目描述:
1 | This is a base question! |
考点:base 系列编码
赛博厨子一把梭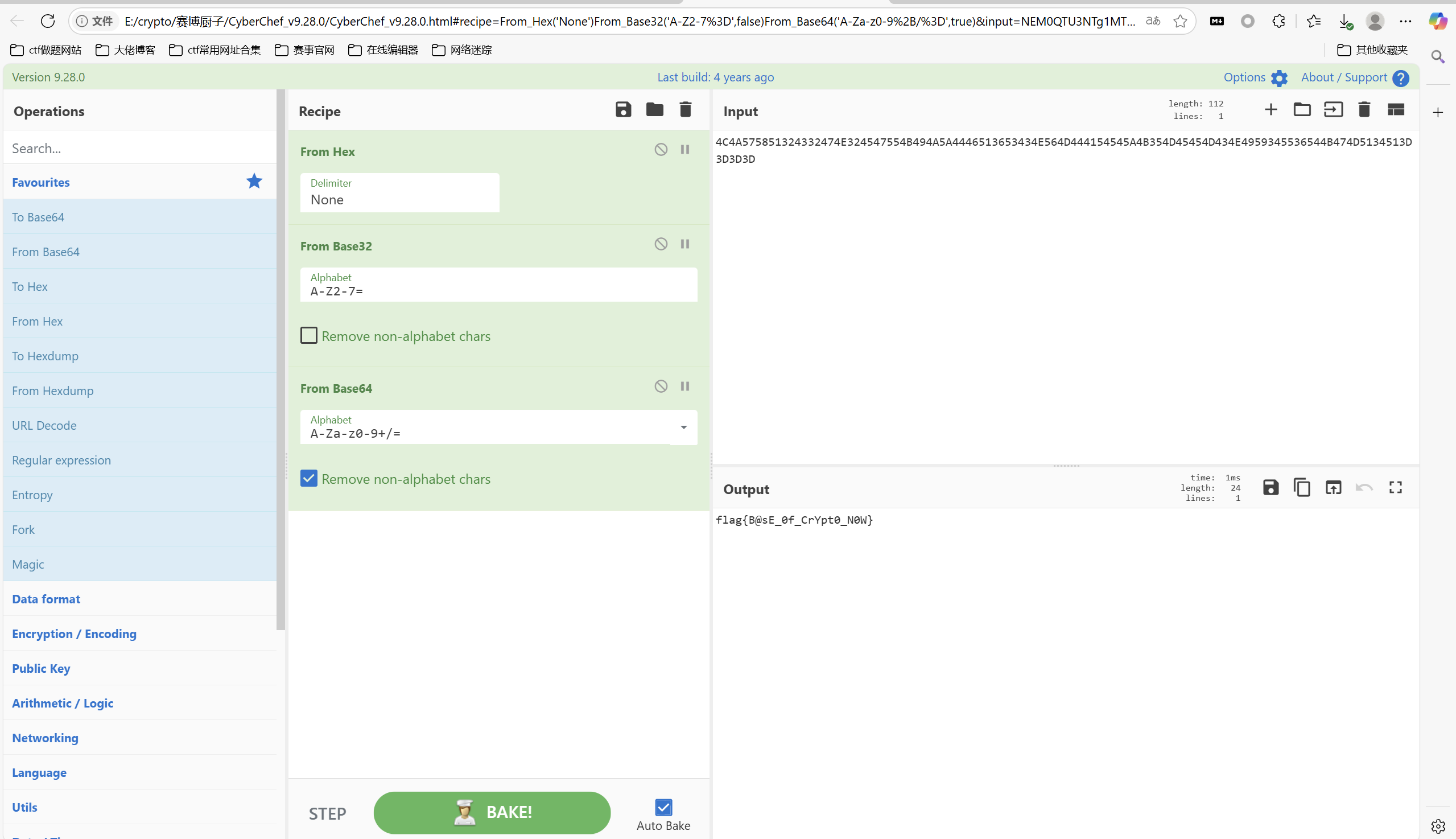
最后flag为
1 | flag{B@sE_0f_CrYpt0_N0W} |
Strange King
题目描述:
1 | 某喜欢抽锐刻 5 的皇帝想每天进步一些,直到他娶了个模,回到原点,全部白给😅 这是他最后留下的讯息:ksjr{EcxvpdErSvcDgdgEzxqjql},flag 包裹的是可读的明文 |
考点:变异凯撒
题目描述中的皇帝是凯撒皇帝,key是5,凯撒解密发现有一个递增 2 的规律,为了避免超出字母表范围,模的话是对应的 0-25,我们再模一个 26
exp:
1 | txt = 'ksjr{EcxvpdErSvcDgdgEzxqjql}' |
运行得到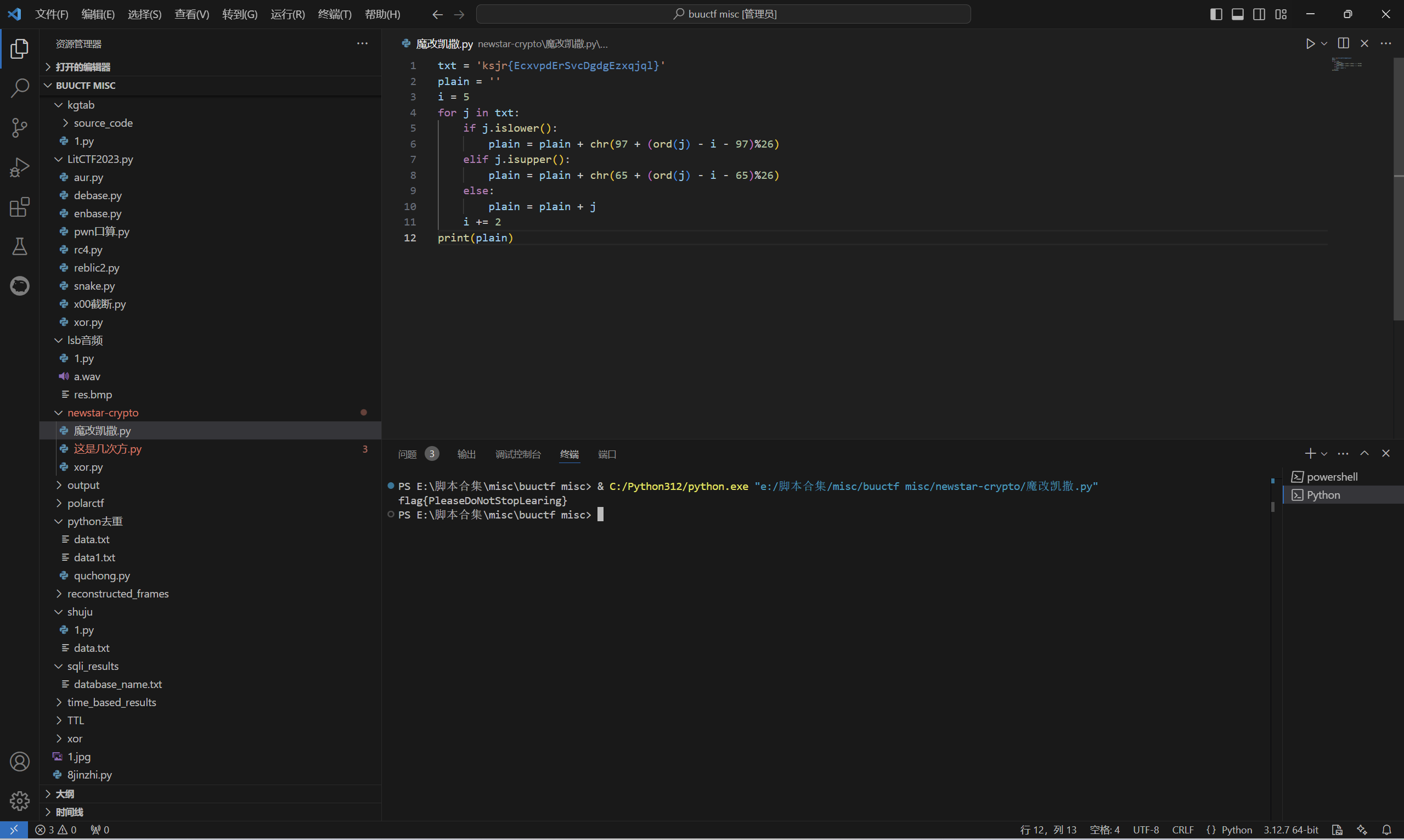
最后flag为
1 | flag{PleaseDoNotStopLearing} |
xor
题目描述:
1 | 如果再来一次的话,就能回到从前,一切都会好起来的😭 |
下载附件
1 | #As a freshman starting in 2024, you should know something about XOR, so this task is for you to sign in. |
考点:异或
exp:
1 | from pwn import xor |
运行得到
最后flag为
1 | flag{0ops!_you_know_XOR!} |
一眼秒了
题目描述:
1 | n 小小的也很可爱 |
下载附件
1 | from Crypto.Util.number import * |
考点:RSA
分解素数n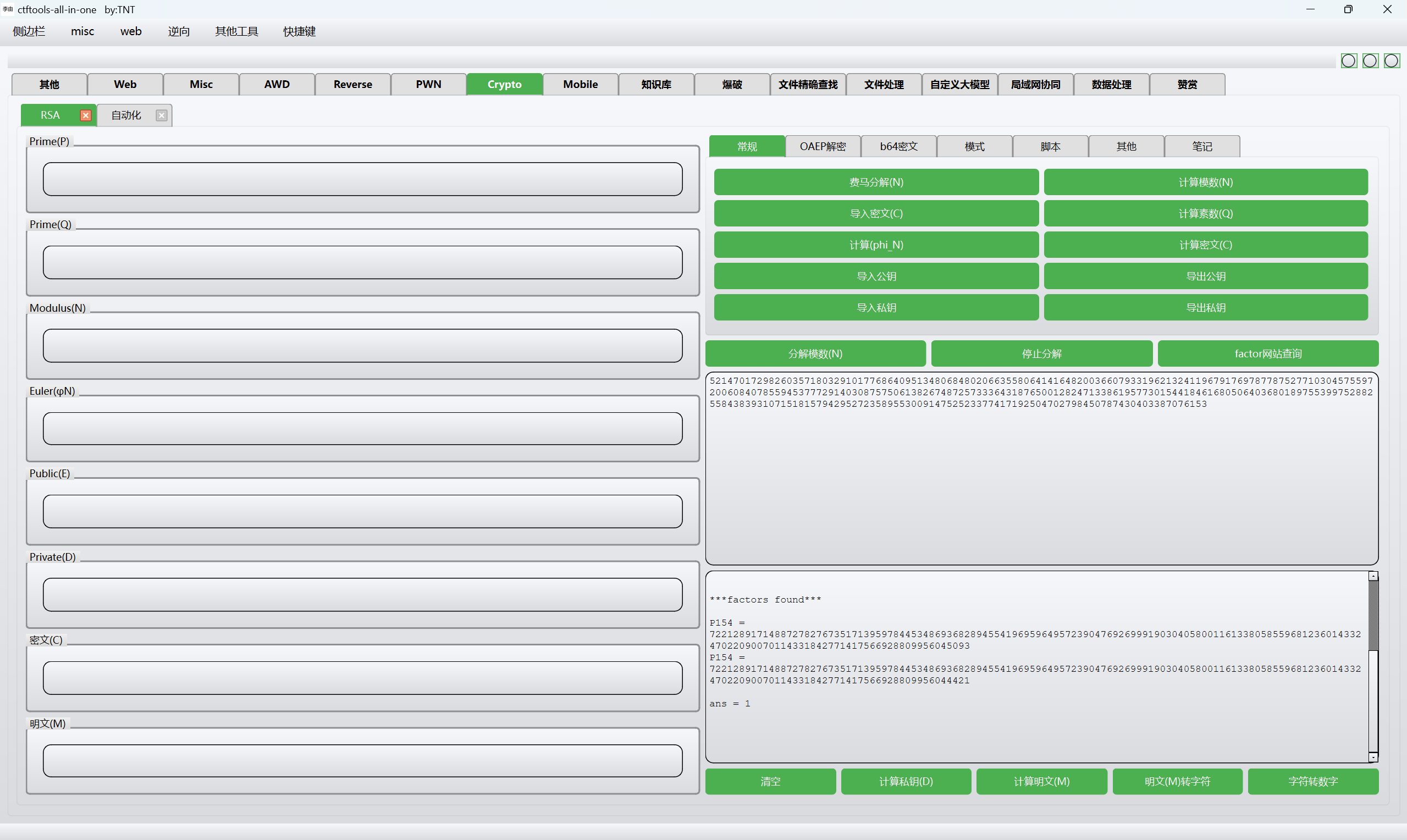
然后一把梭得到flag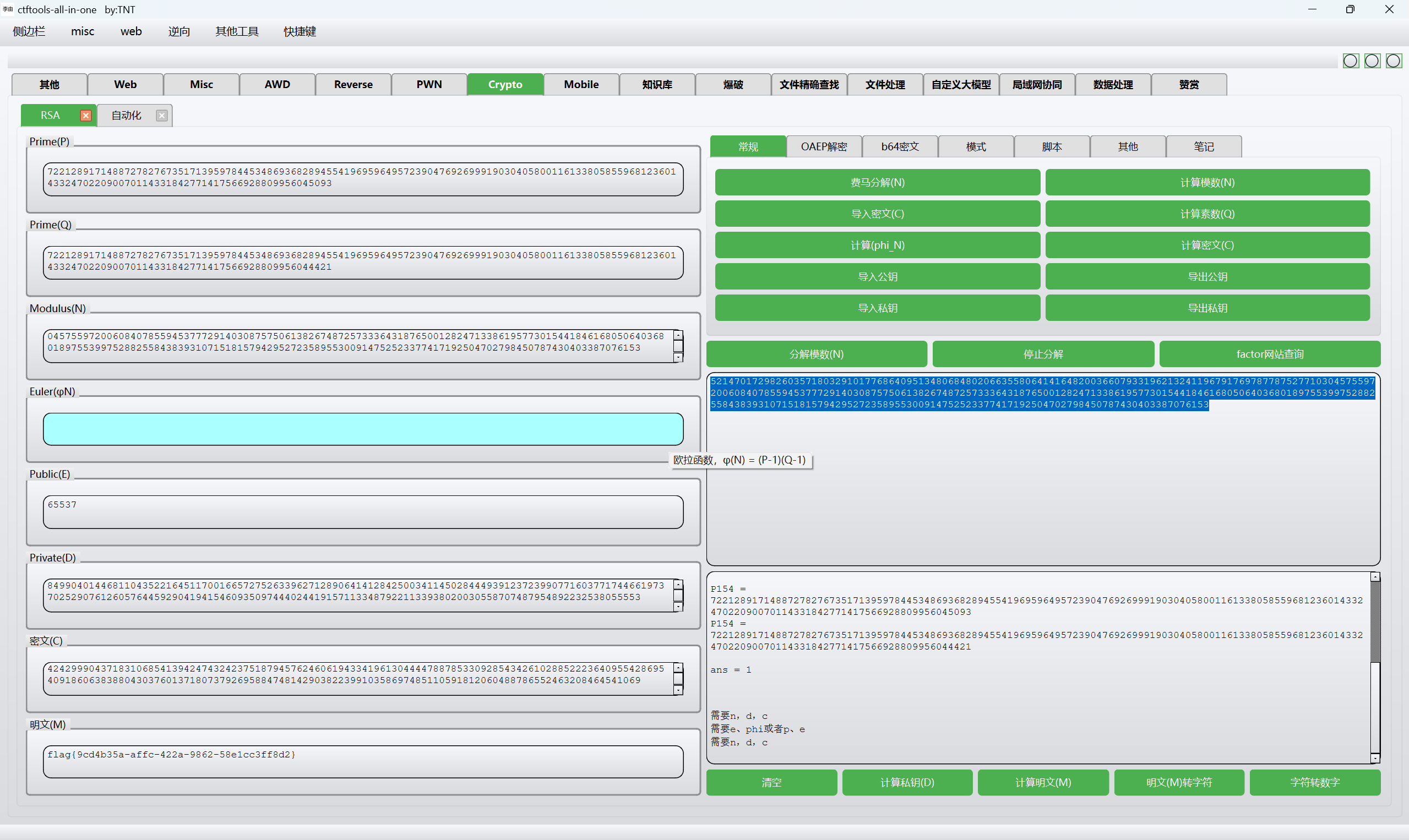
最后flag为
1 | flag{9cd4b35a-affc-422a-9862-58e1cc3ff8d2} |
week2
Just one and more than two
题目描述:
1 | 欸,少了少了?😨噢,又多了多了!😱 |
下载附件
1 | from Crypto.Util.number import * |
考点:欧拉函数
解题:
1 | 第一部分解密: |
exp:
1 | from Crypto.Util.number import * |
运行得到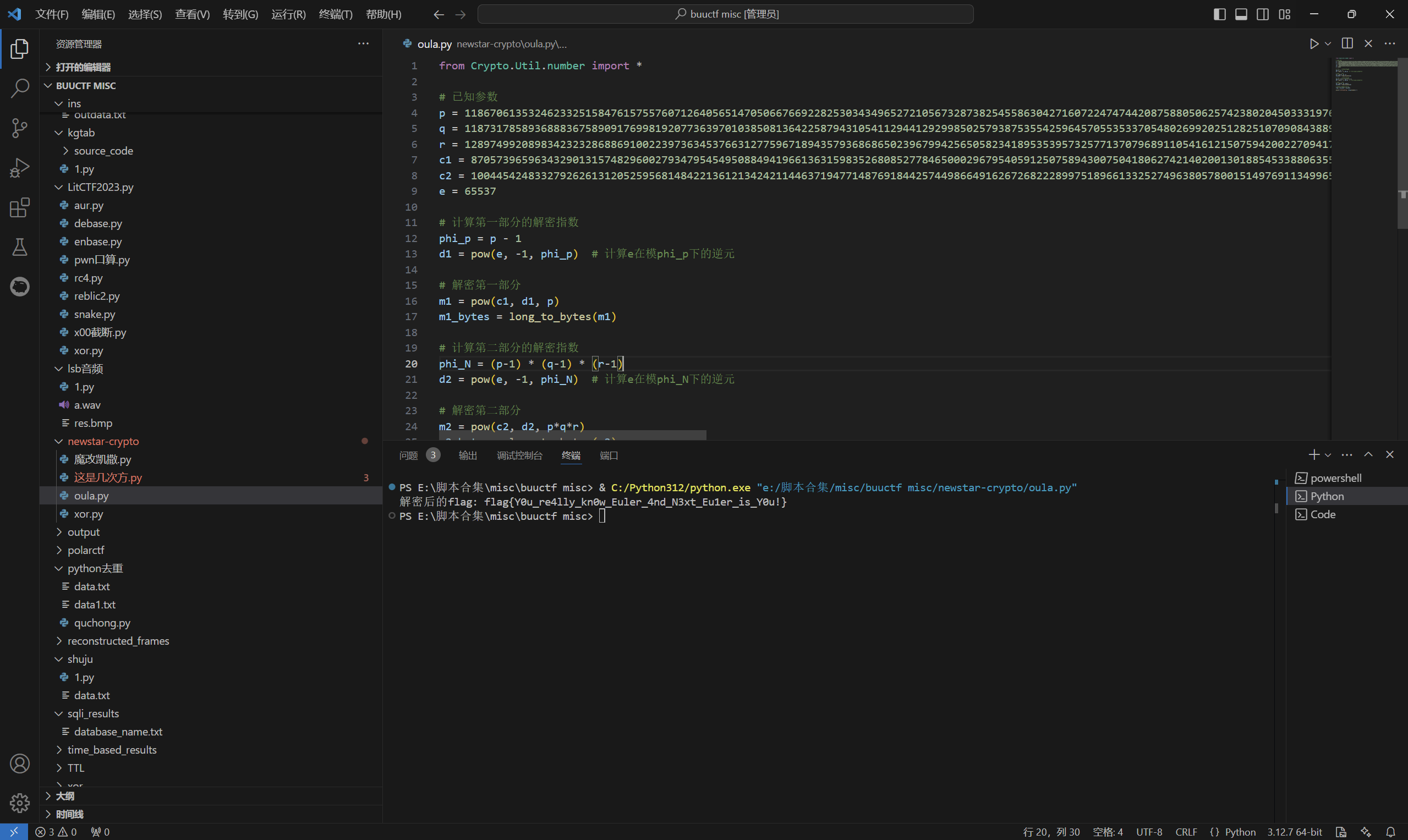
最后flag为
1 | flag{Y0u_re4lly_kn0w_Euler_4nd_N3xt_Eu1er_is_Y0u!} |
Since you konw something
题目描述:
1 | 你见到了上周的老朋友,你只需告诉他一部分信息,他就会给你 key |
下载附件
1 | from pwn import xor |
考点:异或爆破key
exp:
1 | from pwn import xor |
运行得到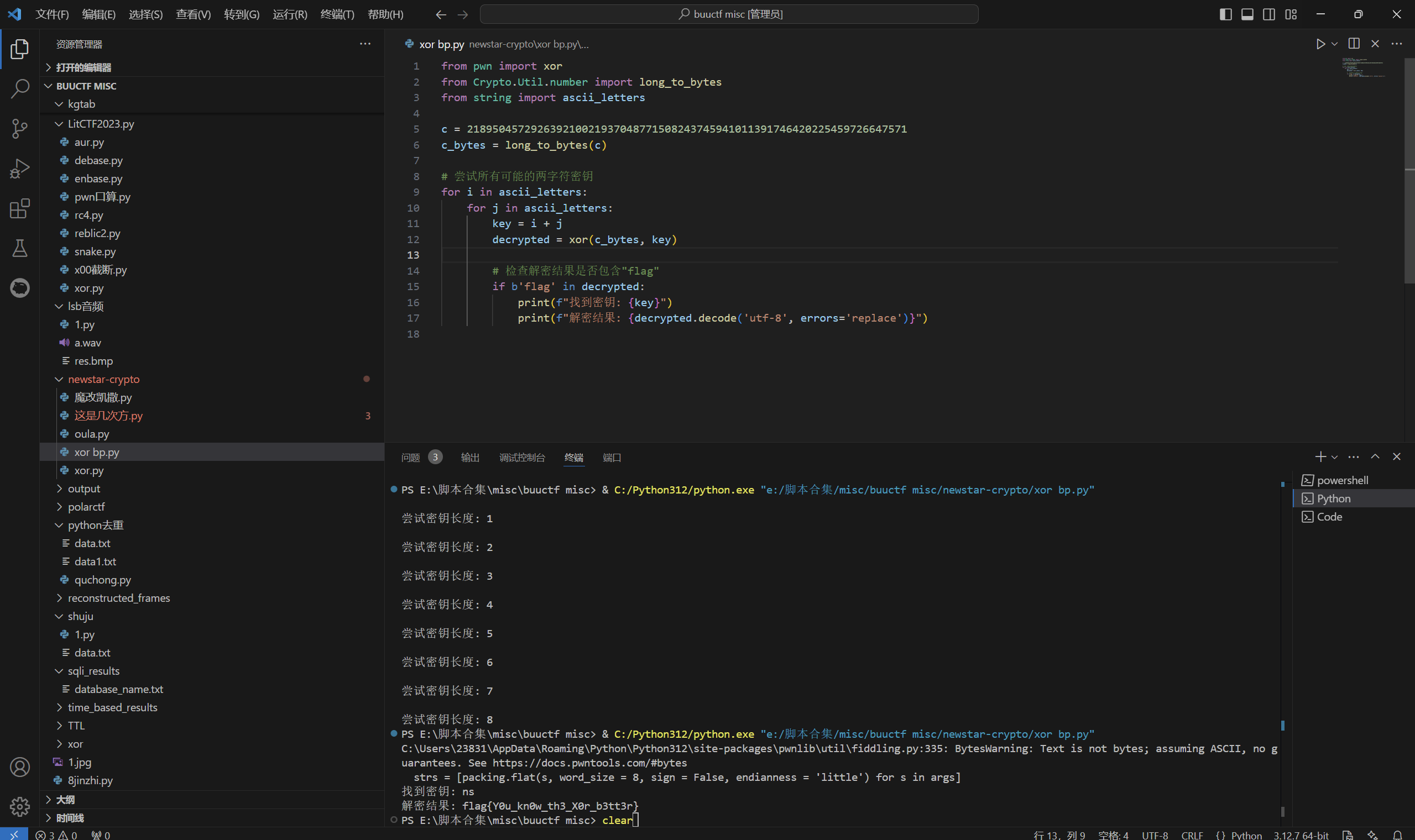
最后flag为
1 | flag{Y0u_kn0w_th3_X0r_b3tt3r} |
茶里茶气
题目描述:
1 | 茶?是红茶、绿茶还是奶茶? |
下载附件
1 | from Crypto.Util.number import * |
考点:TEA算法
还原算法即可
解题思路
1 | 代码解析: |
exp:
1 | v2 = 0 |
运行得到
最后flag为
1 | flag{f14gg9_te2_1i_7ea_7} |
这是几次方?疑惑!
题目描述:
1 | ^ w ^ |
下载附件
1 | from Crypto.Util.number import * |
考点:异或符号的运算优先级
在 Python 中异或先计算两边,再进行异或操作
所有 hint 是 p 和 e+10086 的异或结果,可以求p
1 | p=hint^(e+10086) |
exp:
1 | from Crypto.Util.number import * |
运行得到
最后flag为
1 | flag{yihuo_yuan_lai_xian_ji_suan_liang_bian_de2333} |
week3
不用谢喵
题目描述:
1 | ——求求你帮我解密吧,我什么都会做的😭 |
下载附件
1 | from Crypto.Cipher import AES |
考点:AES算法
解题思路
1 | AES-CBC模式加密过程: |
exp:
1 | from Crypto.Cipher import AES |
运行得到
最后flag为
1 | flag{HOw_c4REfu1Ly_yOu_O65ERve!} |
两个黄鹂鸣翠柳
题目描述:
1 | 数行白鹭上青天 |
下载附件
1 | import random |
考点:关联信息攻击,多项式 gcd
参考
exp:
1 | from Crypto.Util.number import * |
运行得到
官方做法是
Half-GCD 算法
exp:
1 | from Crypto.Util.number import * |
运行得到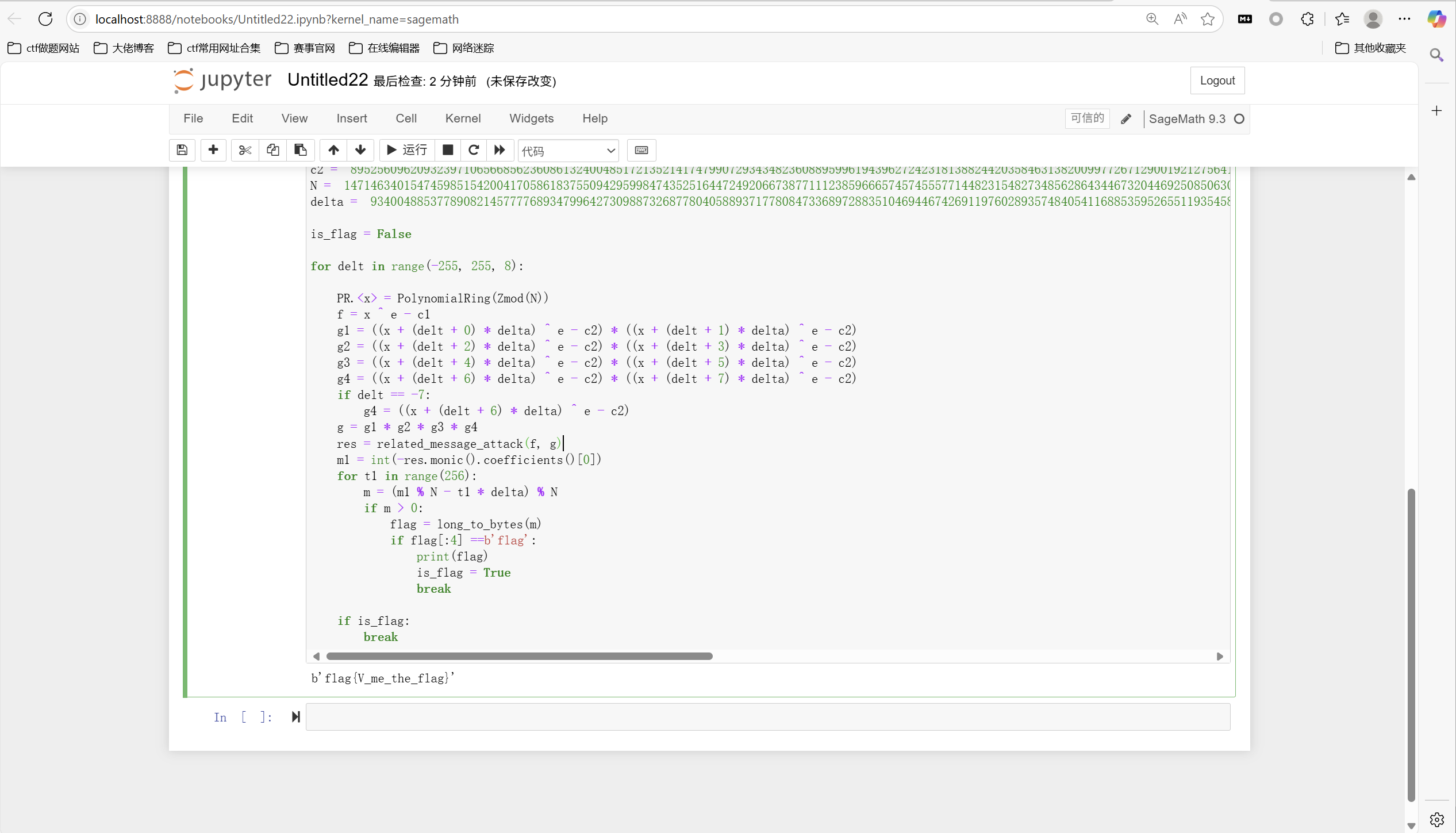
最后flag为
1 | flag{V_me_the_flag} |
故事新编 1
题目描述:
1 | 我亦曾无敌人间三百年 |
下载附件
1 | from hashlib import md5 |
考点:维吉尼亚爆破
在线网站爆破
然后直接将zen1和key内容填上,运行脚本即可
exp:
1 | from hashlib import md5 |
运行得到
最后flag为
1 | flag{b14375358eabfea4e405bd2186936289} |
故事新编 2
题目描述:
1 | 生于余烬,归于虚无。 |
hint:
1 | 请注意首尾的换行符 |
下载附件
1 | from hashlib import md5 |
考点:变异维吉尼亚爆破
依旧在线网站爆破
根据提示修改,然后直接将zen2和key2内容填上,运行脚本即可
exp:
1 | from hashlib import md5 |
运行得到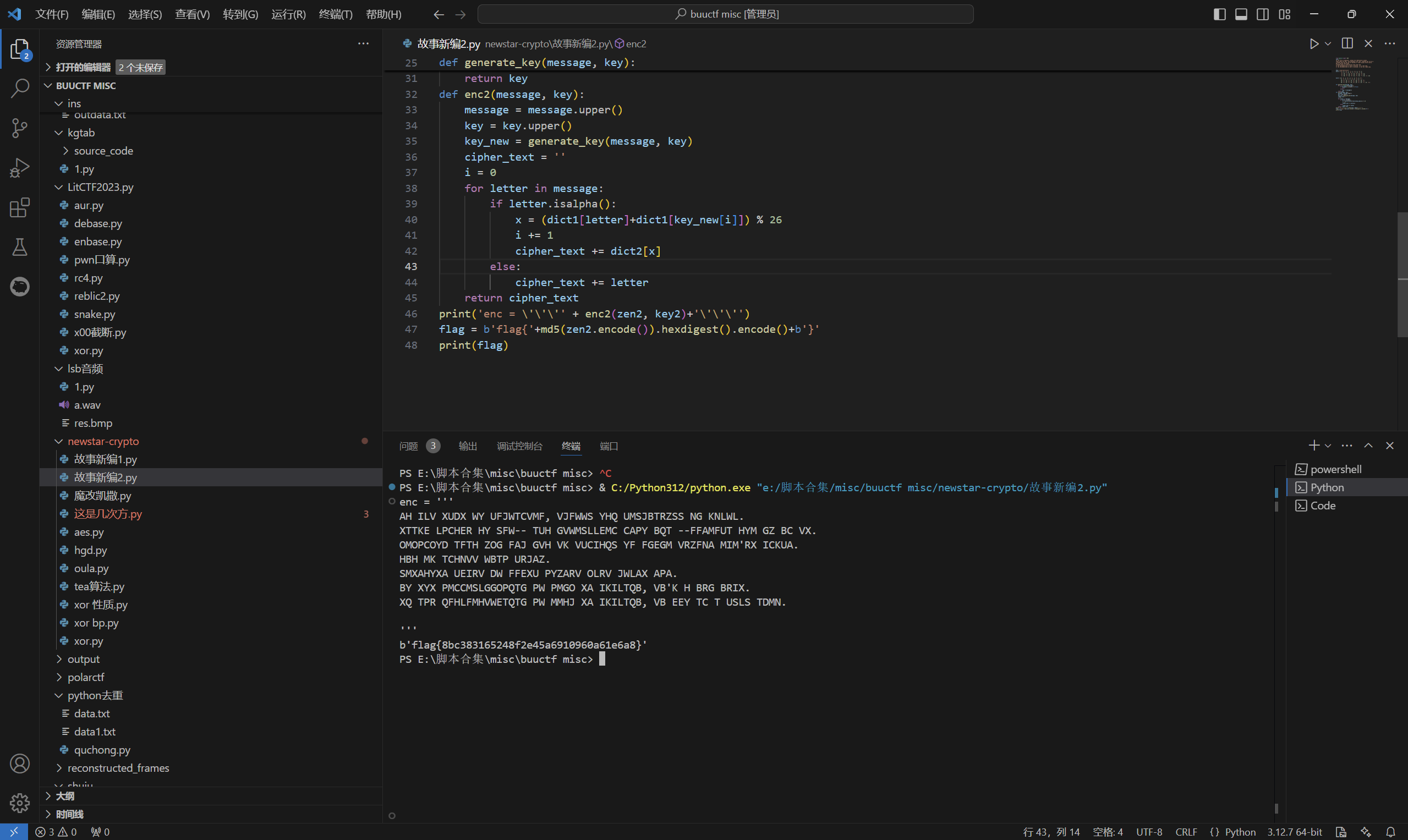
最后flag为
1 | flag{8bc383165248f2e45a6910960a61e6a8} |
没 e 这能玩?
题目描述:
1 | 公钥到处乱传,这下大家都能加密了——我不想把 e 告诉大家,只有聪明的宝宝才可以知道 |
下载附件
1 | from Crypto.Util.number import * |
考点:离散对数
1 | e = discrete_log(2**512, hint, big_prime) |
exp:
1 | from Crypto.Util.number import * |
运行得到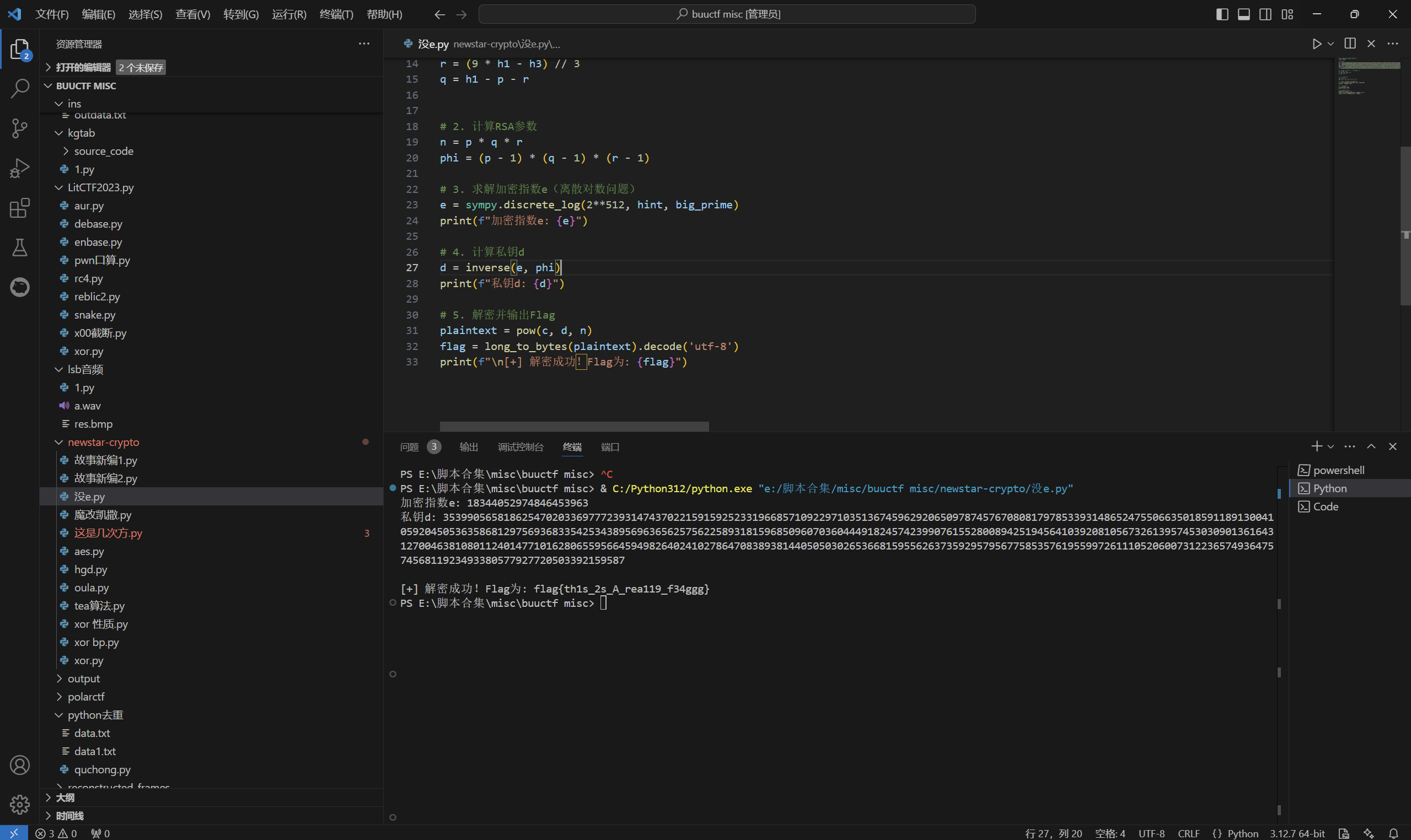
最后flag为
1 | flag{th1s_2s_A_rea119_f34ggg} |
week4
俱以我之名
题目描述:
1 | 开启技能后,在天赋生效范围内可部署地面召唤「黄金盟誓」;技能期间可攻击被天赋生效范围阻挡的敌人,攻击时伤害类型变为真实,对 RSA 造成真实伤害。 |
下载附件
1 | from Crypto.Util.number import * |
考点:维纳攻击和连分数
参考文章
求Golden_Oath,以及pq关系
exp:
1 | from Crypto.Util.number import * |
运行得到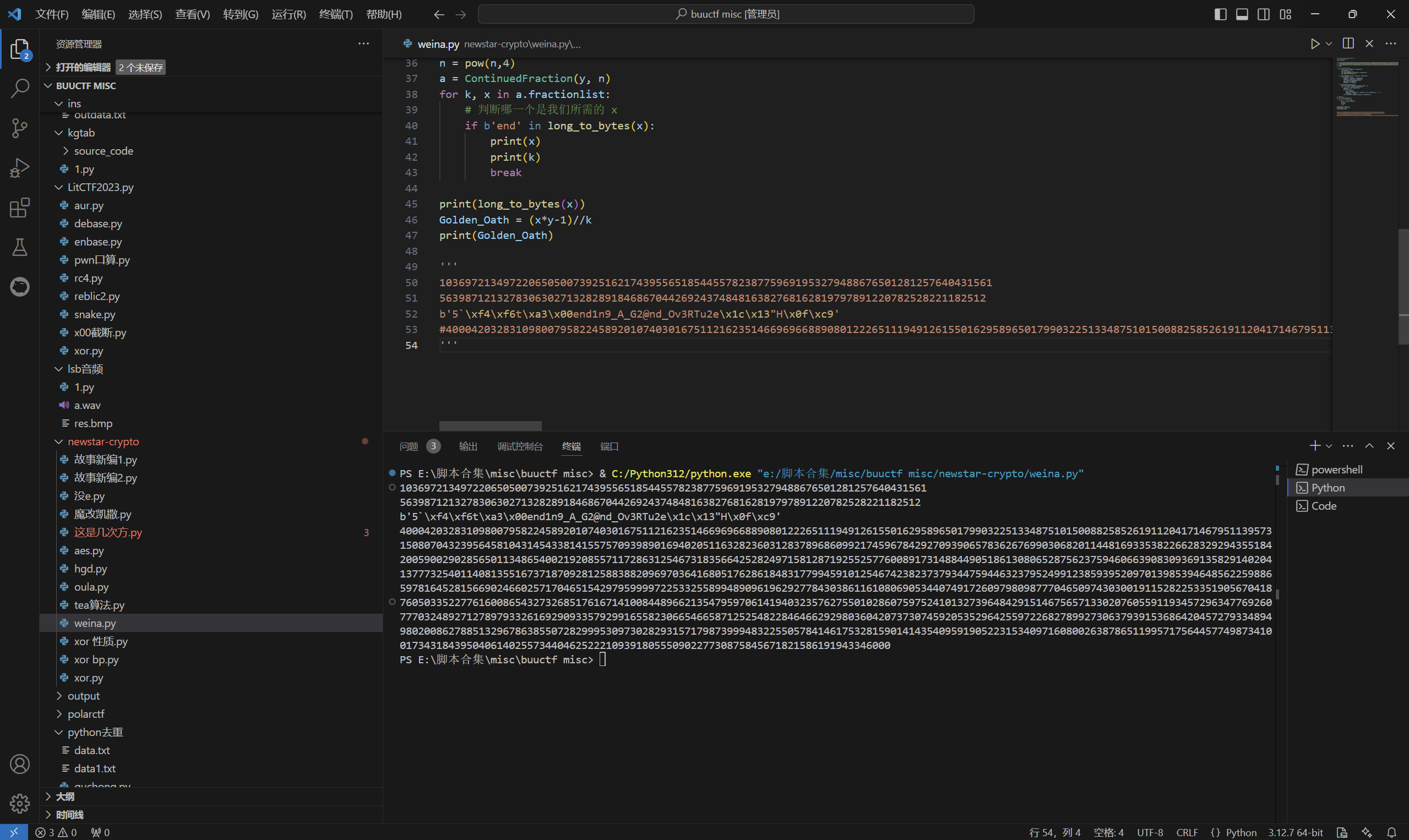
使用 sympy库解方程
exp:
1 | Golden_Oath = 400042032831098007958224589201074030167511216235146696966889080122265111949126155016295896501799032251334875101500882585261911204171467951139573150807043239564581043145433814155757093989016940205116328236031283789686099217459678429270939065783626769903068201144816933538226628329294355184200590029028565011348654002192085571172863125467318356642528249715812871925525776008917314884490518613080652875623759460663908309369135829140204137773254011408135516737187092812588388209697036416805176286184831779945910125467423823737934475944632379524991238593952097013985394648562259886597816452815669024660257170465154297959999722533255899489096196292778430386116108069053440749172609798098777046509743030019115282253351905670418760503352277616008654327326851761671410084489662135479597061419403235762755010286075975241013273964842915146756571330207605591193457296347769260777032489271278979332616929093357929916558230665466587125254822846466292980360420737307459205352964255972268278992730637939153686420457279334894980200862788513296786385507282999530973028293157179873999483225505784146175328159014143540959190522315340971608002638786511995717564457749873410017343184395040614025573440462522210939180555090227730875845671821586191943346000 |
运行得到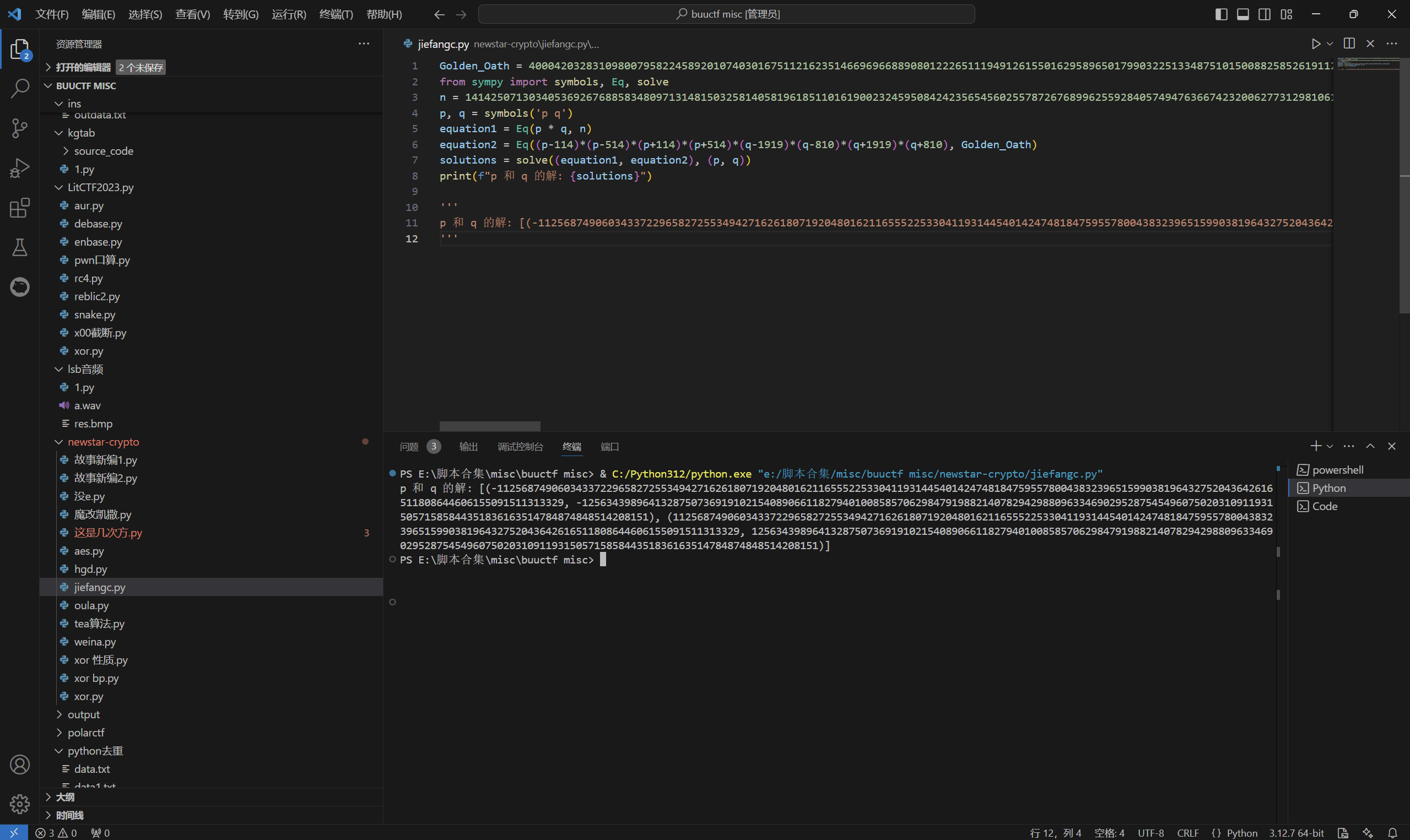
得到p,q,常规rsa解密即可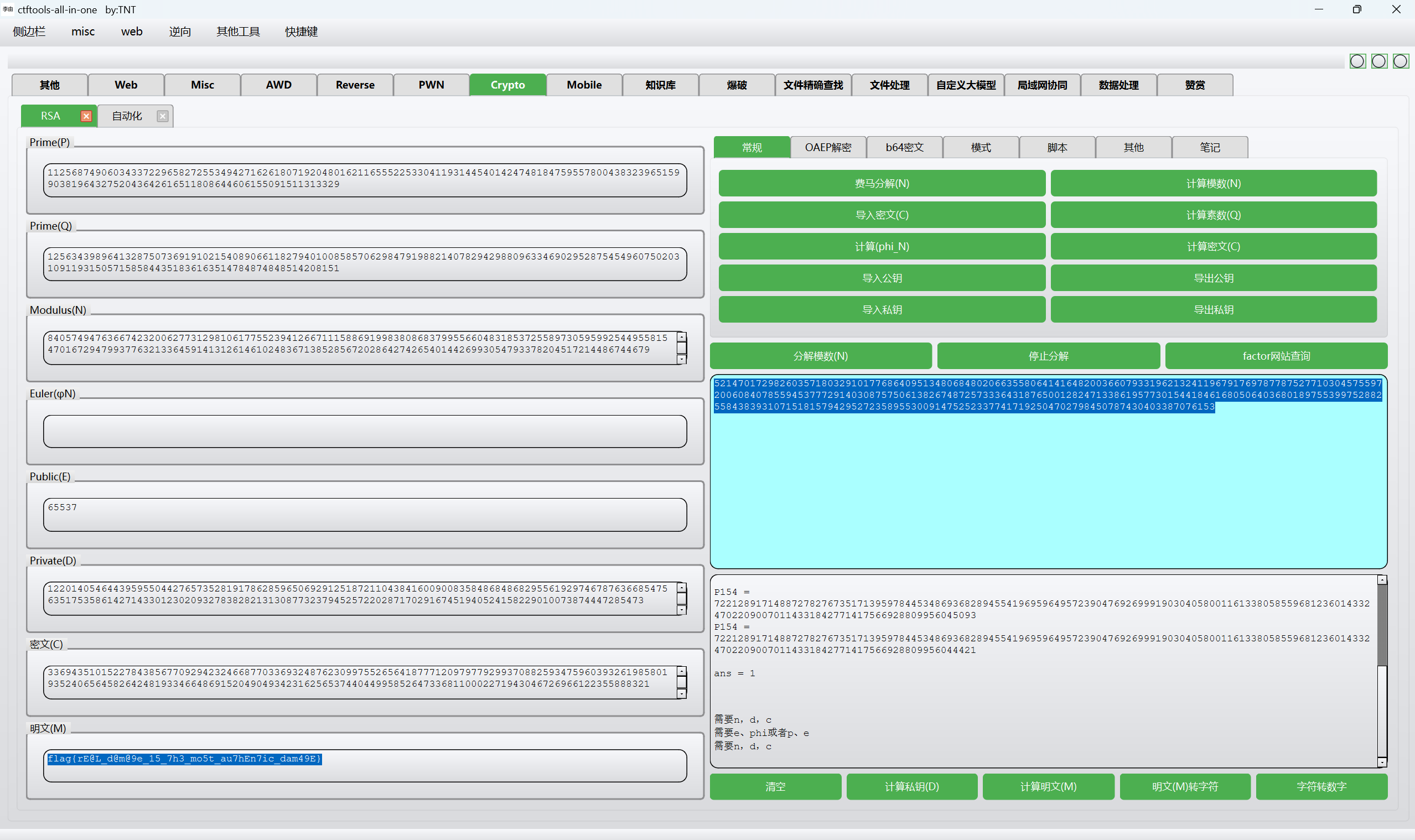
最后flag为
1 | flag{rE@L_d@m@9e_15_7h3_mo5t_au7hEn7ic_dam49E} |
圣石匕首
题目描述:
1 | 贤者拿到了一段 exp,运行它即可快速解开谜题,获取 flag. 但是他好像没有见过这种代码…… |
下载附件
1 | import gmpy2 |
考点:sagemath使用
直接sage运行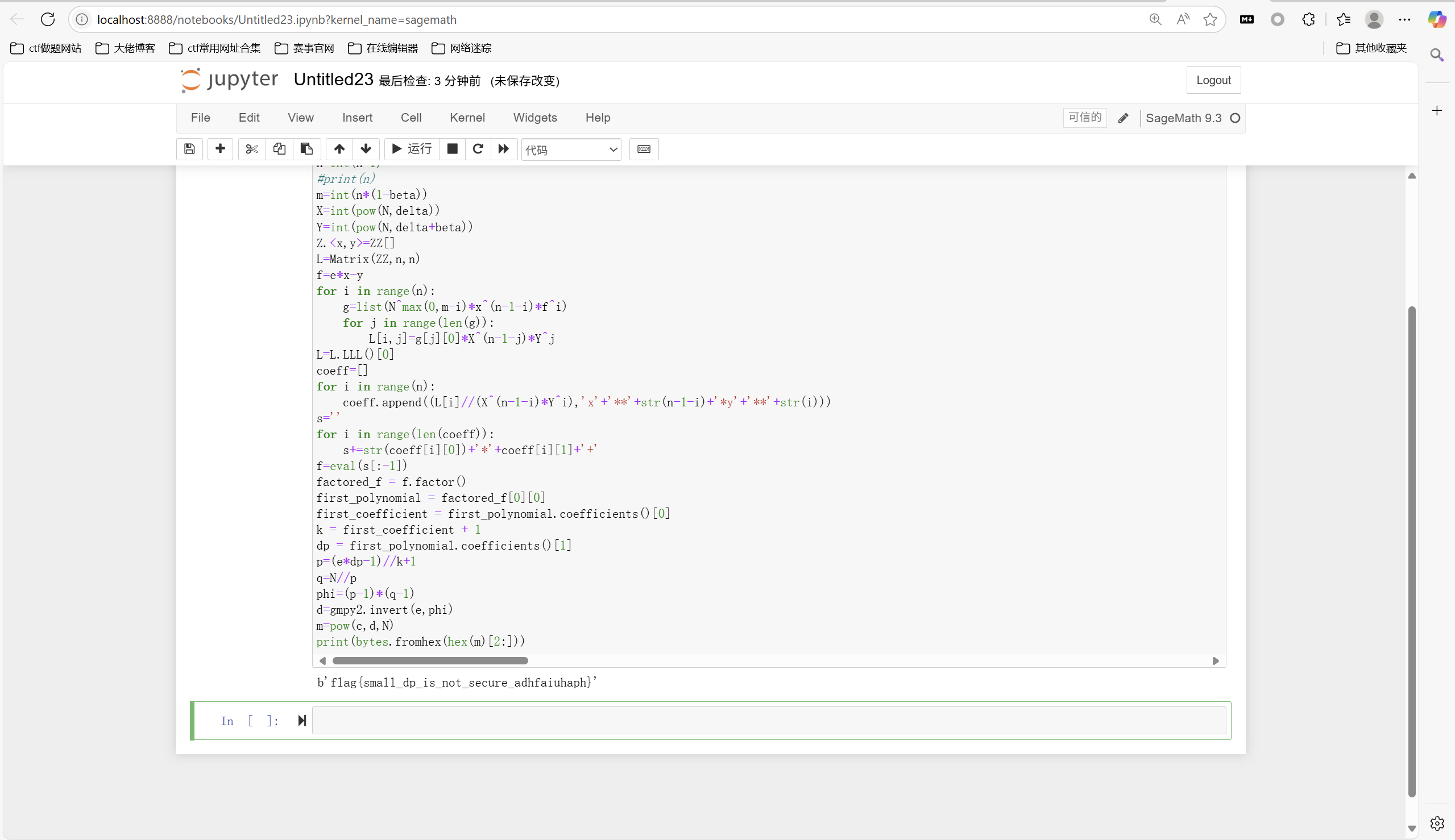
最后flag为
1 | flag{small_dp_is_not_secure_adhfaiuhaph} |
欧拉欧拉!!
题目描述:
1 | 完啦!q 被 ≪大运撞进二进制世界,它能否和 p 联手一起,拿到 φ,回到十进制世界 |
下载附件
1 | from Crypto.Util.number import * |
考点:二进制加法,间接求欧拉函数
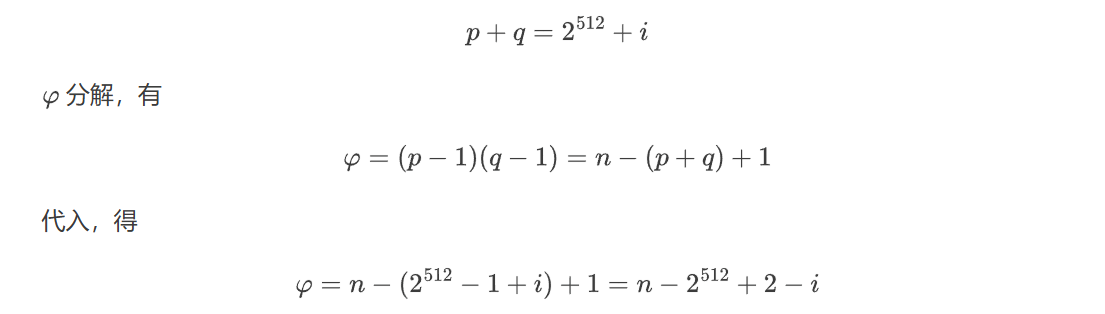
exp:
1 | from Crypto.Util.number import * |
运行得到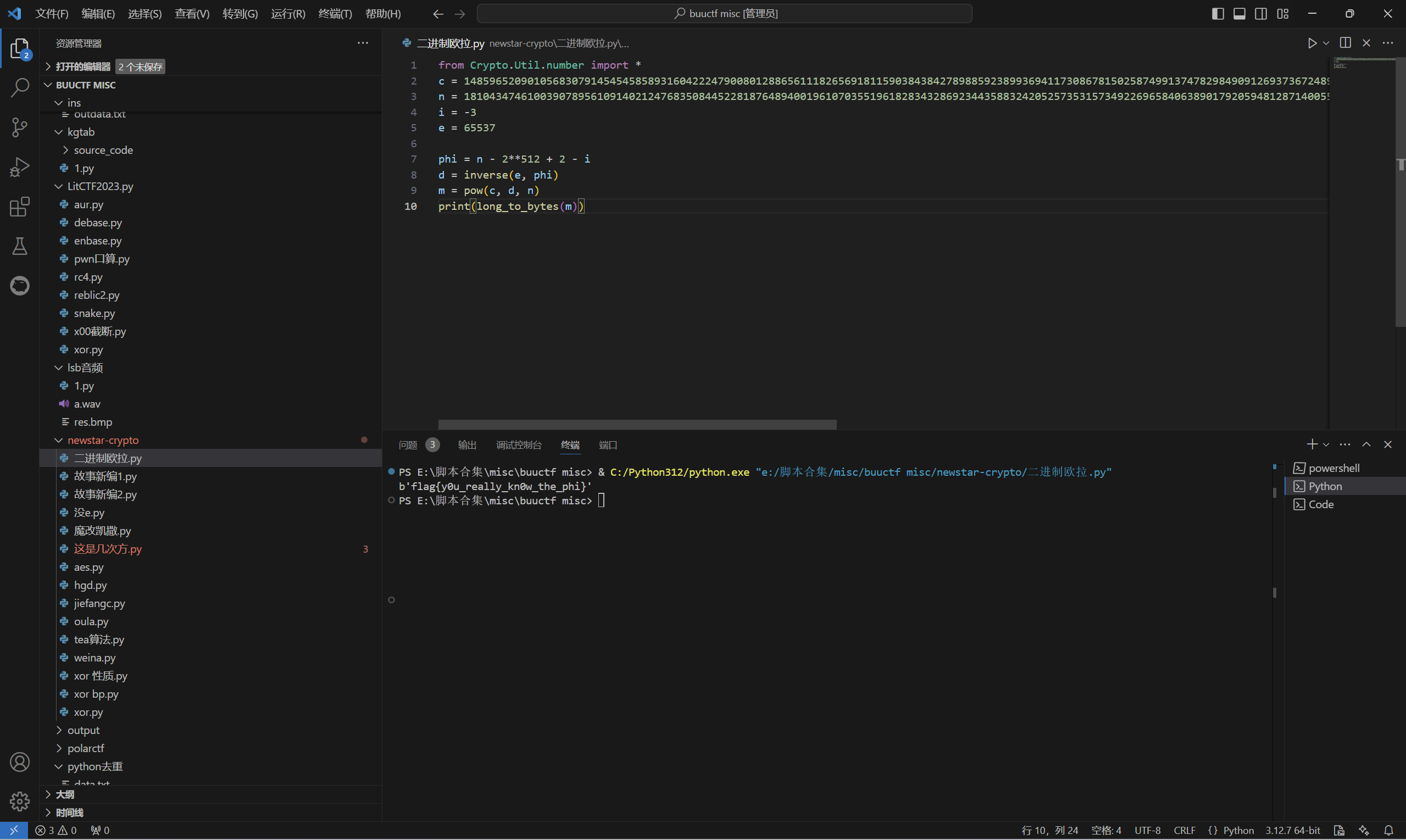
最后flag为
1 | flag{y0u_really_kn0w_the_phi} |
week5
RSA? cmd5!
题目描述:
1 | 应该都了解 RSA 解密原理了吧? |
下载附件
1 | from Crypto.Util.number import * |
考点:RSA MD5数字签名
exp:
1 | from Crypto.Util.number import * |
运行得到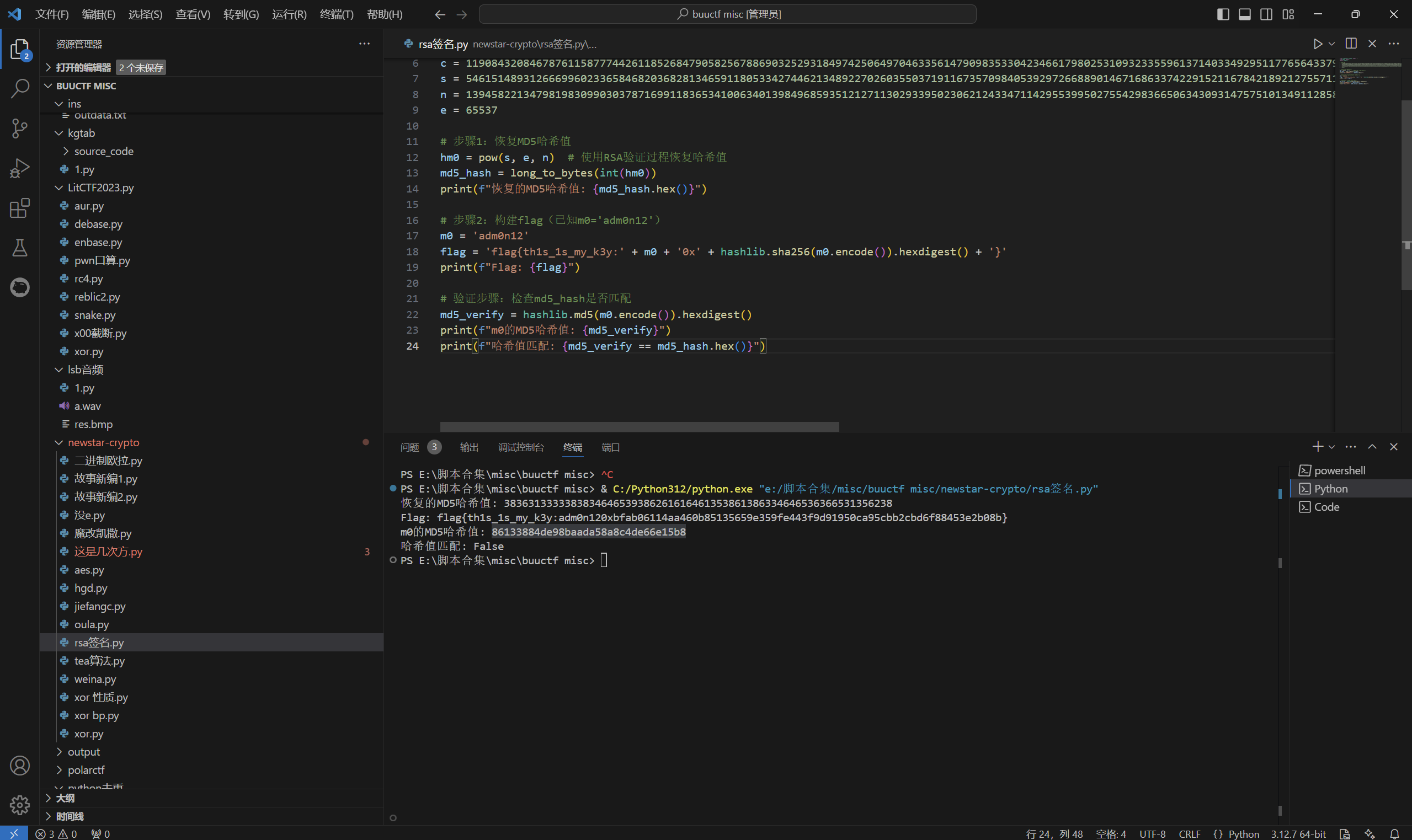
最后flag为
1 | flag{th1s_1s_my_k3y:adm0n120xbfab06114aa460b85135659e359fe443f9d91950ca95cbb2cbd6f88453e2b08b} |
easy_ecc
题目描述:
1 | 简单的椭圆曲线密码入门 |
下载附件
1 | from Crypto.Util.number import * # type: ignore |
考点:ECC
exp:
1 | from Crypto.Util.number import long_to_bytes |
运行得到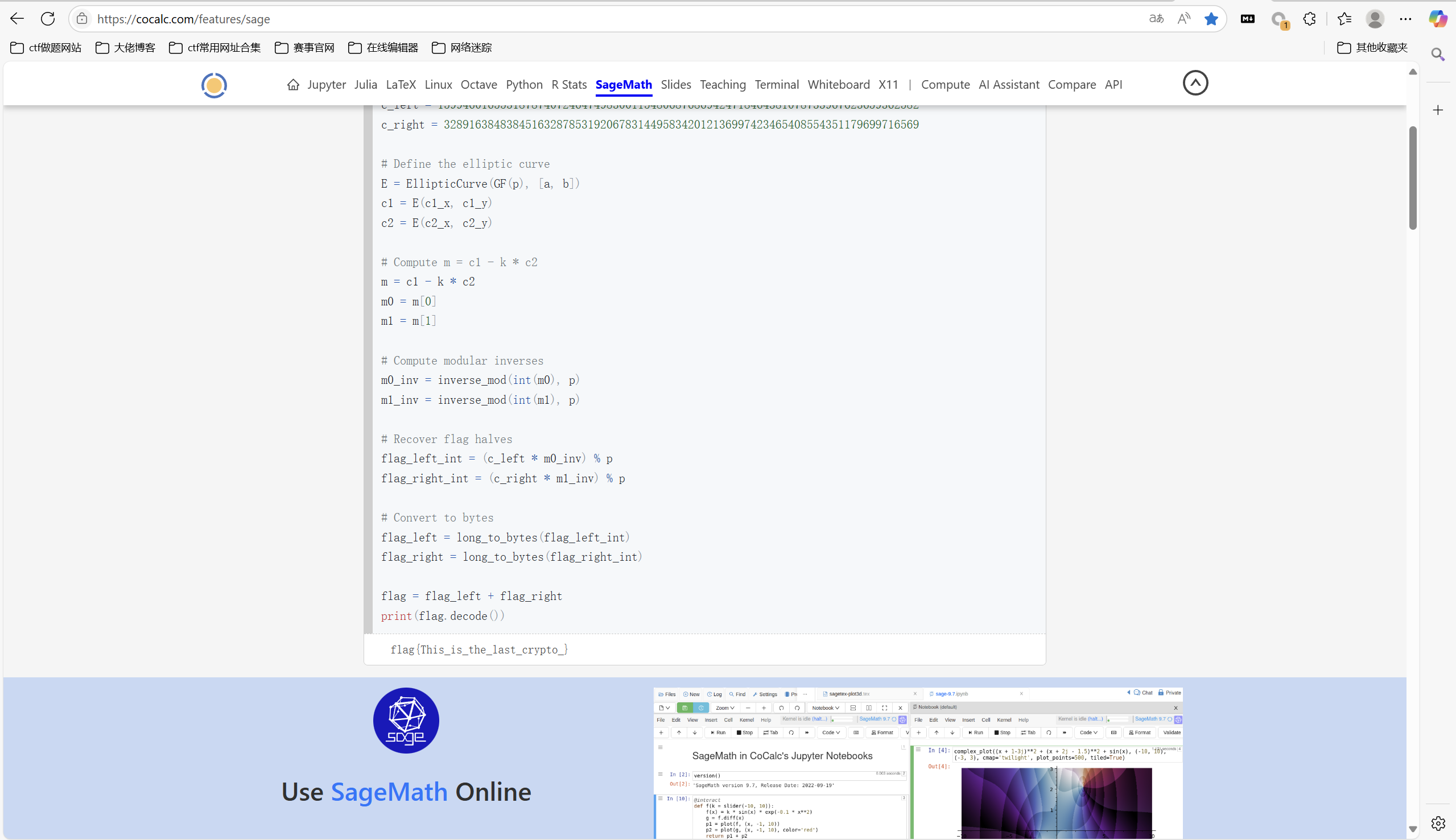
最后flag为
1 | flag{This_is_the_last_crypto_} |
学以致用
题目描述:
1 | —— 帮帮我,sagemath 先生,TAT |
下载附件
1 | import random |
考点:groebner_basis()
3个方程2个未知数,度又很低,直接求groebner_basis
exp:
1 | # sage |
运行得到
最后flag为
1 | flag{W1Sh_you_Bec0me_an_excelL3nt_crypt0G2@pher} |
格格你好棒
题目描述:
1 | 连 n 都没有给的 RSA?!!!快去求救格哥哥! |
下载附件
1 | from Crypto.Util.number import * |
考点:格攻击
参考
【CTF-Crypto】格密码基础(例题较多,非常适合入门!)_ctf crypto-CSDN博客
exp:
1 | from gmpy2 import * |
运行得到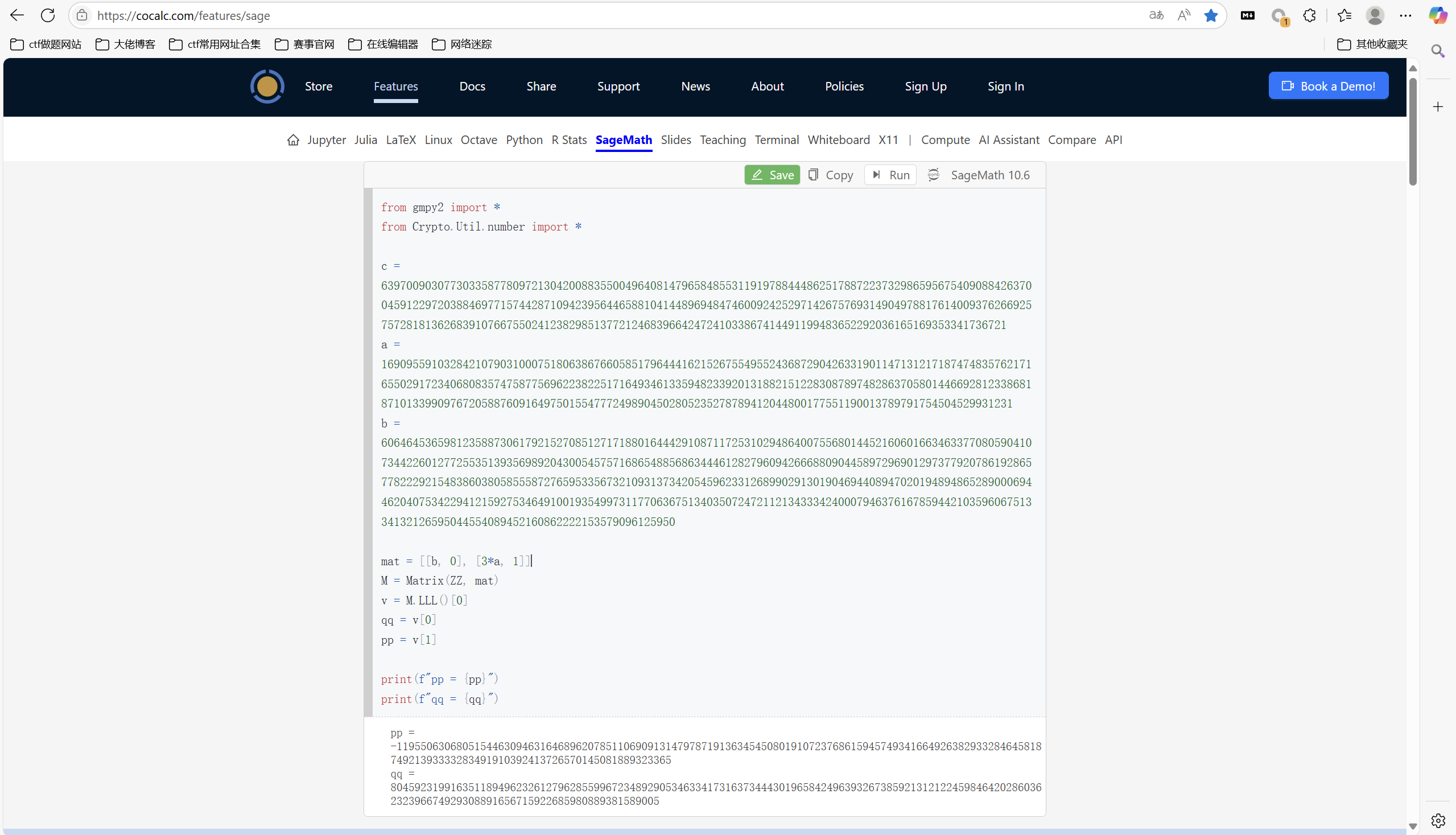
exp:
1 | import gmpy2 |
运行得到flag
1 | flag{u_are_@_master_of_latt1ce_Crypt0gr@phy} |
没 e 也能玩
题目描述:
1 | 哎,不是哥们,没 e 居然也能玩 |
下载附件
1 | from Crypto.Util.number import * |
考点:dp,dq 泄露
一把梭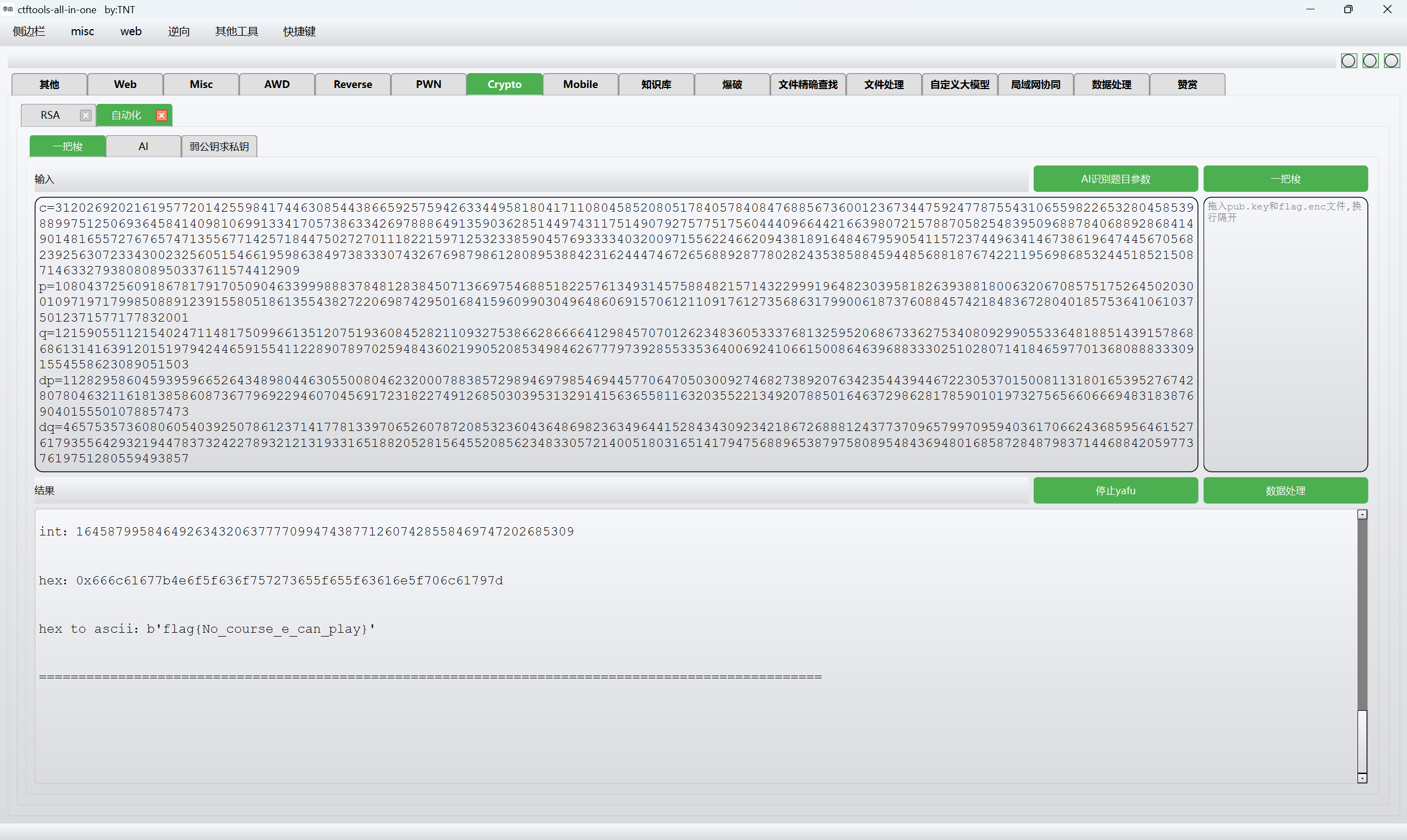
最后flag为
1 | flag{No_course_e_can_play} |